Home > Integrated Products > Integrated System for Azure Stack Hub > White Papers > Monitoring Dell EMC Integrated System for Microsoft Azure Stack Hub with System Center Operations Manager > Configuring SCOM
Configuring SCOM
-
Preparing SCOM
When you configure SCOM to receive SNMP traps from OpenManage Enterprise and OpenManage Network Manager, there are several options. Some customers may already have set up SCOM as an SNMP receiver to accommodate downstream monitoring tools and devices. The method that is described in this section is based on the Kevin Holman blog post Alerting on SNMP traps in SCOM - Without discovering the SNMP Device. Dell Technologies labs followed the steps in this blog post, and we have documented the steps for reference and comparison with your SCOM environment.
Note: Before you do the steps that are described in this section, complete a full backup of the SCOM environment. User either traditional backup and recovery tools or snapshot technology on a virtualized platform. You may also prefer to contact Microsoft Support for help with setting up SCOM as an SNMP trap receiver.
Verifying SCOM management server host-based firewall rules
Verify that all necessary firewall rules have been enabled on the SCOM management server to receive SNMP traps. Test SNMP communications with target servers, if necessary. The following screenshots show the inbound and outbound rules that are required for this purpose:
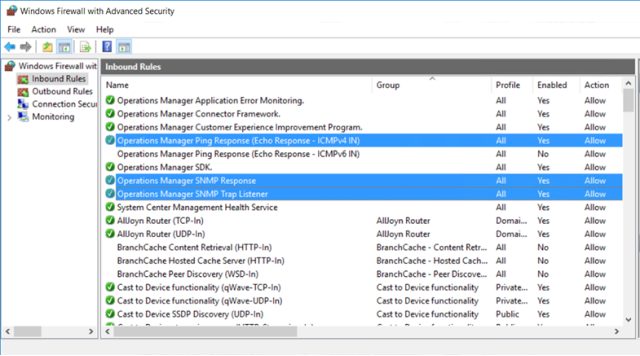
Figure 25. Enabling SCOM server inbound firewall rules
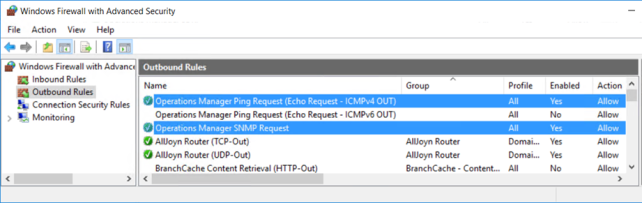
Figure 26. Enabling SCOM server outbound firewall rules
If the rules are incorrectly configured, you see SNMP traps reaching the SCOM management server from OpenManage Enterprise and OpenManage Network Manager through a utility, such as Wireshark. You do not see those traps displayed in the SCOM console monitoring view.
Downloading files from Microsoft TechNet
Review the contents of the Kevin Holman blog post Alerting on SNMP traps in SCOM – Without discovering the SNMP Device. Download a copy of the sample Management Pack and sample CSV file from Microsoft TechNet at SCOM Management Pack to Alert on SNMP Traps without Network Discovery.
Note: To adhere to your corporate monitoring standards, you must modify the sample Management Pack. We used the default Management Pack in the Dell Technologies lab for testing purposes only. The figures in the following sections reflect the use of the default Management Pack:
Preparing the CSV file
Procedure
To prepare the CSV file, after you download the networklist.csv file from TechNet:
- Modify the contents of the networklist.csv file to include the relevant information about the DellEMC-MGMTVM and DellEMC-OMEntVM virtual machines.
Note: To determine the community string of the SCOM environment stated in Base64, follow the instructions in the blog post. In the Dell Technologies lab, we used the cs3commst1ng community string when translating to Base64.
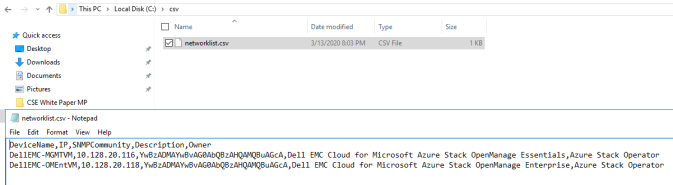
Figure 27. Modifying the CSV file
- Place the networklist.csv file in a file system share that is accessible from the SCOM management server.
In the Dell Technologies lab, we created a share that is named CSV, on a central file server, and granted everyone read permission to the share.
Importing Management Pack into SCOM
Procedure
To import Management Pack into SCOM:
- In the SCOM management console, go to Administration and right-click Management Packs. Select Import Management Packs.
- Under Select Management Packs, click Add, and then select Add from disk. Answer No to the question about whether you would like to search the online catalog for these dependencies.
- Select the Demo.SNMPDevice.xml file and click Open, and then click Install.
The following screenshot shows that Management Pack is already imported:
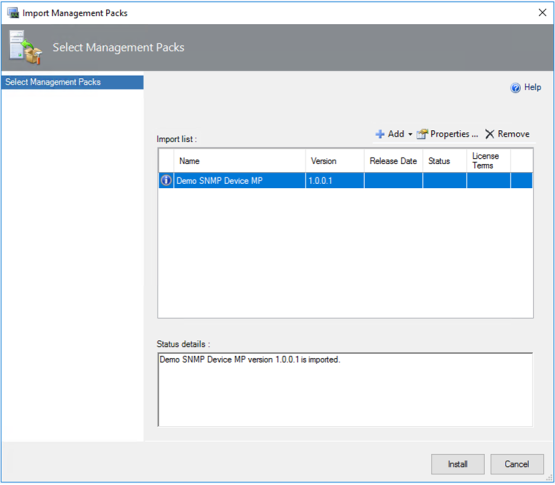
Figure 28. Importing Management Pack into SCOM
Note: It can take a while for the Management Pack to appear in the SCOM management server. Ensure that the Management Pack is visible under Administration > Management Packs > Installed Management Packs, as shown in the following figure, before proceeding with the next step:

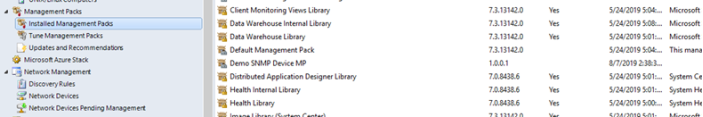
Figure 29. Verifying that Management Pack is in SCOM (example, Demo SNMP Device MP)
Creating object discovery override
Management Pack creates an object discovery in SCOM that you must customize.
Procedure
To create an object discovery override:
- In the SCOM management console, go to Authoring > Management Pack Objects > Object Discoveries.
In the test environment, we used the default object Demo SNMP Device Class Discovery.
- Right-click the object that you want to modify to fit your environment. From the list box, choose Overrides > Override the Object Discovery > For all objects of class: Demo SNMP Device Resource Pool
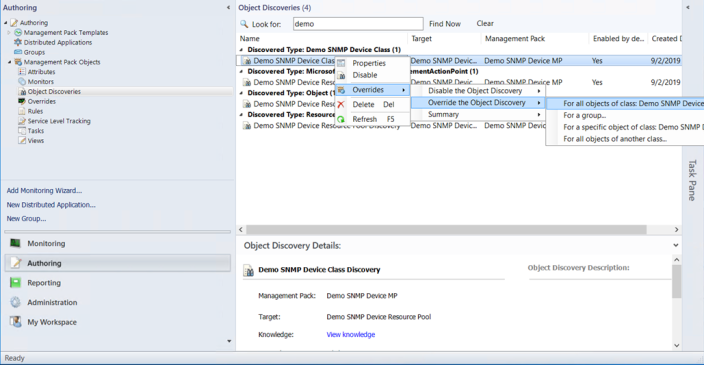
Figure 30. Creating the override
- In Override Properties, under Override-controlled parameters, select the Override checkbox for parameter CSVPath.
- Under Override Value for parameter CSVPath, enter the file server share path where the networklist.csv file resides. Click OK.
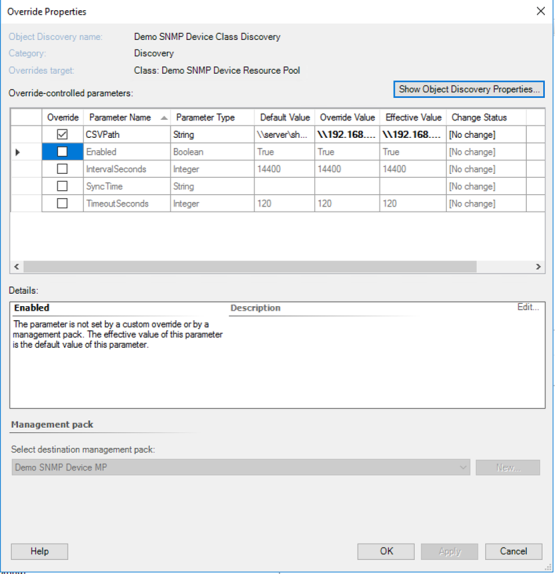
Figure 31. Changing the CSVPath override value for the discovery object
Configuring the resource pool
Procedure
To configure the resource pool:
- In the SCOM management console, go to Administration > Resource Pools.
In the test environment, we created Demo SNMP Device Resource Pool.
- Right-click the relevant resource pool, and select Manual Membership from the list box.
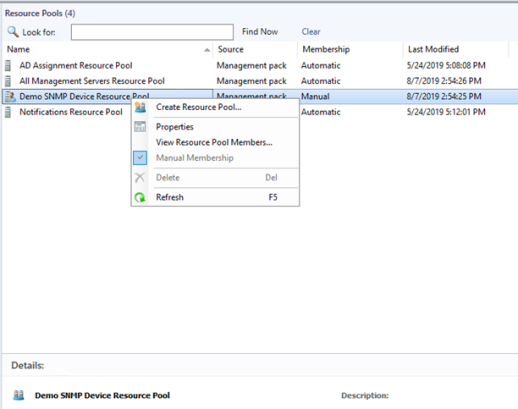
Figure 32. Modifying the resource pool membership type
- A Manual Membership dialog box displays. Click Yes to continue.
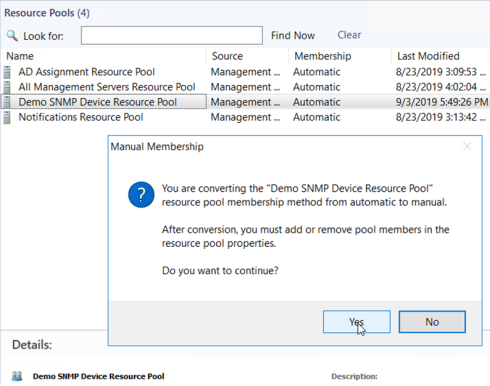
Figure 33. Warning about changing to manual membership
- Right-click the same resource pool again, and select Properties.
- In the wizard, click Next until you get to Pool Membership.
In our example, the SCOM management server should be the only visible pool member.
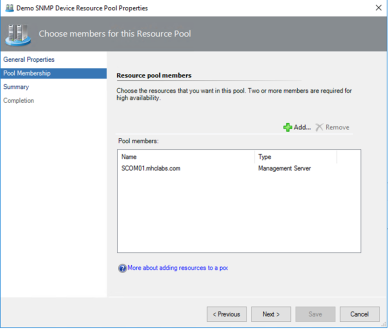
Figure 34. Adding resource pool members
- Add or remove resource pool members, if required, and then click Next.
- Under Summary, verify that all details are correct, and then click Save.
- Under Completion, click Close to exit the wizard.
Verifying SCOM monitoring view
Management Pack has created a monitoring view. In the test environment, we named the monitoring view Demo SNMP Devices. Under Demo SNMP Devices, we named the state view SNMP Devices, which contains the contents of the CSV file that we prepared previously.
Procedure
- In the SCOM management console, go to Monitoring and expand the list.
- Select the state view and verify the contents.
Note: You might need to refresh the SNMP Devices view to see the list of servers.
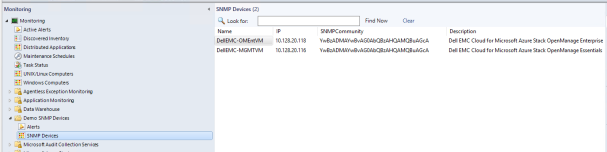
Figure 35. Viewing HLH VMs under SNMP Devices state view
SCOM is ready to receive SNMP traps from OpenManage Enterprise and OpenManage Network Manager.
For more information about the rules that are created with Management Pack, see the Kevin Holman blog post Alerting on SNMP traps in SCOM – Without discovering the SNMP Device.
