

Building on VxRail HCI System Software: the advantages of multi-cluster active management capabilities
Wed, 24 Apr 2024 11:57:53 -0000
|Read Time: 0 minutes
The signs of autumn are all around us, from the total takeover of pumpkin-spiced everything to the beautiful fall foliage worthy of Bob Ross’s inspiration. Like the amount of change autumn brings forth, so too does the latest release of VxRail ACE, or should I preface that with ‘formerly known as’? I’ll get to that explanation shortly.
This release introduces multi-cluster update functionality that will further streamline the lifecycle management (LCM) of your VxRail clusters at scale. With this active management feature comes a new licensing structure and role-based access control to enable the active management of your clusters.
Formerly known as VxRail ACE
The colors of the leaves are changing and so is the VxRail ACE name. The brand name VxRail ACE (Analytical Consulting Engine), will no longer be used as of this release. While it had a catchy name and was easy to say, there are two reasons for this change. First, Analytical Consulting Engine no longer describes the full value or how we intend to expand the features in the future. It has grown beyond the analytics and monitoring capabilities of what was originally introduced in VxRail ACE a year ago and now includes several valuable LCM operations that greatly expand its scope. Secondly, VxRail ACE has always been part of the VxRail HCI System Software offering. Describing the functionality as part of the overall value of VxRail HCI System Software, instead of having its own name, simplifies the message of VxRail’s value differentiation.
Going forward, the capability set (that is, analytics, monitoring, and LCM operations) will be referred to as SaaS multi-cluster management -- a more accurate description. The web portal is now referred to as MyVxRail.
Cluster updates
Cluster updates is the first active management feature offered by SaaS multi-cluster management. It builds on the existing LCM operational tools for planning cluster updates: on-demand pre-update health checks (LCM pre-check) and update bundle downloads and staging. Now you can initiate updates of your VxRail clusters at scale from MyVxRail. The benefits of cluster updates on MyVxRail tie closely with existing LCM operations. During the planning phase, you can run LCM pre-checks of the clusters you want to update. This informs you if a cluster is ready for an update and pinpoints areas for remediation for clusters that are not ready. From there, you can schedule your maintenance window to perform a cluster update and, from MyVxRail, initiate the download and staging of the VxRail update bundle onto those clusters. With this release, you can now execute cluster updates for those clusters. Now that’s operational efficiency!
When setting a cluster update operation, you have the benefit of two pieces of information – a time estimate for the update and the change data. The update time estimate will help you determine the length of the maintenance window. The estimate is generated by telemetry gathered about the install base to provide more accurate information. The change data is the list of the components that require an update to reach the target VxRail version.
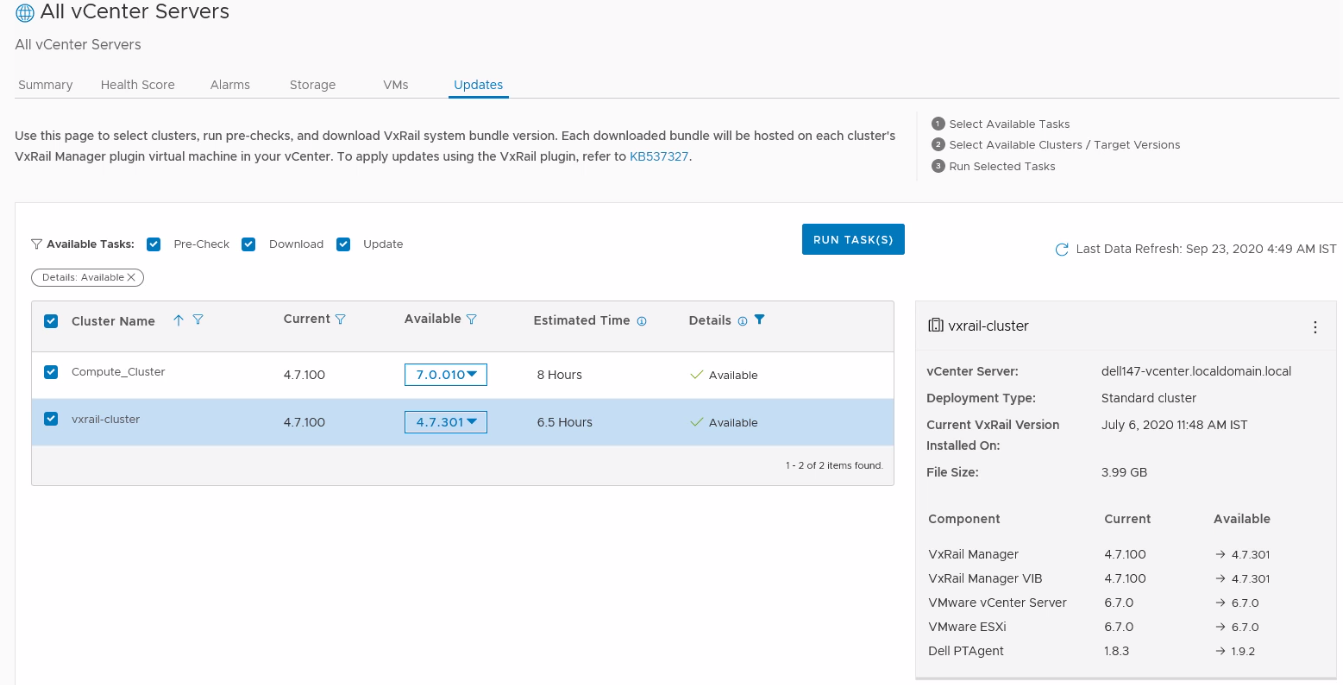
Figure 1 MyVxRail Updates tab
Role-based access control
Active management requires role-based access control so that you can provide permissions to the appropriate individuals to perform configuration changes to your VxRail clusters. You don’t want anyone with access to MyVxRail to perform cluster updates on the clusters. SaaS multi-cluster management leverages vCenter Access Control for role-based access. From MyVxRail, you will be able to register MyVxRail with the vCenter Servers that are managing your VxRail clusters. The registration process will give VxRail privileges to vCenter Server to build roles with specific SaaS multi-cluster management capabilities.
MyVxRail registers the following privileges on vCenter:
- Download software bundle: downloads and stages the VxRail software bundle onto the cluster
- Execute health check: performs an on-demand pre-update health check on the cluster
- Execute cluster update: initiates the cluster update operation on the clusters
- Manage update credentials: modifies the VxRail infrastructure credentials used for active management
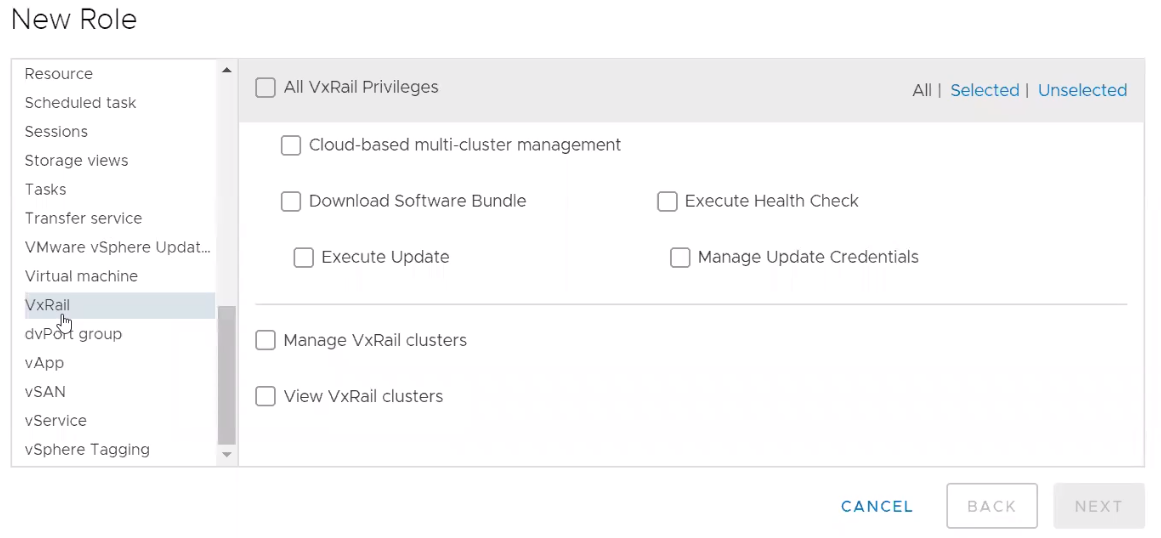
Figure 2 VxRail privileges for vCenter access control
VxRail Infrastructure Credentials
We’ve done more to make it easier to perform cluster updates at scale. Typically, when you’re performing a single cluster update, you have to enter the root account credentials for vCenter Server, Platform Services Controller, and VxRail Manager. That’s the same process when performing it from VxRail Manager. But that process can get tedious when you have multiple clusters to update.
VxRail Infrastructure Credentials can store those credentials so you can enter them once, at the initial setup of active management, and not have to do it again as you perform a multi-cluster update. MyVxRail can read the stored credentials that are saved on each individual cluster for security.
Big time saver! But how secure is it? More secure than hiding Halloween candy from children. For a user to perform cluster update, the administrator needs to add the ‘execute cluster update’ privilege to the role assigned to that user. Root credentials can only be managed by users assigned with a role that has the ‘manage update credentials’ privilege.
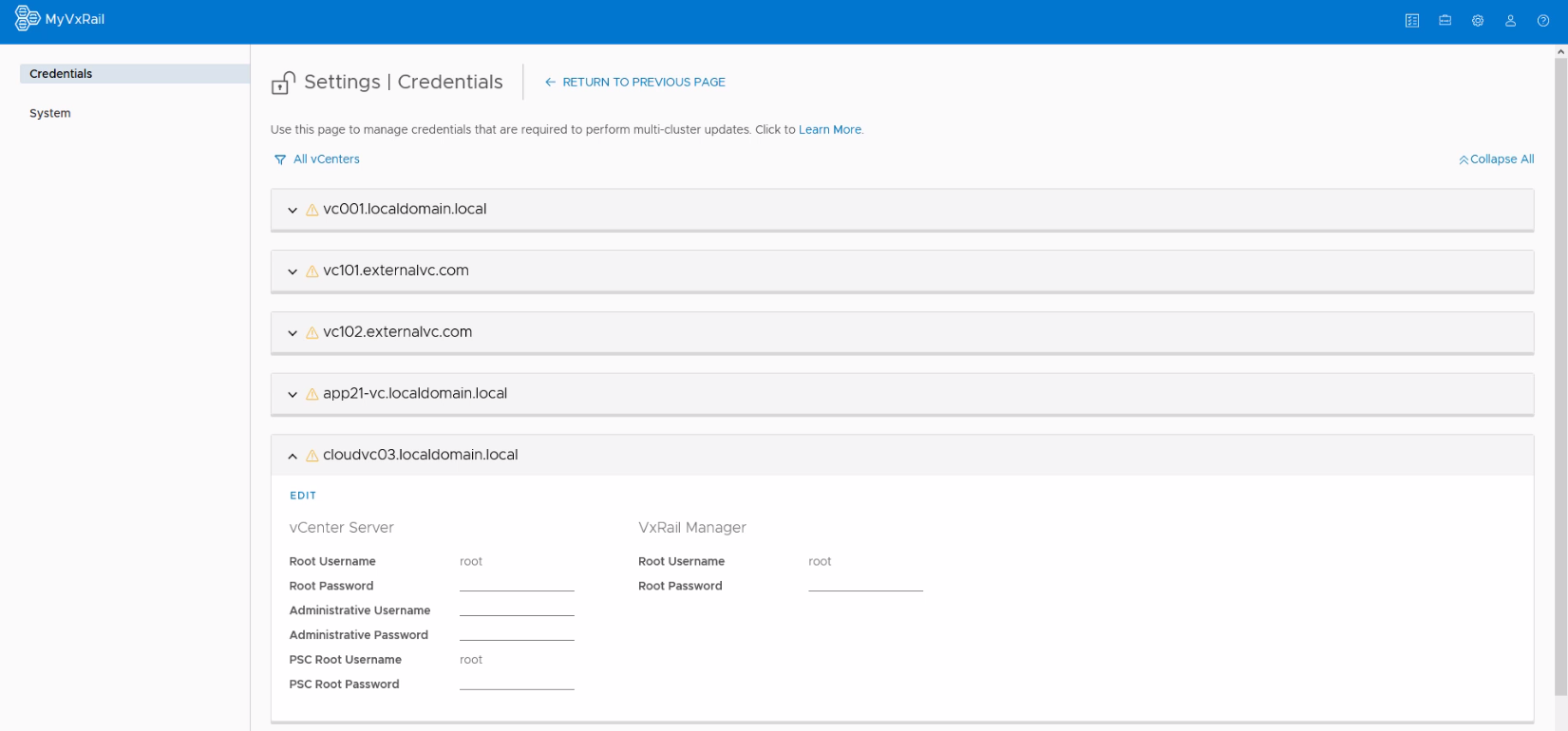
Figure 3 MyVxRail credentials manager
Licensing
The last topic is licensing. While all the capabilities you have been using on MyVxRail come with the purchase of the VxRail HCI System Software license, multi-cluster update is different. This feature requires a fee-based add-on software license called ‘SaaS active multi-cluster management for VxRail HCI System Software’. All VxRail nodes come with VxRail HCI System Software and you have access to MyVxRail and SaaS multi-cluster management features, except for cluster update. For you to perform an update of a cluster on MyVxRail, all nodes in the clusters must have the add-on software license.
Conclusion
That is a lot to consume for one release. Hopefully, unlike your Thanksgiving meal, you can stay awake for the ending. While the brand name VxRail ACE is no more, we’re continuing to deliver value-adding capabilities. Multi-cluster update is a great feature to further your use of MyVxRail for LCM of your VxRail clusters. With role-based access and VxRail infrastructure credentials, rest assured you’re benefitting from multi-cluster update without sacrificing security.
To learn more about these features, check out the VxRail techbook and the interactive demo for SaaS multi-cluster management.
Daniel Chiu, VxRail Technical Marketing
Related Blog Posts

HCI Security Simplified: Protecting Dell VxRail with VMware NSX Security
Fri, 08 Apr 2022 18:14:37 -0000
|Read Time: 0 minutes
The challenge
Cybersecurity and protection against ransomware attacks are among the top priorities for most customers who have successfully implemented or are going through a digital transformation. According to the ESG’s 2022 Technology Spending Intentions Survey:
- 69 percent of respondents shared that their spending on cybersecurity will increase in 2022 (#1).
- 48 percent of respondents believe their IT organizations have a problematic shortage of existing skills in this area (#1).
- 38 percent of respondents believe that strengthening cybersecurity will drive the majority of technology spending in their organization in the next 12 months (#1).
The data clearly shows that this area is one of the top concerns for our customers today. They need solutions that significantly simplify increasing cybersecurity activities due to a perceived skills shortage.
It is worth reiterating the critical role that networking plays within Hyperconverged Infrastructure (HCI). In contrast to legacy three-tier architectures, which typically have a dedicated storage network and storage, HCI architecture is more integrated and simplified. Its design lets you share the same network infrastructure for workload-related traffic and intercluster communication with the software-defined storage. The accessibility of the running workloads (from the external network) depends on the reliability of this network infrastructure, and on setting it up properly. The proper setup also impacts the performance and availability of the storage and, as a result, the whole HCI system. To prevent human error, it is best to employ automated solutions to enforce configuration best practices.
VxRail as an HCI system supports VMware NSX, which provides tremendous value for increasing cybersecurity in the data center, with features like microsegmentation and AI-based behavioral analysis and prevention of threats. Although NSX is fully validated with VxRail as a part of VMware Cloud Foundation (VCF) on VxRail platform, setting it outside of VCF requires strong networking skills. The comprehensive capabilities of this network virtualization platform might be overwhelming for VMware vSphere administrators who are not networking experts. What if you only want to consume the security features? This scenario might present a common challenge, especially for customers who are deploying small VxRail environments with few nodes and do not require full VCF on the VxRail stack.
The great news is that VMware recognized these customer challenges and now offers a simplified method to deploy NSX for security use cases. This method fits the improved operational experience our customers are used to with VxRail. This experience is possible with a new VMware vCenter Plug-in for NSX, which we introduce in this blog.
NSX and security
NSX is a comprehensive virtualization platform that provides advanced networking and security capabilities that are entirely decoupled from the physical infrastructure. Implementing networking and security in software, distributed across the hosts responsible for running virtual workloads, provides significant benefits:
- Flexibility—Total flexibility for positioning workloads in the data center enables optimal use of compute resources (a key aspect of virtualization).
- Optimal consumption of CPU resources —Advanced NSX features only consume CPU from the hosts when they are used. This consumption leads to lower cost and simplified provisioning when compared to running the features on dedicated appliances.
- High performance—NSX features are performed in VMware ESXi kernel space, a unique capability on vSphere.
The networking benefits are evident for large deployments, with NSX running in almost all Fortune 100 companies and many medium scale businesses. In today’s world of widespread viruses, ransomware, and even cyber warfare, the security aspect of NSX built on top of the NSX distributed firewall (DFW) is relevant to vSphere customers, regardless of their size.
The NSX DFW is a software firewall instantiated on the vNICs of the virtual machines in the data center. Thanks to its inline position, it provides maximum filtering granularity because it can inspect the traffic coming in and going out of every virtual machine without requiring redirection of the traffic to a security appliance, as shown in the following figure. It also moves along with the virtual machine during vMotion and maintains its state.
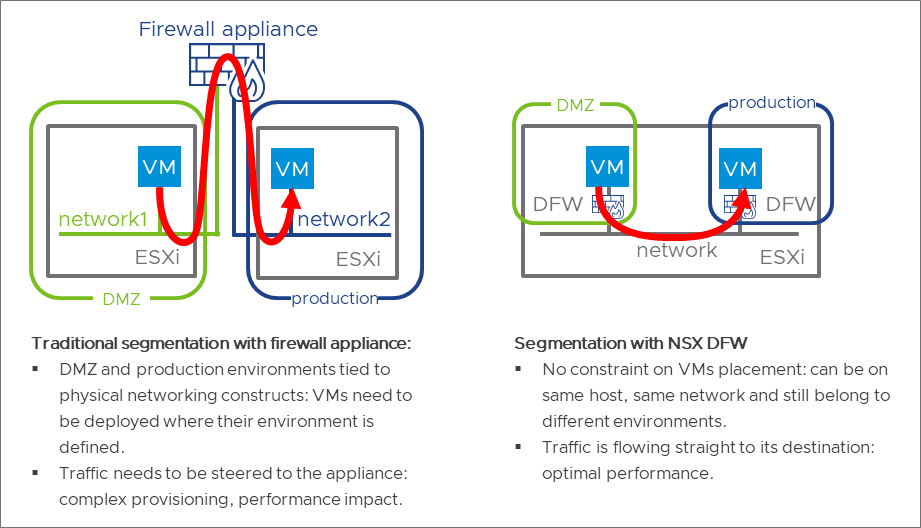
Figure 1: Traditional firewall appliance compared to the NSX DFW
The NSX DFW state-of-the-art capabilities are configured centrally from the NSX Manager and allow implementing security policies independently of the network infrastructure. This method makes it easy to implement microsegmentation and compliance requirements without dedicating racks, servers, or subnets to a specific type of workload. With the NSX DFW, security teams can deploy advanced threat prevention capabilities such as distributed IDS/IPS, network sandboxing, and network traffic analysis/network detection and response (NTA/NDR) to protect against known and zero-day threats.
A dedicated solution for security
Many NSX customers who are satisfied with the networking capability of vSphere run their production environment on a VDS with VLAN-backed dvportgroups. They deploy NSX for its security features only, and do not need its advanced networking components. Until now, those customers had to migrate their virtual machines to NSX-backed dvportgroups to benefit from the NSX DFW. This migration is easy but managing networking from NSX modifies the workflow of all the teams, including those teams that are not concerned by security:
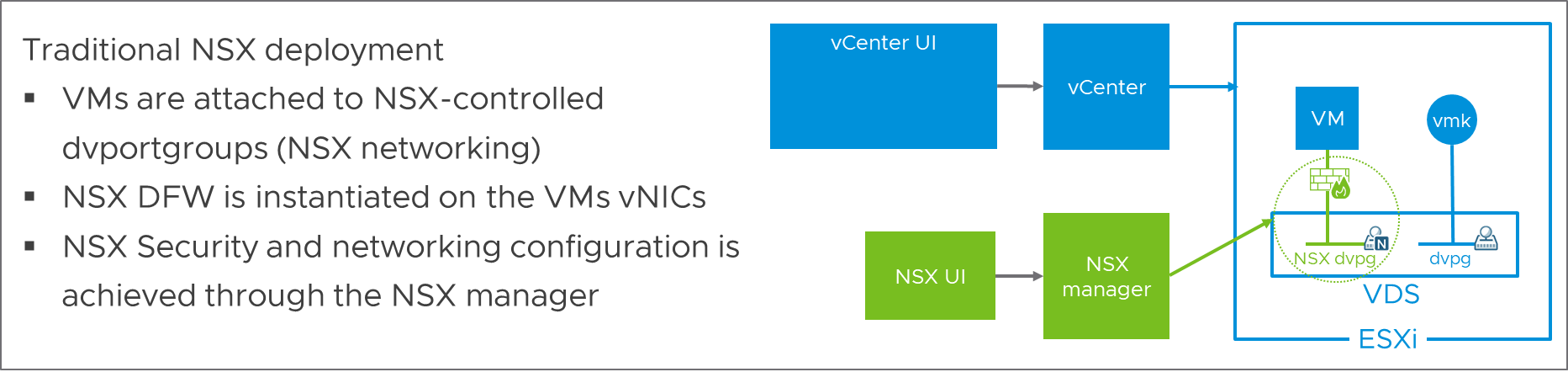
Figure 2: Traditional NSX deployment
Starting with NSX 3.2, you can run NSX security on a regular VDS, without introducing the networking components of NSX. The security team receives all the benefits of NSX DFW, and there is no impact to any other team:
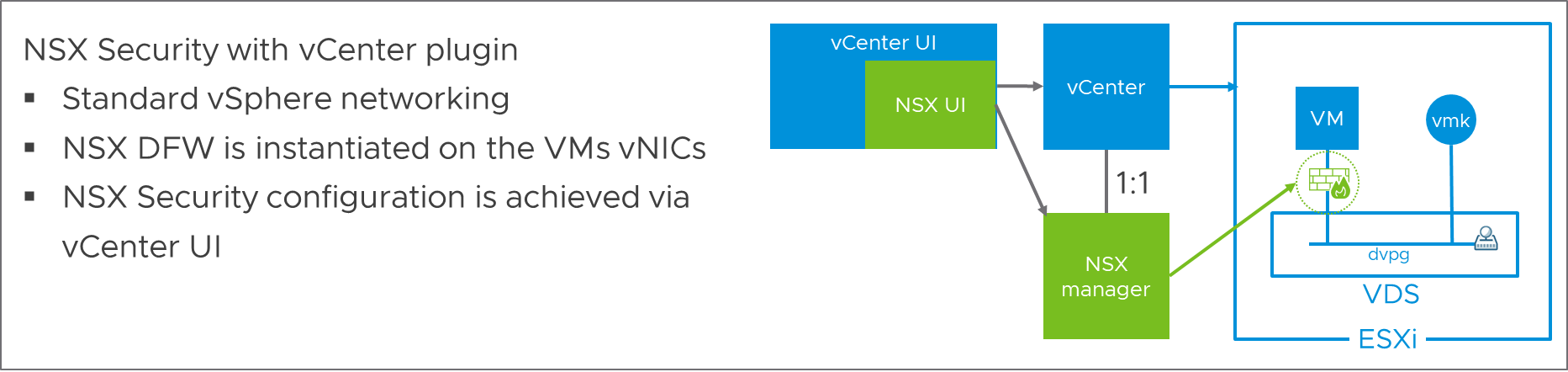
Figure 3: NSX Security with vCenter Plugin
Even better, NSX can now integrate further with vCenter, thanks to a plug-in that allows you to configure NSX from the vCenter UI. This method means that NSX can be consumed as a simple security add-on for a traditional vSphere deployment.
How to deploy and configure NSX Security
Requirements
First, we need to ensure that our VxRail environment meets the following requirements:
- vCenter Server 7.0 U3c (included with VxRail 7.0.320)
- VDS 6.7 or later
- The OVA for NSX-T with the vCenter Plugin version 3.2 or later and an appropriate NSX license
Deploy the NSX Manager and the NSX DFW on ESXi hosts
Running NSX in a vSphere environment consists of deploying a single NSX Manager virtual machine protected by vSphere HA. A shortcut in vCenter enables this step:
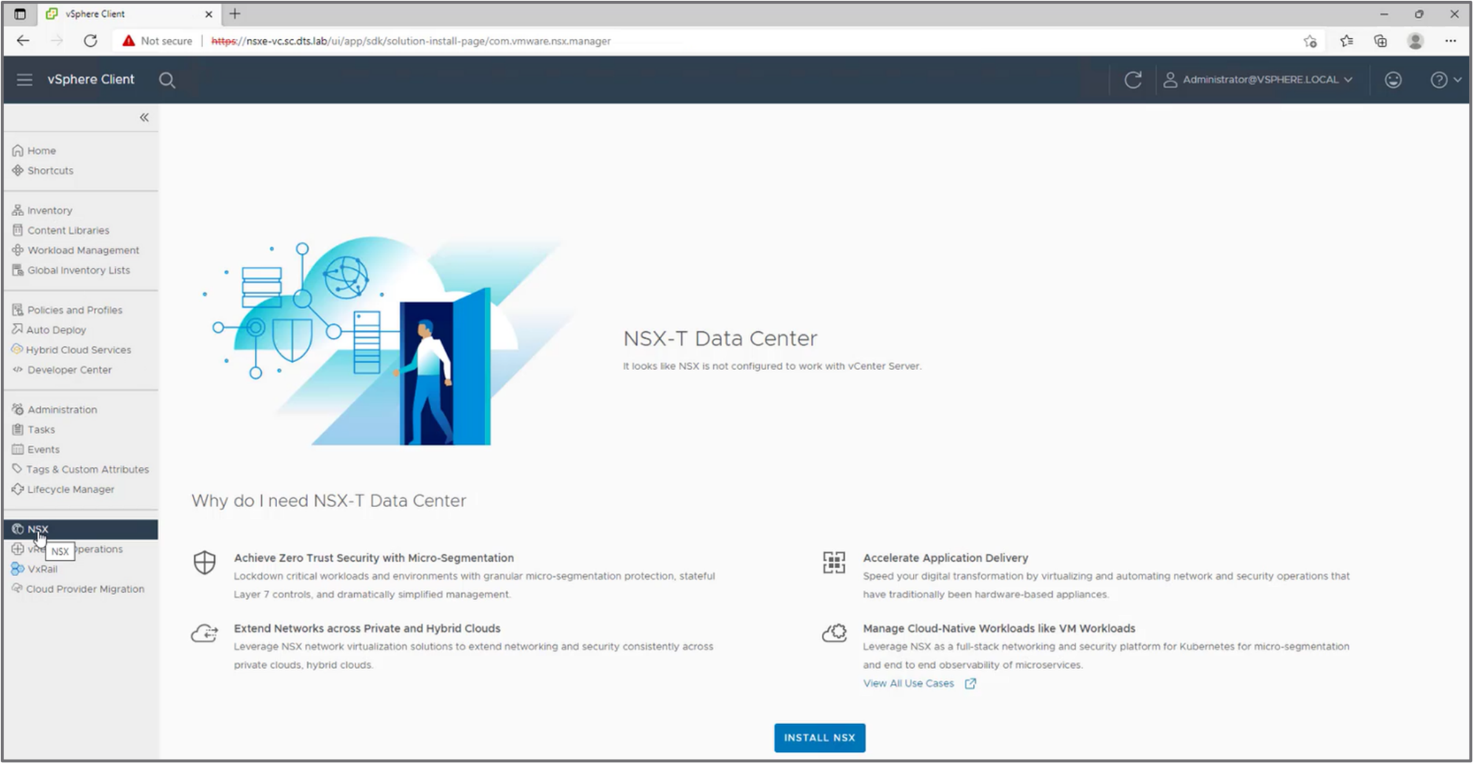
Figure 4: Deploy the NSX Manager appliance virtual machine from the NSX tab in vCenter
When the NSX Manager is up and running, it sets up a one-to-one association with vCenter and uploads the plug-in that presents the NSX UI in vCenter, as if NSX security is part of vCenter. The vCenter administrator becomes an effective NSX security administrator.
The next step, performed directly from the vCenter UI, is to enter the NSX license and select the cluster on which to install the NSX DFW binaries:
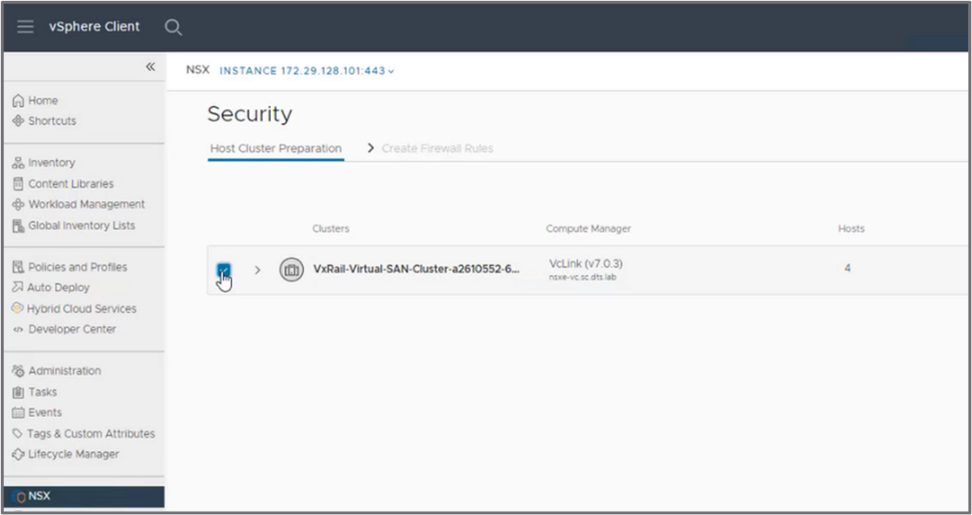
Figure 5: Select the clusters that will receive the NSX DFW binaries
After the DFW binaries are installed on the ESXi hosts, the NSX security is deployed and operational. You can exit the security configuration wizard (and configure directly from the NSX view in the vCenter UI) or let the wizard run.
Run the security configuration wizard
After installing the NSX binaries on the ESXi hosts, the plug-in runs a wizard that guides you through the configuration of basic security rules according to VMware best practices. The wizard gives the vSphere administrator simple guidance for implementing a baseline configuration that the security team can build on later. There are three different steps in this guided workflow.
First step—Segment the data center in groups
Perform the following steps, as shown in the following figure:
- Create an infrastructure group, identifying the services that the workloads in the data center will access. These services typically include DNS, NTP, DHCP servers, and so on.
- Segment the data center coarsely in environments, such as groups like Development, Production, and DMZ.
- Segment the data center finely by identifying applications running across the different environments.
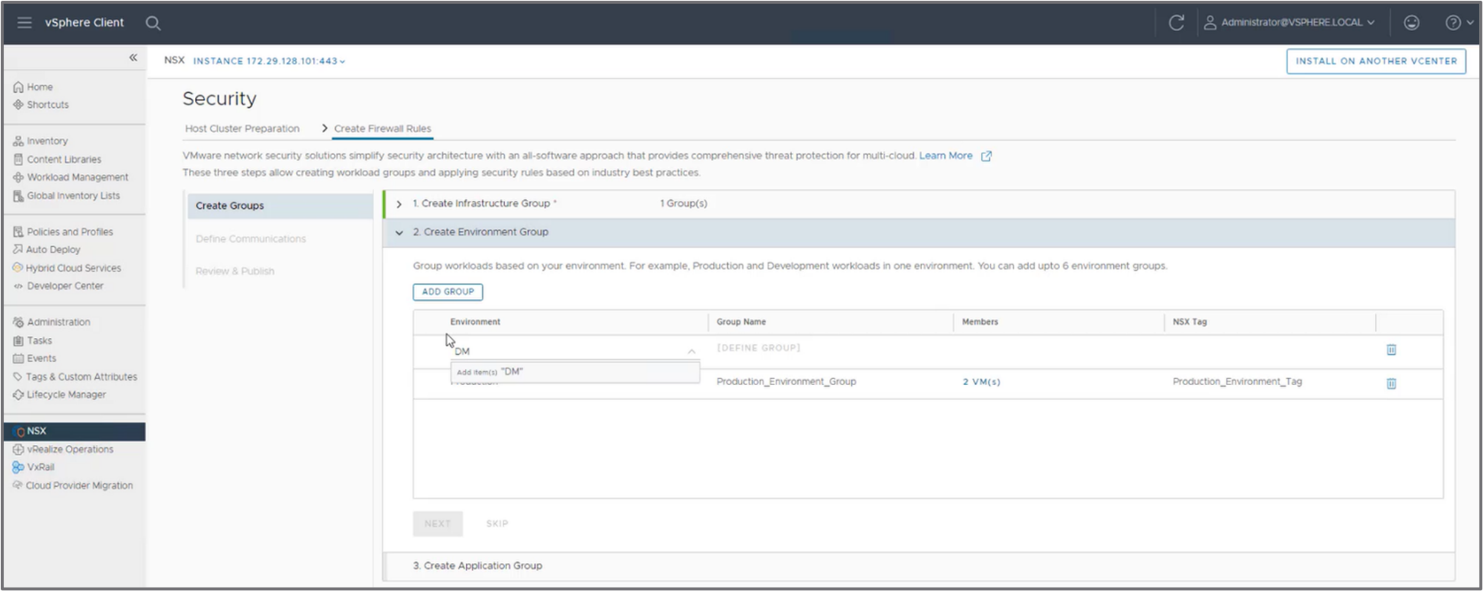
Figure 6: Example of group creation
Second step—Define communication between different groups
Perform the following steps, as shown in the following figure:
- Define which groups can access the infrastructure services
- Define how the different environments communicate with each other
- Define how applications communicate with each other
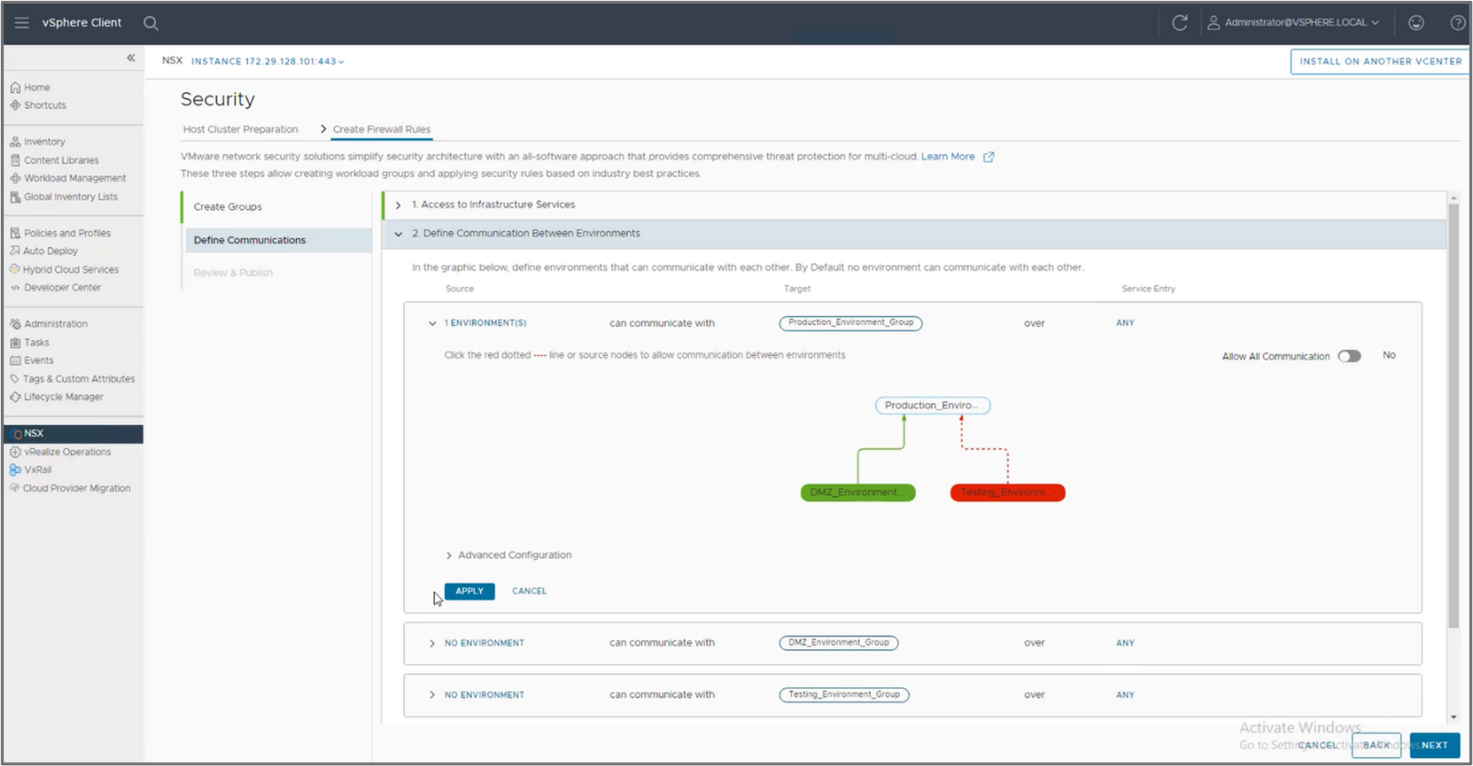
Figure 7: Define the communication between environments using a graphcial represenation
Third step—Review the configuration and publish it to the NSX DFW
After reviewing the configuration, publish the configuration to NSX:
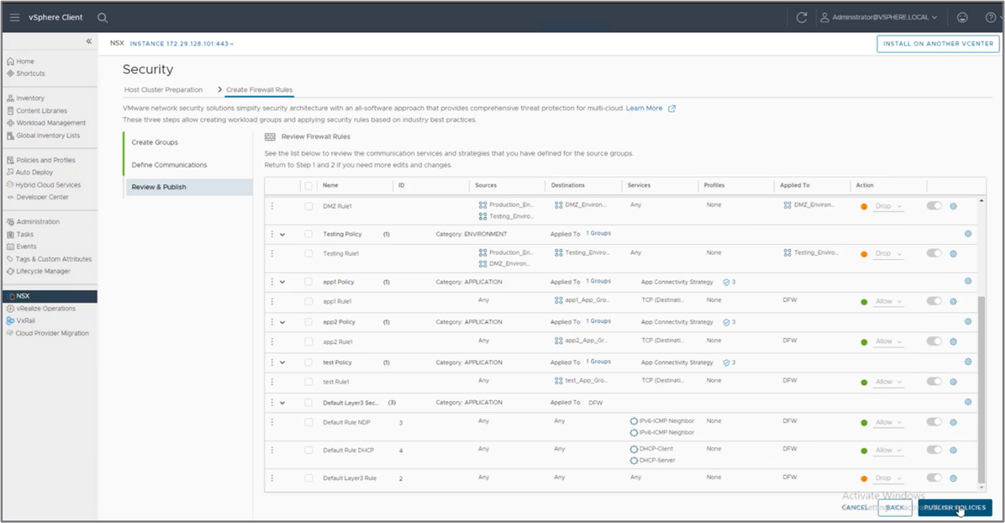
Figure 8: Review DFW rules before exiting the wizard
The full NSX UI is now available in vCenter. Select the NSX tab to access the NSX UI directly.
Final thoughts
The new VMware vCenter Plug-in for NSX drastically simplifies the deployment and adoption of NSX with VxRail for security use cases. In the past, advanced knowledge of the network virtualization platform was required. A vSphere adminstrator can now deploy it easily, using an intuitive configuration wizard available directly from vCenter.
The VMware vCenter Plug-in for NSX provides the kind of simplified and optimized experience that VxRail customers are used to when managing their HCI environment. It also addresses the challenge that customers face today, improving security even with a perceived shortage of skills in this area. Also, it can be configured easily and quickly, making the robust NSX security features more available for smaller HCI deployments.
Additional resources:
VMworld 2021 Session: NET1483 - Deploy and Manage NSX-T via vCenter: A Single Console to Drive VMware SDDC
Planning Guide: Dell EMC VxRail Network Planning Guide – Physical and Logical Network Considerations and Planning
ESG Research Report: 2022 Technology Intentions Survey
Authors:
Francois Tallet, Technical Product Manager, VMware
Karol Boguniewicz, Senior Principal Engineering Technologist, Dell Technologies

VxRail brings key features with the release of 4.7.510
Mon, 17 Aug 2020 18:31:30 -0000
|Read Time: 0 minutes
VxRail recently released a new version of our software, 4.7.510, which brings key feature functionality and product offerings
At a high level, this release further solidifies VxRail’s synchronous release commitment with vSphere of 30 days or less. VxRail and the 4.7.510 release integrates and aligns with VMware by including the vSphere 6.7U3 patch release. More importantly, vSphere 6.7U3 provides the underlying support for Intel Optane persistent memory (or PMem), also offered in this release.
Intel Optane persistent memory is non-volatile storage medium with RAM-like performance characteristics. Intel Optane PMem in a hyperconverged VxRail environment accelerates IT transformation with faster analytics (think in-memory DBMS), and cloud services.
Intel Optane PMem (in App Direct mode) provides added memory options for the E560/F/N and P570/F and is supported on version 4.7.410. Additionally, PMem will be supported on the P580N beginning with version 4.7.510 on July 14.
This technology is ideal for many use cases including in-memory databases and block storage devices, and it’s flexible and scalable allowing you to start small with a single PMem module (card) and scale as needed. Other use cases include real-time analytics and transaction processing, journaling, massive parallel query functions, checkpoint acceleration, recovery time reduction, paging reduction and overall application performance improvements.
New functionality enables customers to schedule and run "on demand” health checks in advance, and in lieu of the LCM upgrade. Not only does this give customers the flexibility to pro-actively troubleshoot issues, but it ensures that clusters are in a ready state for the next upgrade or patch. This is extremely valuable for customers that have stringent upgrade schedules, as they can rest assured that clusters will seamlessly upgrade within a specified window. Of course, running health checks on a regular basis provides sanity in knowing that your clusters are always ready for unscheduled patches and security updates.
Finally, the VxRail 4.7.510 release introduces optimized security functionality with two-factor authentication (or 2FA) with SecurID for VxRail. 2FA allows users to login to VxRail via the vCenter plugin when the vCenter is configured for RSA 2FA. Prior to this version, the user would be required to enter username and password. The RSA authentication manager automatically verifies multiple prerequisites and system components to identify and authenticate users. This new functionality saves time by alleviating the username/password entry process for VxRail access. Two-factor authentication methods are often required by government agencies or large enterprises. VxRail has already incorporated enhanced security offerings including security hardening, VxRail ACLs and RBAC, KMIP compliant key management, secure logging, and DARE, and now with the release of 4.7.510, the inclusion of 2FA further distinguishes VxRail as a market leader.
Please check out these resources for more VxRail 4.7.510 information:
By: KJ Bedard - VxRail Technical Marketing Engineer
LinkedIn: https://www.linkedin.com/in/kj-bedard-50b25315/
Twitter: @KJbedard


