Home > Data Protection > PowerProtect Data Manager > PowerProtect Data Manager: Virtual Machine Backup and Recovery > vCenter authentication
vCenter authentication
-
At the root level of the vCenter, set up a separate vCenter user account that is strictly dedicated for use with Data Manager and the VM Direct protection engine. Use of a generic user account such as “Administrator” might make future troubleshooting efforts difficult because it might not be clear which “Administrator” actions are interfacing, or communicating, with Data Manager. Using a separate vCenter user account ensures maximum clarity if it becomes necessary to examine vCenter logs.
Before using the vCenter user account with Data Manager, or before using the Single Sign-on (SSO) admin user with the VM Direct appliance, the user must be an administrator on the vCenter root node. Users who inherit permissions from group roles are not valid.
Starting with Data Manager 19.15, when adding a VMware vCenter server as an asset source, the “Verify User” option is available to verify if the user has the minimum required vCenter user account privileges. Upon verification of the certificate, the “Verify User” button next to the Host Credentials becomes enabled.
 If the user has sufficient privileges, a message displays indicating that the check completed successfully, and no further action is required. If the check determines that the user does not have all the required privileges, a dialog will display the additional privileges that are required. Add the listed privileges to this user within the vSphere Client or select another user from the host credentials list. If a privilege check failure occurs because the ymdm service is unavailable or there is a network connectivity issue, an error message displays with information on how to resolve the issue.
If the user has sufficient privileges, a message displays indicating that the check completed successfully, and no further action is required. If the check determines that the user does not have all the required privileges, a dialog will display the additional privileges that are required. Add the listed privileges to this user within the vSphere Client or select another user from the host credentials list. If a privilege check failure occurs because the ymdm service is unavailable or there is a network connectivity issue, an error message displays with information on how to resolve the issue.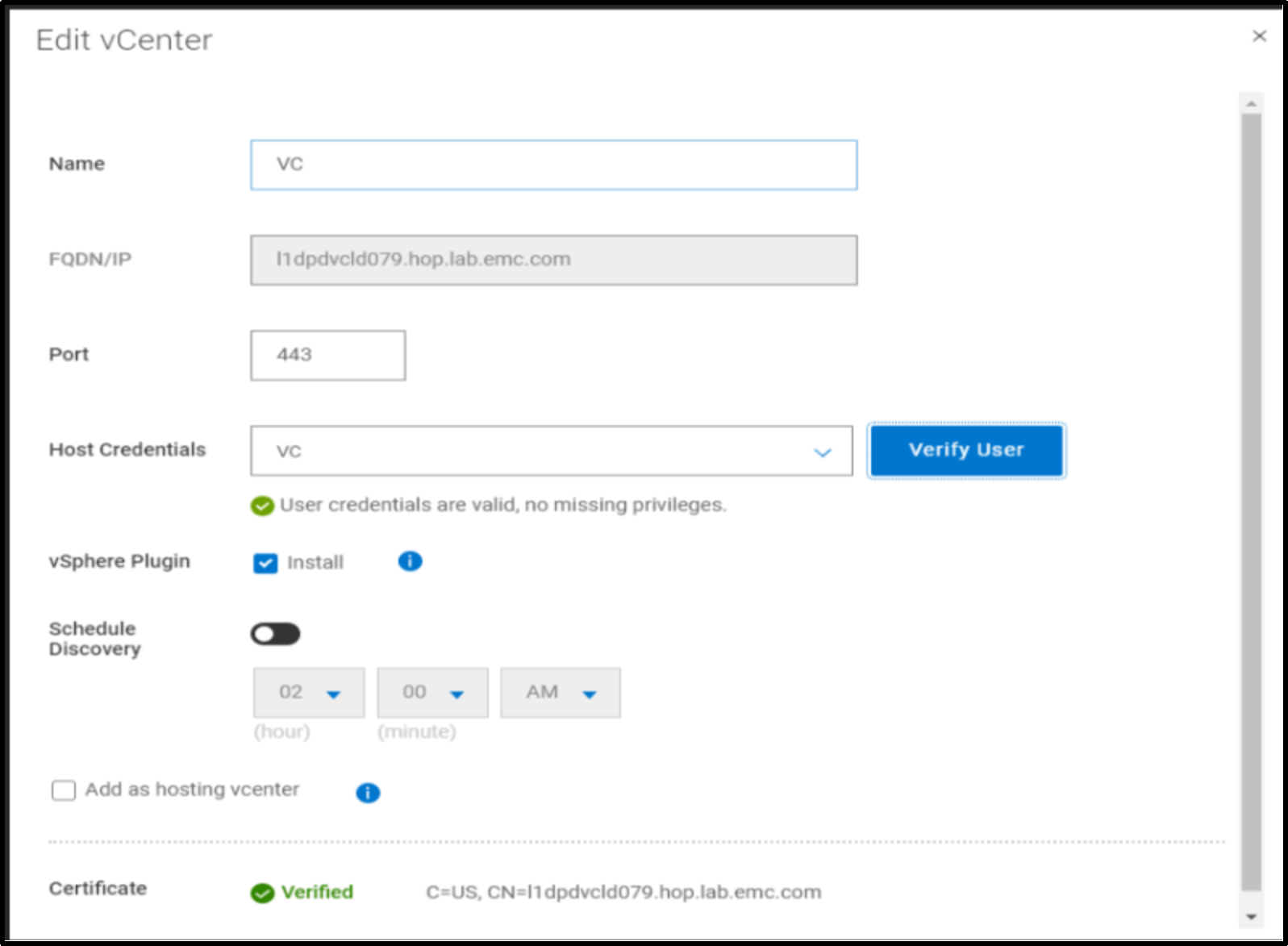

Note: ESX 6.0 U2 and above are supported for VMware Protection. By default, Data Manager enforces SSL certificates during communication with vCenter Server. If a certificate appears, click Verify to accept the certificate. Do not disable certificate enforcement.
