Data Protection for PowerStore with PowerProtect DD Series Appliances
Download PDFTue, 09 May 2023 23:47:18 -0000
|Read Time: 0 minutes
Summary
Dell PowerStore is a revolutionary storage appliance that is designed for the data era. PowerStore is a data-centric, intelligent, and adaptable infrastructure solution that provides various ways to protect your data, locally and remotely. With PowerStore Manager, you can protect your data locally by creating snapshots (point-in-time copies) of volumes, volume groups, virtual machines, or file systems. You can also apply remote protection by replicating your data to a remote system or by mirroring the data using metro volumes for redundancy in the event of a disaster.
Native integration of Dell PowerProtect DD series appliances with PowerStore
Starting with PowerStoreOS (Operating System) version 3.5, a new remote backup solution is introduced which provides an additional method to protect your data in a PowerStore cluster. Dell PowerProtect DD series appliances can be added as a remote system to protect the resources (volumes and volume groups) on PowerStore. PowerStore can send backups directly to DD series appliances with no backup application required.
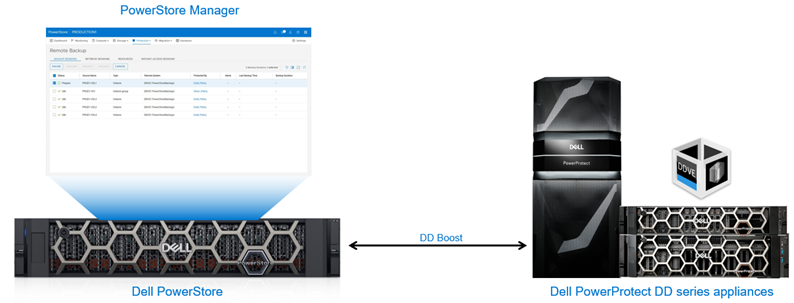
Figure 1. Remote backup – PowerStore to DD series appliances
DD series appliances enable organizations to protect, manage, and recover data at scale across their diverse environments. PowerStore supports backing up to a physical PowerProtect appliance or to PowerProtect DD Virtual Edition (DDVE). DDVE is supported either on-premise or within AWS. A single DD series appliance can be added to the same PowerStore cluster multiple times, provided that a different Storage Unit ID is used. This ability allows you to back up different resources to different locations within a single DD series appliance.
The key features are:
- Self-service remote backup with DD series appliances as the target remote system
- Backup and retrieve PowerStore block volumes and volume groups data with DD series
- Ability to Instantly access the remote snapshot residing on a DD series appliance
- Supports both physical and software-defined DD series appliances. Supports PowerProtect DD Virtual Edition with AWS cloud provider.
- PowerStore leverages DD Boost protocol to send data to DD series
- End to end data protection orchestration using PowerStore Manager
- Direct encrypted transfer from PowerStore to DD series
The key benefits are:
- Zero impact on hosts because backups run directly on PowerStore
- Incremental forever data protection strategy for PowerStore block volumes and volume groups
- Backup different resources to different locations within a single DD series appliance
- Ability to configure local and remote protection within a single protection policy with independent schedule and retention
- Replication between DD series appliances and to the cloud
Steps to protect resources on PowerStore with DD series
Figure 2 below explains the steps to protect resources (volumes and volume groups) on PowerStore with DD series appliances.
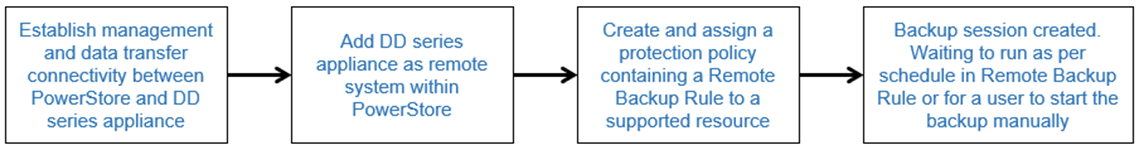
Figure 2. Steps to protect resources on PowerStore with DD series
Remote session operations
With PowerStore integration with DD series appliances, you can protect PowerStore volumes and volume groups directly to DD series appliances. With this ability you can perform remote session operations, such as backup, retrieve, and instant access. A remote session tracks each of these operations. Remote backup, retrieve, and instant access sessions go through various states that indicate the session’s progress and any possible issues.
Backup session
PowerStore utilizes backup sessions to create remote backups (snapshots) on the DD series appliances. When a protection policy containing a remote backup rule is assigned to a supported resource, a backup session is created. There is no manual way to configure a backup session without a protection policy. Only one backup rule can be added per protection policy.
A protection policy can be created to provide local and remote protection for PowerStore resources. Each protection policy for the same volume or volume group can include replication rule, remote backup rule, and snapshot rules, which are independent with schedule and retention.
When a backup is run, a snapshot of a volume or a volume group is created on the PowerProtect system. The created snapshots are crash-consistent and there is no application integration. A backup can be started manually by a user or automatically according to the schedule defined in the remote backup rule. Remote snapshots are created with an expiration time based on the remote backup rule associated with the resource.
The snapshots that are created manually by a user inherit the remote backup rule’s retention policy. Only the initial backup is full; subsequent backups are incremental. Backup session states when running a backup include ‘idle’, ‘prepare’, ‘in-progress’, ‘paused’, ‘cancelling’, and ‘failed’. Figure 3 depicts the high-level backup workflow.
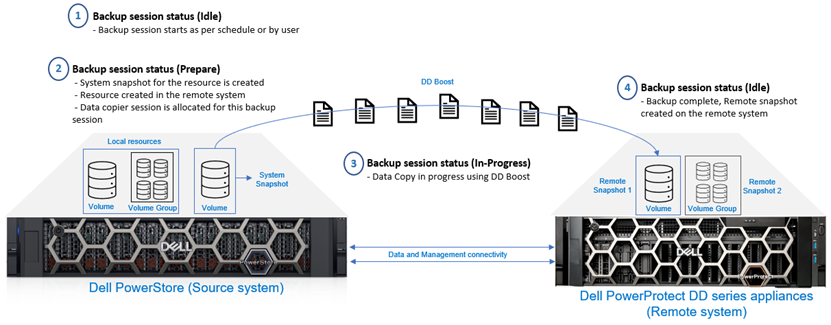
Figure 3. Backup session – High-level workflow
When performing incremental backups, only the unique data is traversed through the network to create a remote snapshot on the DD series appliances. The PowerStore snapshot differential feature, and DD series virtual synthetic operations, enable the implementation of an incremental forever data protection strategy. Only the changed blocks are sent to DD series and aggregated into the full consistent remote snapshot. The snapshot can be retrieved either incrementally or fully to the same PowerStore cluster or different cluster. When the backup is complete, users can view the list of all resources that have been backed up from the Resources page in the PowerStore Manager UI.
Retrieve session
When remote snapshots are created on the DD series appliances, backups can be retrieved to an existing or new PowerStore cluster. The retrieve option is used to copy a remote snapshot for a volume or volume group and save it as a local snapshot in the PowerStore cluster. This local snapshot will be set to no automatic deletion, where the user can update the expiration time or change it to a secure snapshot. Based on the use case, a differential or a full data copy is required. Figure 4 shows the high-level retrieve workflow.
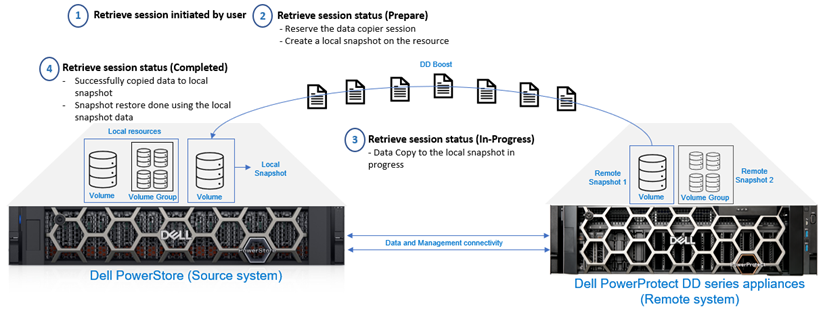
Figure 4. Retrieve session - High-level workflow
You may want to retrieve a remote snapshot for restoring the source resource or for creating a thin clone.
Retrieve a remote snapshot to the same PowerStore cluster:
- If the source volume or volume group of the retrieved backup still exists in the system, a local snapshot is created on the PowerStore cluster under the source resource. If possible, the retrieval is incremental - only the changes from the source volume are retrieved, which makes the retrieval process efficient.
- If the source volume or volume group of the retrieved backup no longer exists in the system, both a new resource and a local snapshot are created, and the new resource is restored with the snapshot data.
Retrieve a remote snapshot to a different PowerStore cluster:
- Because the source volume or volume group never existed on that cluster, both a new resource and a local snapshot are created. The new resource is restored with the snapshot data, returning the resource to the same state as the original.
Instant Access session
An instant access session allows a host to access a volume or volume group remote snapshot residing on a DD series appliance. From PowerStore Manager, you can create an instant access session to view the remote snapshot contents without having to retrieve them on the PowerStore cluster. Instant Access enables users to instantly access deleted, corrupted, or modified data within the remote snapshot. Only one instant access session is allowed per remote snapshot. When an instant access session is running, the PowerStore appliance does not perform backup and retrieve operations, and local resources are not protected until the instant access sessions are ended. Figure 5 shows the high-level instant access session workflow.
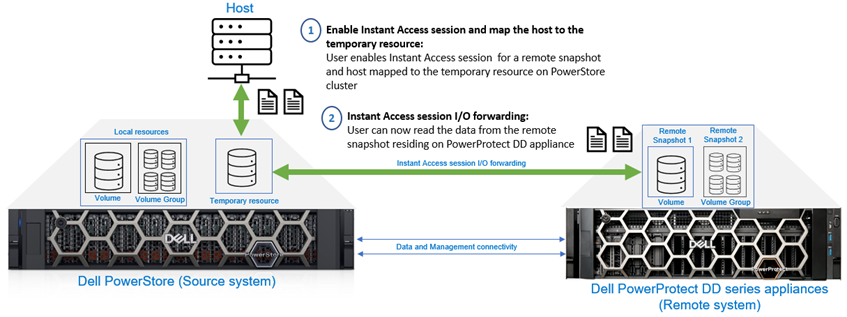
Figure 5. Instant Access session - High-level workflow
When enabling Instant Access for a volume snapshot, you can configure host access before enabling the session. For an instant access session on a volume group snapshot, the user must add the host access to the remote snapshot volumes after the session is created.
Note: Instant Access is supported for all block resources except VMware VMFS datastores. If access to data within a remote snapshot of a VMFS datastore is required, customers can still perform a retrieve operation on the remote snapshot and create and mount a thin clone.
Data protection is a mission-critical priority for any modernized technology, as organizations increasingly rely on innovative storage technology appliances such as PowerStore. This unique data protection solution, which integrates PowerStore with DD series appliances, ensures continuous availability of data in PowerStore to help organizations meet their SLAs.
References
Dell PowerStore:
- Dell PowerStore – Product website
- Dell PowerStore: Snapshots and Thin Clones
- Dell PowerStore: Info Hub
Dell PowerProtect DD series appliances:
- PowerProtect DD Series Appliances – Product website
- PowerProtect DD Series Appliances - Data Sheet
- PowerProtect DD Series Appliances - Spec Sheet
- Dell PowerProtect DD Series Appliances - Info Hub
Related Documents

Dell Technologies Data Protection for VMware Telco Cloud Platform
Fri, 28 Apr 2023 19:38:15 -0000
|Read Time: 0 minutes
Summary
Any modernized infrastructure undoubtedly requires a data protection strategy to avoid downtime, prevent data loss, and recover quickly in case of a disaster. Dell Technologies provides effective data protection solutions to help organizations solve a number of significant challenges. Dell PowerProtect Data Manager is one of the effective data protection solutions to protect VMware Telco Cloud Platform management/workload cluster components and application workloads.
Protecting VMware Telco Cloud Platform with Dell PowerProtect Data Manager
VMware Telco Cloud Platform is a modernization solution that deploys cloud-native and virtual network functions consistently, at web-scale speed, and without disruption. VMware Telco Cloud Platform is a cloud-native platform that empowers communication service providers (CSPs) to manage virtual network functions (VNFs) and Containerized Network Functions (CNFs) across the core, far edge radio access network (RAN), enterprise edge, and cloud with efficiency, scalability, and agility. Telco Cloud Platform provides the framework to deploy and manage VNFs and CNFs quickly and efficiently across distributed 5G networks. You can run VNFs and CNFs from dozens of vendors, on any cloud, with holistic visibility, orchestration, and operational consistency.
Telco Cloud Platform is powered by field-proven compute and networking coupled with VMware Telco Cloud Automation and a telco-grade Kubernetes distribution. VMware Telco Cloud Platform empowers CSPs to modernize their 5G networks so they can rapidly deploy and efficiently operate multi-vendor CNFs and VNFs. The compute and networking, which are supplied by VMware vSphere and VMware NSX-T Data Center, enable CSPs to run both CNFs and VNFs on consistent horizontal infrastructure. The Kubernetes distribution—VMware Tanzu Kubernetes Grid—is designed to support telecommunications use cases.
The essentials include:
- Software-defined data protection: Provides flexible data protection and compliance across applications and cloud-native IT environments
- Unique protection: Ensures availability of all your Telco Cloud Platform components and workloads without business disruption
- Autonomous operations: Automated discovery and protection of databases, virtual machines, file systems and Kubernetes containers
- Efficient protection: Protects data directly to Dell PowerProtect DD series appliances with optional replication to secure Cyber Recovery vault
- Self-service backup and restore: Enables data owners from their native interfaces
- PowerProtect Data Manager Appliance: Integrated data protection platform that combines Data Manager software in a single appliance
- OTEL Assurance: Validated by Dell’s Open Telco Ecosystem Lab
The key capabilities are:
- Protection for the entire VMware Telco Cloud Platform stack including your mission critical applications
- VM image and file-level protection for the management/workload clusters components or instances
- Namespace level/PVC protection for TKG cluster workloads
- VMware virtual machines in a reliable and efficient manner using the Transparent Snapshot Data Mover (TSDM) mechanism.
Dell PowerProtect Data Manager
PowerProtect Data Manager software is an enterprise solution that provides software-defined data protection, deduplication, operational agility, self-service, and IT governance. Data Manager gives you valuable insight into protected on-premises and in-cloud workloads, applications, file systems, and virtual machines (VMs). Plus, complete oversight and governance to ensure compliance.
Designed with operational simplicity and agility in mind, Data Manager enables the protection of traditional workloads including Oracle, Exchange, SQL, SAP HANA and file systems as well as Kubernetes containers and virtual environments. Restore data on-premises or in the cloud. Governance control ensures IT compliance, making even the strictest service level objectives obtainable.
PowerProtect Data Manager key features include the following:
- Software-defined data protection with integrated deduplication, replication, and reuse
- Data backup and recovery self-service operations from native applications that are combined with central IT governance
- Multicloud optimization with integrated Cloud Tiering
- SaaS-based monitoring and reporting
- Modern services-based architecture for ease of deployment, scaling, and updating
PowerProtect Data Manager for VMware Telco Cloud Platform
The PowerProtect Data Manager is a virtual appliance that can be deployed on or outside of VMware Telco Cloud Platform environment to protect the management and workload components and application workload data.
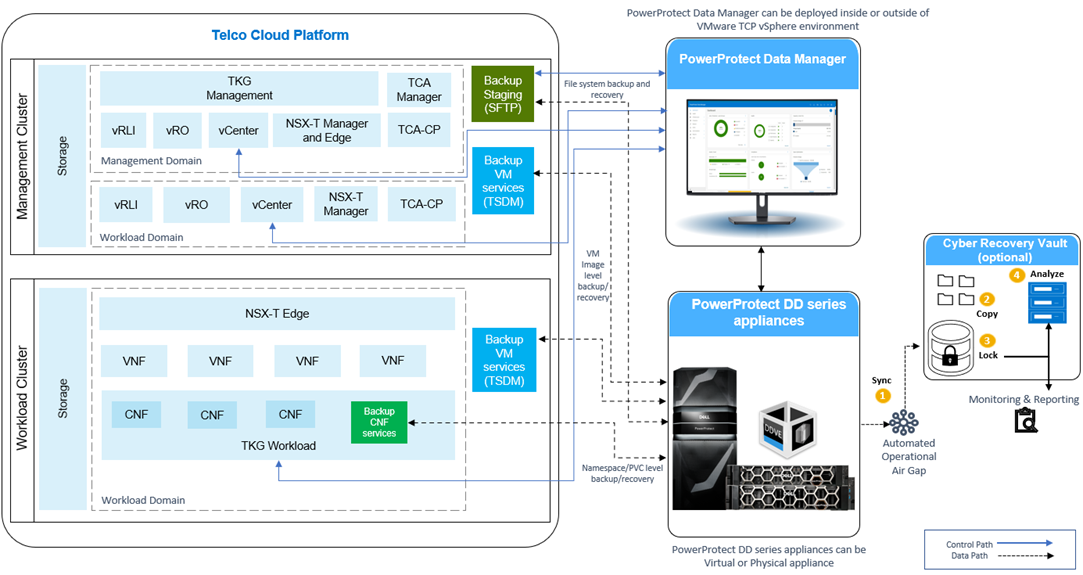
Figure 1. PowerProtect Data Manager protecting VMware Telco Cloud Platform
PowerProtect Data Manager is integrated with PowerProtect DD series appliances as the protection target where the backups are stored. A PowerProtect DD series appliance can be a physical or virtual appliance.
In addition to being deployable stand-alone, PowerProtect Data Manager is available as an integrated appliance, the Dell PowerProtect Data Manager appliance. The Data Manager Appliance offers an integrated data protection platform that combines protection storage with PowerProtect Data Manager software and cloud readiness – all in a single appliance. The Data Manager Appliance provides a unified user experience and automates discovery and protection of databases, VMs, file systems, and Kubernetes containers.
Optionally, data can be replicated from a production DD series appliance to another DD series appliance or to a DD series appliance in Cyber Recovery vault using the Dell PowerProtect Cyber Recovery solution. PowerProtect Cyber Recovery provides proven, modern, and intelligent protection to isolate critical data, identify suspicious activity, and accelerate data recovery, allowing you to resume normal business operations quickly.
PowerProtect Cyber Recovery key features include the following:
- Operational air gap with data isolation and immutability
- CyberSense analytics and Machine Learning monitor data integrity
- Accelerate cyber and ransomware attack data recovery
Data Protection methods for VMware Telco Cloud Platform infrastructure components and application workloads
For VMware Telco Cloud Platform management domain (Management workload cluster), the following table shows the core components and the backup methods used.
TCP component | Backup/Restore method |
Management vCenter server | File level |
NSX-T Manager nodes | File level |
vRealize Log Insight | VM Image level |
vRealize Operations Manager | VM Image level |
vRealize Orchestrator | VM Image level |
Telco Cloud Automation Manager | File level |
Telco Cloud Automation Control plane | File level |
Tanzu Kubernetes Grid Management cluster | VM Image level |
For VMware Telco Cloud Platform workload domain (Management workload cluster), the following table shows the core components and the backup/restore methods used.
TCP component | Backup/Restore method |
Workload vCenter server | File level |
NSX-T Manager nodes | File level |
vRealize Log Insight | VM Image level |
vRealize Orchestrator | VM Image level |
Telco Cloud Automation Control plane | File level |
For VMware Telco Cloud Platform general purpose VMs (Management workload cluster), the following table shows the core components and the backup/restore methods used.
Other component (examples) | Backup/Restore method |
DNS, NTP, DHCP, Web servers, database, filesystem | VM Image level /File level/database |
Harbor registry, other registry | VM Image level or File level |
Customized applications on VM’s/Tanzu Kubernetes Grid | Namespace/PVC or Image level |
For the VMware Telco Cloud Platform compute workload domain (Workload cluster), the following table shows the core components and the backup/restore methods used.
TCP component | Backup/Restore method |
Virtual Network Functions (VNFs) | VM level (TSDM) or File level or File/DB level |
Tanzu Kubernetes Grid Workload cluster (CNFs) | Namespace and PVC level with application consistency |
The following table shows the backup system components protection.
Backup component | Backup/Restore method |
Backup Staging VM | File level |
Backup Server (PowerProtect Data Manager) | PowerProtect Data Manager disaster recovery process |
PowerProtect DD series appliances | Replication to another DD series appliance or DD series appliance in Cyber Recovery vault |
Protecting management/workload cluster components and VNFs using image-level or file system backup
The management and workload cluster vCenter servers are integrated with Data Manager and discovered as an asset source after being registered with PowerProtect Data Manager. PowerProtect Data Manager discovers the management workload domain components and application workload (VNFs) as virtual-machine assets for protection. Data Manager can prot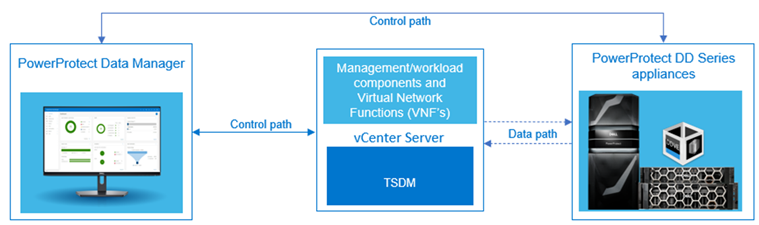 ect VMware virtual machines in a reliable and efficient manner using the Transparent Snapshot Data Mover (TSDM) mechanism. Transparent Snapshots simplifies VM image backups for near-zero impact to your VMs or VM resources – and it works with any VMware supported storage. For more details about TSDM, see the technical white paper PowerProtect Data Manager: VMware Virtual Machine Protection Using Transparent Snapshots.
ect VMware virtual machines in a reliable and efficient manner using the Transparent Snapshot Data Mover (TSDM) mechanism. Transparent Snapshots simplifies VM image backups for near-zero impact to your VMs or VM resources – and it works with any VMware supported storage. For more details about TSDM, see the technical white paper PowerProtect Data Manager: VMware Virtual Machine Protection Using Transparent Snapshots.
Protecting TKG cluster workloads (CNFs)
With PowerProtect Data Manager, the Tanzu Kubernetes Grid cluster workloads, such as namespaces and Persistent Volume Claims (PVCs) on Telco Cloud Platform, are protected efficiently using the Velero component and cProxy pod (data mover). When the Tanzu Kubernetes Grid cluster is added as an asset source in PowerProtect Data M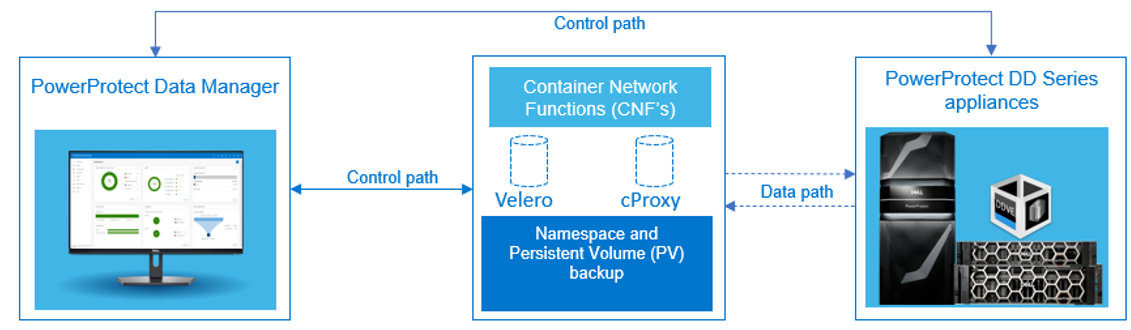 anager and discovery is complete, the associated namespaces are available as assets for protection. The PowerProtect Data Manager supports agentless, application-consistent backups of database applications that reside in Kubernetes pods. The PowerProtect Data Manager provides a standardized way to quiesce a supported database, back up the data from that database, and then return the database to operation.
anager and discovery is complete, the associated namespaces are available as assets for protection. The PowerProtect Data Manager supports agentless, application-consistent backups of database applications that reside in Kubernetes pods. The PowerProtect Data Manager provides a standardized way to quiesce a supported database, back up the data from that database, and then return the database to operation.
Protecting the SFTP server (Staging VM)
For file level-based backup of VMware Telco Cloud Platform components, the respective VMware Telco Cloud Platform management and compute workload component dump is created and sent to an SFTP target (staging VM). Later, the SFTP target (staging VM) is protected using a file system agent-based backup method with PowerProtect Data Manager.
Dell Technologies enables you to simplify the experience of adopting modern data protection. PowerProtect Data 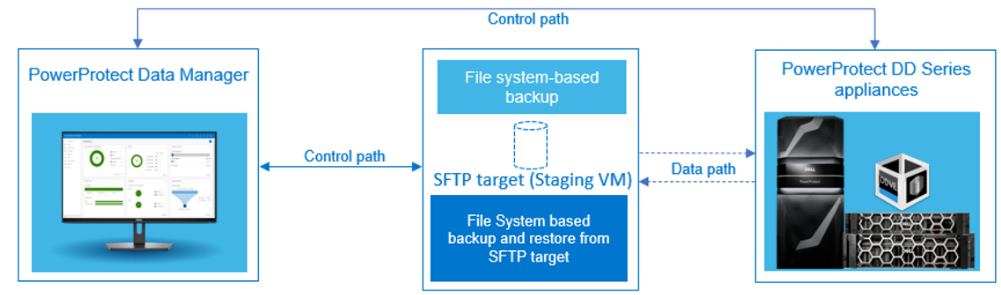 Manager enables users to protect, manage, and recover data in on-premises, virtualized, and cloud deployments. This platform provides centralized governance that helps mitigate risk and assures compliance of SLAs and SLOs through simple protection workflows. PowerProtect Data Manager is one of the effective solutions to protect VMware vSphere components and application workload data on VMware Telco Cloud Platform.
Manager enables users to protect, manage, and recover data in on-premises, virtualized, and cloud deployments. This platform provides centralized governance that helps mitigate risk and assures compliance of SLAs and SLOs through simple protection workflows. PowerProtect Data Manager is one of the effective solutions to protect VMware vSphere components and application workload data on VMware Telco Cloud Platform.
Note: This document focuses on protecting the CNFs and VNFs on VMware Telco Cloud Platform infrastructure, however it can also be used to protect other VNFs and CNFs as well as VMware components outside of the VMware Telco Cloud Platform infrastructure.
Assurance provided by OTEL
The Open Telecom Ecosystem Lab (OTEL) accelerates and simplifies the creation of an open, modern telecom ecosystem. By validating complex technical solutions through our virtual and physical OTEL labs, we’re helping partners reduce the costs and risk of deployment while opening new 5G and cloud native opportunities.
OTEL offerings driving the open 5G opportunity:
- Partner/Industry Certification -- Self-Certification that enables independent software vendors to de-risk deployments and make the ecosystem consumable. Also, Joint-Certification improves outcomes and business value by verifying ecosystem partner compatibility.
- Solution Validation -- End-to-end CSP and telecom partner solution validation, life-cycle management, and enhanced service support.
- Proof of Concept -- Work with partners and CSPs to develop early evaluation and sand box development to drive ecosystem adoption.
- Demonstration and Training -- Showcase new capabilities and support technical training activities.
To learn more about our Open Telecommunication Ecosystem Lab please see additional resources at: OTEL (Open Telecom Ecosystem Labs).
Technical References
The following Dell Technologies resources provide additional information about PowerProtect Data Manager:
The following VMware resources provide additional information about VMware Telco Cloud Platform:
The following Dell Technologies resources provide additional information about OTEL and VMware Telco Cloud Platform:

PowerEdge MX and NVMe/TCP Storage
Fri, 28 Jul 2023 17:46:12 -0000
|Read Time: 0 minutes
Introduction
Dell PowerEdge MX was introduced in 2018, and since then Dell Technologies has continued to add new features and functionality to the platform. One such area is the support of NVMe over TCP (NVMe/TCP). As new applications such as Artificial Intelligence and Machine Learning (AI/ML) and the continuing consolidation of virtual workloads demand greater storage performance, NVMe/TCP brings performance improvements over protocols such as iSCSI at a lower price point than compatible Fibre Channel (FC) infrastructure (see Transport Performance Comparison). Incorporating this protocol into storage solution architecture brings new opportunities for higher performance using Ethernet and retiring FC infrastructure.
This tech note describes the architecture required to build PowerEdge MX solutions that use NVMe/TCP, simplifying connectivity to external storage arrays by reducing the physical network and streamlining protocols. It describes the value proposition and technology building blocks and provides high-level configuration examples using VMware.
Technology architecture
The four components of a Dell NVMe/TCP solution are a compute layer with the appropriate host network interface enabled for NVMe/TCP, high-performance 25 GbE or 100 GbE switching network, storage array supporting NVMe/TCP, and, finally, a management application to configure and control access. Dell offers several end-to-end PowerEdge MX base storage solutions that support NVMe/TCP on either 25 GbE or 100 GbE networking. The solutions include PowerEdge servers, PowerSwitch networking, and several Dell storage array products with Dell SmartFabric Storage Software for zoning management.
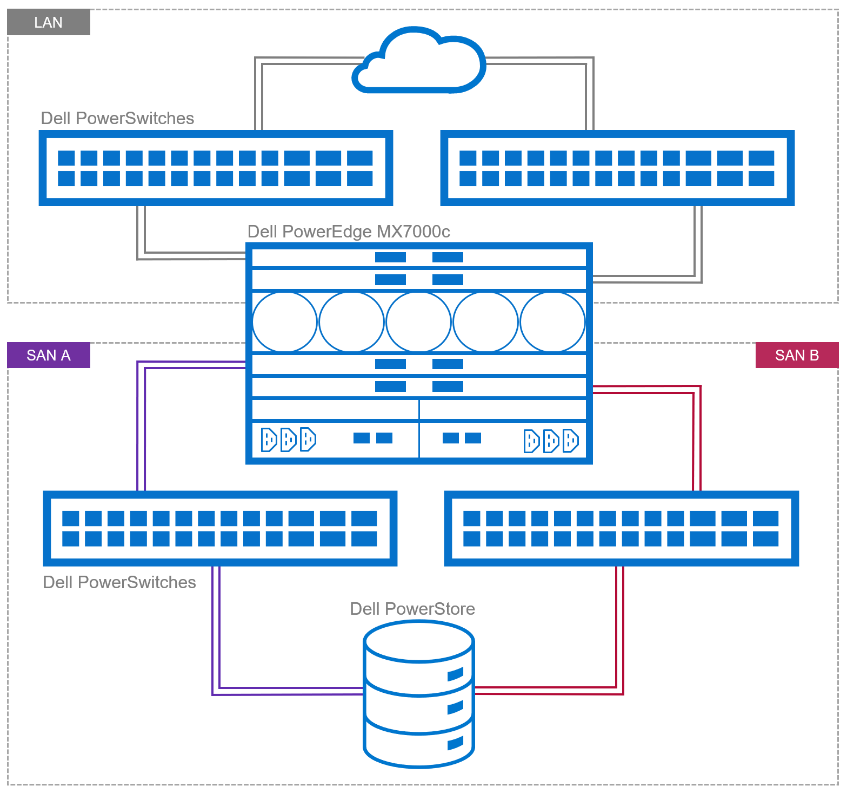
Figure 1. Example of NVMe/TPC SAN and LAN architecture
Dell continues to validate and expand the matrix of supported hardware and software. The document, NVMe/TCP Host/Storage Interoperability Simple Support Matrix, is available on E-Lab Navigator and updated on a regular basis. It includes details about tested configurations and supported storage arrays, such as PowerStore and PowerMax.
Table 1. Example of supported configurations extracted from NVMe/TCP Host/Storage Interoperability Simple Support Matrix
Server | NIC | MX Firmware/ | Storage Array | Boot From San | OS |
MX750c MX760c | Broadcom 57508 dual 100 GbE Mezz card | MX baseline 2.10.00 | PowerMax 2500/8500 OS 10.0.0 / 10.0.1 | No | VMware ESXi 8.0 |
MX760c
| Broadcom 57504 dual 25 GbE Mezz card | MX baseline 2.00.00 | PowerMax 2500/8500 OS 10.0.0 / 10.0.1 | No | VMware ESXi 8.0 |
MX750c MX760c | Broadcom 57508 dual 100 GbE Mezz card | MX baseline 2.10.00 | PowerStore 500T/1000T 3000T/7000T 9000T | No | VMware ESXi 8.0 |
MX760c | Broadcom 57504 dual 25 GbE Mezz card | MX baseline 2.00.00 | PowerStore 500T/1000T 3000T/7000T 9000T | No | VMware ESXi 8.0 |
These are the minimum supported versions. See the Dell support site for the latest approved version.
PowerEdge MX
The 100 GbE mezzanine card was added to the PowerEdge MX compute sled connectivity portfolio in April 2023. The PowerEdge MX offers a choice of both 25 GbE and 100 GbE at the compute sled, with a selection of various networking I/O modules.
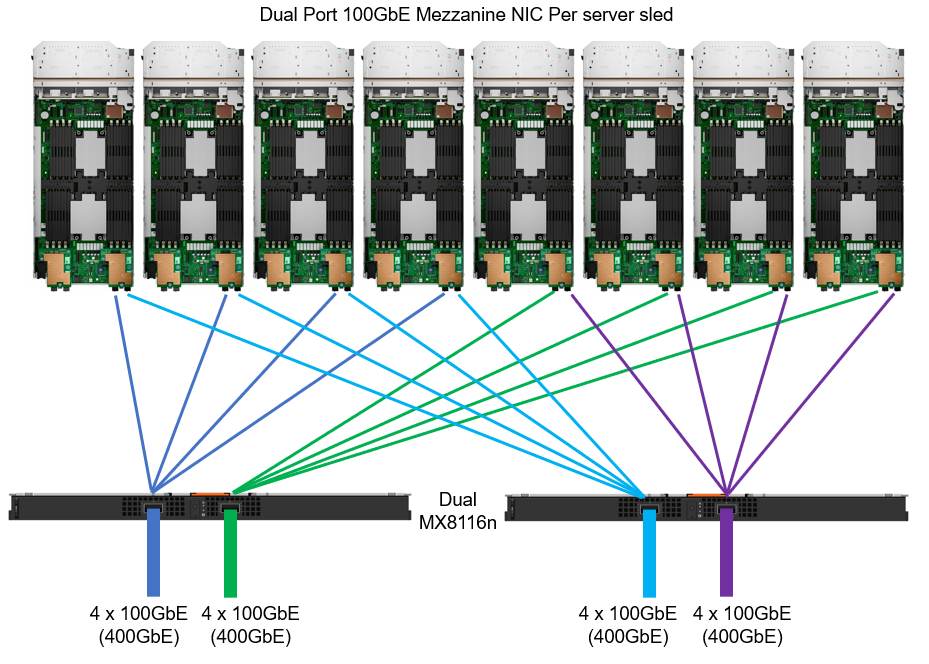
Figure 2. MX chassis 100 GbE architecture
IP switch fabric
NVMe/TCP traffic uses traditional TCP/IP protocols, meaning the network design can be quite flexible. Often, existing networks can be used. The best-practice topology dedicates switches and device ports for storage area network (SAN) traffic only. In Figure 1, local area network (LAN) traffic connects to a pair of switches northbound from Fabric A in the MX chassis. Fabric B connects to dedicated, air-gapped switches to reach the storage array.
For more details about NVMe/TCP networking, see the SmartFabric Storage Software Deployment Guide.
For 25 GbE connectivity, there are a number of options, starting with dual- or quad-port mezzanine cards, with a selection of pass-through or fabric expansion modules or full switches integrated into the PowerEdge MX chassis. For scalability, a pair of external top-of-rack (ToR) switches are implemented for interfacing with the storage array.
For 100 GbE end-to-end connectivity, the MX8116n Fabric Expander Module is a required chassis component for the PowerEdge MX platform. A Z9432F-ON ToR switch is then required for MX8116n connectivity. The Z9432F supports 32 ports x 400 GbE (or 64 ports x 200 GbE using breakouts or 128 ports x multiple interface speeds from 10 GbE to 400 GbE ports using breakouts). So how does the Z9432F-ON work in the MX 100 GbE solution? The 400 GbE ports on the MX8116n connect to ports on the PowerSwitch. The solution scales the network fabric to 14 chassis with 112 PowerEdge MX compute sleds. Each MX7000 chassis uses only 4 x 400 GbE cables, dramatically reducing and simplifying cabling (see Figure 2).
Storage
Taking Dell PowerFlex as an example, NVMe/TCP is supported in the following manner: PowerFlex storage nodes are joined in storage pools. Typically, similar disk types are used within a pool (for example, a pool of NVMe drives or a pool of SAS drives). Volumes are then carved out from that pool, meaning the blocks/chunks/pages of that volume are distributed across every disk in the pool. Regardless of the underlying technology, these volumes can be assigned an NVMe/TCP storage protocol interface ready to be accessed across the network from the hosts accordingly.
Let’s look at another example—this one for Dell PowerStore, which is an all-NVMe flash storage array. A volume can be created and then presented using NVMe/TCP across the network. This allows the performance of the NVMe devices to be shared across the network, offering a truly end-to-end NVMe experience.
NVMe/TCP zoning
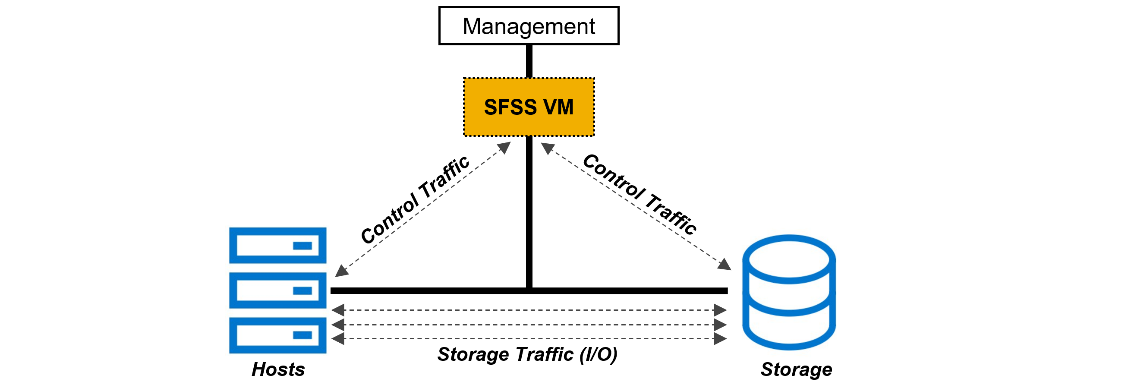
An advantage and challenge of Ethernet-based NVMe/TCP is that it scales out from tens to hundreds to thousands of fabric endpoints. This quickly becomes arduous, error prone, and highly cost inefficient. FC excels at automatic endpoint discovery and registration. For NVMe/TCP to be a viable alternative to FC in the data center, it must provide users with FC-like endpoint discovery and registration, and FC-like zoning capabilities. Dell SmartFabric Storage Software (SFSS) is designed to help automate the discovery and registration of hosts and storage arrays using NVMe/TCP.
Figure 3. Dell SmartFabric Storage Software (SFSS)
Dell SFSS is a centralized discovery controller (CDC). It discovers, registers, and zones the devices on the NVMe/TCP IP SAN. Customers can control connectivity from a single, centralized location instead of having to configure each host and storage array manually.
VMware support
In October 2021, VMware announced support of the NVMe/TCP storage protocol with the release of VMware vSphere 7 Update 3. VMware has since included support in vSphere 8. It is a simple task to configure an ESXi host for NVMe/TCP. Just select the adapter from the standard list of storage adapters for each required host. Once the adapter is selected in vSphere, the new volume appears automatically as a namespace, assuming access has been granted through SFSS. Any storage volume accessed through NVMe/TCP can be used to create a standard VMFS datastore.
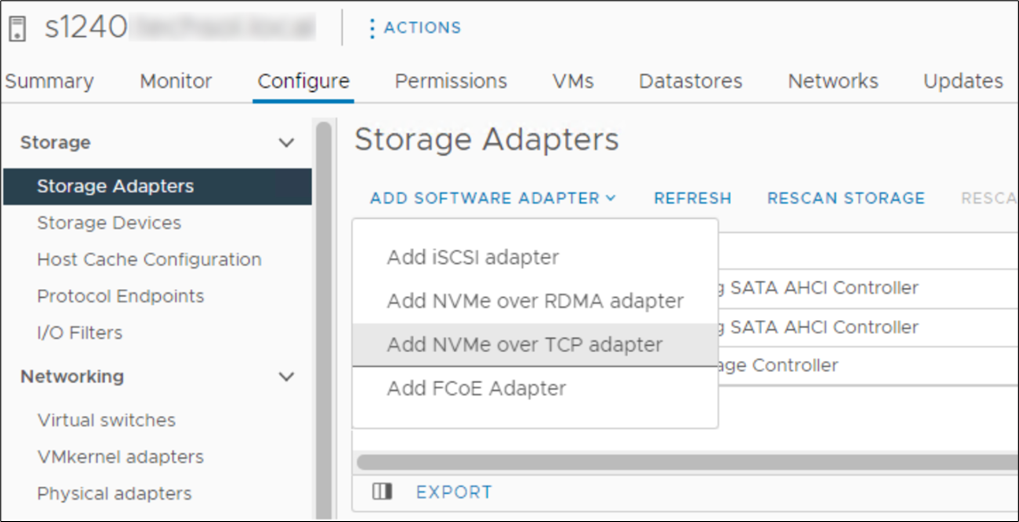 Figure 4. Adding NVMe/TCP adapter in vSphere
Figure 4. Adding NVMe/TCP adapter in vSphere
Conclusion
NVMe/TCP is now a practical alternative to iSCSI and a replacement to older FC infrastructure. With NVMe/TCP's ability to provide higher IOPS at a lower latency while consuming less CPU than iSCSI, and offering similar performance to FC, NVMe/TCP can provide an immediate benefit. In addition, for customers who have cost constraints or skill shortages, moving from FC to NVMe/TCP is a viable choice. Dell SmartFabric Storage Software is the key component that makes scale-out NVMe/TCP infrastructures manageable. SFSS enables an FC-like user experience for NVMe/TCP. Hosts and storage subsystems can automatically discover and register with SFSS so that a user can create zones and zone groups in a familiar FC-like manner. Using Dell PowerEdge MX as the server compute element dramatically simplifies physical networking so customers can more quickly realize NVMe/TCP storage benefits.
References
- SmartFabric Storage Software Deployment Guide
- PowerEdge MX I/O Guide
- SmartFabric Storage Software: Create a Centralized Discovery Controller for NVMe/TCP (video)
- NVMe/TCP Host/Storage Interoperability (E-Lab Support Matrix)
- Dell Technologies Simple Support Matrices (storage E-Lab Support Matrices portal)