Home > Integrated Products > VxBlock 1000 and 3-Tier Platform Reference Architectures > White Papers > Reference Architecture: Dell EMC PowerProtect Cyber Recovery for Converged Infrastructure > Test configuration
Test configuration
-
The following figure shows the lab configuration used for Cyber Recovery testing with VxBlock 1000 Integrated Data Protection with one exception. The lab environment did not include a firewall between the customer network and the Cyber Recovery network for the management data path. The Cyber Recovery vault was managed entirely from within the vault. For remote management of the Cyber Recovery vault, a firewall, as shown, is required to ensure a secure environment.
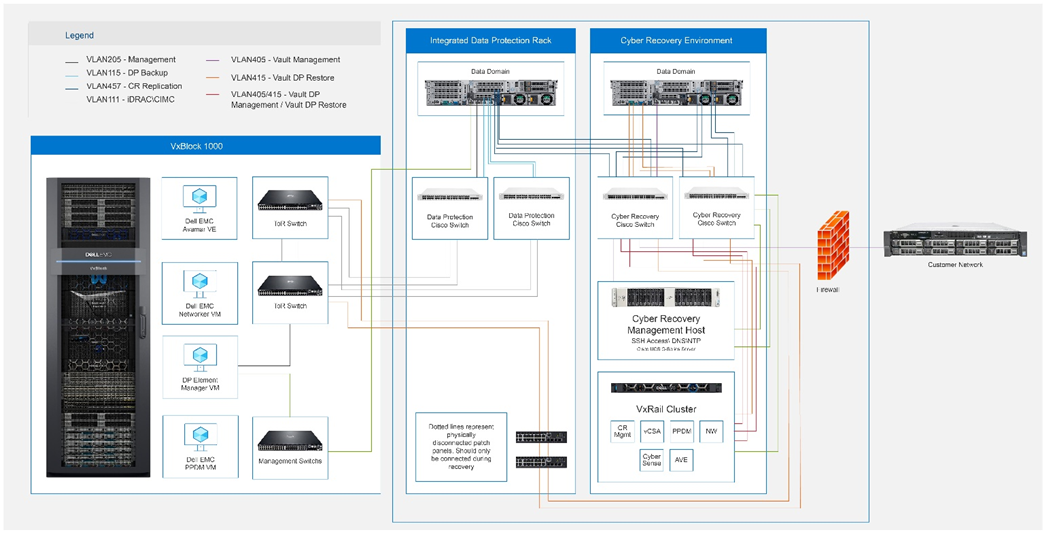
Figure 2. Lab configuration for Cyber Recovery testing
Note: This lab configuration is an example of a Cyber Recovery vault environment; do not implement this environment without engaging a DPS Sales Engineer (SE) and the BRDC to ensure a properly sized and secure Cyber Recovery vault environment. Engage a DPS SE early enough to determine the front-end data sizing for any Cyber Recovery solution. Possible design changes might have to be considered for the DPS backup application and CyberSense sizing requirements.
The VxBlock integrated data protection system is configured and integrated like a typical data protection backup integration. However, there is one key difference with the integration of Cyber Recovery; the production PowerProtect DD6900 system has an additional pair of 25 GbE IO modules that are configured for LACP and are used strictly for replication to the Cyber Recovery vault environment. These connections are made directly to the Cyber Recovery environment Cisco Nexus 93180YC-FX switches. By not connecting directly to the integrated data protection Cisco Nexus 93180YC-FX switches, you can avoid creating uplinks from the Integrated Data Protection switches to the Cyber Recovery Nexus switches to eliminate another possible attack vector.
As with the production DD6900 connections for production backup and restore operations, the connections for replication to the Cyber Recovery vault are configured as LACP hash XOR-L2L3 and are tagged with the Cyber Recovery replication VLAN ID. The interfaces on the Cyber Recovery Cisco Nexus 93180YC-FX switches are configured as a Virtual Port Channel (VPC) to provide both bandwidth aggregation and redundancy. The port channel is also configured to only allow the Cyber Recovery replication VLAN ID, which helps reduce the attack vector of the Cyber Recovery vault environment.
The Cyber Recovery vault DD9900 system includes two pairs of 25 GbE IO modules. Both pairs of 25 GbE IO modules connect directly to the Cyber Recovery Cisco Nexus 93180YC-FX switches and are configured as LACP hash XOR-L2L3. One virtual interface is used for Cyber Recovery restore, and is tagged with the Cyber Recover restore VLAN ID. The other virtual interface is used for Cyber Recovery replication and is tagged with the Cyber Recovery replication VLAN ID. The Cyber Recovery Cisco Nexus 93180YC-FX switch interfaces to which the DD9900 systems are connected are configured as VPCs to provide both bandwidth aggregation and redundancy. These port channels are also configured to only allow the respective VLAN IDs for Cyber Recovery restore and replication; this configuration also helps reduce the attack vector of the Cyber Recovery vault environment. For DD9900 management, the ethMa and iDRAC interfaces are both connected to the Cyber Recovery Cisco Nexus 93180YC-FX switches. This connection allows in-band and out-of-band management.
A three-node VxRail cluster is also deployed in the Cyber Recovery vault environment. Each VxRail node has four physical connections alternating between the two Cyber Recovery Cisco Nexus 93180YC-FX switches to provide for the vSphere ESXi host uplinks. The VxRail cluster has a dedicated vCenter virtual appliance to manage the VxRail data center, cluster, and vSAN. The Cyber Recovery management virtual appliance is also deployed to the VxRail cluster. For Cyber Recovery restore purposes, AVE, a CentOS Linux-based NetWorker Server virtual machine, and a PowerProtect Data Manager virtual appliance are also deployed and configured on the VxRail cluster according to the Dell EMC PowerProtect Cyber Recovery Product Guide. For analytics and analysis, a CentOS Linux virtual machine installed with CyberSense is also deployed to the VxRail cluster.
The Cisco UCS C220-M5 rackmount server is a bare-metal system deployed with the CentOS 7.9 Linux operating system. The Linux operating system is configured to provide both DNS and NTP services for the entire Cyber Recovery vault environment. These services are key to the successful deployment and configuration of the VxRail cluster.
