Home > Integrated Products > VxBlock 1000 and 3-Tier Platform Reference Architectures > White Papers > Reference Architecture: Dell EMC PowerProtect Cyber Recovery for Converged Infrastructure > Overview
Overview
-
Over the past three years of helping our customers protect their critical data and recover their businesses following a successful cyberattack or ransomware incident, we have found that there are three main common characteristics of a Cyber Recovery solution:
- Isolation—Physical (using a locked room on-premises or in an off-premises or cloud-based vault) and logical (data and management path or command and control access) separation of the Cyber Recovery vault from the attack surface of production and backup infrastructure
- Immutability—As defined by Dell Technologies, hardware and software, and additional controls that ensure that the original integrity, confidentiality, and availability of the vault data is preserved
- Intelligence—Application of innovative and comprehensive tools and analytics, machine learning, and AI within the security of the Cyber Recovery vault to identify potential cyber threats or corruption and to ensure that vaulted data is recoverable
It is significant that these three components work independently and collectively in an integrated solution to provide the maximum levels of security and protection for vaulted data. They provide the best possible chance to recover vaulted data with integrity and confidence if an attack penetrates the data center.
Solutions that offer one or two of these common characteristics as features of backup or disaster recovery (DR) products and services, while useful, cannot be expected to provide the same levels of protection of critical data when a sophisticated attack impacts production, backup, and perhaps DR.
Features such as storing backups in some immutable form provide an incremental amount of protection over nonimmutable backups. This feature alone does not withstand insider credentialed attacks or network time protocol (NTP) attacks. These NTP attacks trick many software-defined storage systems into releasing the retention period if cyber criminals tamper with the NTP setting to indicate falsely that the retention period has expired.
While intrinsic security provides a foundation for our overall security and cyberrelated standards across Dell Technologies, our Cyber Recovery solutions and services provide the highest levels of protection, integrity, and confidentiality for your most valuable data and critical business systems. Due to the most sophisticated cyber threats, we are not focusing on preventing ransomware or cyberattacks but on protecting critical data or applications and enabling you to recover those assets with integrity so that you can resume normal business operations with confidence.
Our Cyber Recovery solution protects the most critical data in a vault environment. Ideally, the Cyber Recovery vault is physically isolated – a locked cage or room – and is always logically isolated using an operational air gap. The Cyber Recovery vault components are never accessible from the production system. When the air gap is unlocked, access to the Cyber Recovery vault target system is extremely limited. This feature is a key to the maturity of our solution. The Cyber Recovery vault is not an extra data center but is usually located at the production or corporate data center.
The Cyber Recovery vault operates by using four basic steps:
- Data representing critical applications is synchronized through the air gap, which is unlocked by the management server, into the Cyber Recovery vault and replicated into the Cyber Recovery vault target storage. The air gap is then relocked.
- A copy of that data is created. Vault retention is configurable. Most customers keep about a month's worth of copies.
- The data is retention locked to further protect it from accidental or intentional deletion.
- Optionally, the CyberSense analytics engine analyzes the data.
Recovering data from the Cyber Recovery vault after a cyberattack or for recovery testing procedures is critical. There are several ways to perform a recovery. The following figure highlights the basic recovery steps:
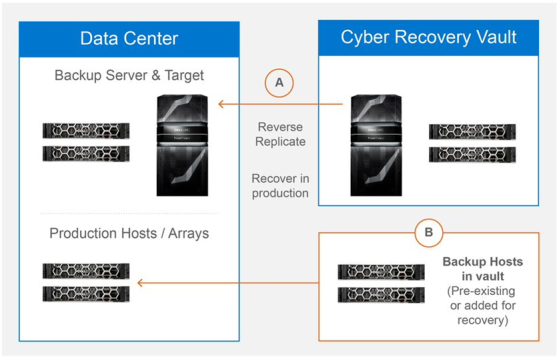
Figure 1. Basic recovery steps
The recovery steps include:
- Evaluate analytics results
- Select restore points
- Restore data with the original backup application, using the Cyber Recovery vault data and catalog
- Cleanse and update impacted applications as necessary
