Blogs

New SEC Cyber Security Disclosure Rules Can Impact Your Business
Tue, 31 Oct 2023 16:12:27 -0000
|Read Time: 0 minutes
For the past few years, organizations of all sizes have realized the risk and impact that a Cyber Attack could have on their organization, including loss of revenue, brand impact, business interruption, remediation costs, and more.
A new rule from the Securities and Exchange Commission (SEC) now identifies cyber as a true category of business risk, joining numerous other challenges that companies face including financial, operational, regulatory, and compliance. This new rule officially declares that cyber is “EVERYONE’s” issue, and defending your business is critical to your shareholders, customers, and employees.
Effective Dec 18, 2023, the SEC adopted final rule – Final Rule: Cybersecurity Risk Management, Strategy, Governance, and Incident Disclosure – which requires disclosure of material cybersecurity incidents on Form 8-K and periodic disclosure of a registrant’s cybersecurity risk management, strategy, and governance in annual reports (see note 1).
“Whether a company loses a factory in a fire — or millions of files in a cybersecurity incident — it may be material to investors,” said SEC Chair Gary Gensler.
Why: Ransomware attacks are ongoing and pose a risk to all parties engaged in public companies, including investors. As remote work has increased, so has the adversary’s ability to capitalize on an attack. The SEC has concluded that there needs to be a more consistent way to provide disclosure.
What is Required: Under the new regulations, public companies will need to disclose, “any cybersecurity incident they determine to be material and describe the material aspects of the nature, scope, and timing of the incident, as well as the material impact or reasonably likely material impact of the incident on the registrant, including its financial condition and results of operations.”
For more information, please review the SEC Fact Sheet.
Impact on Customers: The new regulations enable the CISO and other security teams to create further awareness of cybersecurity within their own organization. The requirements mandate that you provide the following information:
- When the incident was discovered and whether it is ongoing
- A brief description of the nature and scope of the incident
- Whether any data were stolen, altered, accessed, or used for any other unauthorized purpose
- The effect of the incident on the registrant’s operations and whether the registrant has remediated or is currently remediating the incident
- Who to contact for help
Summary: Cyber is a top challenge that is not going away. Cyber Security Teams are essential for the well-being of the organization and are critical in protecting assets, employees, and C level executives.
It is of the utmost importance that C Level leadership understands that it’s not just the responsibility of CISO or CIO but also of the Board and the C suite to manage risk.
Dell provides end to end proactive and reactive solutions to help customers reduce their risk. The following checklist will help you consider and distill some of the risks your company faces:
- What are your critical assets? Have you identified top risks?
- If you experienced a material cyber incident, who would you call and do you have a way to understand what happened?
- Is your team managing the top cyber risks proactively and continuously so that you can monitor threats and vulnerabilities before they become material incidents?
- Can you provide Rapid analysis of what happened?
Dell provides a managed detection and response solution that monitors your environment 24/7, including protection, remediation, and analysis of your data as well as continuous monitoring.
Our Vulnerability Scanning searches for Vulnerabilities, helping you identify your assets and any areas to fix and patch.
Dell also provides Incident Response services to restore, rebuild, and remediate your issues to get you back into operating your business.
Resources
NOTE 1: SECURITIES AND EXCHANGE COMMISSION 17 CFR Parts 229, 232, 239, 240, and 249 [Release Nos. 33-11216; 34-97989; File No. S7-09-22] RIN 3235-AM89 Cybersecurity Risk Management, Strategy, Governance, and Incident Disclosure AGENCY: Securities and Exchange Commission.
NOTE 2: Advice and commentary in this paper does not constitute Dell Legal advice. Anyone reading this should consult their own legal team for advice and opinion.
Author: Steven Granat
Contact: Steven.Granat@Dell.com
#IWORK4DELL
Four Commonly Overlooked Foundations for Cybersecurity
Wed, 29 Mar 2023 13:46:53 -0000
|Read Time: 0 minutes
Lack of well-maintained foundational cybersecurity elements creates gaps, residual risks, and other operational challenges. These challenges lead organizations to a weakened cybersecurity posture.
Four commonly overlooked foundational elements are:
- Asset management
- Business impact analysis
- Risk management
- Threat and vulnerability management
These elements, coupled with the pace of change in the industry and the need to quickly mitigate risks, cause organizations to make decisions about controls and solutions without all the necessary information.
To mitigate this problem, organizations need to examine the foundational components used as input to the cybersecurity control decision processes.
Asset management across on-premises and cloud
A 2022 ThoughtLab Group study estimated that cybersecurity attacks during the next two years will primarily target misconfigurations, human error, poor maintenance, and unknown assets. Comprehensive asset management is critical to inform cybersecurity decision-making designed to mitigate many of these challenges.
The asset management strategy and process for on-premises and cloud should include:
- Devices (for example, computers, Internet of Things [IoT], mobile)
- Applications
- Identities (internal and external)
- Data (for example, repositories, sensitivity, ownership, data flows)
- Employees, contractors, partners, vendors, and providers
- Supply chain (leveraging data such as value stream maps to help identify the supply chain assets)
Asset inventory management is one of the most difficult tasks for an organization to establish and maintain. It is a continuous process, and changes to the environment are frequent (new servers, updates, user and data creation/deletion, and so on).
If organizations do not understand what they have, they cannot begin to estimate its value and priority in the business impact analysis. Organizations will also be unable to determine (through the risk management process) what risks are associated with an asset if they do not know it exists or if they have incorrect data. For example, if a server is incorrectly identified as running a certain application or patch level, it will have different risks associated with it than if that server has a different application running or patch level deployed.
Business impact analysis
In the past, the business impact analysis (BIA) was conducted mainly to gather application details, assess the impact of disasters, and aid in making decisions for recovery controls. However, today the BIA serves as a critical foundational component for an organization's cybersecurity program, providing insights into overall business risks, including disaster recovery.
Establishing and regularly updating the business asset values and priorities—through a qualitative, quantitative, or hybrid approach—provides the baseline for the BIA. Once assets are identified and sensitivity is understood (Quinn, and others, Using Business Impact Analysis to Inform Risk Prioritization and Response, 2022), determination of their business value (focusing on cyber or digital assets) and priority, including tiering, can be made. (While people may be considered as an asset in asset management, their monetary value is typically not measured in the BIA.)
The BIA should then continue the asset evaluation by identifying potential threats. It should assess the potential impact of the threats and determine the probability of their occurrence on the assets and, ultimately, the business. This assessment provides the critical input needed for risk management and shows where the BIA and risk management intersect.
The NIST IR 8286D (2022) provides additional detail regarding the BIA and its critical role in the risk management processes. If done incorrectly, the BIA could lead to improperly prioritizing a system, inadequate controls being implemented to that system, and, ultimately, a breach of the system.
Risk management
Risk management is a large, complex process that intersects many aspects of cybersecurity. It can involve a wide range of activities, including conducting a BIA, assessing risks, and managing vulnerabilities and threats.
The output from the BIA informs the risk management process. It does this by providing an understanding of the impact of an incident so that the risk management process can prioritize controls and resources and determine the risk strategy. Strategies include mitigation, avoidance, transference, reduction, or accepting the risk. Combinations of risk strategies should be leveraged to close gaps that lead to residual risk. With this approach to risk management, organizations can stay ahead of the ever-changing threats and challenges.
Risk management can cover various cross-sections of the business, such as supply chain, third-party vendors, and regulatory compliance. Supply chain and third-party vendor risk should be part of an overall risk management strategy. “82 percent [of CIOs surveyed] say their organizations are vulnerable to cyberattacks targeting software supply chains” (Barker, 2022). Combining outputs from asset management and vulnerability management with organization risk strategies, organizations can make informed decisions that provide continuity through the supply chain and third-party vendor support.
Threat and vulnerability management
According to the Check Point Cyber Security Report 2021, 75 percent of attacks exploited vulnerabilities at least 2 years old. Threat and vulnerability management includes scanning, vulnerability scoring and prioritization, and updating necessary to thwart these attacks.
The outputs of asset management data identify systems to be scanned for vulnerabilities. Risk and vulnerability management overlap; threat and vulnerability management informs the risk management process, which prioritizes and determines how to address each vulnerability.
An organization’s cybersecurity program matures by incorporating threat and vulnerability management into its cybersecurity processes.
Conclusion
Cybersecurity is challenging due to constantly evolving threats. A wide range of adversaries adds to the complexity. Many organizations successfully capture data but then fail to maintain it, increasing both the vulnerability and the risk of a cyberattack. To stay ahead of constant expansion of threats and challenges in cybersecurity, organizations must establish and maintain the foundational components of asset management, BIA, risk management, and threat and vulnerability. These foundational components are interdependent. A change in data in one component often requires a change in another.
Partnering with experienced cybersecurity experts can help ensure that your organization stays protected against potential threats. Act today by contacting a Dell Technologies account representative to learn more about how Dell can help your organization safeguard against potential cyber threats.
Resources
- Barker, I. (2022, 5). 82 percent of CIOs believe their software supply chains are vulnerable. Retrieved from Beta News: https://betanews.com/2022/05/31/82-percent-of-cios-believe-their-software-supply-chains-are-vulnerable/
- Quinn, S., Ivy, N., Chua, J., Barrett, M., Feldman, L., Topper, D., . . . Gardner, R. (2022, 11). Using Business Impact Analysis to Inform Risk Prioritization and Response. Retrieved from NIST: https://nvlpubs.nist.gov/nistpubs/ir/2022/NIST.IR.8286D.pdf
- ThoughtLab Group. (2022). Cybersecurity Solutions for a Riskier World eBook. Retrieved from ThoughtLab Group: https://thoughtlabgroup.com/wp-content/uploads/2022/05/Cybersecurity-Solutions-for-a-Riskier-World-eBook_FINAL-2-1.pdf
Author: Chris Morgan, Principal Consultant
https://www.linkedin.com/in/cmorgandell/

Protect Your Systems and Data with Dell Technologies
Tue, 07 Feb 2023 23:04:19 -0000
|Read Time: 0 minutes
Threats can come from anywhere, which is why it is critical to secure all aspects of your enterprise network — from edge to endpoint, data center to cloud. At Dell Technologies, we make it easier to protect your data wherever it is stored, managed or used with security that’s built into our industry‑leading servers, storage, hyperconverged infrastructure (HCI) and data protection appliances.
Dell PowerStore systems provide a great example of the protection we offer. PowerStore is renowned for helping companies across the globe store and manage data resources. Businesses have come to rely on PowerStore for many reasons, but mainly it’s chosen for its high performance and scale‑out capabilities, versatility, and rich feature set, which delivers all things to all customers. Part of that rich feature set is layer upon layer of security.
Here’s a glimpse into some of the key security features that come with Dell PowerStore systems, and how these features can help to protect your data and system.
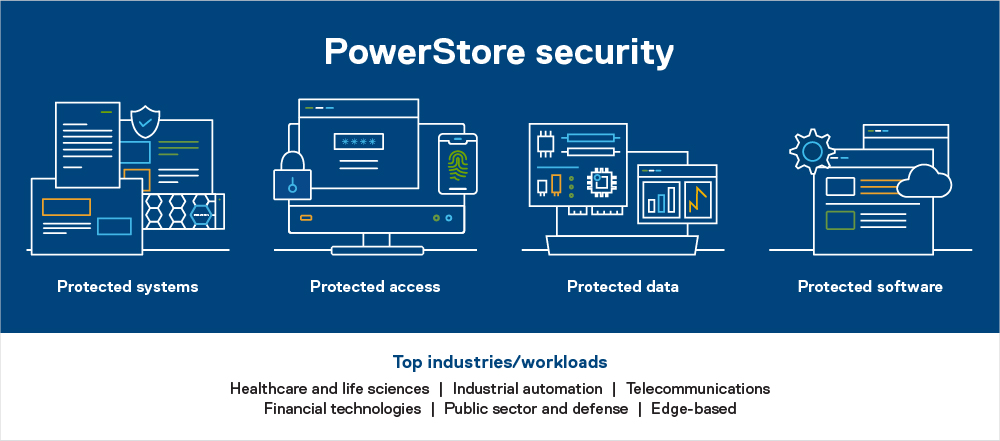
Protected systems
PowerStore includes numerous built-in features designed to protect the system. Features include the hardware root of trust and secure boot, which help to combat rootkit attacks and prevent unwanted code from executing on the OS.
Hardware root of trust provides an immutable, silicon-based solution to cryptographically attest to the integrity of the BIOS and firmware. It ensures that there have been no malicious modifications made throughout the supply chain or after installation.
Likewise, Data at Rest Encryption (D@RE) in PowerStore uses FIPS 140-2 validated self-encrypting drives (SEDs). This capability and KMIP (internal and external key manager support) are critical components of the feature set that help prevent data from being accessed physically, if a drive is removed.
Protected access
We’ve also included access control and logging capabilities with PowerStore to help you manage access to data and systems. Role-based access control and LDAP/LDAPS can reduce employee downtime, improve productivity, and make it easier to set access policies. Audit logging tracks changes and events on the system and can notify you to anomalies.
Dell PowerStore Manager is a critical tool that helps you manage system settings related to security topics, including encryption, and managing SSH access. TLS and IPsec are used to encrypt plaintext communication, protecting sensitive data that PowerStore appliances transmit over the cluster network. HTTP redirect adds another layer of security by redirecting any HTTP request to the more secure HTTPS protocol.
Additional access-related security measures include features like customizable login banners, third-party certificate support, VLAN segmentation, IPv6 support and Secure Connect Gateway.
Protected data
When looking to protect the data that resides on your PowerStore system, you should know that Dell Technologies offers various functionalities to help protect against ransomware and viruses from infecting your system — or to mitigate data loss in unforeseen circumstances.
Read-only snapshots, for example, enable point-in-time restores for data corruption or accidental deletion. PowerStore also allows you to perform asynchronous remote replication to another cluster for localized disasters such as floods or earthquakes. Metro replication lets you replicate synchronously to another cluster at short distances in an active/active configuration. This can help protect against power outages and other natural disasters.
But that’s not all. Other data protection functionality in PowerStore includes things like FLR, CEPA/CAVA for virus and ransomware, Secure NFS (Kerberos), SMB3 data-in-flight encryption, iSCSI CHAP, and Dynamic Resiliency Engine.
Protected software
Finally, to help protect software, Dell Technologies relies heavily on CloudIQ, which is a cloud-based AIOps proactive monitoring and predictive analytics application for Dell systems. CloudIQ uses machine learning and predictive analytics to identify potential issues, anomalies, and security risks, and proactively notifies users, allowing them to take quick action to remediate identified issues. In addition to identifying security risks, the cybersecurity feature in CloudIQ also consolidates security advisories about vulnerabilities in Dell infrastructure products discovered by Dell security specialists and the industry at large.
In addition, our Secure Development Lifecycle Program / Dell maturity model is aligned with NIST guidelines and directives to ensure high standards when it comes to protection. We also offer digitally signed firmware validation, software code integrity, and plug-ins.
Prioritize data protection
Data is the lifeblood of your organization. It’s what makes your business function, which is why you want to take special precautions to protect it.
Dell PowerStore systems make the process of protecting your data easier than ever. Plus, with such a comprehensive feature set to draw from, you’ll find exactly what you need to address your unique security situation and requirements.
Take advantage of the many PowerStore features to protect your data — and the system itself.
Learn more about PowerStore and its security features by checking out these resources:
- Dell PowerStore: Cybersecurity
- Dell PowerStore Manager Overview
- Dell PowerStore: Replication Technologies
- Dell PowerStore: Snapshots and Thin Clones

Part 2 – PowerProtect Cyber Recovery – Abilities and Improvements in the Cloud
Thu, 26 Jan 2023 21:42:07 -0000
|Read Time: 0 minutes
In my previous blog I talked about the new abilities on the cloud for the PowerProtect Cyber Recovery 19.11 release, which also covered Cyber Recovery on Microsoft Azure.
This time I want to focus on the latest release of Cyber Recovery 19.12 that supports a Google Cloud Platform (GCP) deployment with the entire Cyber Recovery Vault content.
As in AWS and Azure, the architecture remains the same: there’s a dedicated VPC with a Cyber Recovery Jump Host running in its own isolated subnet, and another isolated subnet that runs the Cyber Recovery Management Host and the Vault DDVE. The entire solution is secure with GCP firewall rules that prevent access to the vault. Only the Cyber Recovery Jump Host can access the Cyber Recovery Management Host and Vault DDVE.
You’ll notice in the following architecture diagram that the vault has a second VPC with a subnet, which doesn’t exist in the AWS or Azure deployments. That’s because this is how GCP handles and allows the DDVE to have another NIC (that’s intended for replication).
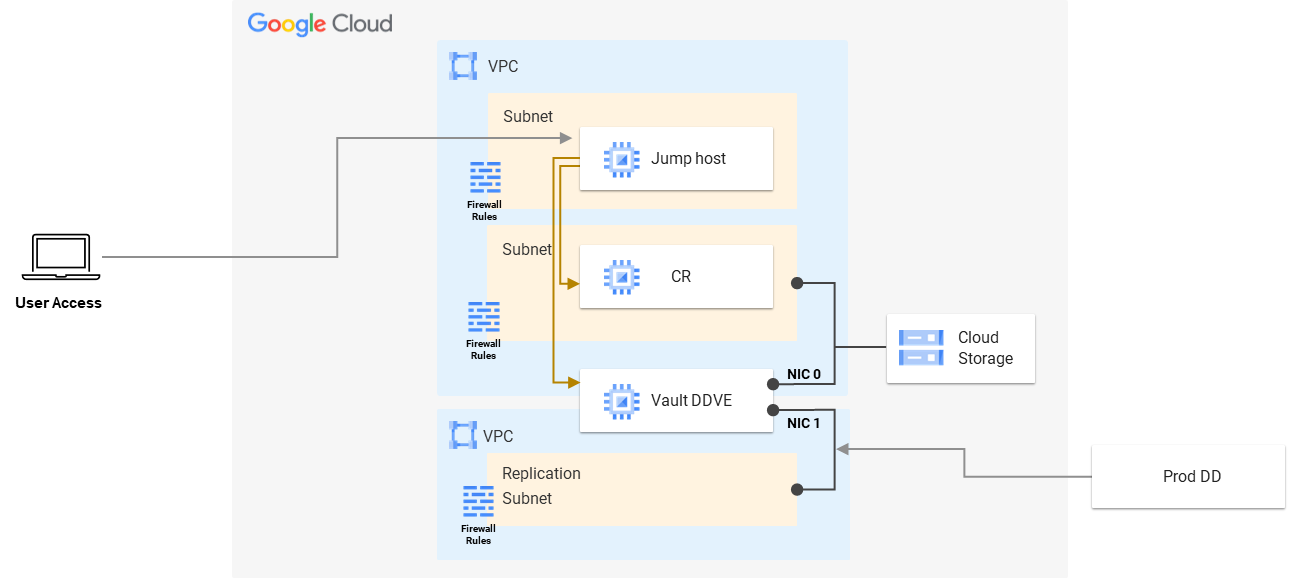
The deployment process is similar to the deployment process for other cloud platforms and is based on a template that deploys the entire Cyber Recovery Vault and its components.
Note: Deploying PowerProtect Cyber Recovery in the cloud must be performed by Dell Technologies Professional Services.
Now that we’ve talked about GCP, we should talk about CyberSense on AWS, which I know a lot of people have been waiting for. Starting in the Cyber Recovery 19.12 release, CyberSense 8.0 is also available for deployment on AWS using an AMI that can be shared with the customer’s AWS account.
Cyber Recovery users who run their vault on AWS can now deploy CyberSense in their vault, connect it to their Cyber Recovery Management Host, and use it to analyze their CR copies.
CyberSense was improved for this release and uses DDBoost (instead of just NFS) to read data from the DDVE, to make the analysis process much faster!
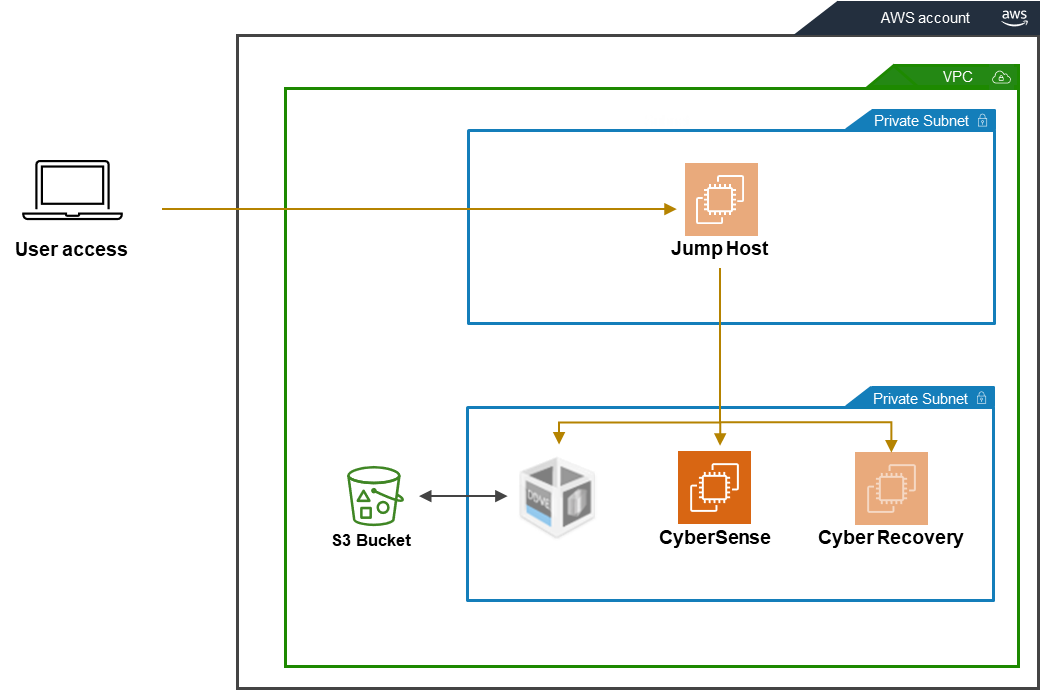
There’re other exciting new features coming out in Dell PowerProtect Cyber Recovery and CyberSense – so make sure to check out the latest release notes and documents.
Resources
Additional interesting resources can be found here:
Author: Eli Persin, Principal Systems Engineer

PowerProtect Cyber Recovery – Abilities and Improvements in the Cloud
Thu, 26 Jan 2023 21:42:07 -0000
|Read Time: 0 minutes
As part of organizations’ cloud journey, their presence in the cloud is increasing and they are running their development and production environment, or some of it, in the cloud.
Although running in the cloud has its own benefits, the need for cyber recovery abilities doesn’t change from on-premises to cloud, because the dangers remain the same.
Organizations understand the benefits and contributions of a working cyber recovery solution. And PowerProtect Cyber Recovery provides them exactly that, and it’s already supported on AWS.
The design is simple – organizations run their Cyber Recovery vault on their AWS cloud account. Their production site is also in the cloud. The production and the vault can be deployed in different regions or even using different cloud accounts. (It is also possible to run the Cyber Recovery vault on the cloud in conjunction with an on-premises production environment, but this option is less recommended). The production data could be protected with PowerProtect Data Manager (for example) with PowerProtect DDVE and replicated to the vault DDVE.
Until the recent PowerProtect Cyber Recovery 19.11 release, these environments were missing an important component that completes the solution on the cloud – CyberSense.
CyberSense will soon be supported on AWS, so you will be able to deploy it as an EC2 instance and be able to analyze their copies.
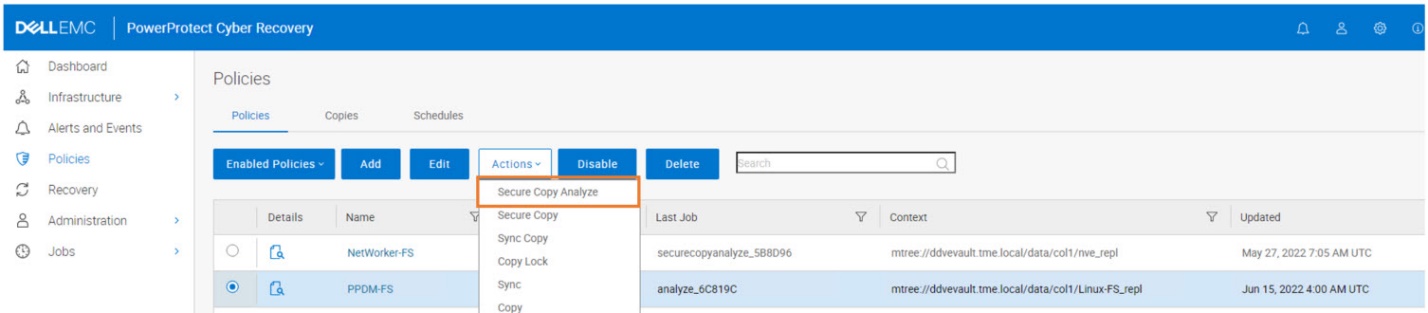
New also to the PowerProtect Cyber Recovery 19.11 release is the ability to use the “Secure Copy Analyze” action, which saves you from having to run “Secure Copy” first, followed by “Analyze” on the copy itself after it’s created.
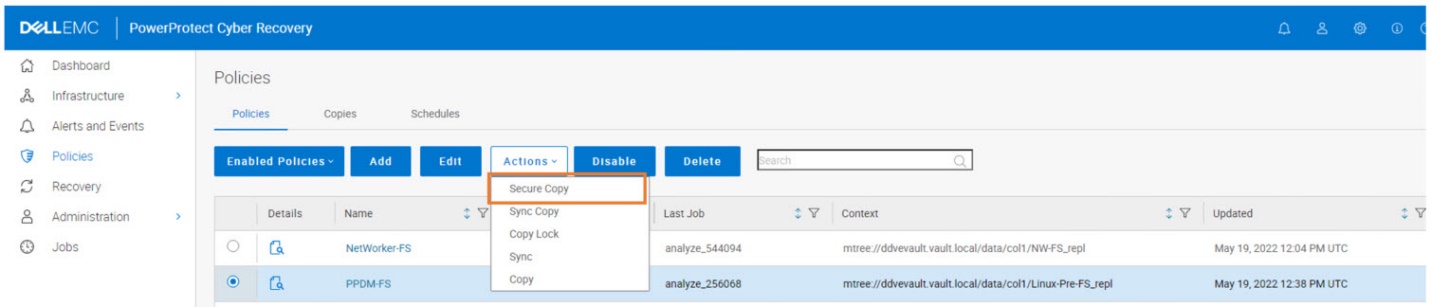
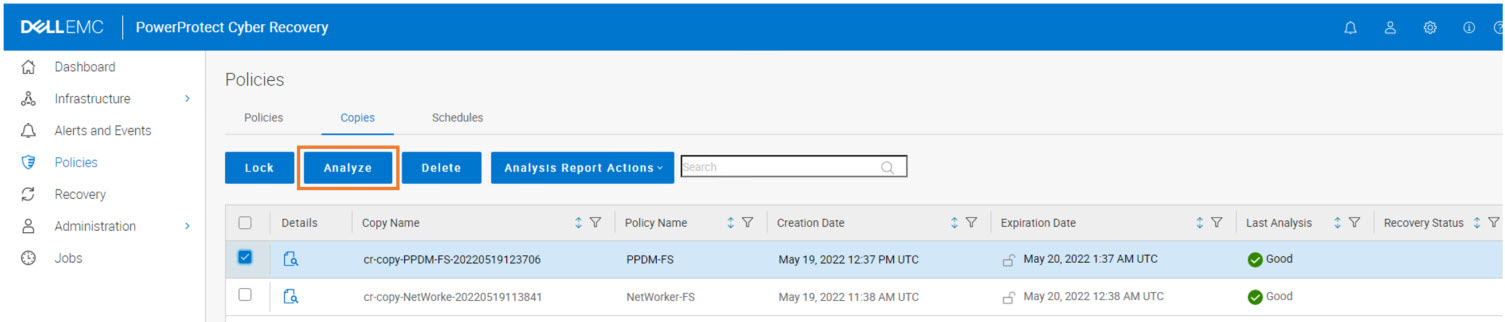
You can now simply select “Secure Copy Analyze” to combine both actions:
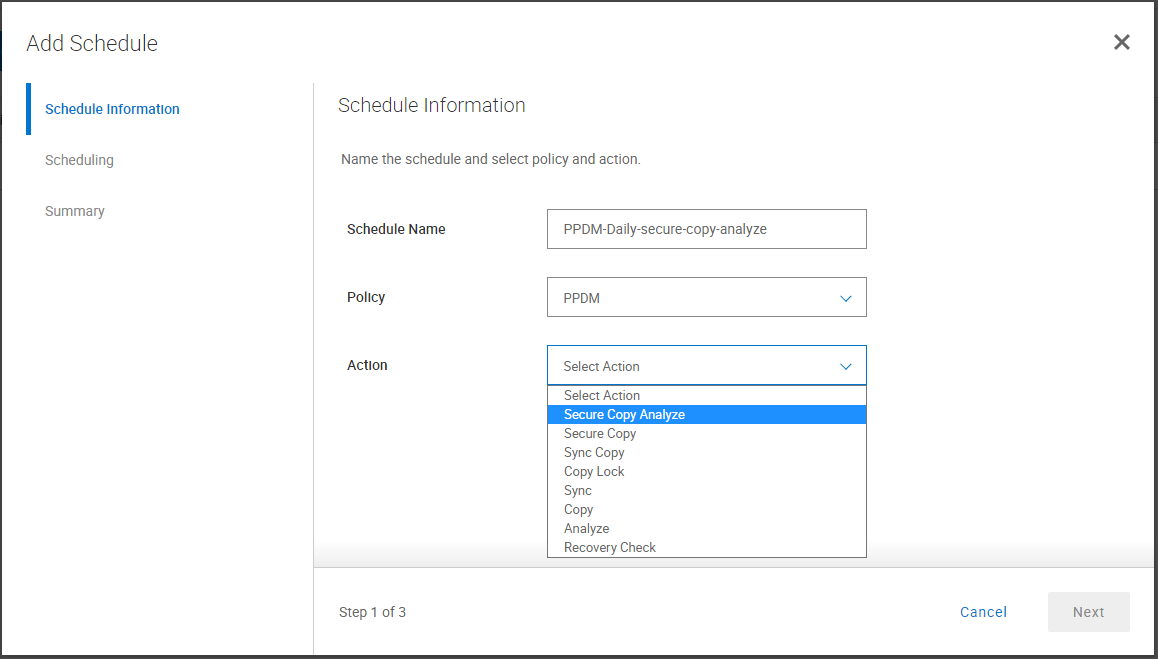
You can also change their two “Secure Copy” and “Analyze” schedules to a single “Secure Copy Analyze” schedule. This means that if you have multiple sites replicating to the vault or multiple policies, you’ll be able to reduce the number of schedules that you need to maintain.
These new features are exciting on their own, but why stop there?
PowerProtect Cyber Recovery 19.11 also allows you to deploy the Cyber Recovery solution on Azure! Here’s a simplified view:
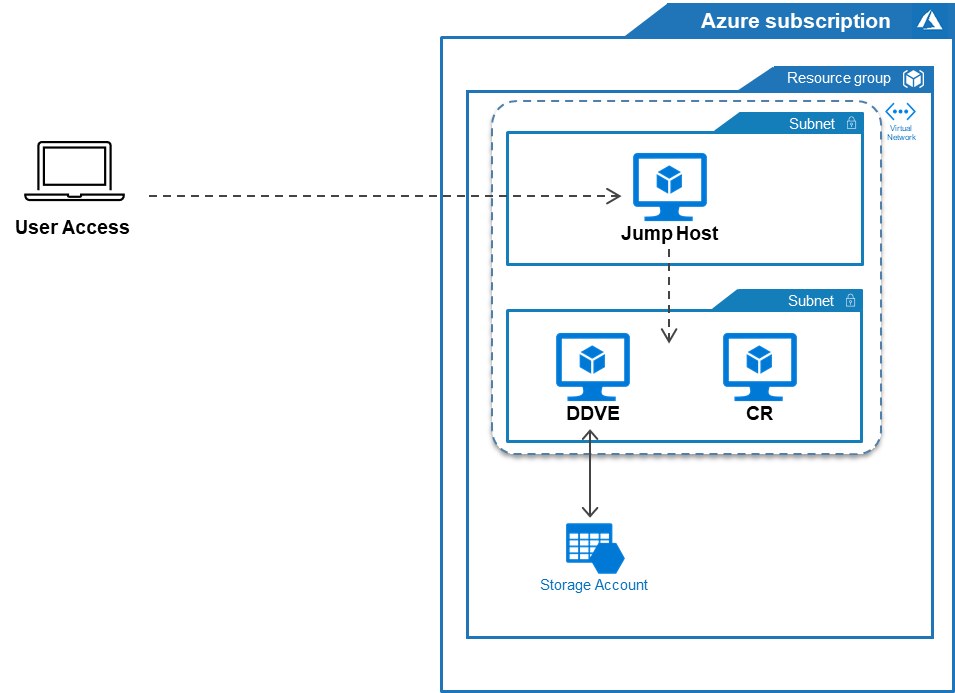
In this figure, notice that the Cyber Recovery components are the same as those in the on-premises and on AWS deployments. The Cyber Recovery host and a PowerProtect DD system are on an isolated subnet, and the Jump host is on another isolated subnet providing access to the Cyber Recovery server and the DDVE. (CyberSense is not supported yet on Azure.)
Note: Deploying PowerProtect Cyber Recovery in the cloud must be performed by Dell Technologies Professional Services.
Resources
Additional interesting resources can be found here:
Author: Eli Persin

Why Fortify with Modern Security and Zero Trust?
Thu, 26 Jan 2023 21:34:59 -0000
|Read Time: 0 minutes
Today’s infrastructure landscape is rapidly changing. Customers’ data is scattered — across cloud, multi-cloud, core datacenter, and edge. And with that comes a more challenging threat landscape. The security provisions you deployed yesterday may not be ready for today’s security reality. Cyberattacks can come from anywhere — inside and outside of your organization. This means that you must have a comprehensive and continuous security strategy that is cyber resilient and enables zero trust principles.
Why bother with a comprehensive approach like zero trust?
Cyber threats are real. And the damage caused by attacks can be costly and devastating. Likewise, regulatory pressures (from a compliance, financial, and liability perspective) that have come about as a result of these attacks are growing.
This, combined with the complexity of the modern IT infrastructure and the sophistication of today’s threat landscape, requires a trust model that validates at every point in the IT environment before permissions are granted.
Zero trust is an approach to security that assumes that every part of your infrastructure is at risk — requiring continuous verification and validation. While the purpose of this blog is not to talk in depth about what zero trust is, we do want to explain its validity given today’s threat landscape and explain how Dell Technologies’ cyber-resilient architecture is the foundation for the critical elements of a zero-trust environment.
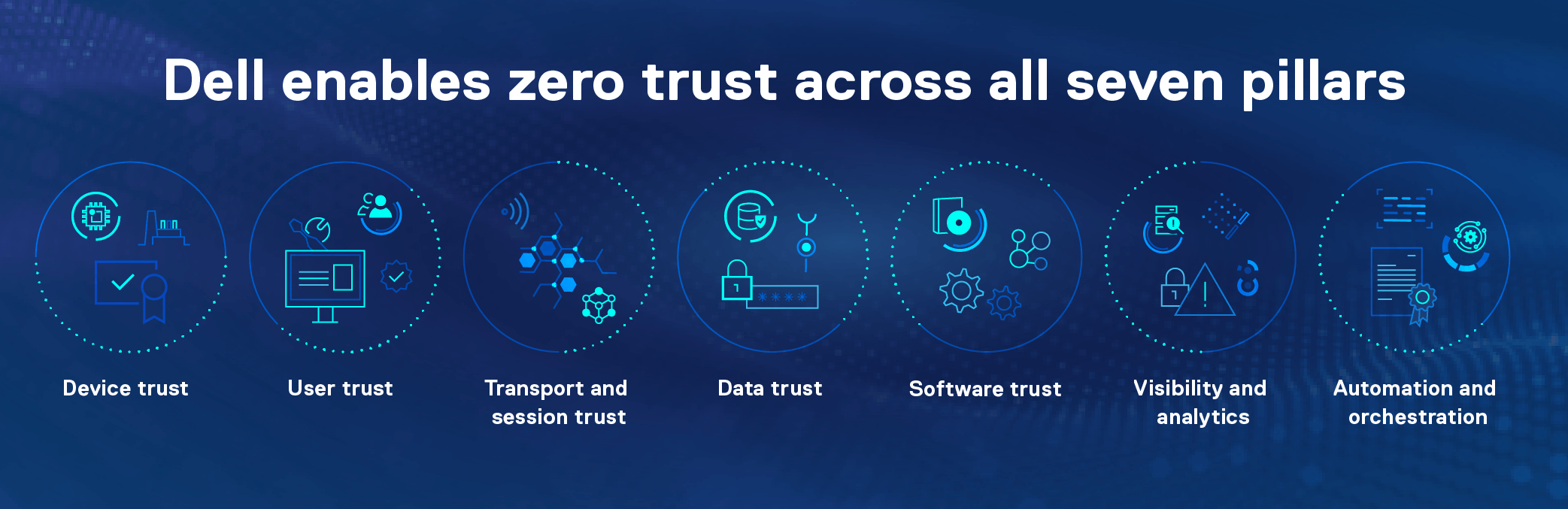
Learn more about how Dell provides broad coverage across these pillars in our Zero trust architecture infographic.
You might be wondering, why does zero trust have so many categories? The simple answer is that you need as complete and continuous coverage as possible across your infrastructure if you want your security efforts to be successful. For example, your organization might do encryption really well. But this doesn’t matter if you don’t have strong multifactor authentication to identify the users of that encrypted data. Your organization is only as secure as your weakest link, which is why focusing on all seven pillars is your best defense in combating threats.
While the ultimate goal is to keep attacks from coming in at all, rejecting them at the point of entry, that’s not always possible. The zero-trust model requires more refined validation at key intersections for verified trust, optimizing least privilege without impacting workload efficiency. However, if a breach does occur, the sphere in which they could do damage should be minimized, along with an enhanced ability to detect and remediate immediately. Dell Technologies’ cyber-resilient architecture, enhanced over many years, is the foundation for the critical elements of a zero-trust environment.
What is the value of having a cyber-resilient architecture?
In simple terms, cyber resiliency within your infrastructure is what helps minimize the exposure to attacks. Dell Technologies solutions are hardened and designed to help you protect, detect, and recover from cyberattacks.
Dell, of course, has been talking about its cyber-resilient architecture for a long time. What’s changed now, however, is that given the emerging threat landscape, we can see how zero trust goes hand in hand with a cyber-resilient architecture. And it’s why we’re continually making enhancements to our cyber-resilient architecture: to provide even greater visibility, risk reduction, and resilience — so that your infrastructure intrinsically supports a zero-trust approach.
We’ll explore cyber resiliency in more detail in a later blog. For now, you can find additional information about Dell’s cyber-resilient architecture in our infographic and video.
Why partner with Dell?
Dell creates the products and features to help you meet your zero-trust goals. We also watch the regulatory landscape to make sure that our solutions meet industry standards and exceed capabilities in the area of security. We do this through:
Processes: Delivering a cyber-resilient architecture requires security awareness and discipline at each stage of development. The Dell Secure Development Lifecycle (SDL), for example, outlines the set of activities required throughout the product lifecycle to promptly build security resiliency and consistent security capabilities into our products and respond to any security vulnerability.
Additional security solutions: In addition to embedding layered security into our products, we provide standalone security solutions focused on specific areas, like data protection. If data does get compromised, you want a backup system that enables business continuity and provides assurance that the backup itself hasn’t been compromised. Offerings like Dell PowerProtect Cyber Recovery and CyberVault enable a robust backup, including the use of Airgap and CyberSense to detect anomalies and mitigate potential problems that could compromise your data.
Simplification: Security controls are useless if they’re not being used. While Dell provides you with sophisticated security controls, we’ve also significantly simplified their use and deployment. Look for more information about “security complexity” in a later blog.
Supply chain security: At Dell, we’re also focused on personnel, operational, and supplier provisions for supply chain security. We have technologies and programs in place, like Secured Component verification that enable the verification of your components from the factory to your site.
Regulatory certifications: We closely monitor regulatory requirements around the world — and make sure our solutions contain the certifications (FIPS, USGv6, Common Criteria, and others) that matter to you. With this focus, we’re able to provide security controls that match emerging regulatory requirements, helping to keep your business secure and compliant.
This is just a glimpse of what Dell Technologies is doing in this space. As Cybersecurity Awareness month kicks off, please take time to read the follow-on blogs in this series and discover the different ways that Dell Technologies is working hard to protect your business.
Author: Craig Phelps

The power of cyber resiliency at your core
Thu, 26 Jan 2023 21:34:59 -0000
|Read Time: 0 minutes
At Dell Technologies, we often talk about how security is ingrained into our product DNA. What we mean is that security is never an afterthought — it’s never something that we build on after the product itself is complete.
Instead — and our Secure Development Lifecycle (SDL) is a key part of this — we continually design our products with past, current and future security threats in mind. And we supplement secure product development with external audits and continuous testing and evaluation to find and remedy vulnerabilities that do occur.
Dell’s commitment to customers
Attacks on the infrastructure layer, especially the firmware, are on rise. According to a Microsoft Security Signals report, more than 83% of enterprises have experienced at least one firmware attack in the past two years.
At Dell, we understand that securing the infrastructure layer is fundamental to protecting any IT environment against modern threats. Our cyber-resilient infrastructure has security built into every phase starting from the supply chain to the operation and eventual retirement of products. We are also committed to making sure any vulnerabilities or exposures found in the field, that could impact our products, get mitigated through rapid response on our end.
Let’s talk about how we secure our PowerEdge servers.
Cyber resiliency is key
Modern server platforms are highly complex, with hundreds of components — a lot of which require firmware for configuration and management of the component during the boot process and operation of the server.
Given the complexity of today’s platforms and the level of sophistication of cyberattacks, we recognize that it is not possible to prevent 100% of attacks. Some breaches are inevitable, especially when it comes to new devices and firmware, for example. Cyber resiliency — the ability to anticipate, withstand and recover from attacks — is therefore fundamental to surviving in this threat landscape.

At Dell, we use the NIST framework of Protect, Detect and Recover to guide our resiliency efforts. At the same time, the process of identifying and designing these capabilities is done through the zero-trust approach — with a focus on increasing the granularity of controls and checks in the systems — and by anticipating how our customers will want to use these capabilities while they are setting up their zero-trust IT environments and deployments.
Cyber resiliency built into PowerEdge
Dell PowerEdge servers offer cyber-resilient infrastructure by anchoring platform integrity to a silicon-based Root of Trust and using automated features to continuously protect the system during its operation.
Root of Trust: PowerEdge offers end-to-end boot resilience by enabling UEFI secure boot, which is anchored in our silicon-based platform Root of Trust. This immutable Root of Trust is the starting point of the chain of trust used to cryptographically authenticate the different pieces of firmware that get loaded on PowerEdge servers. Our secure boot helps to make sure that the firmware is coming from a trusted source and has not been tampered with in any way.
UEFI certificate customization: PowerEdge servers provide capabilities for complete customization of UEFI secure boot, giving system owners an option to avoid relying on third-party industry keys and industry certificate authorities. The NSA has recognized that fully customized UEFI secure boot offers the highest level of security and provides the best protection against threats. And it’s important to note that Dell was the first server vendor to provide these capabilities to customers.
CPU security
In addition to fully customizable UEFI secure boot, PowerEdge servers offer a complementary layer of protection against things like sleep attacks by enabling Intel Boot Guard and AMD Platform Secure Boot features. These features add robustness to the chain of trust process by verifying the firmware before it gets executed on the processor and eliminating attacks between time of check by UEFI secure boot and time of use of the firmware on the processor.
Drift detection: Beyond assuring boot integrity, PowerEdge can also lock down the system configuration and automatically detect drift in firmware versions and the configuration of the system. If drift is detected, PowerEdge can respond by automatically initiating rollback of the firmware and OS to a “known good” version.
Through these features, PowerEdge servers offer end-to-end boot resilience by protecting against attacks on the firmware, detecting any ongoing attack on firmware and/or system configuration, and automatically recovering from attacks by rolling the system configuration and firmware back to a safe, verified version. What’s also important to note is that this happens with no manual intervention at machine speed, which is critical for minimizing system downtime.
But Dell goes even further
When it comes to the firmware, it's important to reiterate that Dell is committed to providing rapid response and mitigation to CVEs. What you might not know is that the majority of attacks occur because known vulnerabilities are not being patched in the field.
We don’t want to leave our customers vulnerable, which is why we’re always working to improve our service-level agreements (SLA) for updates and patches that help mitigate new threats as quickly as possible.
Resiliency is just one small facet of Dell’s overall security stance. Take time to learn more about what we’re doing to protect your devices, your data, and your business. PowerEdge, like the rest of the Dell fleet of products, has a broad feature set that goes beyond resiliency — and is capable of meeting your risk tolerance requirements and regulatory and compliance needs.
Find additional resources on Dell Technologies Info Hub.


