

Protect Your Systems and Data with Dell Technologies
Tue, 07 Feb 2023 23:04:19 -0000
|Read Time: 0 minutes
Threats can come from anywhere, which is why it is critical to secure all aspects of your enterprise network — from edge to endpoint, data center to cloud. At Dell Technologies, we make it easier to protect your data wherever it is stored, managed or used with security that’s built into our industry‑leading servers, storage, hyperconverged infrastructure (HCI) and data protection appliances.
Dell PowerStore systems provide a great example of the protection we offer. PowerStore is renowned for helping companies across the globe store and manage data resources. Businesses have come to rely on PowerStore for many reasons, but mainly it’s chosen for its high performance and scale‑out capabilities, versatility, and rich feature set, which delivers all things to all customers. Part of that rich feature set is layer upon layer of security.
Here’s a glimpse into some of the key security features that come with Dell PowerStore systems, and how these features can help to protect your data and system.
Protected systems
PowerStore includes numerous built-in features designed to protect the system. Features include the hardware root of trust and secure boot, which help to combat rootkit attacks and prevent unwanted code from executing on the OS.
Hardware root of trust provides an immutable, silicon-based solution to cryptographically attest to the integrity of the BIOS and firmware. It ensures that there have been no malicious modifications made throughout the supply chain or after installation.
Likewise, Data at Rest Encryption (D@RE) in PowerStore uses FIPS 140-2 validated self-encrypting drives (SEDs). This capability and KMIP (internal and external key manager support) are critical components of the feature set that help prevent data from being accessed physically, if a drive is removed.
Protected access
We’ve also included access control and logging capabilities with PowerStore to help you manage access to data and systems. Role-based access control and LDAP/LDAPS can reduce employee downtime, improve productivity, and make it easier to set access policies. Audit logging tracks changes and events on the system and can notify you to anomalies.
Dell PowerStore Manager is a critical tool that helps you manage system settings related to security topics, including encryption, and managing SSH access. TLS and IPsec are used to encrypt plaintext communication, protecting sensitive data that PowerStore appliances transmit over the cluster network. HTTP redirect adds another layer of security by redirecting any HTTP request to the more secure HTTPS protocol.
Additional access-related security measures include features like customizable login banners, third-party certificate support, VLAN segmentation, IPv6 support and Secure Connect Gateway.
Protected data
When looking to protect the data that resides on your PowerStore system, you should know that Dell Technologies offers various functionalities to help protect against ransomware and viruses from infecting your system — or to mitigate data loss in unforeseen circumstances.
Read-only snapshots, for example, enable point-in-time restores for data corruption or accidental deletion. PowerStore also allows you to perform asynchronous remote replication to another cluster for localized disasters such as floods or earthquakes. Metro replication lets you replicate synchronously to another cluster at short distances in an active/active configuration. This can help protect against power outages and other natural disasters.
But that’s not all. Other data protection functionality in PowerStore includes things like FLR, CEPA/CAVA for virus and ransomware, Secure NFS (Kerberos), SMB3 data-in-flight encryption, iSCSI CHAP, and Dynamic Resiliency Engine.
Protected software
Finally, to help protect software, Dell Technologies relies heavily on CloudIQ, which is a cloud-based AIOps proactive monitoring and predictive analytics application for Dell systems. CloudIQ uses machine learning and predictive analytics to identify potential issues, anomalies, and security risks, and proactively notifies users, allowing them to take quick action to remediate identified issues. In addition to identifying security risks, the cybersecurity feature in CloudIQ also consolidates security advisories about vulnerabilities in Dell infrastructure products discovered by Dell security specialists and the industry at large.
In addition, our Secure Development Lifecycle Program / Dell maturity model is aligned with NIST guidelines and directives to ensure high standards when it comes to protection. We also offer digitally signed firmware validation, software code integrity, and plug-ins.
Prioritize data protection
Data is the lifeblood of your organization. It’s what makes your business function, which is why you want to take special precautions to protect it.
Dell PowerStore systems make the process of protecting your data easier than ever. Plus, with such a comprehensive feature set to draw from, you’ll find exactly what you need to address your unique security situation and requirements.
Take advantage of the many PowerStore features to protect your data — and the system itself.
Learn more about PowerStore and its security features by checking out these resources:
- Dell PowerStore: Cybersecurity
- Dell PowerStore Manager Overview
- Dell PowerStore: Replication Technologies
- Dell PowerStore: Snapshots and Thin Clones
Related Blog Posts

Protect Your Systems and Data with Dell Technologies
Mon, 23 Jan 2023 15:24:08 -0000
|Read Time: 0 minutes
Threats can come from anywhere, which is why it is critical to secure all aspects of your enterprise network — from edge to endpoint, data center to cloud. At Dell Technologies, we make it easier to protect your data wherever it is stored, managed or used with security that’s built into our industry‑leading servers, storage, hyperconverged infrastructure (HCI) and data protection appliances.
Dell PowerStore systems provide a great example of the protection we offer. PowerStore is renowned for helping companies across the globe store and manage data resources. Businesses have come to rely on PowerStore for many reasons, but mainly it’s chosen for its high performance and scale‑out capabilities, versatility, and rich feature set, which delivers all things to all customers. Part of that rich feature set is layer upon layer of security.
Here’s a glimpse into some of the key security features that come with Dell PowerStore systems, and how these features can help to protect your data and system.

Protected systems
PowerStore includes numerous built-in features designed to protect the system. Features include the hardware root of trust and secure boot, which help to combat rootkit attacks and prevent unwanted code from executing on the OS.
Hardware root of trust provides an immutable, silicon-based solution to cryptographically attest to the integrity of the BIOS and firmware. It ensures that there have been no malicious modifications made throughout the supply chain or after installation.
Likewise, Data at Rest Encryption (D@RE) in PowerStore uses FIPS 140-2 validated self-encrypting drives (SEDs). This capability and KMIP (internal and external key manager support) are critical components of the feature set that help prevent data from being accessed physically, if a drive is removed.
Protected access
We’ve also included access control and logging capabilities with PowerStore to help you manage access to data and systems. Role-based access control and LDAP/LDAPS can reduce employee downtime, improve productivity, and make it easier to set access policies. Audit logging tracks changes and events on the system and can notify you to anomalies.
Dell PowerStore Manager is a critical tool that helps you manage system settings related to security topics, including encryption, and managing SSH access. TLS and IPsec are used to encrypt plaintext communication, protecting sensitive data that PowerStore appliances transmit over the cluster network. HTTP redirect adds another layer of security by redirecting any HTTP request to the more secure HTTPS protocol.
Additional access-related security measures include features like customizable login banners, third-party certificate support, VLAN segmentation, IPv6 support and Secure Connect Gateway.
Protected data
When looking to protect the data that resides on your PowerStore system, you should know that Dell Technologies offers various functionalities to help protect against ransomware and viruses from infecting your system — or to mitigate data loss in unforeseen circumstances.
Read-only snapshots, for example, enable point-in-time restores for data corruption or accidental deletion. PowerStore also allows you to perform asynchronous remote replication to another cluster for localized disasters such as floods or earthquakes. Metro replication lets you replicate synchronously to another cluster at short distances in an active/active configuration. This can help protect against power outages and other natural disasters.
But that’s not all. Other data protection functionality in PowerStore includes things like FLR, CEPA/CAVA for virus and ransomware, Secure NFS (Kerberos), SMB3 data-in-flight encryption, iSCSI CHAP, and Dynamic Resiliency Engine.
Protected software
Finally, to help protect software, Dell Technologies relies heavily on CloudIQ, which is a cloud-based AIOps proactive monitoring and predictive analytics application for Dell systems. CloudIQ uses machine learning and predictive analytics to identify potential issues, anomalies, and security risks, and proactively notifies users, allowing them to take quick action to remediate identified issues. In addition to identifying security risks, the cybersecurity feature in CloudIQ also consolidates security advisories about vulnerabilities in Dell infrastructure products discovered by Dell security specialists and the industry at large.
In addition, our Secure Development Lifecycle Program / Dell maturity model is aligned with NIST guidelines and directives to ensure high standards when it comes to protection. We also offer digitally signed firmware validation, software code integrity, and plug-ins.
Prioritize data protection
Data is the lifeblood of your organization. It’s what makes your business function, which is why you want to take special precautions to protect it.
Dell PowerStore systems make the process of protecting your data easier than ever. Plus, with such a comprehensive feature set to draw from, you’ll find exactly what you need to address your unique security situation and requirements.
Take advantage of the many PowerStore features to protect your data — and the system itself.
Learn more about PowerStore and its security features by checking out these resources:
- Dell PowerStore: Cybersecurity
- Dell PowerStore Manager Overview
- Dell PowerStore: Replication Technologies
- Dell PowerStore: Snapshots and Thin Clones

Configuring PowerStore File Extension Filtering to Prevent Ransomware
Wed, 06 Sep 2023 18:12:28 -0000
|Read Time: 0 minutes
Overview
Disallowing known ransomware extensions from being written to the file system can be a simple and effective mechanism to deter and/or prevent ransomware. PowerStore file systems include a file extension filtering capability that restricts specific file extensions from being stored on an SMB share. Traditionally, this feature has been used to prevent users from storing non-business data on a share, however its uses extend to blocking malicious extensions from being written to a share at all.
File extension filtering can be leveraged in conjunction with other features such as CEPA to implement a ransomware strategy with multiple layers of defense. Let’s dive into how to configure PowerStore file extension filtering to better protect your system today.
Configuration
To configure file extension filtering:
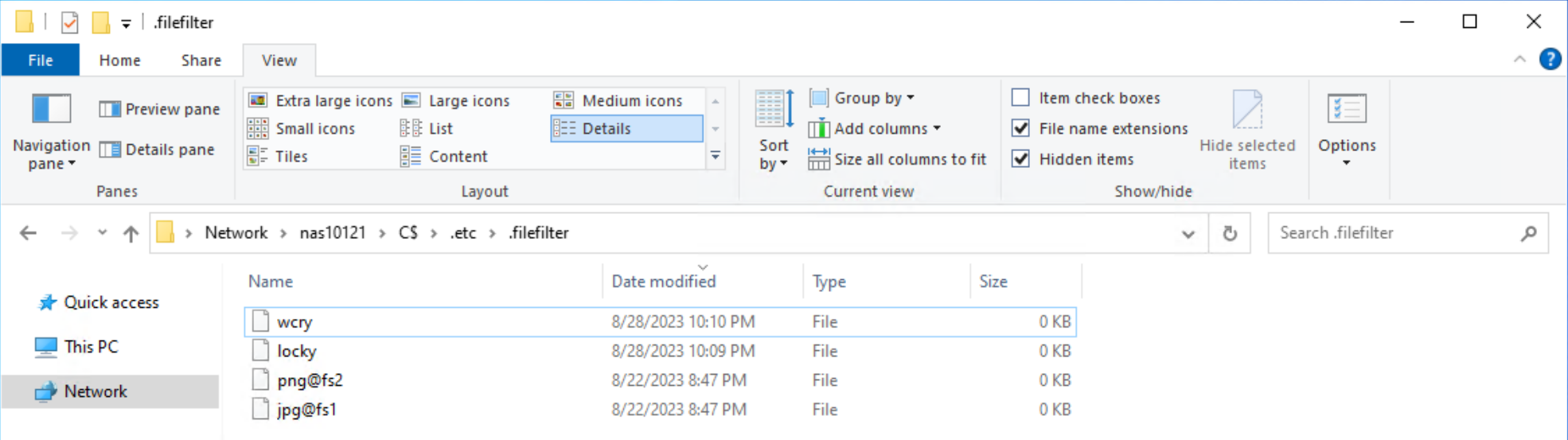
- Go to the \\<SMB_Server>\c$\.etc\.filefilter directory as an administrator
- To configure a filter, create an empty file using the naming convention extension@sharename
- For example, to filter .wcry ransomware files on the FS1 share, create a file named wcry@FS1
- To enable the filter on all shares on the SMB server, create the file with only the extension, such as wcry
You can configure multiple filters by creating additional files in this directory. For ransomware prevention use cases, create additional filters for other known ransomware extensions. Each SMB server has its own independent file extension filtering configuration, so each can be customized with its own configuration. The following figure shows an example of the configuration of the file extension filtering.
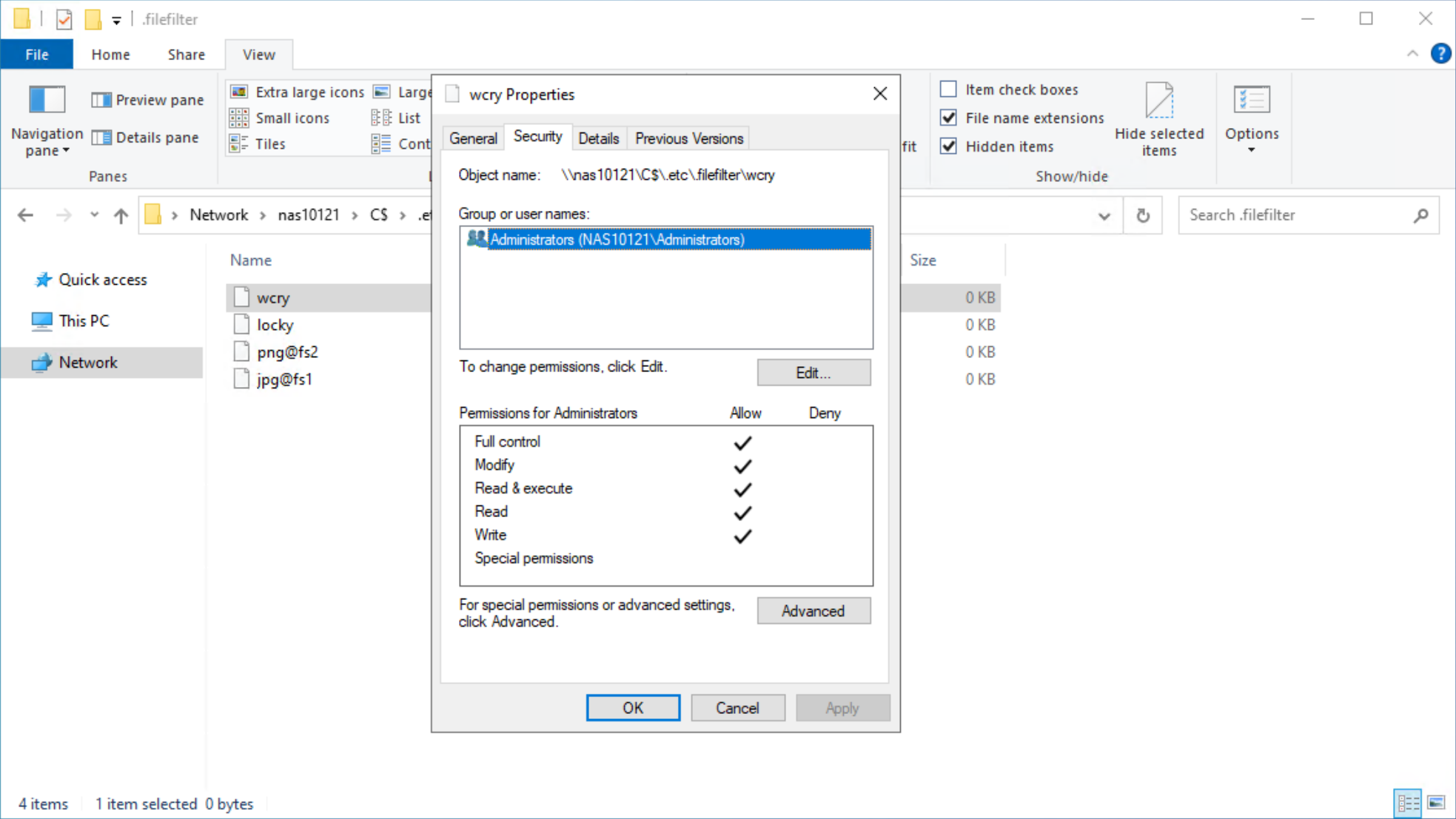
After configuring a file extension filter, you can permit exceptions for specific users or groups by changing the ACL on the filter file to provide Full Control privileges to the users or groups that should be excluded.
For example, if the Administrators group is provided Full Control permissions on the wcry filter file, then users in the Administrators group can store .wcry files on the share, while others cannot. Exceptions can be configured independently for each file filter being created, as shown in the following figure.
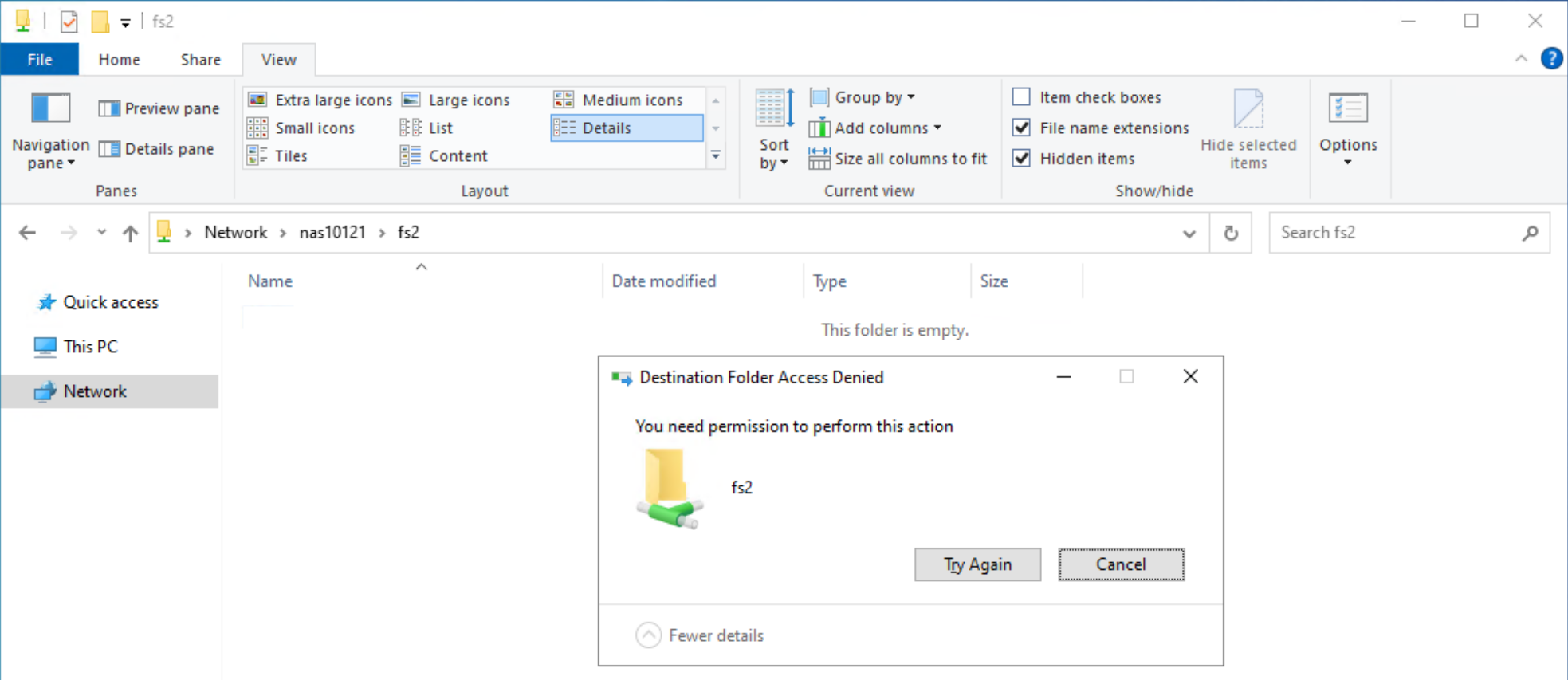
When users attempt to copy a file with a blocked extension, they receive an Access Denied error, as shown in the following figure.
Considerations
Note that this feature only works on SMB and does not filter file extensions when writing over NFS. Users could manually rename file extensions to bypass this filter, provided those other extensions are not also explicitly blocked, however malware may not be able to adapt and work around this as easily. Since the list of filtered extensions must be checked each time a file is written, having many filters could impact performance.
Conclusion
File extension filtering is a simple and powerful capability that provides administrators the ability to control the type of data that is stored on an SMB share. Easy to configure and able to provide an additional layer of protection against ransomware activity, file extension filtering is an effective addition to any comprehensive cybersecurity strategy to protect and secure your data.
Resources
The following resources provide more information about PowerStore:
Author: Wei Chen, Technical Staff, Engineering Technologist



