

What's New in PowerStore OS 3.5?
Fri, 19 May 2023 16:56:13 -0000
|Read Time: 0 minutes
Dell PowerStoreOS 3.5 is the latest software release for the Dell PowerStore platform. In this release, there has been a large focus on data protection and security for PowerStore T as well as File networking, scalability, and more. We’ll cover all of these in this blog!
The following list highlights the major features to expect in this software release followed by additional details for each category.
- Security: On the security side of the house, we’ve implemented support for Multi-Factor Authentication (MFA) for PowerStore Manager and REST API using RSA SecurID. Following the US Federal Security Technical Guide conditions, PowerStore now complies with STIG requirements. Also, users can now import a 3rd party certificate for the VMware VASA provider.
- Data Protection: We’ve added a few different enhancements to our data protection capabilities: the largest feature is a native backup solution that integrates with Dell PowerProtect DD series appliances. Metro Volume has seen some UI enhancements to help guide customers on selecting appropriate host connectivity options. The new secure snapshot setting protects snapshots from being accidentally or maliciously deleted.
- File Enhancements: Through PowerStore Manager and REST, users can now manage file share permissions (ACLs). Fail-Safe Networking (FSN) can be created for NAS server interfaces, a lightweight and switch-agnostic form of link redundancy that complements link aggregation.
- Scaling & Capacity: We’ve improved scalability limits for file systems, volumes, and vVols. We’ve also added a Recycle Bin for retrieving deleted volumes, volume groups, and snapshots within an expiration period.
Security
Multi-Factor Authentication
Multi-Factor Authentication (MFA), also known as two-factor authentication, has become a modern-day standard not only in the datacenter, but in our everyday lives. In PowerStoreOS 3.5 and later, users can now enable MFA for PowerStore Manager and REST API. Once configured using your existing RSA Authentication Manager, users have two-factor authentication with LDAP users or PowerStore manager users using their RSA SecurID token.
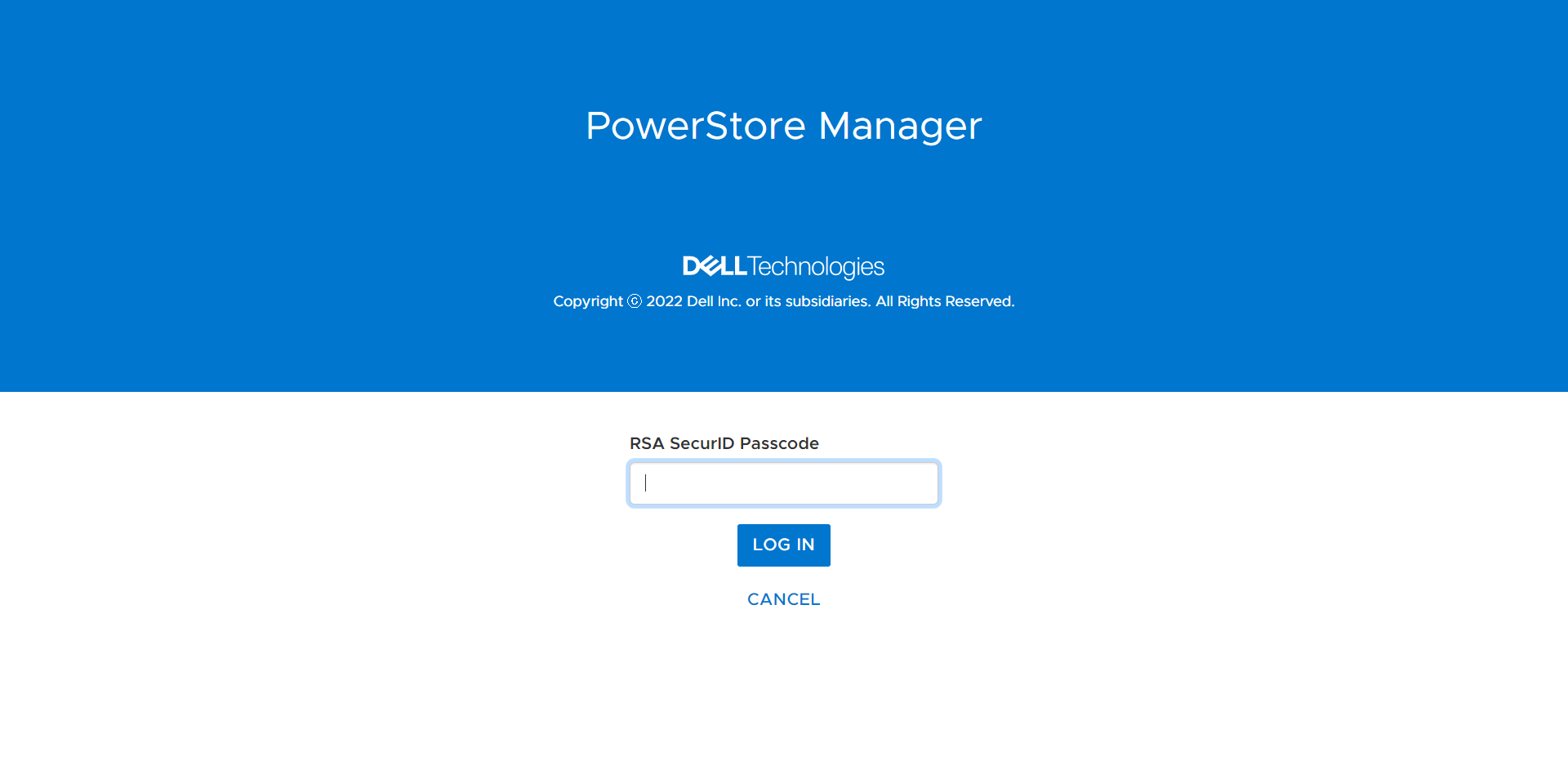
Security Technical Implementation Guides (STIG compliance)
STIG mode is an optional setting that implements security configuration changes to harden the existing appliance all the way down to PowerStore’s base OS and containers. Having STIG compliance is typically a requirement for US Federal customers and dark sites alike. STIG compliance is also a prerequisite for the Approved Product List (APL) certification which is a standard for Department of Defense (DoD) organizations.
With Multi-Factor Authentication, Secure Snapshots, and STIG compliance, PowerStore is hardened to accommodate the security requirements of the US Federal Government and Zero Trust security environments.
Data Protection
Native PowerProtect DD Backup Integration
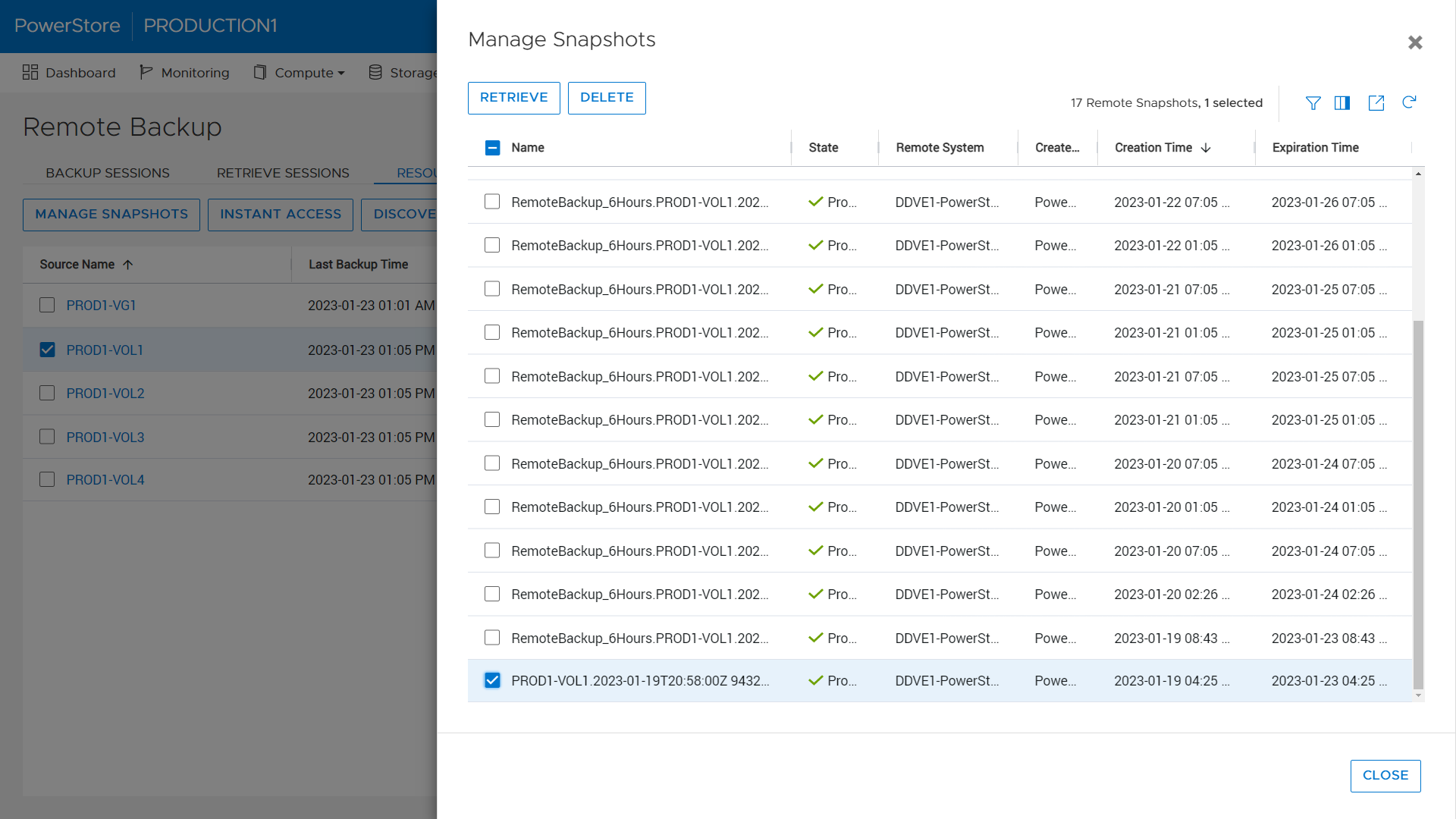
Studies show that using a backup and storage solution from a single vendor can reduce data protection administration costs by up to 22%. Using PowerStore’s native PowerProtect integration, backups in the form of remote snapshots can be initiated directly from PowerStore Manager using a remote connection to the PowerProtect DD appliance (physical or virtual edition). Users can set up cloud or on-prem backup in just 90 seconds natively within PowerStore Manager. PowerStore enables faster backups through tight integration with PowerProtect DD Appliances, enabling the ability to back up to 150TB daily.
Backups can be initiated manually or through a new protection rule called a Remote Backup Rule. Users can create remote backup sessions, retrieve snapshots, recover deleted or corrupted resources, and provide hosts with access to snapshots directly on the PowerProtect appliance. This host access, called Instant Access, provides access to data from a remote PowerProtect appliance in just seven clicks from a single UI.
Metro Volume
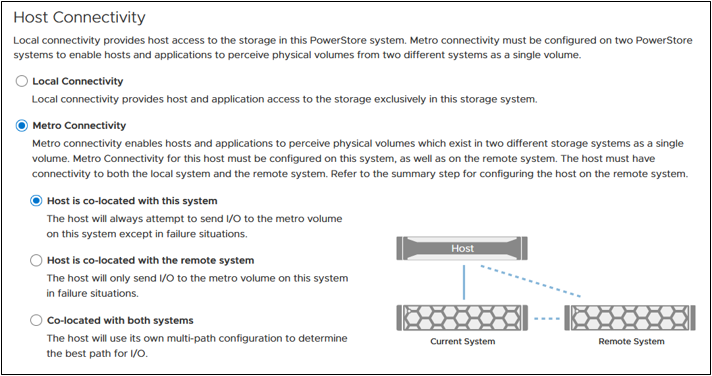
Native Metro Volume, PowerStore’s synchronous active/active block replication technology introduced in PowerStoreOS 3.0, has been updated to include graphical representation of the host’s connectivity during setup to help users pick the right configuration. These configurations are Local Connectivity (also known as non-uniform), where the host is only connected to the local PowerStore appliance, and Metro Connectivity (known as uniform), where the host has connections to both local and remote PowerStore appliances. When selecting metro connectivity, the UI helps guide the user through the different connectivity options:
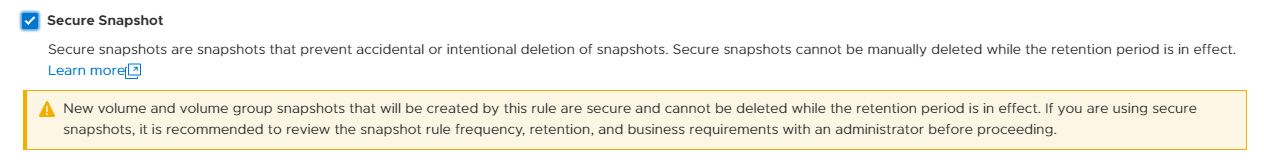
Secure Snapshots
The Secure Snapshot setting is an optional setting for volume and volume group snapshots. When the Secure Snapshot setting is enabled, the snapshot is protected from deletion until the retention period expires. The Secure Snapshot option also cannot be disabled on a snapshot after it is enabled. This provides a cost-effective line of defense against ransom attacks and accidental deletion of snapshots, volumes, or volume groups. Secure snapshots can also be created automatically using a Protection Policy containing a Snapshot Rule with the Secure Snapshot option enabled. The Secure Snapshot option within the Snapshot Rule can be enabled or disabled at any time. Changing this setting only affects future snapshot creations.
File enhancements
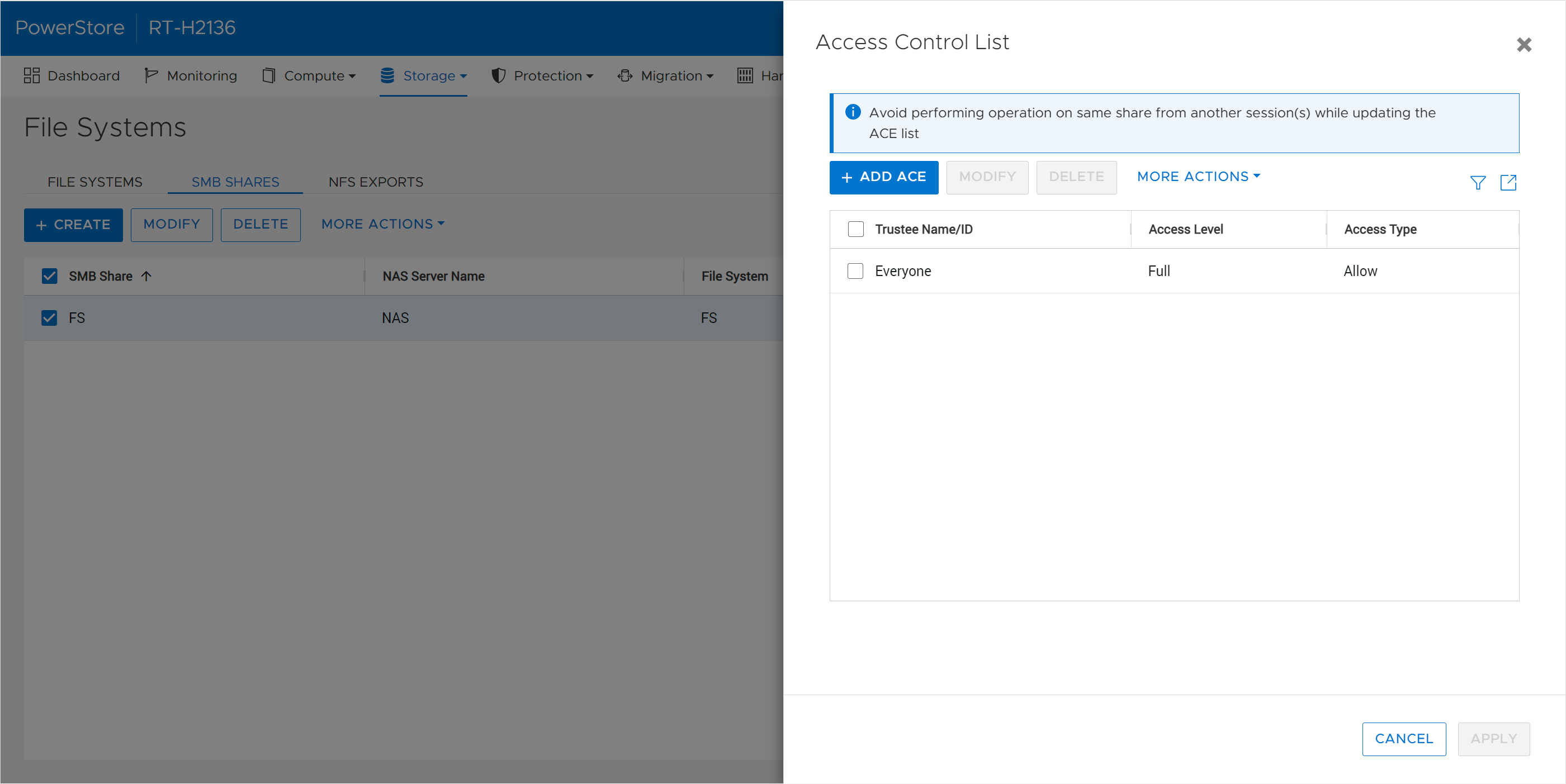
SMB share permissions (ACLs)
When provisioning a NAS share usingthe SMB protocol, the share permissions are managed from the client within an Access Control List (ACL). With PowerStoreOS 3.5, these permissions within the ACL can be managed directly from PowerStore Manager or REST API. Leveraging this feature, PowerStore users can define and manage existing share permissions without requiring access to the client-side environment.
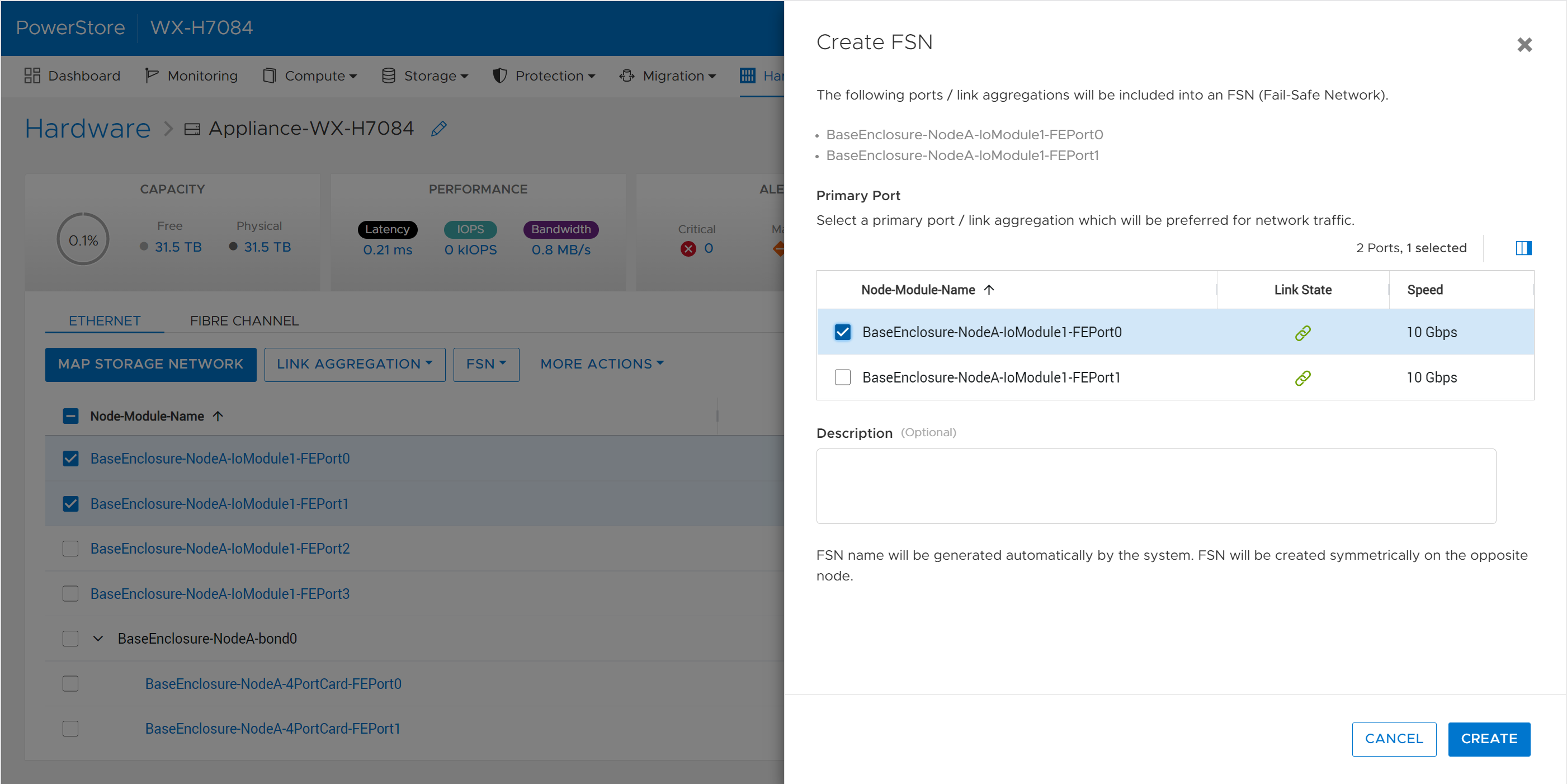
Fail-Safe Networking (FSN)
Fail-Safe Networking is a well-known feature used in other products across the Dell portfolio, such as Unity XT, which provides a mechanism for switch-level redundancy. You may ask if this is needed since PowerStore already supports Link Aggregation (LA). Fail-Safe Networking provides a high availability solution that is switch agnostic for NAS interfaces. With FSN, users can eliminate single points of failure (ports, cables, switches, and so on) by linking ports together in an active/passive configuration. An FSN can consist of individual ports, Link Aggregations, or a combination of both. When used in conjunction with LA, multiple ports can be used as part of the active or backup part of the FSN.
Scalability and Capacity
File, volume, and vVol limit increase
Across the board, PowerStoreOS 3.5 brings increased limits to the number to file systems, volumes, and vVols that can be provisioned. The amount that the limits have increased for each of these resources depends on the PowerStore model. A few examples: the number of NAS servers for the PowerStore 3200 and higher is increased from 50 to 250 NAS servers per appliance. On a PowerStore 9200, the combined max number of volumes, vVols, and file systems is now 16,600 per appliance. There are also up to 4x the number of .snapshot files and file systems that can be provisioned. For a full list of resource limits on PowerStore, check out the support matrix.
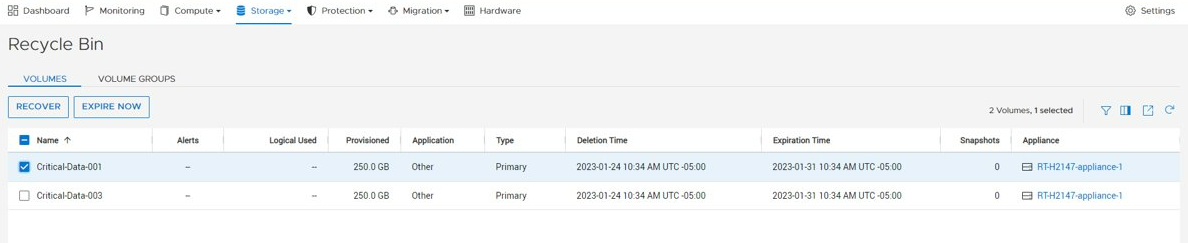
Recycle bin
Research indicates that human error proves to be the most common cause of data loss - typically in the form of accidental deletion of data, unorganized data, or administrative errors. In the PowerStoreOS 3.5 release, we’ve introduced a recycle bin feature to combat accidental deletion of block storage resources. If a block resource is deleted, it will enter the recycle bin by default. The recycle bin is located in the Storage > Recycle Bin section of PowerStore Manager. In there, users can view, restore, and permanently expire volumes, volume groups, and their corresponding snapshots. Users can also customize the expiration period from 0-30 days depending on their requirements.
Conclusion
The PowerStoreOS 3.5 release offers a multitude of enhancements across the board for the PowerStore product. In the modern data center, PowerStore continues to deliver on security, data protection, and scalability with the performance of an end-to-end NVMe platform. It’s no wonder that PowerStore is deployed in over 90% of Fortune 500 vertical sectors and rated #1[1] in customer satisfaction!
Resources
For additional information about the features above, along with other information about the PowerStoreOS 3.5 release, consult the whitepaper and solution documents found below:
- Data Protection for PowerStore with PowerProtect DD Series Appliances
- Dell PowerStore Native Integration with Dell PowerProtect DD Series Appliances for DP in Oracle Environments
- Time to Rethink your SQL Backup Strategy – Part 2
- Dell PowerStore: Snapshots and Thin Clones
- Dell PowerStore: Cybersecurity
- Dell PowerStore: File Capabilities
- Dell PowerStore: Persistent Data Availability
- Dell PowerStore: Metro Volume
- Dell PowerStore: Microsoft SQL Server Best Practices
- Dell PowerStore: Oracle Best Practices
- Dell PowerStore: Microsoft Hyper-V Best Practices
- Dell PowerStore: MongoDB Solution Guide
- Dell PowerStore: VMware vSphere Best Practices
- Dell PowerStore: VMware vSphere with Tanzu and TKG Clusters
- Dell VxRail and Dell PowerStore: Better Together Through Dynamic AppsON
Other Resources
- What’s New In PowerStoreOS 3.2?
- PowerStore Simple Support Matrix
- PowerStore: Info Hub - Product Documentation & Videos
- Dell Technologies PowerStore Info Hub
Authors: Ryan Meyer and Ryan Poulin
[1] Based on Dell analysis in January 2022 comparing among Top 3 storage providers globally, using double-blinded, competitive benchmark Net Promoter Score (NPS) data gathered by third-party commissioned by Dell for 2H FY22.
Related Blog Posts

What’s New in PowerStoreOS 3.6?
Thu, 05 Oct 2023 14:22:36 -0000
|Read Time: 0 minutes
Dell PowerStoreOS 3.6 is the latest software release on the Dell PowerStore platform.
This release contains a diversified feature set in categories such as hardware, data protection, NVMe/TCP, file, and serviceability. The following list provides a brief overview of the major features in those categories:
- Hardware: PowerStoreOS 3.6 introduces the highly anticipated Data-In-Place (DIP) upgrade feature, which allows users to perform a hardware refresh while remaining online, with no downtime or host migration.
- Data Protection: PowerStoreOS 3.6 now includes support for Metro Witness Server, which allows users to configure a fully active-active configuration for metro volumes across two PowerStore clusters—with more intelligent failure handling, resiliency, and availability during an unplanned outage.
- NVMe/TCP enhancements: Users now have the option to use NVMe storage containers to support host access through the NVMe/TCP protocol for Virtual Volumes (vVols).
- File: Administrators can perform disaster recovery tests within a network bubble, while using an identical configuration as their production NAS server environment.
- Serviceability: To build on the existing remote syslog implementation, PowerStore alerts can now be forwarded to one or more remote syslog servers in PowerStoreOS 3.6. The following sections also provide information about the Non-Disruptive Upgrade (NDU) paths to the PowerStoreOS 3.6 release.
Hardware
Data-In-Place (DIP) upgrades
Data-In-Place upgrades allow users to convert their PowerStore Appliance from a PowerStore x000T model to a PowerStore x200T model. This is a non-disruptive process because only a single node is upgraded at a time, while the other node continues to service host I/O. Data-In-Place upgrades are performed easily through PowerStore Manager’s Hardware tab.
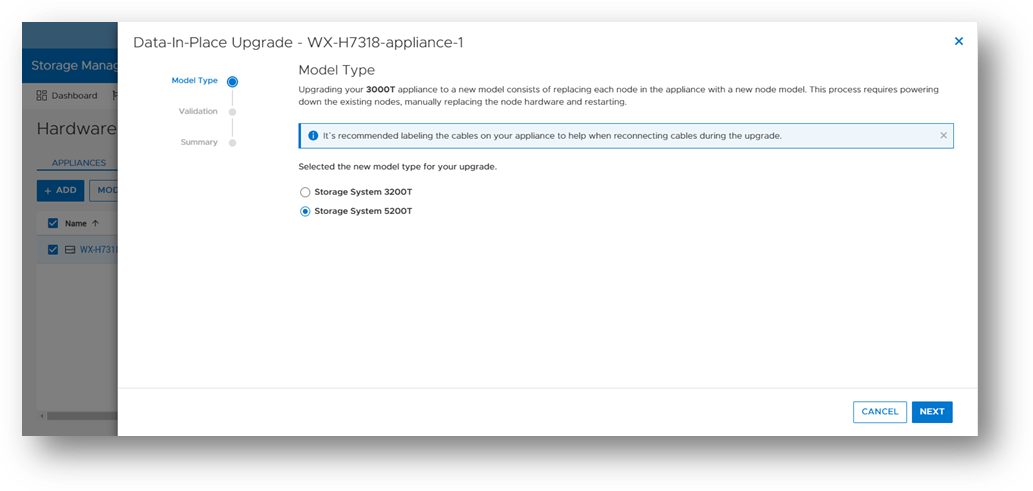
The following table outlines the supported Data-In-Place upgrade paths from the source to target models. For PowerStore 9000T models, only block-optimized upgrades are supported to the PowerStore 9200T model. When upgrading a PowerStore 3000T to a PowerStore 5200T model, additional NVRAM drives are required. When upgrading from a PowerStore 5000T model to a PowerStore 9200T model, a power supply upgrade may also be required.
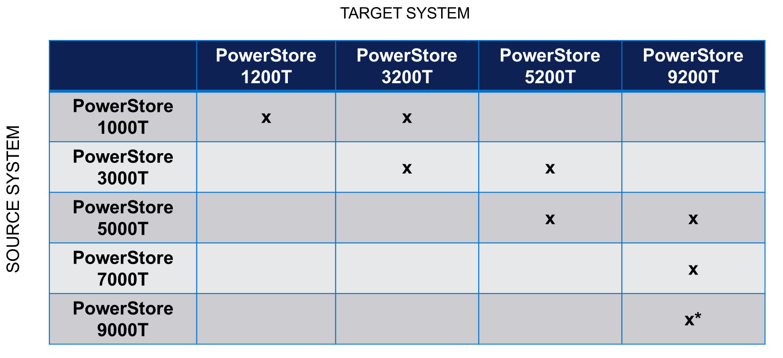
Note: *Denotes only block-optimized upgrade is supported
Data Protection
Metro Witness server support
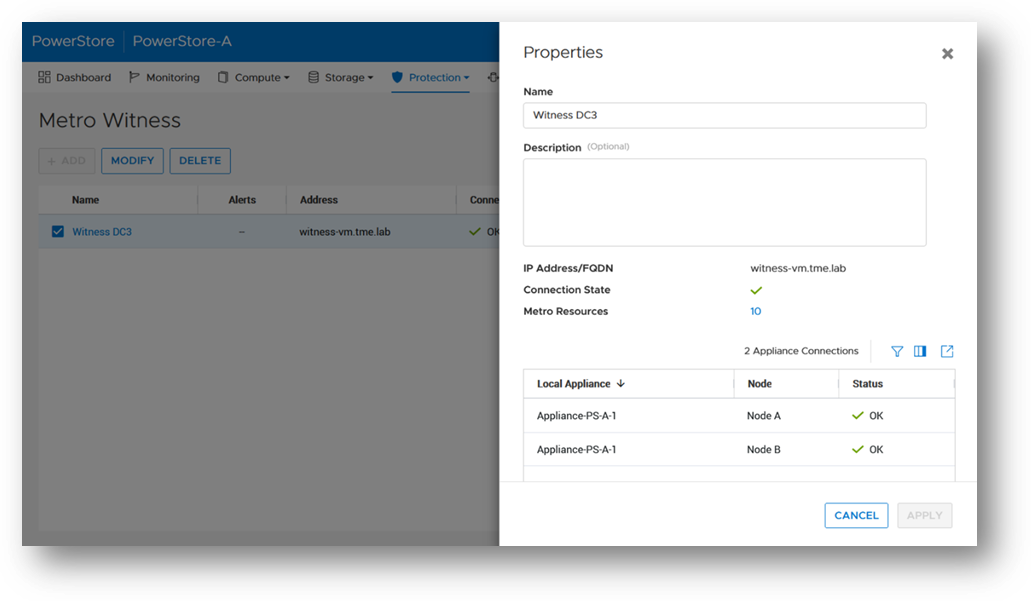
Metro Volume support was introduced in PowerStoreOS 3.0. Since PowerStoreOS 3.0, Metro Volumes required manual intervention to fail over if the preferred site went down. PowerStoreOS 3.6 introduces the Metro Witness server feature. The Metro Witness server runs software that automatically forces the non-preferred site to remain online and service I/O if the preferred site were to go offline.
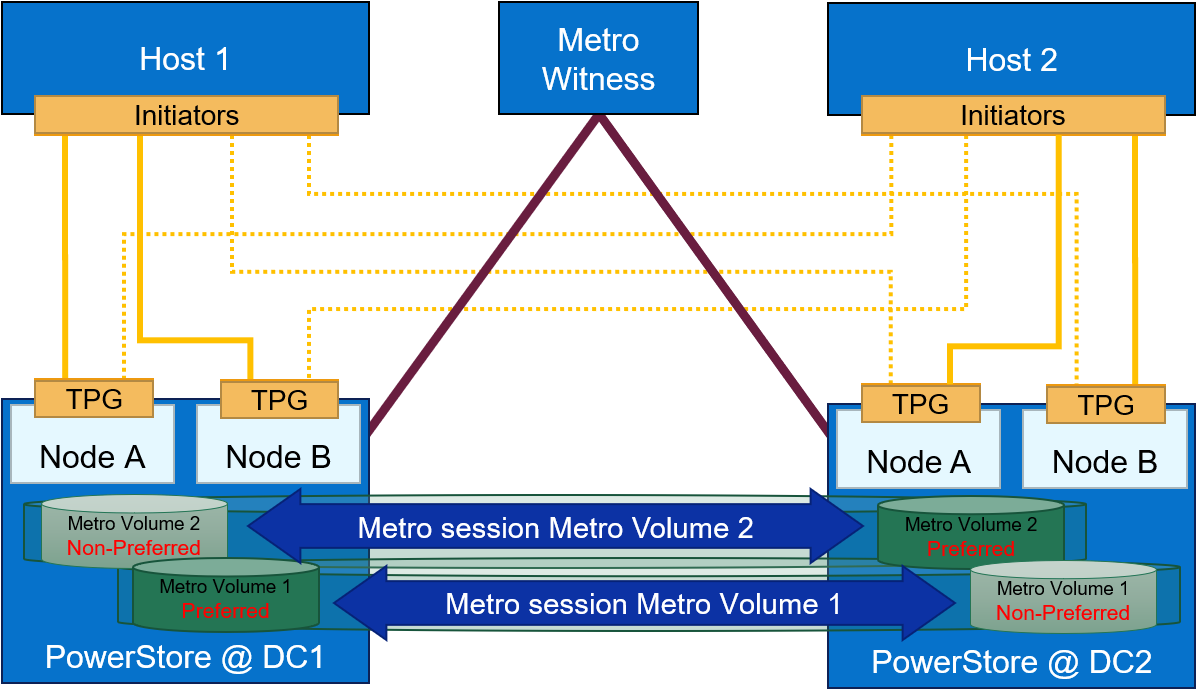
The Metro Witness software is a distributed RPM package available for Linux SLES or RHEL distributions. The RPM can be deployed on a bare-metal server or a virtual machine. The Metro Witness server and software can easily be set up in minutes!
NVMe/TCP enhancements
NVMe/TCP for Virtual Volumes (vVols)
NVMe is transfer protocol that is specifically designed for connecting Solid State Drives (SSDs) to PCIe buses. NVMe over Fabrics (NVMe-oF) is an extension of the NVMe protocol to both TCP and Fibre Channel (FC) data streams. PowerStore currently supports both TCP and FC as NVMe-oF transports.
With the VMware vSphere 8.0U1 release, VMware introduced NVMe/TCP support for vVols. As the request for NVMe/TCP support grows, PowerStoreOS 3.6 expands its existing NVMe/TCP support to vVols as well! With this feature, PowerStore will be the industry’s 1st array to support NVMe/TCP for vVols[1].
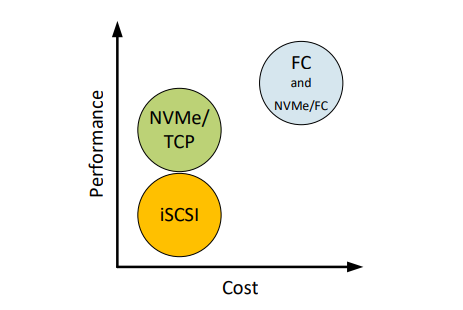
From a performance perspective, NVMe/TCP is comparable to FC. From a cost perspective, NVMe/TCP infrastructure is cheaper than FC and can leverage existing network infrastructure. NVMe/TCP has a higher performance benefit than iSCSI and has lower hardware costs than FC. With the addition of NVMe/TCP support for vVols in PowerStoreOS 3.6, we combine performance, cost, and storage/compute granularity for system administrators.
File
Disaster Recovery (DR) tests within a network bubble
Many organizations are required to run disaster recovery (DR) tests using the exact same configuration as production. This includes identical IP addresses and fully qualified domain names. Running these types of tests reduces risk, increases reproducibility, and minimizes the chance of any surprises during an actual disaster recovery event.
These DR tests are carried out in an isolated environment, which is completely siloed from the production environment. Using network segmentation for proper isolation allows there to be no impact to production or replication. This allows users to meet the requirements of using identical IP addresses and FQDNs during their DR tests.
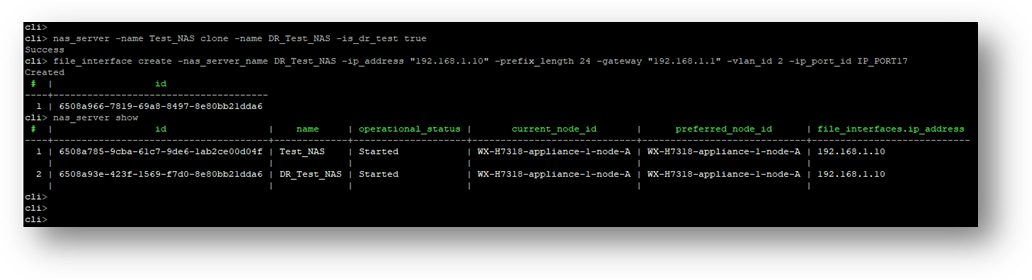
In PowerStoreOS 3.6, the appliance offers the file capability to create a Disaster Recovery Test (DRT) NAS server with a DR test interface. These DRT NAS servers permit a user to create a NAS server with an identical configuration as production, including the ability to duplicate IP addresses.
Note: DRT NAS servers and interfaces can only be configured using the CLI or REST API.
Serviceability
Remote Syslog support for PowerStore alerts
PowerStoreOS 2.0.x introduced support for remote syslog for auditing. These audit types included:
- Config
- System
- Service
- Authentication / Authorization / Logout
PowerStoreOS 3.6 has added support for forwarding of system alerts as well. This equips system administrators with more versatility to monitor their PowerStore appliances from a centralized location.
Upgrade Path
The following table outlines the NDU paths to upgrade to the PowerStoreOS 3.6 release. Depending on your source release, it may be a one or two step upgrade.
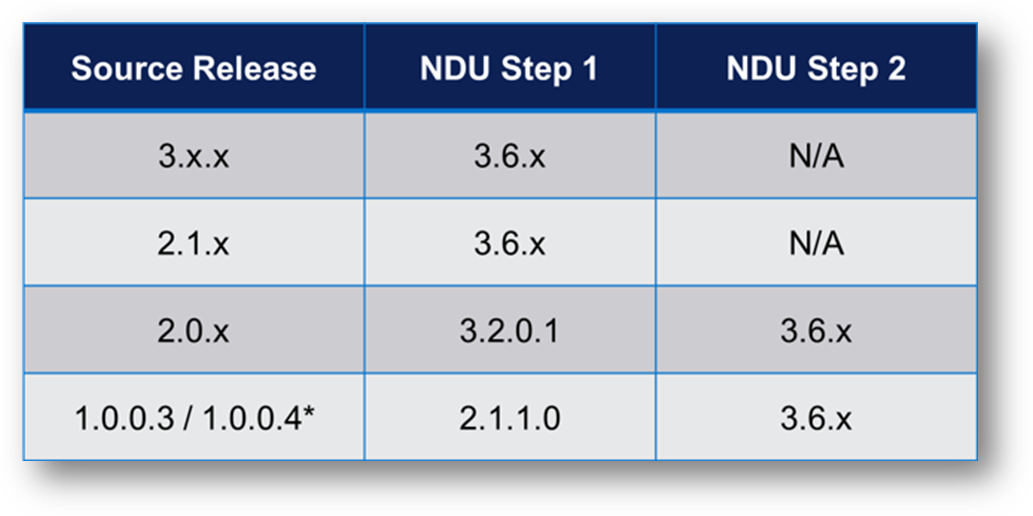
Note: *Denotes source release is not supported on PowerStore 500T models
Conclusion
The PowerStoreOS 3.6 release offers numerous feature enhancements that are unique and deepen the platform. It’s no surprise that PowerStore is deployed in over 90% of Fortune 500 vertical sectors[2] [1]. With PowerStore continuing to deliver on hardware, data protection, NVMe/TCP, file, and serviceability in this release, it’s no secret that the product is extremely adaptable and versatile in modern IT environments.
Resources
For additional information about the features described in this blog, plus other information about the PowerStoreOS 3.6 release, see the following white papers and solution documents:
- Dell PowerStore: Introduction to the Platform
- Dell PowerStore Manager Overview
- Dell PowerStore: File Capabilities
- Dell PowerStore: Replication Technologies
- Dell PowerStore: Virtualization Integration
- Dell PowerStore: Metro Volume
- Dell PowerStore: VMware vSphere Best Practices
- Dell PowerStore: VMware Site Recovery Manager Best Practices
- Dell PowerStore: VMware vSphere with Tanzu and TKG Clusters
- NVMe Transport Performance Comparison
Other Resources
- What’s New in PowerStoreOS 3.5?
- PowerStore Simple Support Matrix
- PowerStore: Info Hub – Product Documentation & Videos
- Dell Technologies PowerStore Info Hub
Author: Louie Sasa
[1] PowerStore is the industry's first array to support NVMe/TCP for vVols. Based on Dell internal analysis, September 2023.
[2] As of January 2023, based on internal analysis of vertical industry categories from 2022 Fortune 500 rankings.

Getting Tough with PowerStore and STIG Mode: Meeting Federal Compliance Requirements
Wed, 09 Aug 2023 15:22:52 -0000
|Read Time: 0 minutes
US Federal Security Technical Information Guide (STIG) overview
Compliance with the US Federal Security Technical Information Guide requirements, (STIG compliance) is a critical feature for many of our customers in the Federal space. STIG compliance is also a prerequisite for the Approved Product List (APL) certification. The latter is also a requirement for some Department of Defense (DoD) sites.
How PowerStoreOS 3.5 is supporting STIG
The new PowerStoreOS 3.5 release now supports STIG mode. This mode applies configuration changes to the core of the product for the system to meet STIG requirements related to the operating system, embedded web server, internal databases, and various networking functions.
Enabling STIG mode
When a user wants to enable STIG mode, they need to run a REST API command against the PowerStore cluster or use the PowerStore command line interface (PowerStore CLI). The following is an example of the REST API command where <IP> is the IP of the PowerStore cluster.
curl -kv https://<IP>:443/api/rest/security_config/1?is_async=true --user admin:Password -X PATCH --data '{"is_stig_enabled":true}' -H "Content-Type:application/json“You can also enable STIG mode by issuing the following command in the PowerStore CLI:
pstcli -user admin -password Password -destination <IP> security_config -id 1 set -is_stig_enabled true -async
When the STIG enable process is kicked off, it takes about 45 minutes to enable STIG mode for a single appliance system. Larger clusters will take a little longer. You can confirm whether the process is running or completed by viewing the job status under Monitoring > Jobs in PowerStore Manager (Figure 1). In this example, notice that the ‘Modify security configuration’ job status is Completed.

Figure 1. STIG enablement job status
Enabling STIG is comparable to a PowerStoreOS upgrade, where the process is coordinated across the cluster, its nodes, and appliances. The process requires reboots across the nodes because of kernel changes and because additional Federal Information Processing Standard (FIPS) settings are enabled. FIPS in this case restricts the communication paths and the encryption used in those paths to be FIPS 140-2 compliant. By default, the drives in PowerStore are already leveraging FIPS encryption for storing data. STIG mode only enables the FIPS communication path part of the FIPS compliance, at the kernel level. This includes items such as data in flight and replication peers.
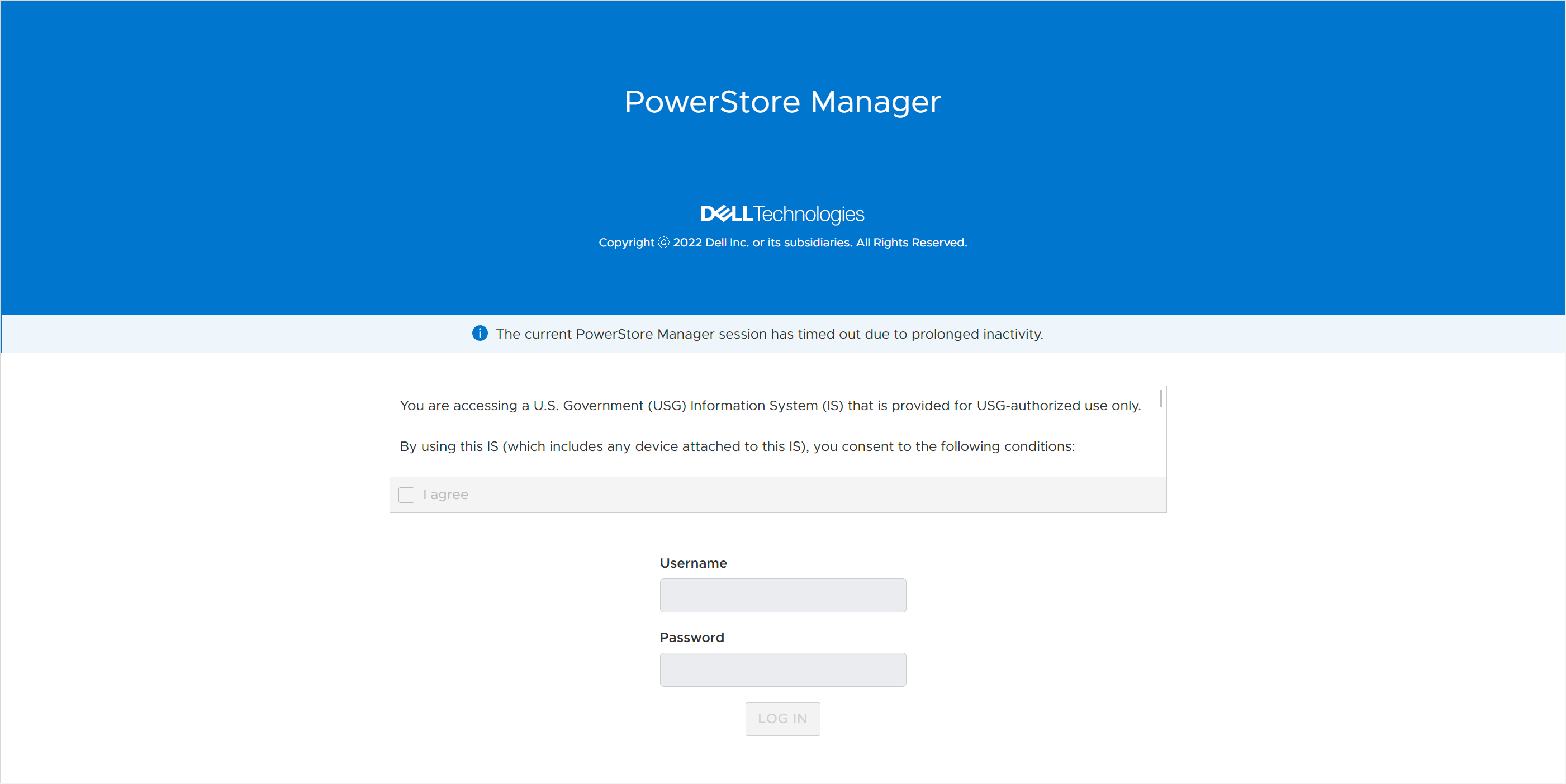
Disabling STIG mode, after it is enabled, is not supported. This is because a user enabling STIG mode is protecting top secret data, and we don’t want to enable anyone to disable this mode. The only way to remove or disable STIG mode from the PowerStore would be to perform a factory reset, which would delete all data. When STIG mode is enabled, PowerStore Manager displays a new login banner, as shown in Figure 2.
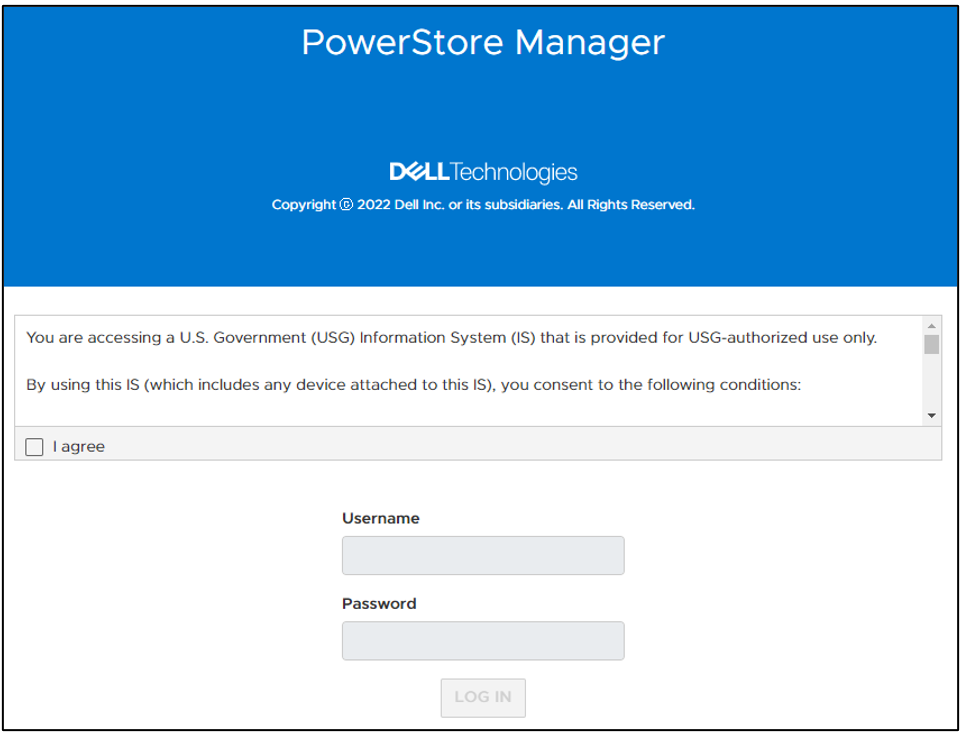
Figure 2. New STIG login banner
The user needs to scroll through this banner and click I agree to be able to input their credentials. They are then prompted to create a new password that meets STIG requirements and increases the security posture of the system. These requirements are outlined in the blue section of Figure 3.
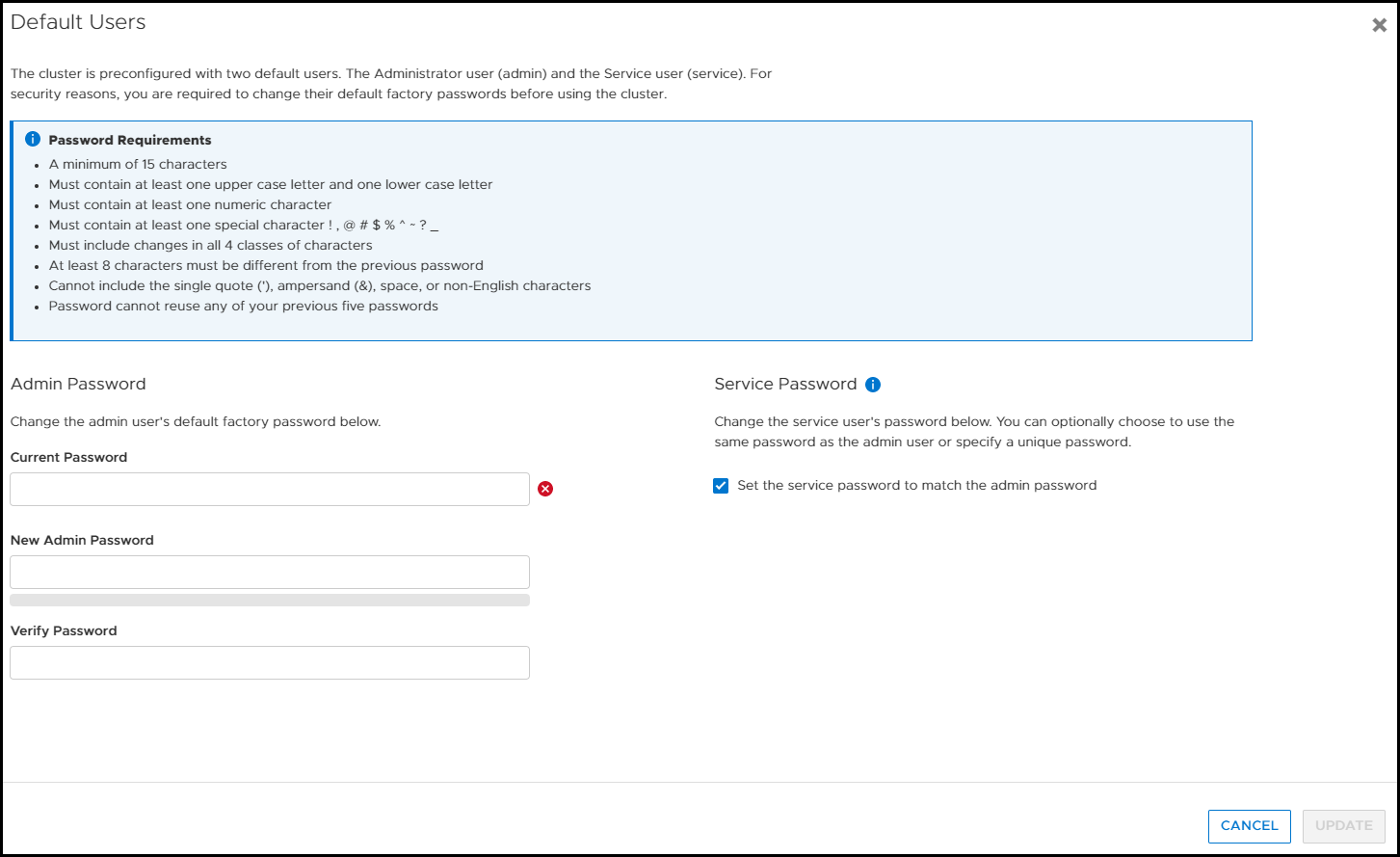
Figure 3. Update password to meet STIG requirements
Now, after logging in for the first time, you can notice a few of the changes from having enabled STIG mode in PowerStore Manager. If we look at the Login Message under Settings, the user can’t disable or change the login banner message. In Figure 4, notice that Enabled is grayed out and the login message is read-only. (If this system weren’t in STIG mode, users would be able to set their own login banner message, and enable or disable it as they see fit.)
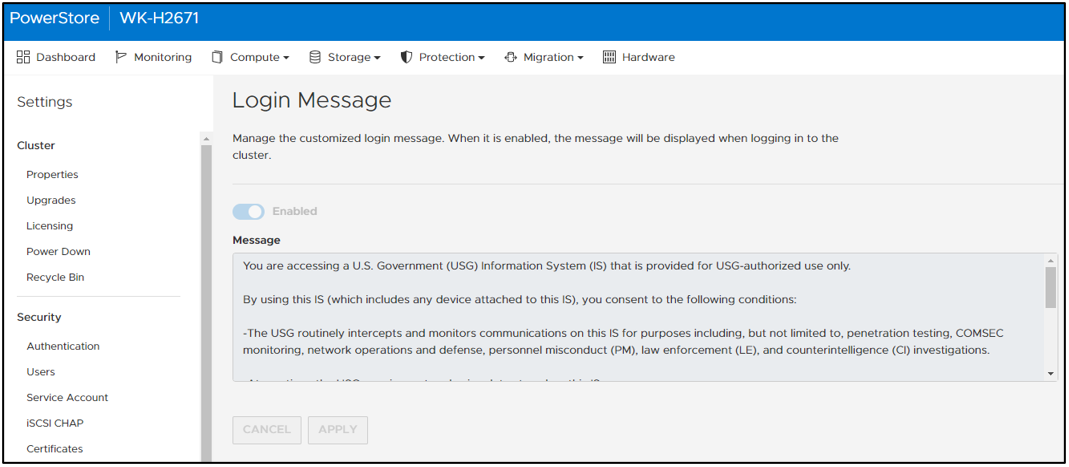
Figure 4. Login message can’t be changed or disabled
In PowerStore Manager, under Settings > Security > Session Timeout, only users with the Administrator or Security Administrator role can change the session timeout value. The options are 5, 10, and 20 minutes. Ten minutes is the default for STIG mode (Figure 5).
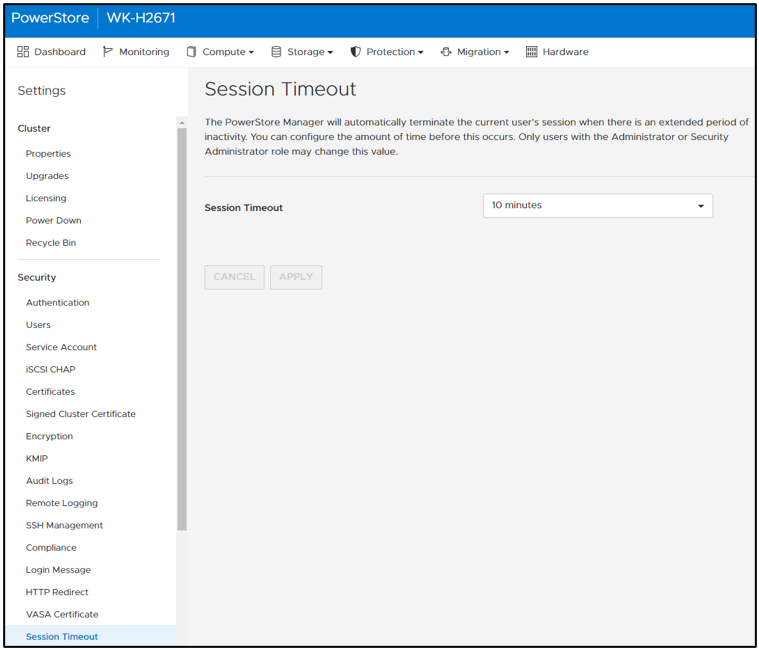
Figure 5. Default STIG mode session timeout
STIG mode also disables the ability for users to add PowerStore appliances to a STIG enabled cluster. Users who want to use multiple appliances must join them together before enabling STIG mode. This helps ensure a high security posture. On the Hardware page, notice that the ADD button is grayed out and that mousing over it displays a tooltip message (Figure 6).
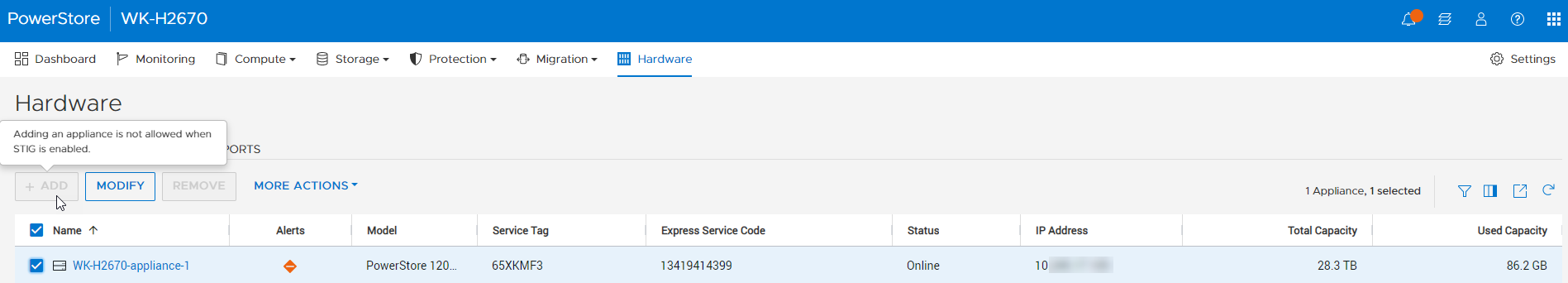
Figure 6. Add appliance disabled
After STIG mode is enabled, the Advanced Intrusion Detection Environment (AIDE) is also enabled on PowerStore. AIDE runs a scan once a day to look for file tampering of system files. This is another method that STIG uses to protect the PowerStore. Because PowerStore system files should only be changed during upgrades, it is easy for AIDE to detect tampering. If tampering is detected, PowerStore alerts appear, and the audit log is updated.
Conclusion
This blog provided you a quick glimpse into how easy it is to enable STIG mode on PowerStore to increase the system’s security posture and meet Federal compliance requirements. We went over some of the basic changes that STIG mode makes on the surface. Many more security items are changed underneath the covers of PowerStore to make it secure for Federal environments. Federal users will benefit from these security features and still be able to take advantage of PowerStore’s intuitive interface.
Resources
For more information about PowerStoreOS 3.5, and PowerStore in general, check out these resources:
- Dell Technologies PowerStore Info Hub
- Dell PowerStore: Cybersecurity White Paper
- Dell PowerStore: Blogs
Author: Andrew Sirpis


