Assets

Enhanced Installer Scripts to Protect Oracle Databases with PowerProtect Data Manager
Wed, 24 Apr 2024 17:14:52 -0000
|Read Time: 0 minutes
Our innovations and support for our customers never stop. We continue to provide extensive data protection support for Oracle databases with PowerProtect Data Manager, and the following installer script enhancements are now available with PowerProtect Data Manager version 19.14 onwards:
- Interactive single script execution to install or uninstall the Oracle RMAN agent and PowerProtect agent service as a root user
- Silent install or uninstall script using command line parameters to install or uninstall the Oracle RMAN agent and PowerProtect agent service as a root user.
Let’s dive in for more detailed information on these script enhancements.
Interactive single script execution to install the Oracle RMAN agent and PowerProtect agent service as a root user
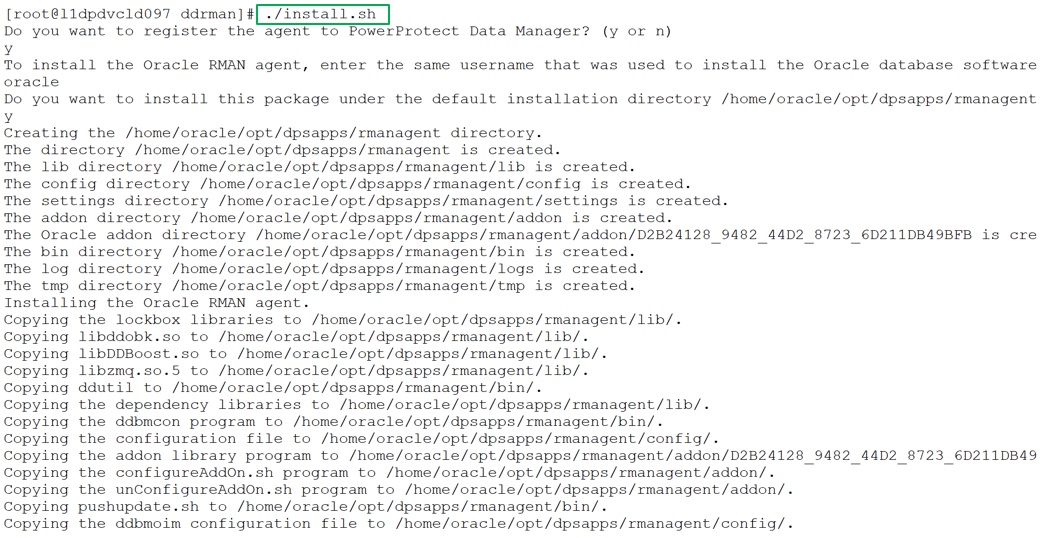
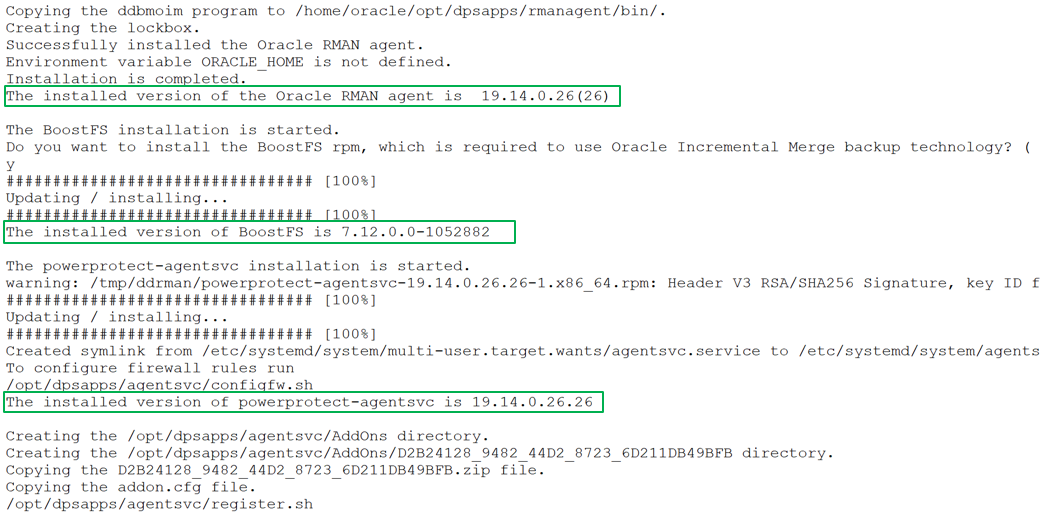
As a root user, you can use the install.sh script to install or update the Oracle RMAN agent, PowerProtect Agent Service, and BoostFS agent. This script also configures the Oracle add-on for PowerProtect Data Manager. These installations occur as a single script installation when run as a root user.
You can also run this script as a non-root user (Oracle User) to install the Oracle RMAN agent only.
The install.sh script guides you through the installation process and requests input, where required, as shown in the following example installation:
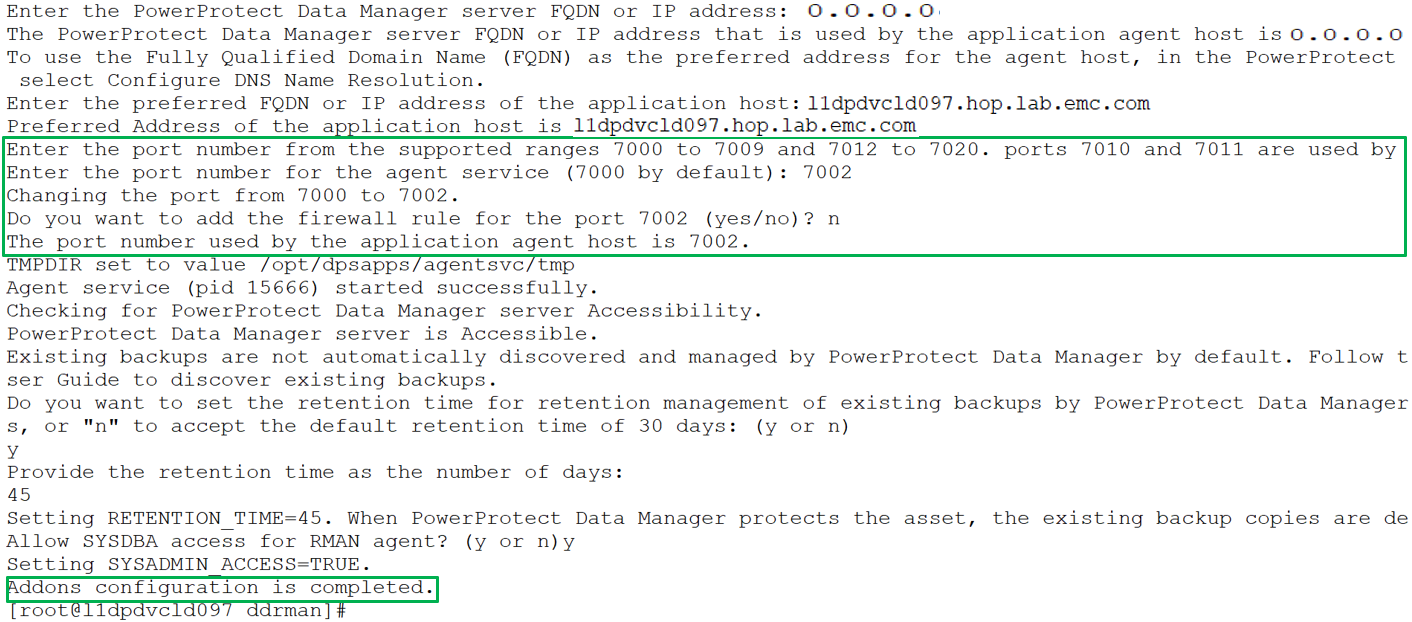
You can specify the preferred FQDN or IP address of the Oracle RMAN agent host and the port to be used for communication between the Oracle RMAN agent and PowerProtect Data Manager. The specified port must be from the supported port ranges 7000 to 7009, and 7012 to 7020. The ports 7010 and 7011 are used by the agent service message bus.
Note: If you do not specify a port number, the default port 7000 is used as the PowerProtect Data Manager communication port.
Note: Run install.sh -h or install.sh --help to obtain more information about the script operation.
Silent install using command line parameters to install the Oracle RMAN agent and PowerProtect agent service as a root user
You can include multiple options in the install.sh command to perform a silent installation of the RMAN agent, PowerProtect agent service, and BoostFS agent, including add-on configurations. The install.sh script accepts command line parameters and environmental variables and the installation can run automatically without user interaction. Run install.sh -h or install.sh --help to see more information about the command line parameters and environmental variables.
For example, the following command installs and registers the Oracle RMAN agent with system administrator privileges, installs the PowerProtect Data Manager agent, and BoostFS package. The command options specify the preferred agent host address, communication port, and configuration of the firewall exception rule. It also specifies the retention time for Oracle RMAN agent backups.
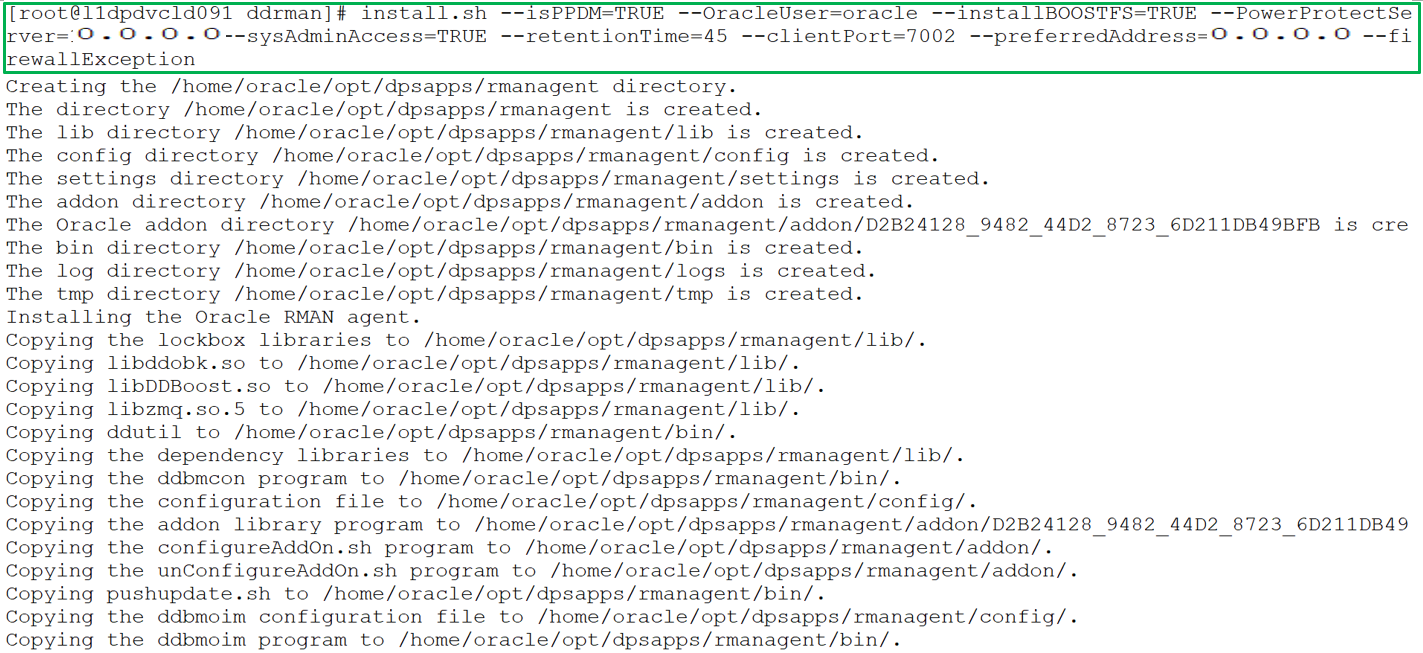
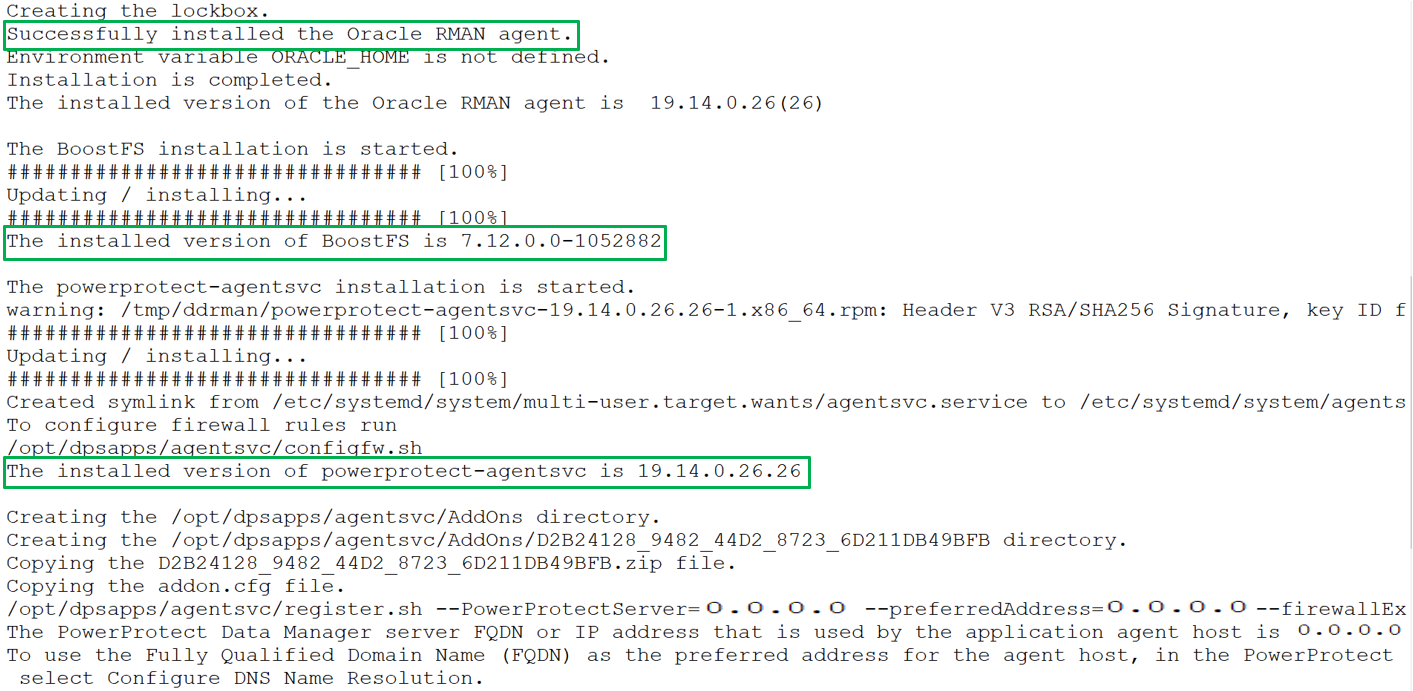
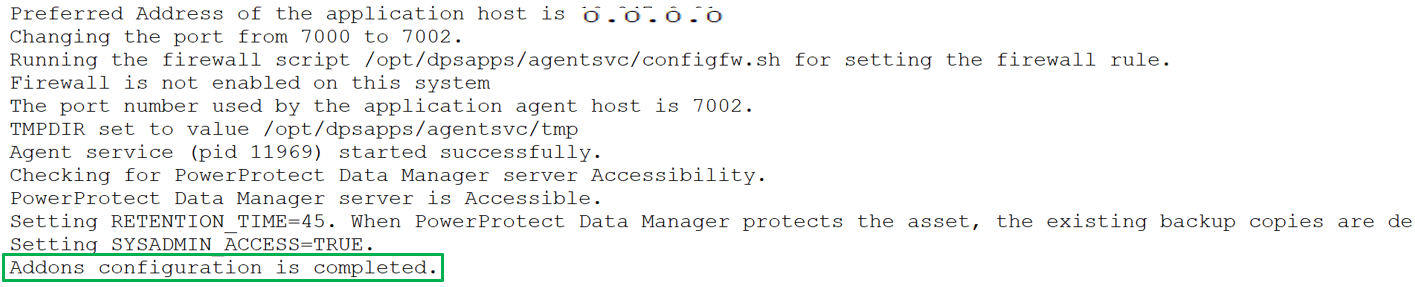
Uninstall both Oracle RMAN agent and PowerProtect agent service as a root user
You can run the uninstall.sh script as a root user to uninstall both the Oracle RMAN agent and PowerProtect Data Manager agent in the same uninstallation session. The script also unconfigures the Oracle addons. The script can guide you through the uninstallation process but can also accept environmental variables to complete automatically the uninstallation process without user interaction.
The following example shows the sample uninstall script executed by a root user:
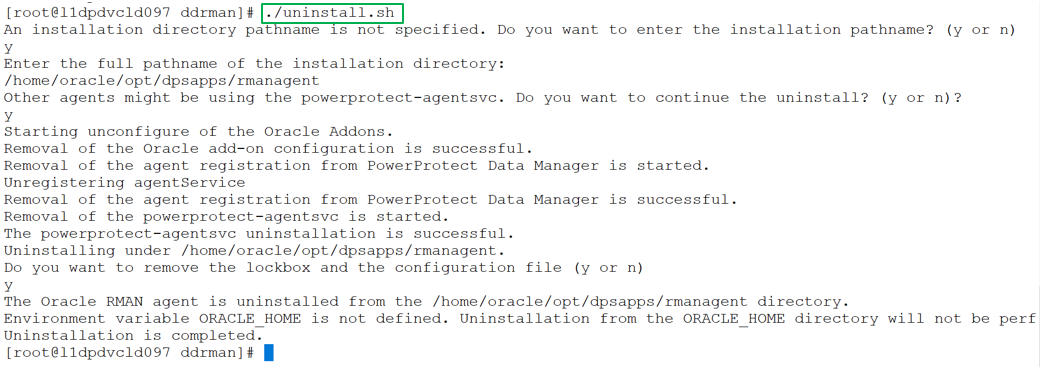
Notes:
- If other agents are installed on the application host, it is recommended to provide "n" for the prompt "Other agents might be using the powerprotect-agentsvc. Do you want to continue the uninstall?”
- Run uninstall.sh -h or uninstall.sh --help to obtain more information about the script operation.
With this efficient script enhancement, install, uninstall, and update operations can be done hassle-free as part of Oracle database protection.
For more details about Oracle database protection enhancements with Data Manager version 19.14, see our technical white paper PowerProtect Data Manager: Oracle RMAN Agent Backup and Recovery.
Author: Vinod Kumar Kumaresan, Principal Engineering Technologist, Data Protection Division

Smart Scale for Dell PowerProtect Appliances, Part I: Innovative Technology to Manage Multi-Exabyte Data
Wed, 24 Apr 2024 17:12:31 -0000
|Read Time: 0 minutes
In its recent Global DataSphere Forecast 2021—2026, IDC predicts that, over the next 5 years, data will grow at a compound annual growth rate (CAGR) of 21.2% and reach more than 221,000 exabytes by 2026[1]. Storing large amounts of data is just one issue; you must protect it as well. Managing an organization's data can be challenging, but it has become even more challenging as cyberattacks are on the rise. When budgets are tight, the burden of protecting data becomes even greater.
With more work on your plate and higher service levels to meet, you might find yourself struggling to keep up with these challenges, which are underpinned by the fact that organizations must often manage multiple data centers and cloud environments. Each data center almost inevitably ends up with a protection storage infrastructure with multiple appliances. These appliances are expanded, upgraded, and retired over time to accommodate new evolving workloads. There is also the challenge of optimizing capacity and performance. This can be a difficult task, but Dell Technologies is committed to help organizations overcome some of these challenges.
Introducing a new technology: Smart Scale for PowerProtect appliances
Keep pace with data growth. Reduce complexity by managing multiple appliances as a single pool of resources through a unified namespace. Pool up to 48 PB of usable capacity, 3 EB logical capacity with typical deduplication rates.
What is Smart Scale?
PowerProtect DD Management Center (DDMC) is a scalable, virtual system-based solution for centralized management of multiple PowerProtect DD series appliances. DDMC is composed of browser-based pages and is installed and runs on a VMware platform or compatible cloud service. Smart Scale is a new feature in DDMC that enables you to group multiple PowerProtect DD systems into a system pool, providing a layer of abstraction between your client's protection policies and the ultimate destination of the client's protected data. Smart Scale simplifies capacity management across multiple DD series appliances in a data center. Analytics provide capacity insights and actionable recommendations for capacity addition and placement, and help to identify unexpected changes.
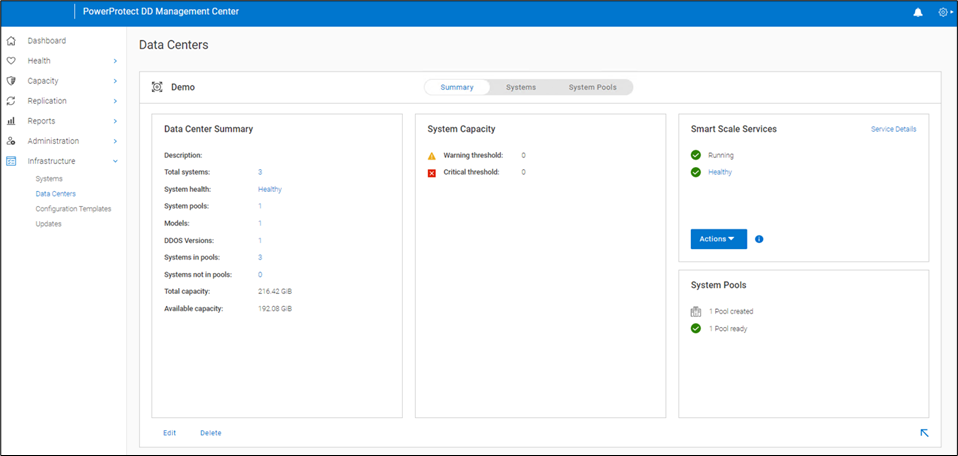
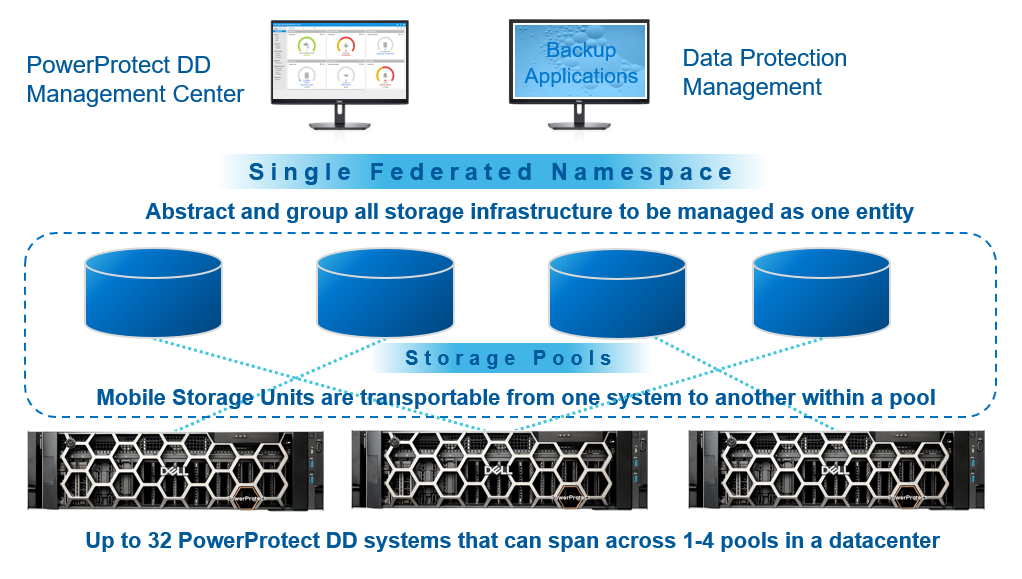
By enabling Smart Scale services from DDMC, the Smart Scale architecture pools together a set of DD series appliances into a group under the data center in which they are coordinated with each other for space balancing. Smart Scale supports up to 32 systems in a system pool and four system pools in a data center.
As protection policies are created, a system pool (rather than a specific system) can be specified as the targeted protection storage. The underlying placement of mobile storage units (MSUs) to appliances can remain transparent to the data protection client. This abstraction helps to provide capacity management and optimal storage unit placement capabilities for the customer without making risky and disruptive changes to the infrastructure. With this new modern approach to management, you can optimize global capacity utilization and deduplication, provide workload balancing to optimize SLAs, and enable easy upgrade or replacement of individual systems in the infrastructure.
How does Smart Scale work?
Smart Scale enhances the traditional storage unit construct, allowing the creation of MSUs that are transportable from one DD series to another within a system pool, making data consolidation and data redistribution straightforward and practical. Smart Scale services perform the actual placement of the backups to one of the DD series appliances in the system pool. The services then seamlessly redirect the backup software, eliminating the need for the backup administrator to modify backup policies with the risks involved when placements are changed. Smart Scale also uses mobile boost users (MBU) that move with the storage unit. This ensures continued secure access without administrative overhead.

Benefits of Smart Scale
Smart Scale simplifies enterprise infrastructure management and provides more scale efficiency than ever before. It includes the following benefits:
- Optimized capacity consumption.
- Simplified capacity management across multiple DD series appliances.
- Maximized deduplication among multiple storage units used in concert.
- Improved load balancing across multiple DD series appliances and more efficient distribution of workloads.
- Heightened ability to meet and surpass data protection SLAs.
- Nondisruptive addition or retirement of DD series appliances.
- Analytics that provide capacity insights and actionable recommendations for capacity additions, placements, and relocations.
- Support for Data at Rest Encryption (D@RE). A system pool can have a mix of encrypted and non-encrypted systems.
How do I get started with Smart Scale?
You can deploy Smart Scale into existing DD series environments using DDMC. The traditional backup operations co-exist with the new Smart Scale capability and the operations that system pools and MSUs support. Smart Scale services are deployed from DDMC on a VMware ESXi platform.
DDMC with Smart Scale services provides:
- Namespace redirection
- Capacity projection insights and recommendations
- Storage unit placement and nondisruptive migration
- Performance analytics
Smart Scale supports DD9900, DD9400, DD6900, and DD6400 models with DDOS 7.8 and later. DDMC must be upgraded to 7.8 or later but supports managing a mixed DD series appliance infrastructure that includes DD systems that are not Smart Scale capable. Smart Scale also supports PowerProtect DD Virtual Edition (DDVE) starting with DDMC version 7.11, where only on-premises DDVE deployed on VMware ESXi is supported. However, the DDOS version must be 7.11 or later. With DDVE support for Smart Scale, a mixture of physical PowerProtect DDs and DDVEs in a system pool is supported.
Data protection software that supports Smart Scale integration includes Dell PowerProtect Data Manager, Dell NetWorker, and Veritas NetBackup.
For the next installments in our Smart Scale blog series, see the following blog posts:
- Smart Scale for Dell PowerProtect Appliances, Part II: Architecture Deep Dive
- Smart Scale for Dell PowerProtect Appliances, Part III: MSU Migration, Replication, Recoverability, and Security
Additional resources for Smart Scale
- Dell PowerProtect DD series appliances
- Smart Scale for PowerProtect Appliances – Technical white paper
- Dell PowerProtect DD Management Center Interactive Demo
Authors:
Vinod Kumaresan (LinkedIn)
Sonali Dwivedi (LinkedIn)

Dell PowerScale: Data Protection with Dell NetWorker using NDMP
Fri, 23 Feb 2024 22:05:51 -0000
|Read Time: 0 minutes
NetWorker for PowerScale data protection
Dell NetWorker is an enterprise-class cross-platform data protection software solution for file servers, application servers, and database management systems across the network. NetWorker supports a wide range of data protection options, including Network Data Management Protocol (NDMP) support for NAS storage devices. Dell PowerScale NAS storage integration with NetWorker software provides esteemed data protection and recovery capabilities for enterprises of all sizes in a secure way.
NetWorker software uses NDMP functionality to enable access to storage in a heterogeneous network environment. NDMP uses TCP/IP to control the movement of the data and specifies various device drivers to store the data on devices.
Three main components support NDMP data operations with the NetWorker software: NDMP Data Server (PowerScale), NDMP Tape Server (the host with the backup device to which NetWorker writes the NDMP data), and the Data Management Agent or DMA (in which the NetWorker server is the DMA).
NDMP Features with Dell NetWorker
Multistreaming
NetWorker 9.0.1 and later supports multistreaming for up to 32 streams for Isilon OneFS 8.0 and later backups. NetWorker uses the client parallelism value that is defined for a PowerScale client to determine how many backups run concurrently.
IPv6
NetWorker storage nodes support IPv6 communications with a NetWorker server. By default, NDMP backup and recovery operations use IPv6 to create the data connection between the NDMP data server and mover server.
Checkpoint restart
The PowerScale filers create a snapshot of the file system before the backup. The save set is generated from the snapshot.
Volume Based Backup (vbb) supports
Data Access in Real Time (DART) version 5.5 and later.
Direct Access Recovery (DAR) and Dynamic Direct Access Recovery (DDAR)
DAR and DDAR send file information from the NAS filer to the NetWorker server.
Methods to configure the NDMP Data Server and the NDMP Tape Server to perform backups and recoveries
NDMP local backup (Direct-NDMP)
In an NDMP local backup (Direct-NDMP), the NDMP Data Server (NAS) sends data to a locally attached tape device or library.
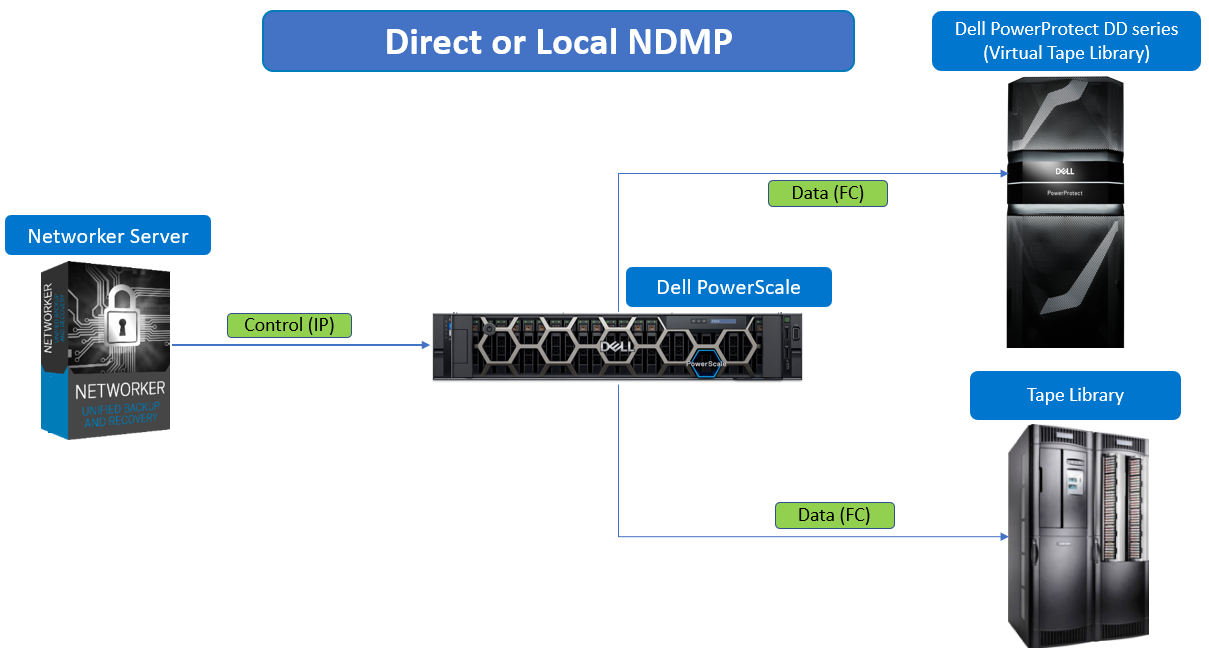 Figure 1. NDMP local backup (Direct-NDMP)
Figure 1. NDMP local backup (Direct-NDMP)
NDMP backups to non-NDMP devices (NDMP-DSA)
NetWorker software writes NDMP data to non-NDMP devices, including tape, virtual tape, AFTD, and Dell PowerProtect DD series appliances. A backup of NDMP data to a non-NDMP device is performed in one of two ways:
- NDMP data sent to non-NDMP devices that are local to the NetWorker server
- NDMP data sent to non-NDMP devices that reside on a NetWorker storage node
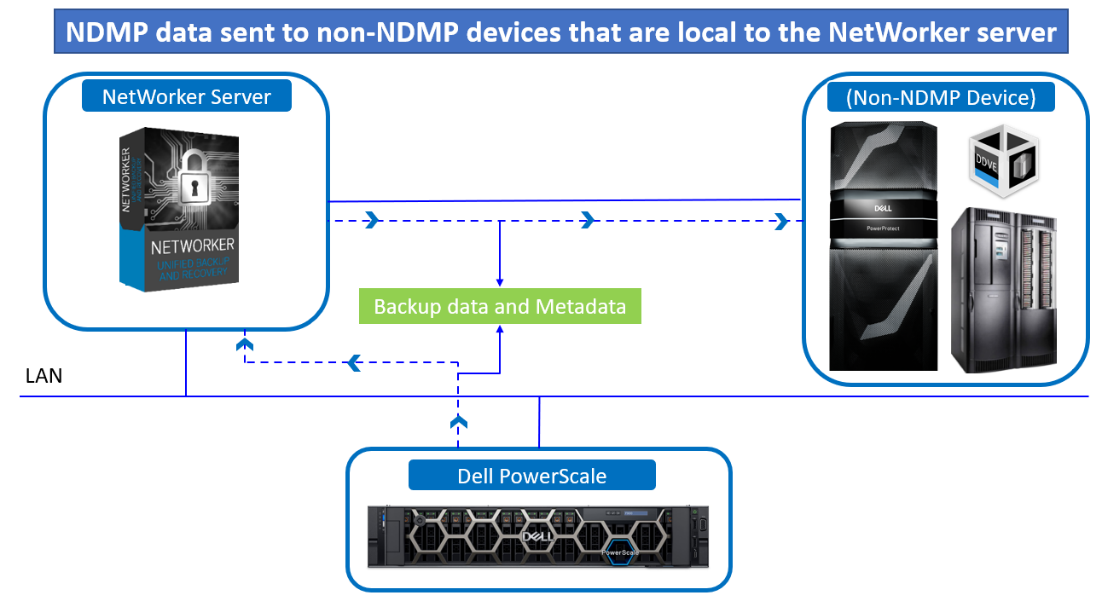 Figure 2. NDMP data sent to non-NDMP devices that are local to the NetWorker server
Figure 2. NDMP data sent to non-NDMP devices that are local to the NetWorker server
NDMP data sent to non-NDMP devices that are local to the NetWorker servers has the following characteristics:
- The backup data traverses the network between the NetWorker server and the NDMP data server.
- The metadata, the NDMP control information, and the file history (FH) remains local to the NetWorker server and still traverse the network.
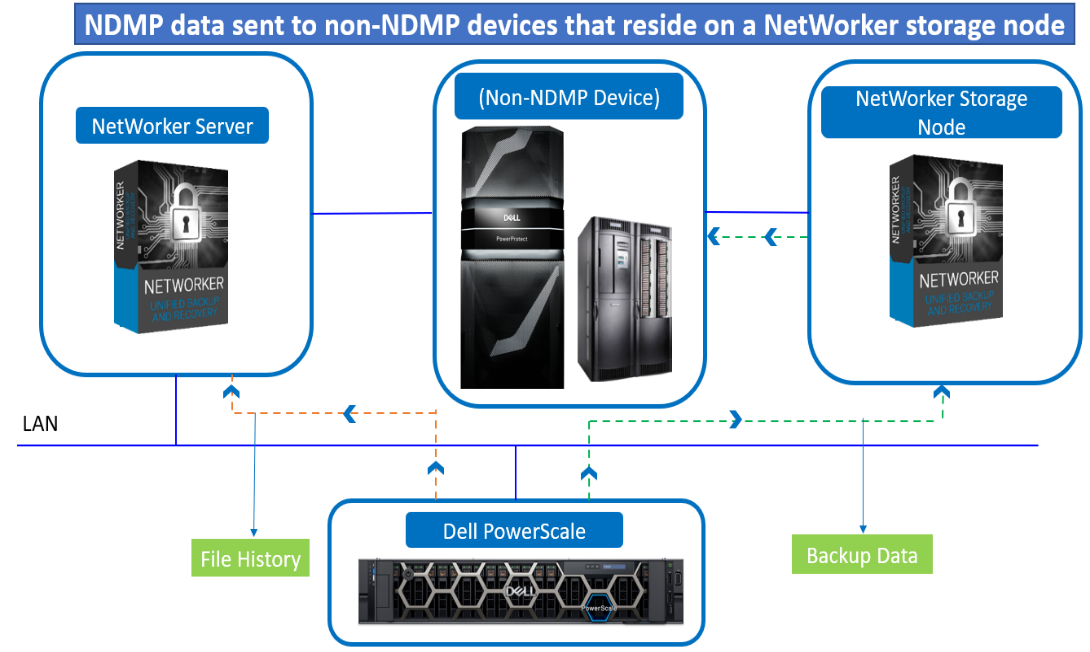 Figure 3. NDMP data sent to non-NDMP devices that reside on a NetWorker storage node
Figure 3. NDMP data sent to non-NDMP devices that reside on a NetWorker storage node
NDMP backups can be configured to write data to a NetWorker storage node in one of two ways:
- Immediate save (nsrdsa_save runs on storage node)
- Non-immediate save (nsrdsa_save runs on NetWorker Server)
Immediate save (nsrdsa_save runs on storage node)
The nsrdsa_save backup command runs on the NetWorker storage node. The NetWorker software uses TCP/IP and shared memory to communicate between the nsrdsa_save and nsrmmd processes.
Non-immediate save (nsrdsa_save runs on NetWorker Server)
By default, NDMP backups to a non-NDMP device use non-immediate save. When configuring an NDMP backup to use non-immediate save, the following actions occur:
- The nsrdsa_save backup command runs on the NetWorker server.
- The nsrdsa_save process uses TCP/IP to read the data in a local buffer.
- The nsrdsa_save process transmits the data to the nsrmmd process on the storage node.
- The nsrmmd process writes the data to the storage device.
Three-party backup
A three-party or three-way backup sends NDMP data to an NDMP Tape Server, however the NDMP Data Server and the NDMP Tape Server are not the same physical host.
There are two main types of three-party backups:
- In the first scenario, NetWorker sends the NDMP data to non-NDMP devices (NDMP-DSA). The NDMP Data Server and the NDMP Tape Server reside on different physical hosts. The NDMP Tape Server is always a NetWorker Server or a NetWorker Storage Node. Hence, NDMP-DSA is also a three-way NDMP backup.
- In the second scenario, NetWorker sends NDMP data to NDMP devices. The data flows from the NDMP Data Server to the NDMP Tape Server and then to a library that is locally attached to the NDMP Tape Server. In this configuration, the NDMP save sets cannot be archived
Dynamic drive sharing
Dynamic Drive Sharing (DDS) is a feature that provides NetWorker software with the ability to recognize shared physical tape drives.
DDS enables NetWorker software to perform the following operations:
- Skip the shared tape drives that are in use
- Route the backups or recoveries to other available shared tape drives
Benefits of DDS
Enabling DDS on a NetWorker system provides these benefits:
- Reduces storage costs
- Reduces LAN traffic
- Provides fault tolerance
- Provides configuration over a greater distance
References
Author: Vinod Kumaresan

Dell PowerScale: Data Protection with Dell Avamar NDMP Accelerator
Fri, 23 Feb 2024 22:02:09 -0000
|Read Time: 0 minutes
Dell Avamar for PowerScale Data Protection
Dell Avamar provides fast, reliable NAS system backup and recovery through the Avamar NDMP Accelerator, dramatically reducing backup times and the impact on NAS resources and allowing for an easier and faster recovery. The NDMP accelerator is available as both a virtual and hardware appliance. The fast-Incremental software architecture provides an efficient solution to protect High-Density File Systems (HDFS).
To back up and restore data residing on NAS systems, Avamar uses a device called an Avamar NDMP Accelerator, hereby referred to as the accelerator. The accelerator is a dedicated Avamar server node that functions as an Avamar client. The accelerator uses NDMP to interface with and access NDMP-based NAS systems.
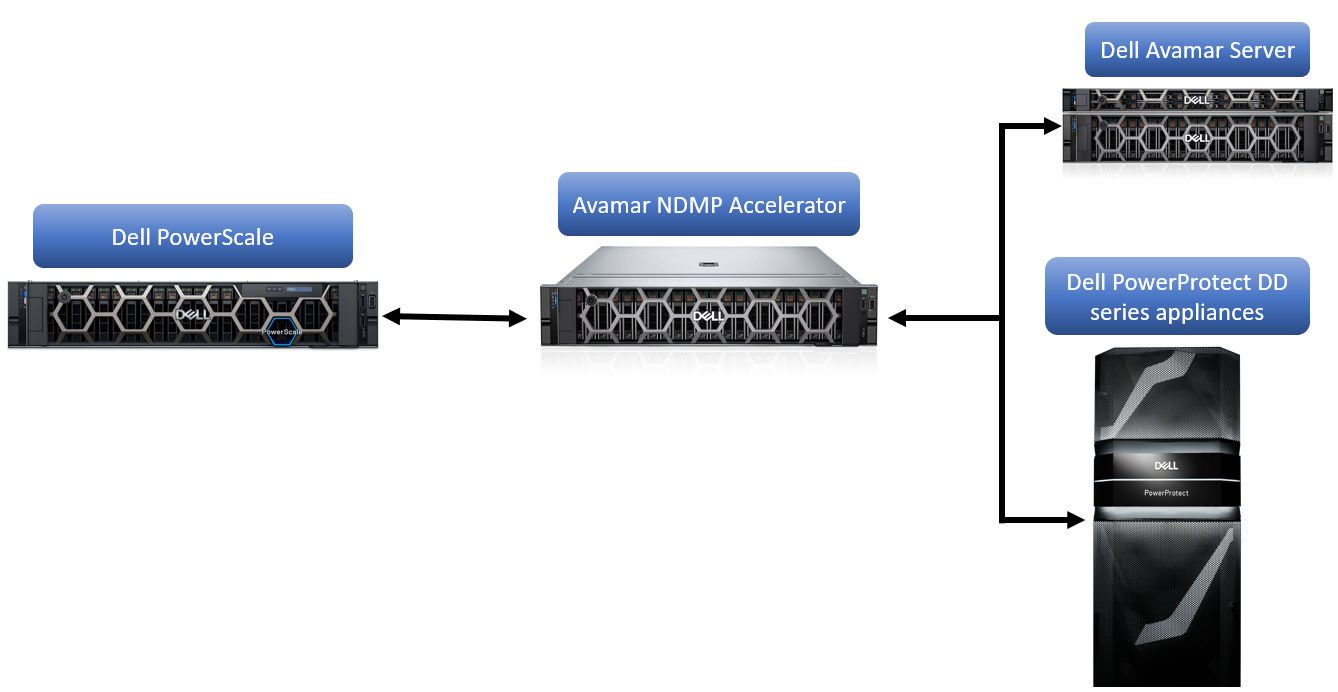 Figure 1. PowerScale Data Protection with Avamar
Figure 1. PowerScale Data Protection with Avamar
Data from the NAS system is not stored on the accelerator. The accelerator performs NDMP processing and real-time data deduplication and then sends the data directly to the Avamar server.
The accelerator can be connected to either a Local Area Network (LAN) or Wide Area Network (WAN) with respect to the Avamar server. However, to ensure acceptable performance, the accelerator must be located on the same LAN as the NAS systems.
On-demand and scheduled NAS system backups can be performed with the accelerator:
- Using Avamar Administrator or the Avamar Management Console Command Line Interface (MCCLI), both on-demand and scheduled backups can be performed.
- Using the avndmp command line interface, on-demand backups can be performed.
Benefits of using Avamar for NAS device data protection
Multiple NAS systems with one accelerator
Single accelerator can support more than one NAS system.
Multiple simultaneous data streams
NDMP plug-ins have a Maximum Concurrent Data Streams setting to control the maximum number of simultaneous NDMP data streams that can be allocated to each NAS system backup or restore operation.
PowerProtect DD support
Backups can be stored on either the Avamar server or a PowerProtect DD system. Backup metadata is stored on the Avamar server.
PowerScale SmartConnect support
Avamar backup data can be stored or restored from a backup to an PowerScale cluster with SmartConnect configuration.
Avamar Installation Manager
Avamar 7.4.x and later versions install the Avamar Installation Manager on the NDMP accelerator node.
Year 2038
Avamar 19.2 and later server subsystems support backup retention until February 2106. However, for earlier releases, due to the signed 32-bit integer time format of UNIX and Linux operating systems, the Avamar server subsystems will support backup retention until January 2038 and therefore cannot restore backup after this date.
NDMP plug-in options for backup
- Maximum concurrent data streams: Maximum number of streams that can be processed concurrently
- Filer dump mode: Prefer Incremental but do a Full if required, force a level 0 dump, and force an incremental (level 1) dump
- Backup label: Custom descriptive label for the backup
- Option to store backup on Dell PowerProtect DD series appliances: Store the backup on a PowerProtect DD instead of the Avamar server
- Encryption method to PowerProtect DD: Encryption method for data transfer between the client and the PowerProtect DD system during backup
- Run user-defined script at start and end of backup: Script to be run before and after each backup target is processed
- PowerScale Browse username: User account for Dell PowerScale™ OneFS™ with privileges for browsing the file system
- PowerScale Browse password: Password for the Dell PowerScale™ OneFS™ user account
NDMP plug-in options for restore
- Maximum concurrent data streams: Maximum number of streams that can be processed concurrently
- Encryption method to PowerProtect DD: Encryption method for data transfer between the client and the PowerProtect DD during restore
- Run user-defined script at start and end of restore: Script to be run before and after each restore target is processed
Virtual NDMP (vNDMP) accelerator node
A customer can leverage the vNDMP option to protect the NAS workload.
The vNDMP option offers the customer a complete user experience from deploying the OVA to registering the NDMP client to the Avamar Server to integrating the vNDMP client instance with the NAS environment. Hence, the user will no longer be required to manually perform the activity.
Upgrading the accelerator software
The accelerator software upgrade workflow contains an upgrade to the SLES 12 SP5 operating system. Avamar 19.4 supports upgrading the NDMP accelerator node from OS SLES 11 SP1 on the Gen4S hardware platform.
References
Author: Vinod Kumaresan

Using Dell PowerFlex and Google Distributed Cloud Virtual for Postgres Databases and How to Protect Them
Fri, 03 Nov 2023 23:27:04 -0000
|Read Time: 0 minutes
Did you know you can get the Google Cloud experience in your data center? Well now, you can! Using Google Distributed Cloud (GDC) Virtual and Dell PowerFlex enables the use of cloud and container workloads – such as Postgres databases – in your data center.
Looking beyond day one operations, the whole lifecycle must be considered, which includes assessing how to protect these cloud native workloads. That’s where Dell PowerProtect Data Manager comes in, allowing you to protect your workloads both in the data center and the cloud. PowerProtect Data Manager enhances data protection by discovering, managing, and sending data directly to the Dell PowerProtect DD series virtual appliance, resulting in unmatched efficiency, deduplication, performance, and scalability. Together with PowerProtect Data Manager, the PowerProtect DD is the ultimate cyber resilient data protection appliance.
In the following blog, we will unpack all this and more, giving you the opportunity to see how Dell PowerFlex and GDC Virtual can transform how you cloud.
What is Google Distributed Cloud Virtual?
We will start by looking at GDC Virtual and how it allows you to consume the cloud on your terms.
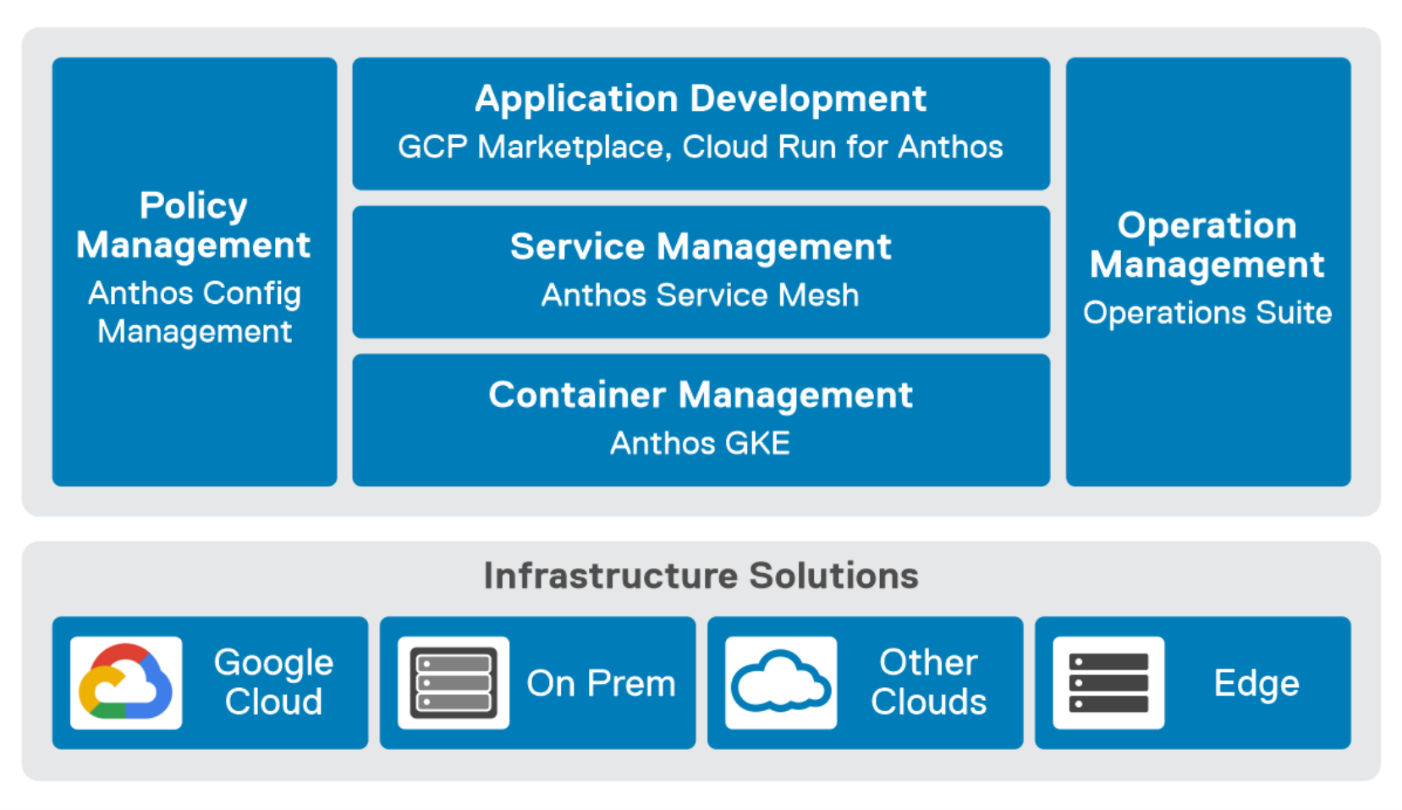
GDC Virtual provides you with a consistent platform for building and managing containerized applications across hybrid infrastructures and helps your developers become more productive across all environments. GDC Virtual provides all the mechanisms required to bring your code into production reliably, securely, and consistently while minimizing risk. GDC Virtual is built on open-source technologies pioneered by Google Cloud including Kubernetes and Istio, enabling consistency between cloud and on premises environments like PowerFlex. Anthos GKE (on GCP and on-prem), Anthos Service Mesh, and Anthos Config Management are the core building blocks of Anthos, which has integrations with platform-level services such as Stackdriver, Cloud Build, and Binary Authorization. GDC Virtual users purchase services and resources from the GCP Marketplace.
Figure 1. GDC Virtual components.
GDC Virtual puts all your IT resources into a consistent development, management, and control framework, automating low-value tasks across your PowerFlex and GCP infrastructure.
Within the context of GCP, the term ‘hybrid cloud’ describes a setup in which common or interconnected services are deployed across multiple computing environments, which include public cloud and on-premises. A hybrid cloud strategy allows you to extend the capacity and capabilities of your IT without the upfront capital expense investments of the public cloud while preserving your existing investments by adding one or more cloud deployments to your existing infrastructure. For more information, see Hybrid and Multi-Cloud Architecture Patterns.
PowerFlex delivers software defined storage to both virtual environments and bare metal hosts providing flexible consumption or resources. This enables both two-tier and three-tier architectures to match the needs of most any environment.
PowerFlex container storage
From the PowerFlex UI – shown in the following figure – you can easily monitor the performance and usage of your PowerFlex environment. Additionally, PowerFlex offers a container storage interface (CSI) and container storage modules (CSM) for integration with your container environment. The CSI/CSM allows containers to have persistent storage, which is important when working with workloads like databases that require it.
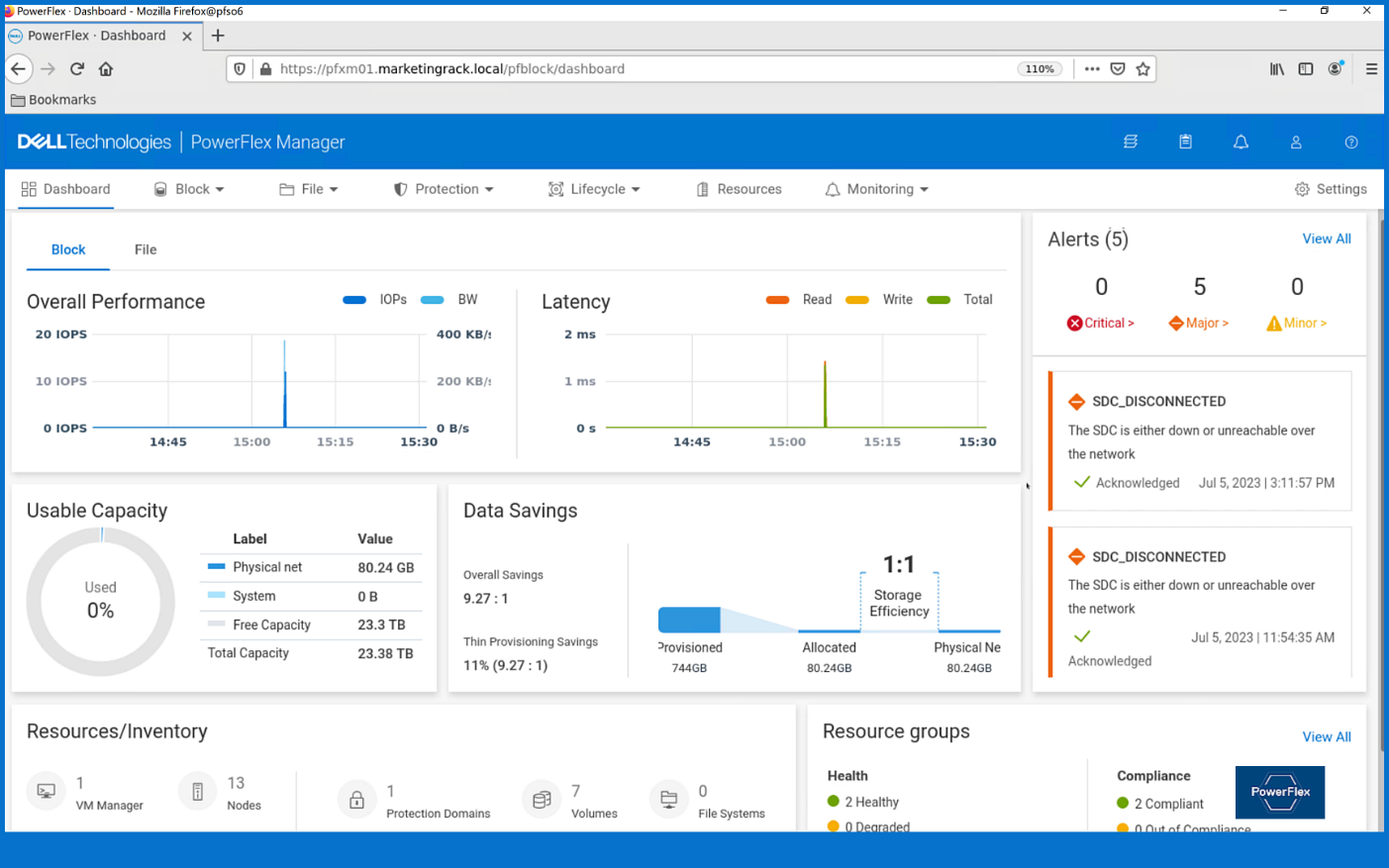
Figure 2. PowerFlex dashboard provides easy access to information.
To gain a deeper understanding of implementing GDC Virtual on Dell Powerflex, we invite you to explore our recently published reference architecture.
Dell engineers have recently prepared a PostgreSQL container environment deployed from the Google Cloud to a PowerFlex environment with GDC Virtual in anticipation of Kubecon. For those who have deployed Postgres from Google Cloud, you know it doesn’t take long to deploy. It took our team maybe 10 minutes, which makes it effortless to consume and integrate into workloads.
Once we had Postgres deployed, we proceeded to put it under load as we added records to it. To do this, we used pgbench, which is a built-in benchmarking tool in Postgres. This made it easy to fill a database with 10 million entries. We then used pgbench to simulate the load of 40 clients running 40 threads against the freshly loaded database.
Our goal wasn’t to capture performance numbers though. We just wanted to get a “warm” database created for some data protection work. That being said, what we saw on our modest cluster was impressive, with sub-millisecond latency and plenty of IO.
Data protection
With our containerized database warmed up, it was time to protect it. As you probably know, there are many ways to do this, some better than others. We’ll spend just a moment talking about two functional methods of data protection – crash consistent and application consistent backups. PowerProtect Data Manager supports both crash-consistent and application consistent database backups.
A “crash consistent” backup is exactly as the name implies. The backup application captures the volume in its running state and copies out the data regardless of what’s currently happening. It’s as if someone had just pulled the power cord on the workload. Needless to say, that’s not the most desirable backup state, but it’s still better than no backup at all.
That’s where an “application consistent” backup can be more desirable. An application consistent backup talks with the application and makes sure the data is all “flushed” and in a “clean” state prior to it being backed up. At least, that’s the simple version.
The longer version is that the backup application talks to the OS and application, asks them to flush their buffers – known as quiescing – and then triggers a snapshot of the volumes to be backed up. Once complete, the system then initiates a snapshot on the underlying storage – in this case PowerFlex – of the volumes used. Once the snapshots are completed, the application-level snapshots are released, the applications begin writing normally to it again, and the backup application begins to copy the storage snapshot to the protected location. All of this happens in a matter of seconds, many times even faster.
This is why application consistent backups are preferred. The backup can take about the same amount of time to run, but the data is in a known good state, which makes the chances of recovery much greater than crash consistent backups.
In our lab environment, we did this with PowerProtect Data Manager and PowerProtect DD Virtual Edition (DDVE). PowerProtect Data Manager provides a standardized way to quiesce a supported database, backup the data from that database, and then return the database to operation. This works great for protecting Kubernetes workloads running on PowerFlex. It’s able to create application consistent backups of the Postgres containers quickly and efficiently. This also works in concert with GDC Virtual, allowing for the containers to be registered and restored into the cloud environment.
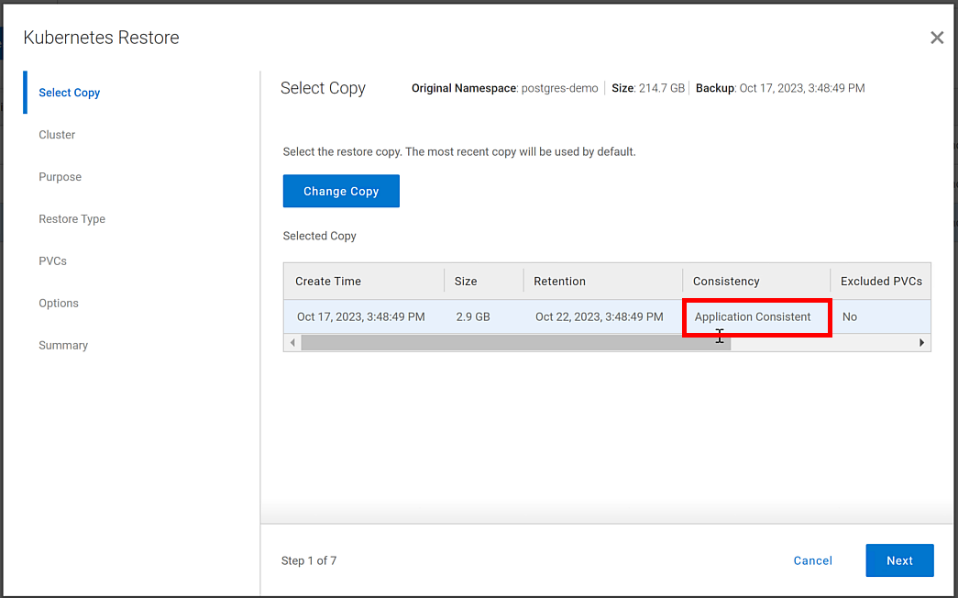
Figure 3. An application consistent backup and its timing in the PowerProtect Data Manager UI
It’s great having application consistent backups of your cloud workloads, “checking” many of those boxes that people require from their backup environments. That said, just as important and not to be forgotten is the recovery of the backups.
Data recovery
As has been said many times, “never trust a backup that hasn’t been tested.” It’s important to test any and all backups to make sure they can be recovered. Testing the recovery of a Postgres database running in GDC Virtual on PowerFlex is as straightforward as can be.
The high-level steps are:
- From the PowerProtect Data Manager UI, select Restore > Assets, and select the Kubernetes tab. Select the checkbox next to the protected namespace and click Restore.
- On the Select Copy page, select the copy you wish to restore from.
- On the Restore Type page, select where it should be restored to.
- Determine how the Persistent Volume Claims (PVCs) and namespace should be restored.
- When finished, test the restore.
You might have noticed in step 4, I mentioned PVCs, which are the container’s connections to the data and, as the name implies, allow that data to persist across the nodes. This is made possible by the CSI/CSM mentioned earlier. Because of the integration across the environment, restoring PVCs is a simple task.
The following shows some of the recovery options in PowerProtect Data Manager for PVCs.
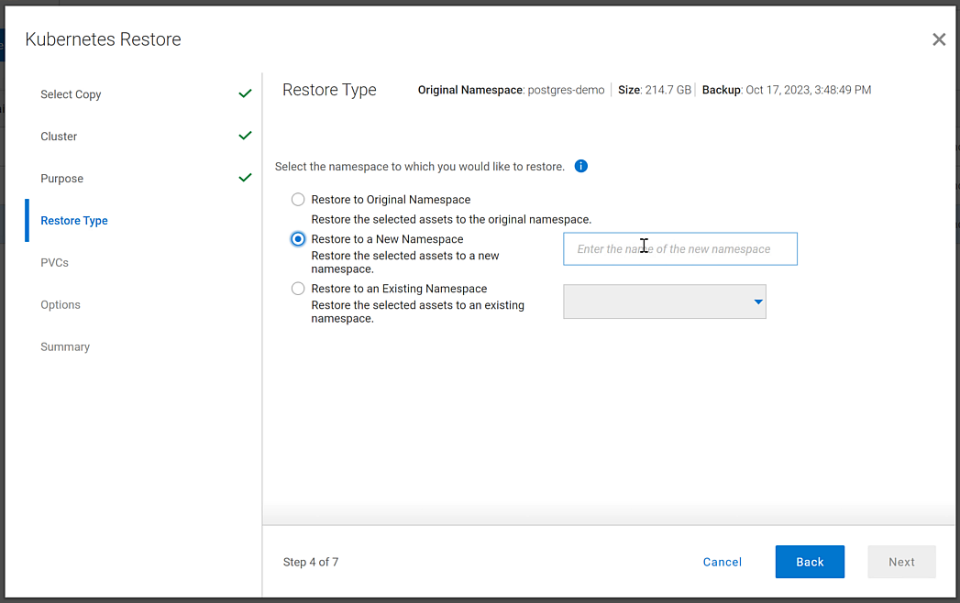
Figure 4. PowerProtect Data Manager UI – Namespace restore options
The recovery, like most things in data protection, is relatively anticlimactic. Everything is functional, and queries work as expected against the Postgres database instance.
Dell and Google Cloud collaborated extensively to create solutions that leverage both PowerFlex and GDC Virtual. The power of this collaboration really shows through when recovery operations just work. That consistency and ease enables customers to take advantage of a robust environment backed by leaders in the space and helps to remove one nightmare that keeps developers and IT admins awake at night, allowing them to rest easy and be prepared to change the world.
If any of this sounds interesting to you and you’ll be at Kubecon in Chicago, Illinois on November 6-9, stop by the Google Cloud booth. We’ll be happy to show you demos of this exciting collaboration in action. Otherwise, feel free contact your Dell representative for more details.
Resources
Authors:
Authors: | Tony Foster, | Vinod Kumar Kumaresan, | Harsha Yadappanavar, |
LinkedIn: | |||
X (formerly Twitter): |
| @harshauy | |
Personal Blog: |
|
|

Smart Scale for Dell PowerProtect Appliances, Part III: MSU Migration, Replication, Recoverability, Security
Tue, 18 Jul 2023 15:44:25 -0000
|Read Time: 0 minutes
In the first blog post of this series, we covered what Smart Scale is and why we need it. In the second part of the series, we covered the architecture deep dive of the solution and how to deploy, set up, and configure workflows.
In this part, let’s discuss Smart Scale Mobile Storage Unit (MSU) migration, replication topology, recovery, and security.
Migrating Mobile Storage Units
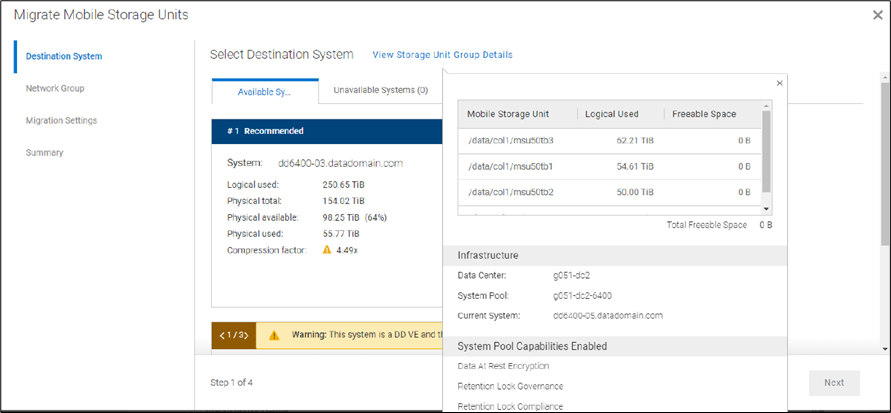
Migrating a Mobile Storage Unit (MSU) is a new feature that helps to migrate a MSU from one DD series appliance to another. In the following figure, notice that “MSU7” has been migrated to DD series appliance 3 from DD series appliance 2 and the client continues to use the “MSU7” on DD series appliance 3 for backup and recovery operations.
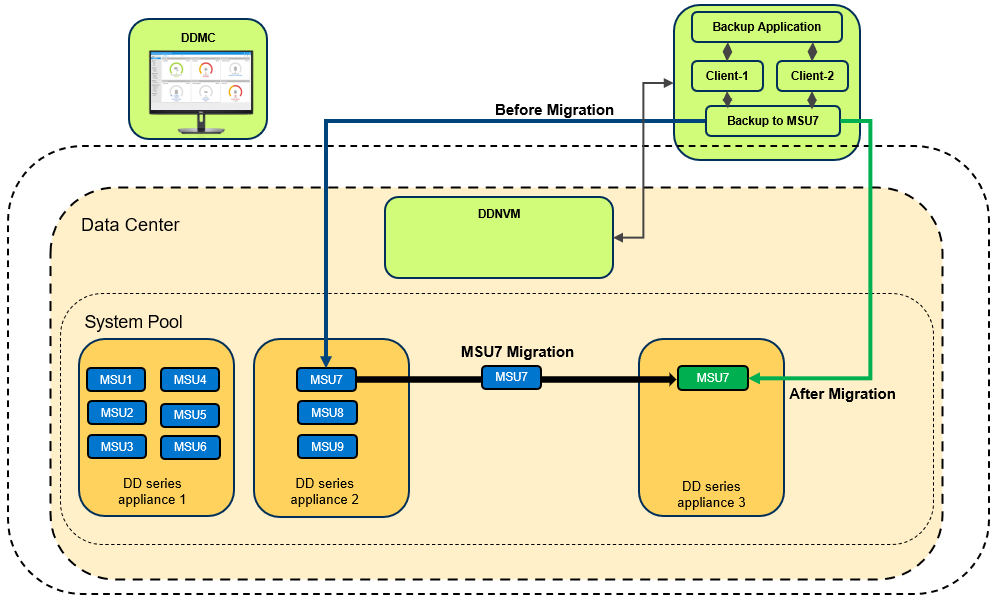
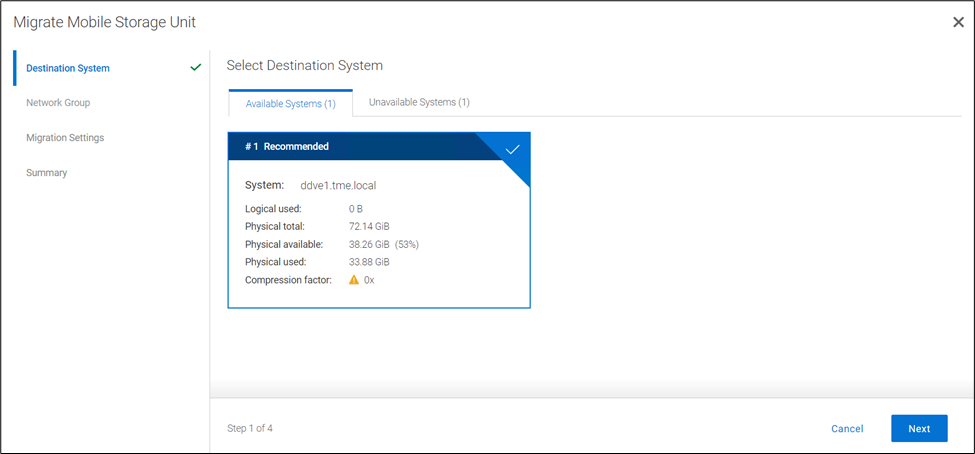
When you initiate the migration, the Migration and Placement Service provides the recommended list of DD series appliances from the available list of DD series appliances in the Data Center. Based on that list, you can select the target system and initiate the migration.
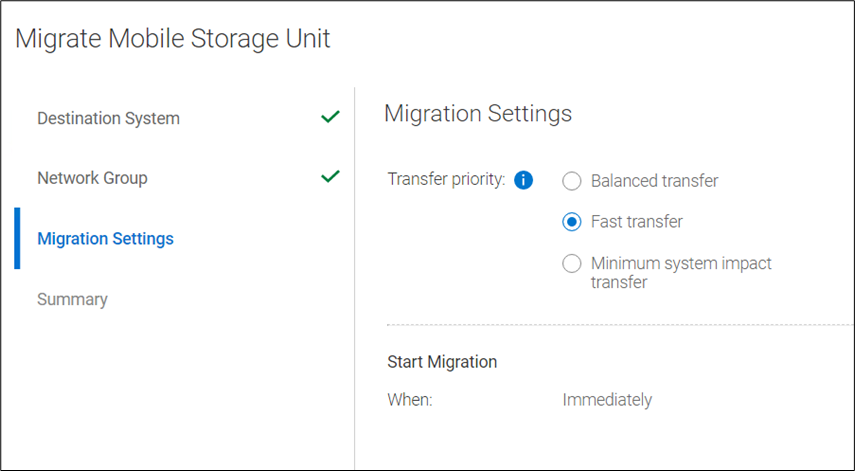
You can select which Network Group to use, and can select from the following migration transfer priorities:
- Balanced Transfer – Balances the resources between the backup and the migration
- Fast Transfer – Uses more resources for migration
- Minimum system impact – Uses fewer resources for the migration
The final step of the migration provides a Review and Commit screen, which includes several migration statistics (such as logical capacity used, physical capacity used and available, and compression factor). Using these analytics, users can optimize appliance and workload lifecycles. When the migration job reaches 100%, it is ready to commit. All the operations (backup or restore) to the source MSU need to be canceled or stopped before committing the migration. There are two options available for the source MSU: you can either mark the MSU to be deleted after a successful migration or you can keep the MSU on the source system. When the commit is done, the remaining data that needs to be synced with the target DDR will be updated. The source MSU is marked as read only; the target MSU is marked as read write. The source MSU is demoted to an Mtree and target system has a new MSU with the same name. The Migration and Placement Service in PowerProtect DD Management Center updates the Namespace Redirection Service Data Manager (NRSDM) about the new location of the MSU. NRSDM then provides that information to the NRS. When a boost client now requests the physical location of the MSU to write the data, NRS provides the target DDR’s IP address. Critically, none of these operations requires reconfiguring the backup software.
Note: Smart Scale is an additional feature of DDMC designed to make administration simple, agile, and flexible. When Smart Scale services are enabled, the customer’s existing environment remains undisturbed. This means that traditional backup operations and storage units co-exist with operations that system pools and mobile storage units support.
MSU affinity group migration
Starting with DDMC version 7.12, migration of a group of MSUs in an affinity group (or a subset of the group) from one DD system to another in a system pool is supported. With MSU affinity group migration, a DDMC administrator can migrate a group of MSUs without having to manually set up multiple migration jobs. There can be up to 32 MTrees in an affinity group.
Replicating Mobile Storage Units
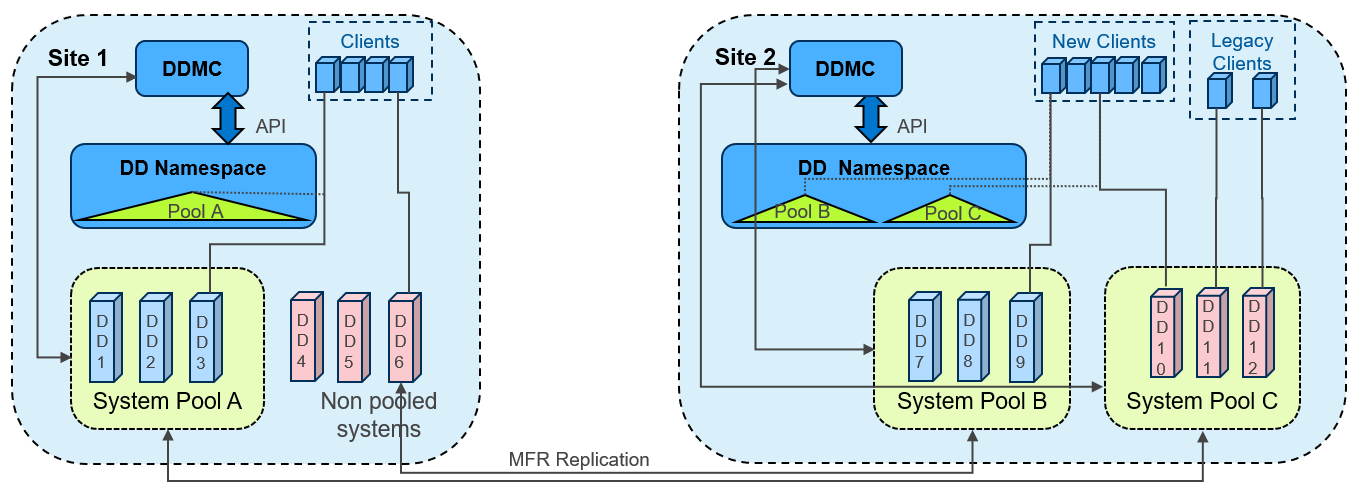
DD series appliances provide automated, policy based, network efficient, and encrypted replication for disaster recovery and multi-site backup and archive consolidation. Smart Scale supports Managed File Replication (MFR) on Mobile Storage Units (MSUs) with Dell PowerProtect Data Manager, Dell NetWorker, and Veritas NetBackup. Types of replications supported are:
- Storage Unit to Storage Unit
- MSUs to Storage Unit, and Storage Unit to MSUs
- MSUs to MSUs
Replication is supported between storage units or MSUs that are within the same data center or not, within the same system pool or not, within the same appliance or not, and within the management domain of a single DDMC or across DDMC deployments.
Recoverbility of Smart Scale services
In the era of performance on appliances, what organizations often ignore is the recoverability of the appliance or service when failures occur. Dell recognizes the importance of your SLA and RPO, keeping that in mind we have built Smart Scale architecture so that it provides an automated response to any disaster, by providing options for quick recovery to ensure minimum downtime.
Let’s divide the Smart Scale architecture into two parts: the Management plane which has all the Smart Scale management services, and the Data plane which stores the actual data (that is, the DD series appliance). Now let’s examine the various recovery abilities available in both planes.
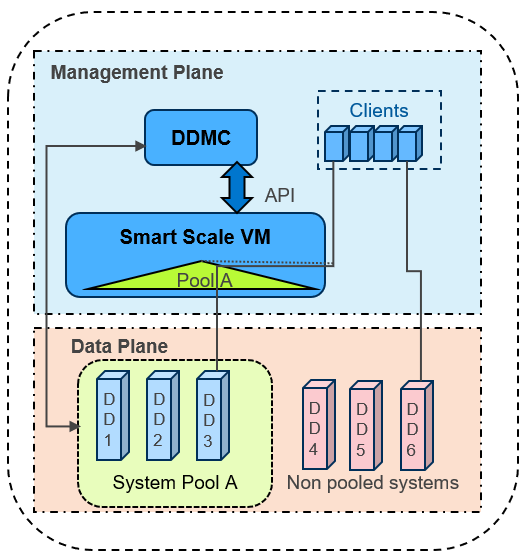
In the management plane
- Smart Scale has intelligent Analytics Services that provide capacity predictions, initial placement, and rebalancing recommendations.
- Micro services in PowerProtect DD Management Center (DDMC) and DD Namespace VM (DDNVM) automatically restart and recover as needed.
- Automated alert notifications are triggered by periodic monitoring of services in DDMC and Namespace VM. In the worst case, DDMC administrators may need to redeploy DDNVM using DDMC (which is quick, by just re-entering the VM credentials).
- The reconciliation service automatically resynchronizes and fixes discrepancies between DDMC and DDNVM.
- DDMC backs up the configuration regularly on a timed basis and whenever administrators make a configuration change.
- DDMC can be recovered with a clean reinstall using configuration backup. If there are no issues in the DDNVM, DDMC can then resynchronize with the running DDNVM, with no need to redeploy DDNVM.
In the data plane
- Data Center services hold a copy of the overall namespace for each pool of DD series appliances, to enable the redirection of backup clients to the appropriate DD series appliance in the pool
- After it is redirected, the backup client connects to the DD series appliance and starts data transfer, then (unless it is restarted) it continues to work even if DDMC or DDNVM have any issues.
- DDMC VM will redeploy DDNVM if necessary
- DDNVM continues working even if DDMC is not available
- Reinstalling DDMC does NOT require reinstalling DDNVM
Security options with Smart Scale services
With the increased rate of cyber-attacks and ransomware threats, it is essential to have services and appliances that have adequate security restrictions for shielding your data from malicious attacks. Smart Scale enables security at every level of the solution. Let’s take a look at the security options available:
Data plane
- D@RE Encryption at rest is supported within Smart Scale. A System Pool may have a mix of encrypted and non-encrypted systems. During migration a warning is given if the selected migration is from encrypted to non-encrypted systems.
- Encryption in flight is supported both for backup/restore and replication, with the same modes of operation as regularly available for PowerProtect appliances.
- MSUs are protected by Mobile Boost Users. These users are migrated between systems automatically as required when MSUs are migrated.
Management plane
- Overall security is applied and managed from DDMC, both in the creation of System Pools and in the creation and mobility of MSUs.
- Certificates are enabled to secure communications between DDMC and DDNVM.
- Most services run as non-root user.
- DDNVM is guest OS enabled, and no customer login is allowed.
Network security
- When creating and enabling MSUs, the supported network groups are selected. Redirection from Pool Access IP to MSUs is restricted only to those network groups enabled for specific MSUs.
- VLANs are supported (but not mandated) using either trunk or access mode (that is, tagging on the node or the network switch) for both appliances and DDNVM.
Smart Scale is about simplifying capacity management across multiple DD series appliances, but it's more than just management and reporting. While it includes analytics, insights, and recommendations around capacity needs and placement, the real value is the system pooling and management it provides. Smart Scale services deliver the next generation of data protection scale, mobility, and insights for PowerProtect DD series appliances.
Thank you for taking a moment to read this series of Smart Scale blog posts. We hope they were useful and helped you to understand the Smart Scale feature comprehensively.
To catch up on the previous Smart Scale blog posts in this series, see:
- Smart Scale for Dell PowerProtect Appliances, Part I: Innovative Technology to Manage Multi-Exabyte Data
- Smart Scale for Dell PowerProtect Appliances, Part II: Architecture Deep Dive
Additional resources for Smart Scale
- Dell PowerProtect DD series appliances
- Smart Scale for PowerProtect Appliances – Technical white paper
- Dell PowerProtect DD Management Center Interactive Demo
Authors:

Smart Scale for Dell PowerProtect Appliances, Part II: Architecture Deep Dive
Tue, 18 Jul 2023 12:18:05 -0000
|Read Time: 0 minutes
In the first blog post of this series, we discussed some of the challenges that are associated with managing large datacenters and multiple appliances, and how Smart Scale can help tackle these issues. Let’s now discuss the solution architecture and workflow in detail.
Deploying Smart Scale Services in PowerProtect DD Management Center (DDMC)
The following are the steps for deploying and setting up Smart Scale services, along with the terminology that is used by the solution:
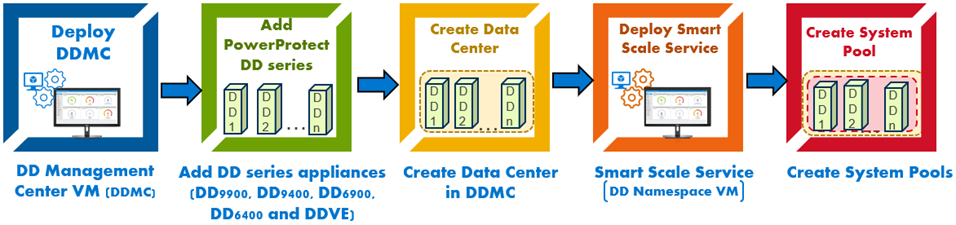
1. To start, if there is an existing DDMC then login to it or deploy a new DDMC. DDMC is a scalable, virtual system-based solution for centralized management of multiple PowerProtect DD series appliances and virtual data protection systems (PowerProtect DD Virtual Edition (DDVE). DDMC is composed of browser-based pages and is installed and runs on a VMware platform or compatible cloud service.
2. Add all DD series appliances (DD9900, DD9400, DD6900, DD6400, and DDVE) to DDMC. (A DDMC instance can support up to 150 DD series appliances.)
3. Create a data center in DDMC. A data center is a logical grouping of DD series appliances located in the same region or building. You can assign a managed DD series appliance to only one data center. You can create multiple data centers to reflect the full organization.
4. For each data center, enable Smart Scale services. Smart Scale services allow you to create system pools and mobile storage units (MSUs) within the system pools. When Smart Scale services are enabled for a data center, DDMC automatically deploys a DD Namespace Virtual Machine (DDNVM) in the appropriate VMware infrastructure.
In DDNVM we have DD Namespace Redirection Service (DDNRS). This service helps DDNVM receive backup client requests and redirects them to the DD series appliance that is hosting the MSU.
Smart Scale services also enable some microservices in DDMC, such as the Placement and Migration Service (PMS). The PMS is a microservice responsible for generating recommendations, such as the best DD series appliance for the initial placement of new MSUs. It also facilitates the intelligent movement of MSUs within a group of multiple DD series appliances (called a system pool) based on factors such as capacity insights, performance, and content overlap. PMS also communicates with DDMC and the Namespaces Redirection Server Database Manager (NRS DB Manager) through a collection of REST APIs. Starting with the DDOS 7.11 release, you can select a system under a pool and create an MSU on the system. The DDMC GUI provides a list of systems in a system pool in a recommended order.
5. After Smart Scale services are deployed, create a system pool in a data center. A system pool in a data center is a defined set of DD series appliances in the same datacenter that you can organize. The reasons for forming system pools can include any combination of security, accounting, locality, and so on. (A data center supports up to four pools; each pool supports up to 32 DD series appliances).
Note: An option to edit and redeploy Smart Scale service is available if the deployment fails or post deployment.
- DDMC manages these DD series appliances and balances client workloads that access the MSUs that are hosted on them. An MSU is a DD Boost storage unit that is hosted on one of the DD series appliances in a system pool. DD Boost clients access the MSUs through the configured network and using the Mobile Boost User (MBU) credentials. An MBU is a user that is associated with a data center. MSUs must be owned by a MBU in the MSUs’ data center.
- DDMC creates and maintains a network group, which is a set of IP addresses, a subnet, and a VLAN ID. All IP addresses in a network group should be in the same family (IPv4 or IPv6). A pool access IP is created for each network group. This IP is a dedicated IP address that enables client access to the system pool. Redirection then occurs within the network group, helping customers manage and maintain separation across the network, and between system pools and MSUs.
High level backup architecture and workflow
While configuring the backup policy, select the system pool IP. When the backup is started (using backup software such as Dell PowerProtect Data Manager), the backup client uses a pool access IP to connect to the DD Namespace VM or Smart Scale services. The DD Namespace VM communicates with the DDMC VM using APIs to get the DD series appliance details from a system pool where there is more space available. The placement and migration service in DDMC provides the sorted list of DD series appliances on that system pool, based on capacity, then DDMC provides the DD details to the DD Namespace VM. The DD Namespace VM returns the information to the backup client. When the backup client receives the DD system’s IP and MSU details, it connects directly to the DD series appliance and starts the data transfer to the MSUs on the recommended DD series appliance.
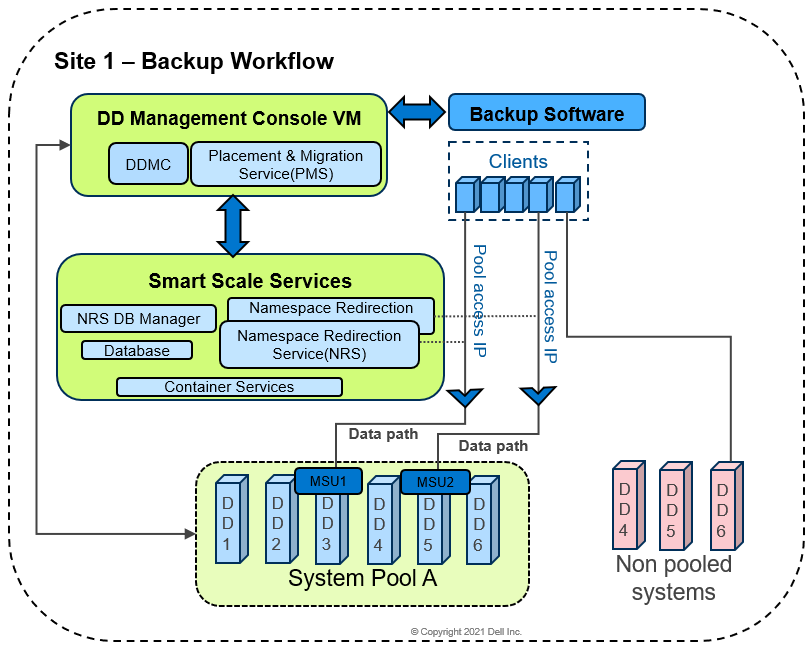
In this figure, because DD3 and DD5 have more available space, MSU1 and MSU2 are created on them for clients requesting backup. When a non-pooled system or regular DD storage unit is used as the backup target during backup policy configuration, it accesses the DD storage unit directly and does not use the DD Namespace redirection service.
Both pooled and non-pooled environments can coexist. This means that backup applications can support a hybrid environment that consists of a DD series appliance that has both regular storage units and system pools mixed with MSUs.
For additional information about Smart Scale architecture and workflow see Smart Scale for PowerProtect Appliances – Technical white paper. See the next blog post in this series, Smart Scale for Dell PowerProtect Appliances, Part III: MSU Migration, Replication, Recoverability, and Security, which talks about Smart Scale MSU migration, replication topology, recovery, and security. You can also go back and check out Smart Scale for Dell PowerProtect Appliances, Part I: Innovative Technology to Manage Multi-Exabyte Data.
Additional resources for Smart Scale
Authors:
Vinod Kumaresan (LinkedIn)
Sonali Dwivedi (LinkedIn)
Data Protection for PowerStore with PowerProtect DD Series Appliances
Tue, 09 May 2023 23:47:18 -0000
|Read Time: 0 minutes
Summary
Dell PowerStore is a revolutionary storage appliance that is designed for the data era. PowerStore is a data-centric, intelligent, and adaptable infrastructure solution that provides various ways to protect your data, locally and remotely. With PowerStore Manager, you can protect your data locally by creating snapshots (point-in-time copies) of volumes, volume groups, virtual machines, or file systems. You can also apply remote protection by replicating your data to a remote system or by mirroring the data using metro volumes for redundancy in the event of a disaster.
Native integration of Dell PowerProtect DD series appliances with PowerStore
Starting with PowerStoreOS (Operating System) version 3.5, a new remote backup solution is introduced which provides an additional method to protect your data in a PowerStore cluster. Dell PowerProtect DD series appliances can be added as a remote system to protect the resources (volumes and volume groups) on PowerStore. PowerStore can send backups directly to DD series appliances with no backup application required.
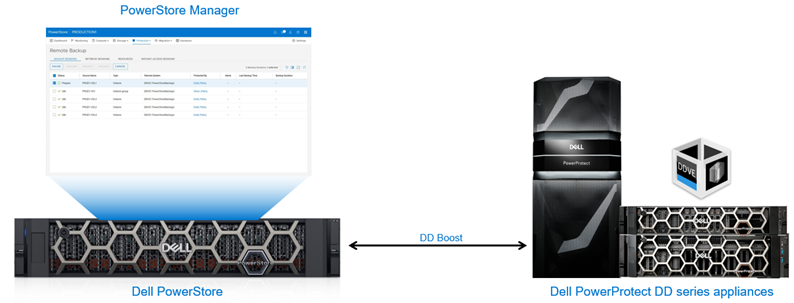
Figure 1. Remote backup – PowerStore to DD series appliances
DD series appliances enable organizations to protect, manage, and recover data at scale across their diverse environments. PowerStore supports backing up to a physical PowerProtect appliance or to PowerProtect DD Virtual Edition (DDVE). DDVE is supported either on-premise or within AWS. A single DD series appliance can be added to the same PowerStore cluster multiple times, provided that a different Storage Unit ID is used. This ability allows you to back up different resources to different locations within a single DD series appliance.
The key features are:
- Self-service remote backup with DD series appliances as the target remote system
- Backup and retrieve PowerStore block volumes and volume groups data with DD series
- Ability to Instantly access the remote snapshot residing on a DD series appliance
- Supports both physical and software-defined DD series appliances. Supports PowerProtect DD Virtual Edition with AWS cloud provider.
- PowerStore leverages DD Boost protocol to send data to DD series
- End to end data protection orchestration using PowerStore Manager
- Direct encrypted transfer from PowerStore to DD series
The key benefits are:
- Zero impact on hosts because backups run directly on PowerStore
- Incremental forever data protection strategy for PowerStore block volumes and volume groups
- Backup different resources to different locations within a single DD series appliance
- Ability to configure local and remote protection within a single protection policy with independent schedule and retention
- Replication between DD series appliances and to the cloud
Steps to protect resources on PowerStore with DD series
Figure 2 below explains the steps to protect resources (volumes and volume groups) on PowerStore with DD series appliances.
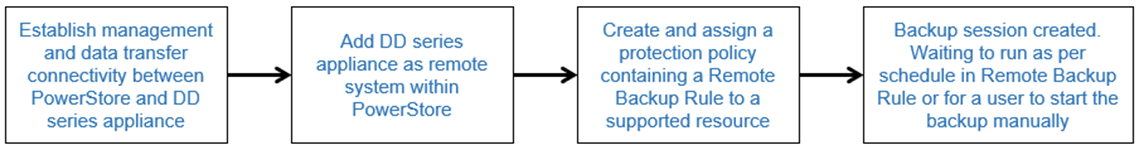
Figure 2. Steps to protect resources on PowerStore with DD series
Remote session operations
With PowerStore integration with DD series appliances, you can protect PowerStore volumes and volume groups directly to DD series appliances. With this ability you can perform remote session operations, such as backup, retrieve, and instant access. A remote session tracks each of these operations. Remote backup, retrieve, and instant access sessions go through various states that indicate the session’s progress and any possible issues.
Backup session
PowerStore utilizes backup sessions to create remote backups (snapshots) on the DD series appliances. When a protection policy containing a remote backup rule is assigned to a supported resource, a backup session is created. There is no manual way to configure a backup session without a protection policy. Only one backup rule can be added per protection policy.
A protection policy can be created to provide local and remote protection for PowerStore resources. Each protection policy for the same volume or volume group can include replication rule, remote backup rule, and snapshot rules, which are independent with schedule and retention.
When a backup is run, a snapshot of a volume or a volume group is created on the PowerProtect system. The created snapshots are crash-consistent and there is no application integration. A backup can be started manually by a user or automatically according to the schedule defined in the remote backup rule. Remote snapshots are created with an expiration time based on the remote backup rule associated with the resource.
The snapshots that are created manually by a user inherit the remote backup rule’s retention policy. Only the initial backup is full; subsequent backups are incremental. Backup session states when running a backup include ‘idle’, ‘prepare’, ‘in-progress’, ‘paused’, ‘cancelling’, and ‘failed’. Figure 3 depicts the high-level backup workflow.
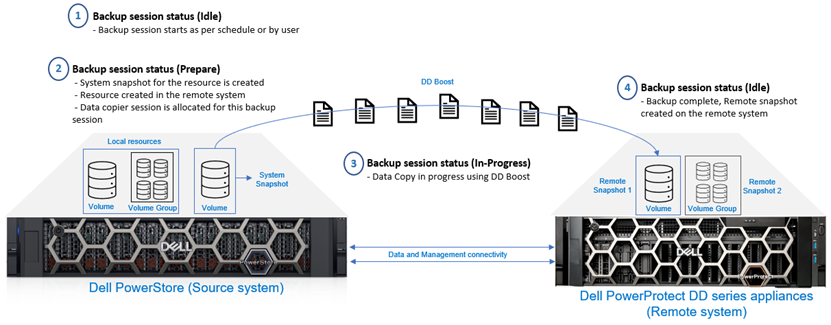
Figure 3. Backup session – High-level workflow
When performing incremental backups, only the unique data is traversed through the network to create a remote snapshot on the DD series appliances. The PowerStore snapshot differential feature, and DD series virtual synthetic operations, enable the implementation of an incremental forever data protection strategy. Only the changed blocks are sent to DD series and aggregated into the full consistent remote snapshot. The snapshot can be retrieved either incrementally or fully to the same PowerStore cluster or different cluster. When the backup is complete, users can view the list of all resources that have been backed up from the Resources page in the PowerStore Manager UI.
Retrieve session
When remote snapshots are created on the DD series appliances, backups can be retrieved to an existing or new PowerStore cluster. The retrieve option is used to copy a remote snapshot for a volume or volume group and save it as a local snapshot in the PowerStore cluster. This local snapshot will be set to no automatic deletion, where the user can update the expiration time or change it to a secure snapshot. Based on the use case, a differential or a full data copy is required. Figure 4 shows the high-level retrieve workflow.
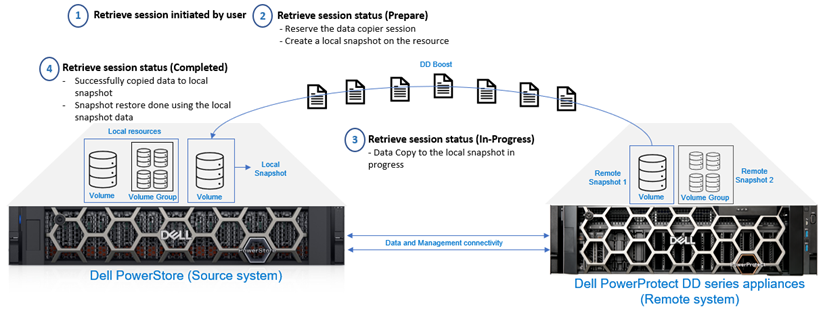
Figure 4. Retrieve session - High-level workflow
You may want to retrieve a remote snapshot for restoring the source resource or for creating a thin clone.
Retrieve a remote snapshot to the same PowerStore cluster:
- If the source volume or volume group of the retrieved backup still exists in the system, a local snapshot is created on the PowerStore cluster under the source resource. If possible, the retrieval is incremental - only the changes from the source volume are retrieved, which makes the retrieval process efficient.
- If the source volume or volume group of the retrieved backup no longer exists in the system, both a new resource and a local snapshot are created, and the new resource is restored with the snapshot data.
Retrieve a remote snapshot to a different PowerStore cluster:
- Because the source volume or volume group never existed on that cluster, both a new resource and a local snapshot are created. The new resource is restored with the snapshot data, returning the resource to the same state as the original.
Instant Access session
An instant access session allows a host to access a volume or volume group remote snapshot residing on a DD series appliance. From PowerStore Manager, you can create an instant access session to view the remote snapshot contents without having to retrieve them on the PowerStore cluster. Instant Access enables users to instantly access deleted, corrupted, or modified data within the remote snapshot. Only one instant access session is allowed per remote snapshot. When an instant access session is running, the PowerStore appliance does not perform backup and retrieve operations, and local resources are not protected until the instant access sessions are ended. Figure 5 shows the high-level instant access session workflow.
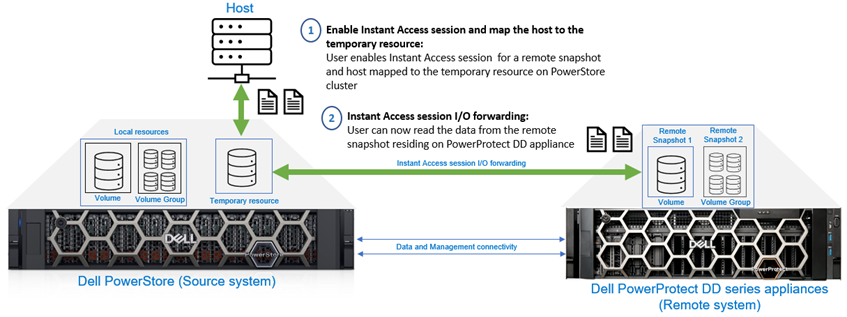
Figure 5. Instant Access session - High-level workflow
When enabling Instant Access for a volume snapshot, you can configure host access before enabling the session. For an instant access session on a volume group snapshot, the user must add the host access to the remote snapshot volumes after the session is created.
Note: Instant Access is supported for all block resources except VMware VMFS datastores. If access to data within a remote snapshot of a VMFS datastore is required, customers can still perform a retrieve operation on the remote snapshot and create and mount a thin clone.
Data protection is a mission-critical priority for any modernized technology, as organizations increasingly rely on innovative storage technology appliances such as PowerStore. This unique data protection solution, which integrates PowerStore with DD series appliances, ensures continuous availability of data in PowerStore to help organizations meet their SLAs.
References
Dell PowerStore:
- Dell PowerStore – Product website
- Dell PowerStore: Snapshots and Thin Clones
- Dell PowerStore: Info Hub
Dell PowerProtect DD series appliances:
- PowerProtect DD Series Appliances – Product website
- PowerProtect DD Series Appliances - Data Sheet
- PowerProtect DD Series Appliances - Spec Sheet
- Dell PowerProtect DD Series Appliances - Info Hub

Dell Technologies Data Protection for VMware Telco Cloud Platform
Fri, 28 Apr 2023 19:38:15 -0000
|Read Time: 0 minutes
Summary
Any modernized infrastructure undoubtedly requires a data protection strategy to avoid downtime, prevent data loss, and recover quickly in case of a disaster. Dell Technologies provides effective data protection solutions to help organizations solve a number of significant challenges. Dell PowerProtect Data Manager is one of the effective data protection solutions to protect VMware Telco Cloud Platform management/workload cluster components and application workloads.
Protecting VMware Telco Cloud Platform with Dell PowerProtect Data Manager
VMware Telco Cloud Platform is a modernization solution that deploys cloud-native and virtual network functions consistently, at web-scale speed, and without disruption. VMware Telco Cloud Platform is a cloud-native platform that empowers communication service providers (CSPs) to manage virtual network functions (VNFs) and Containerized Network Functions (CNFs) across the core, far edge radio access network (RAN), enterprise edge, and cloud with efficiency, scalability, and agility. Telco Cloud Platform provides the framework to deploy and manage VNFs and CNFs quickly and efficiently across distributed 5G networks. You can run VNFs and CNFs from dozens of vendors, on any cloud, with holistic visibility, orchestration, and operational consistency.
Telco Cloud Platform is powered by field-proven compute and networking coupled with VMware Telco Cloud Automation and a telco-grade Kubernetes distribution. VMware Telco Cloud Platform empowers CSPs to modernize their 5G networks so they can rapidly deploy and efficiently operate multi-vendor CNFs and VNFs. The compute and networking, which are supplied by VMware vSphere and VMware NSX-T Data Center, enable CSPs to run both CNFs and VNFs on consistent horizontal infrastructure. The Kubernetes distribution—VMware Tanzu Kubernetes Grid—is designed to support telecommunications use cases.
The essentials include:
- Software-defined data protection: Provides flexible data protection and compliance across applications and cloud-native IT environments
- Unique protection: Ensures availability of all your Telco Cloud Platform components and workloads without business disruption
- Autonomous operations: Automated discovery and protection of databases, virtual machines, file systems and Kubernetes containers
- Efficient protection: Protects data directly to Dell PowerProtect DD series appliances with optional replication to secure Cyber Recovery vault
- Self-service backup and restore: Enables data owners from their native interfaces
- PowerProtect Data Manager Appliance: Integrated data protection platform that combines Data Manager software in a single appliance
- OTEL Assurance: Validated by Dell’s Open Telco Ecosystem Lab
The key capabilities are:
- Protection for the entire VMware Telco Cloud Platform stack including your mission critical applications
- VM image and file-level protection for the management/workload clusters components or instances
- Namespace level/PVC protection for TKG cluster workloads
- VMware virtual machines in a reliable and efficient manner using the Transparent Snapshot Data Mover (TSDM) mechanism.
Dell PowerProtect Data Manager
PowerProtect Data Manager software is an enterprise solution that provides software-defined data protection, deduplication, operational agility, self-service, and IT governance. Data Manager gives you valuable insight into protected on-premises and in-cloud workloads, applications, file systems, and virtual machines (VMs). Plus, complete oversight and governance to ensure compliance.
Designed with operational simplicity and agility in mind, Data Manager enables the protection of traditional workloads including Oracle, Exchange, SQL, SAP HANA and file systems as well as Kubernetes containers and virtual environments. Restore data on-premises or in the cloud. Governance control ensures IT compliance, making even the strictest service level objectives obtainable.
PowerProtect Data Manager key features include the following:
- Software-defined data protection with integrated deduplication, replication, and reuse
- Data backup and recovery self-service operations from native applications that are combined with central IT governance
- Multicloud optimization with integrated Cloud Tiering
- SaaS-based monitoring and reporting
- Modern services-based architecture for ease of deployment, scaling, and updating
PowerProtect Data Manager for VMware Telco Cloud Platform
The PowerProtect Data Manager is a virtual appliance that can be deployed on or outside of VMware Telco Cloud Platform environment to protect the management and workload components and application workload data.
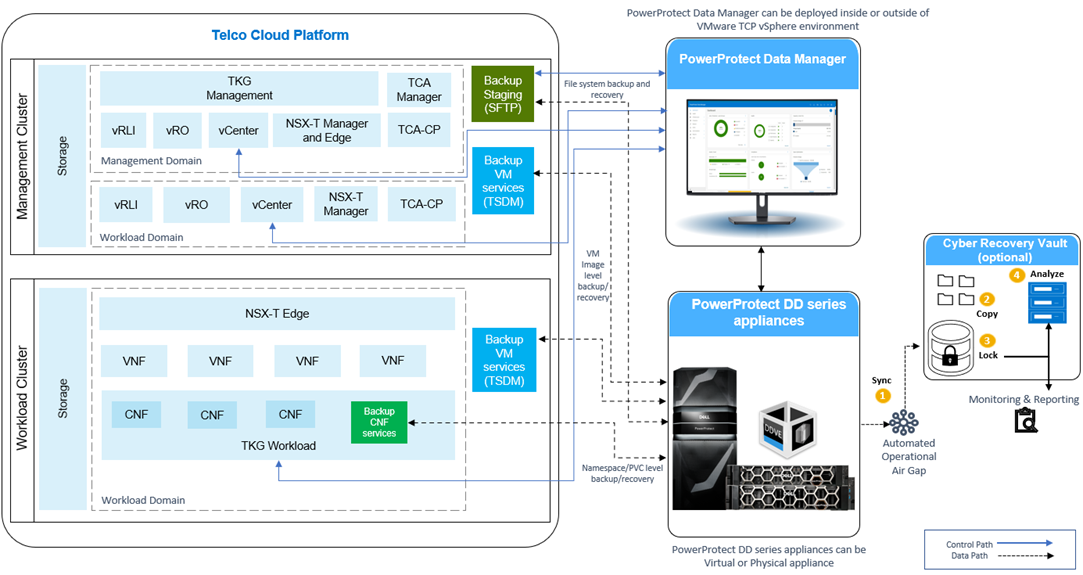
Figure 1. PowerProtect Data Manager protecting VMware Telco Cloud Platform
PowerProtect Data Manager is integrated with PowerProtect DD series appliances as the protection target where the backups are stored. A PowerProtect DD series appliance can be a physical or virtual appliance.
In addition to being deployable stand-alone, PowerProtect Data Manager is available as an integrated appliance, the Dell PowerProtect Data Manager appliance. The Data Manager Appliance offers an integrated data protection platform that combines protection storage with PowerProtect Data Manager software and cloud readiness – all in a single appliance. The Data Manager Appliance provides a unified user experience and automates discovery and protection of databases, VMs, file systems, and Kubernetes containers.
Optionally, data can be replicated from a production DD series appliance to another DD series appliance or to a DD series appliance in Cyber Recovery vault using the Dell PowerProtect Cyber Recovery solution. PowerProtect Cyber Recovery provides proven, modern, and intelligent protection to isolate critical data, identify suspicious activity, and accelerate data recovery, allowing you to resume normal business operations quickly.
PowerProtect Cyber Recovery key features include the following:
- Operational air gap with data isolation and immutability
- CyberSense analytics and Machine Learning monitor data integrity
- Accelerate cyber and ransomware attack data recovery
Data Protection methods for VMware Telco Cloud Platform infrastructure components and application workloads
For VMware Telco Cloud Platform management domain (Management workload cluster), the following table shows the core components and the backup methods used.
TCP component | Backup/Restore method |
Management vCenter server | File level |
NSX-T Manager nodes | File level |
vRealize Log Insight | VM Image level |
vRealize Operations Manager | VM Image level |
vRealize Orchestrator | VM Image level |
Telco Cloud Automation Manager | File level |
Telco Cloud Automation Control plane | File level |
Tanzu Kubernetes Grid Management cluster | VM Image level |
For VMware Telco Cloud Platform workload domain (Management workload cluster), the following table shows the core components and the backup/restore methods used.
TCP component | Backup/Restore method |
Workload vCenter server | File level |
NSX-T Manager nodes | File level |
vRealize Log Insight | VM Image level |
vRealize Orchestrator | VM Image level |
Telco Cloud Automation Control plane | File level |
For VMware Telco Cloud Platform general purpose VMs (Management workload cluster), the following table shows the core components and the backup/restore methods used.
Other component (examples) | Backup/Restore method |
DNS, NTP, DHCP, Web servers, database, filesystem | VM Image level /File level/database |
Harbor registry, other registry | VM Image level or File level |
Customized applications on VM’s/Tanzu Kubernetes Grid | Namespace/PVC or Image level |
For the VMware Telco Cloud Platform compute workload domain (Workload cluster), the following table shows the core components and the backup/restore methods used.
TCP component | Backup/Restore method |
Virtual Network Functions (VNFs) | VM level (TSDM) or File level or File/DB level |
Tanzu Kubernetes Grid Workload cluster (CNFs) | Namespace and PVC level with application consistency |
The following table shows the backup system components protection.
Backup component | Backup/Restore method |
Backup Staging VM | File level |
Backup Server (PowerProtect Data Manager) | PowerProtect Data Manager disaster recovery process |
PowerProtect DD series appliances | Replication to another DD series appliance or DD series appliance in Cyber Recovery vault |
Protecting management/workload cluster components and VNFs using image-level or file system backup
The management and workload cluster vCenter servers are integrated with Data Manager and discovered as an asset source after being registered with PowerProtect Data Manager. PowerProtect Data Manager discovers the management workload domain components and application workload (VNFs) as virtual-machine assets for protection. Data Manager can prot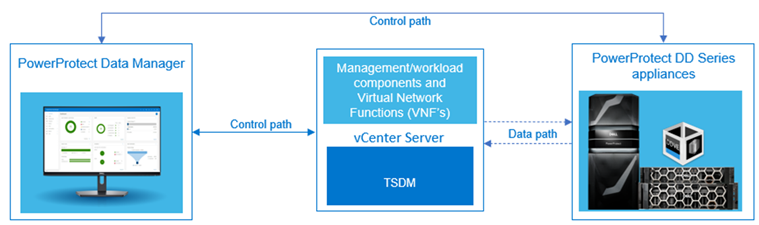 ect VMware virtual machines in a reliable and efficient manner using the Transparent Snapshot Data Mover (TSDM) mechanism. Transparent Snapshots simplifies VM image backups for near-zero impact to your VMs or VM resources – and it works with any VMware supported storage. For more details about TSDM, see the technical white paper PowerProtect Data Manager: VMware Virtual Machine Protection Using Transparent Snapshots.
ect VMware virtual machines in a reliable and efficient manner using the Transparent Snapshot Data Mover (TSDM) mechanism. Transparent Snapshots simplifies VM image backups for near-zero impact to your VMs or VM resources – and it works with any VMware supported storage. For more details about TSDM, see the technical white paper PowerProtect Data Manager: VMware Virtual Machine Protection Using Transparent Snapshots.
Protecting TKG cluster workloads (CNFs)
With PowerProtect Data Manager, the Tanzu Kubernetes Grid cluster workloads, such as namespaces and Persistent Volume Claims (PVCs) on Telco Cloud Platform, are protected efficiently using the Velero component and cProxy pod (data mover). When the Tanzu Kubernetes Grid cluster is added as an asset source in PowerProtect Data M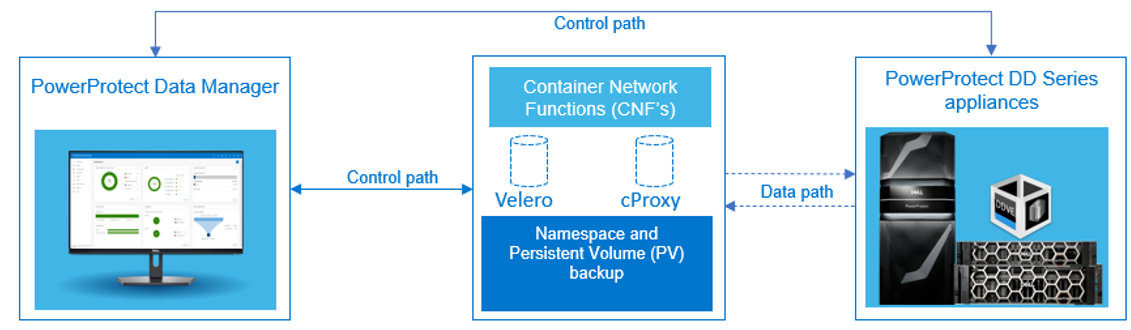 anager and discovery is complete, the associated namespaces are available as assets for protection. The PowerProtect Data Manager supports agentless, application-consistent backups of database applications that reside in Kubernetes pods. The PowerProtect Data Manager provides a standardized way to quiesce a supported database, back up the data from that database, and then return the database to operation.
anager and discovery is complete, the associated namespaces are available as assets for protection. The PowerProtect Data Manager supports agentless, application-consistent backups of database applications that reside in Kubernetes pods. The PowerProtect Data Manager provides a standardized way to quiesce a supported database, back up the data from that database, and then return the database to operation.
Protecting the SFTP server (Staging VM)
For file level-based backup of VMware Telco Cloud Platform components, the respective VMware Telco Cloud Platform management and compute workload component dump is created and sent to an SFTP target (staging VM). Later, the SFTP target (staging VM) is protected using a file system agent-based backup method with PowerProtect Data Manager.
Dell Technologies enables you to simplify the experience of adopting modern data protection. PowerProtect Data 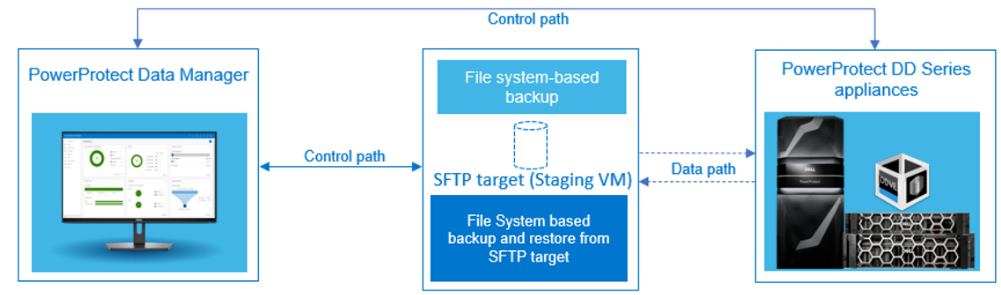 Manager enables users to protect, manage, and recover data in on-premises, virtualized, and cloud deployments. This platform provides centralized governance that helps mitigate risk and assures compliance of SLAs and SLOs through simple protection workflows. PowerProtect Data Manager is one of the effective solutions to protect VMware vSphere components and application workload data on VMware Telco Cloud Platform.
Manager enables users to protect, manage, and recover data in on-premises, virtualized, and cloud deployments. This platform provides centralized governance that helps mitigate risk and assures compliance of SLAs and SLOs through simple protection workflows. PowerProtect Data Manager is one of the effective solutions to protect VMware vSphere components and application workload data on VMware Telco Cloud Platform.
Note: This document focuses on protecting the CNFs and VNFs on VMware Telco Cloud Platform infrastructure, however it can also be used to protect other VNFs and CNFs as well as VMware components outside of the VMware Telco Cloud Platform infrastructure.
Assurance provided by OTEL
The Open Telecom Ecosystem Lab (OTEL) accelerates and simplifies the creation of an open, modern telecom ecosystem. By validating complex technical solutions through our virtual and physical OTEL labs, we’re helping partners reduce the costs and risk of deployment while opening new 5G and cloud native opportunities.
OTEL offerings driving the open 5G opportunity:
- Partner/Industry Certification -- Self-Certification that enables independent software vendors to de-risk deployments and make the ecosystem consumable. Also, Joint-Certification improves outcomes and business value by verifying ecosystem partner compatibility.
- Solution Validation -- End-to-end CSP and telecom partner solution validation, life-cycle management, and enhanced service support.
- Proof of Concept -- Work with partners and CSPs to develop early evaluation and sand box development to drive ecosystem adoption.
- Demonstration and Training -- Showcase new capabilities and support technical training activities.
To learn more about our Open Telecommunication Ecosystem Lab please see additional resources at: OTEL (Open Telecom Ecosystem Labs).
Technical References
The following Dell Technologies resources provide additional information about PowerProtect Data Manager:
The following VMware resources provide additional information about VMware Telco Cloud Platform:
The following Dell Technologies resources provide additional information about OTEL and VMware Telco Cloud Platform:

Flexible Windows Bare-Metal Recovery with PowerProtect Data Manager
Tue, 24 Jan 2023 11:00:27 -0000
|Read Time: 0 minutes
In today’s enterprise, it is certainly not a surprise to hear of a mission-critical application server experiencing downtime or degraded state due to disaster recovery situations, such as hardware failures and cyberattacks. In such situations, bare-metal recovery (BMR) is obviously one of the best disaster recovery solutions. Most users rely on the BMR procedure to restore mission-critical applications, operating environments, and data.
With Dell PowerProtect Data Manager, BMR for a Windows server can be performed efficiently with just a few clicks. Before we explore more about Windows server BMR with PowerProtect Data Manager, let us briefly take a look at BMR.
What is BMR?
BMR, also known as offline recovery, is used as part of a disaster recovery plan that provides protection when a server or a computer will not start after a catastrophic failure. The term bare metal is in reference to a computer without a base operating system or applications. The goal of BMR is to bring a server or computer to the state it was in before the failure.
When is BMR required?
BMR can be used to recover from the following situations:
- To recover a server or a computer entirely after a hardware failure that has been repaired.
- To recover data to a new server or a computer after a hardware failure that cannot be repaired. The new computer does not have an operating system, and the operating system files must also be recovered from the old computer.
BMR of Windows host with PowerProtect Data Manager
Starting with version 19.10, PowerProtect Data Manager supports the file system agent to back up the disaster recovery asset and perform a BMR of a Windows host.
You can use BMR for the following operations:
- Physical machine to physical machine (P2P)
- Physical machine to virtual machine (P2V)
- Virtual machine to virtual machine (V2V)
With PowerProtect Data Manager, you can perform BMR by backing up the disaster recovery asset. When a file system agent backup is performed, there is an extra asset—”disaster recovery”—that is backed up. This asset includes the information required to rebuild the Windows system back to its state at the time of the backup. The data in the disaster recovery asset, plus volume information for those file systems that contain operating system data (critical volumes), are also backed up.
After the disaster recovery asset backup is successful, you can perform the BMR using the customized PowerProtect Data Manager WinPE ISO image. By default, each BMR backup is system state enabled.
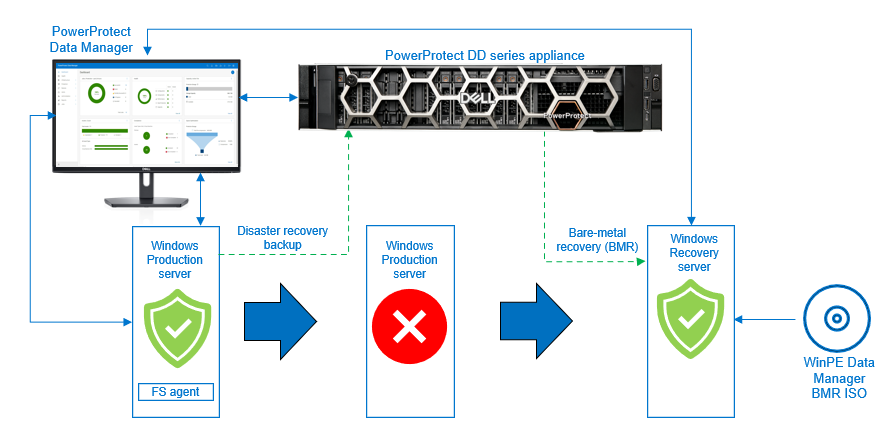
Backing up Windows disaster recovery assets
After you install the file system agent on the Windows file system host and it is approved in the PowerProtect Data Manager UI, the disaster recovery asset is discovered along with the other file system assets.
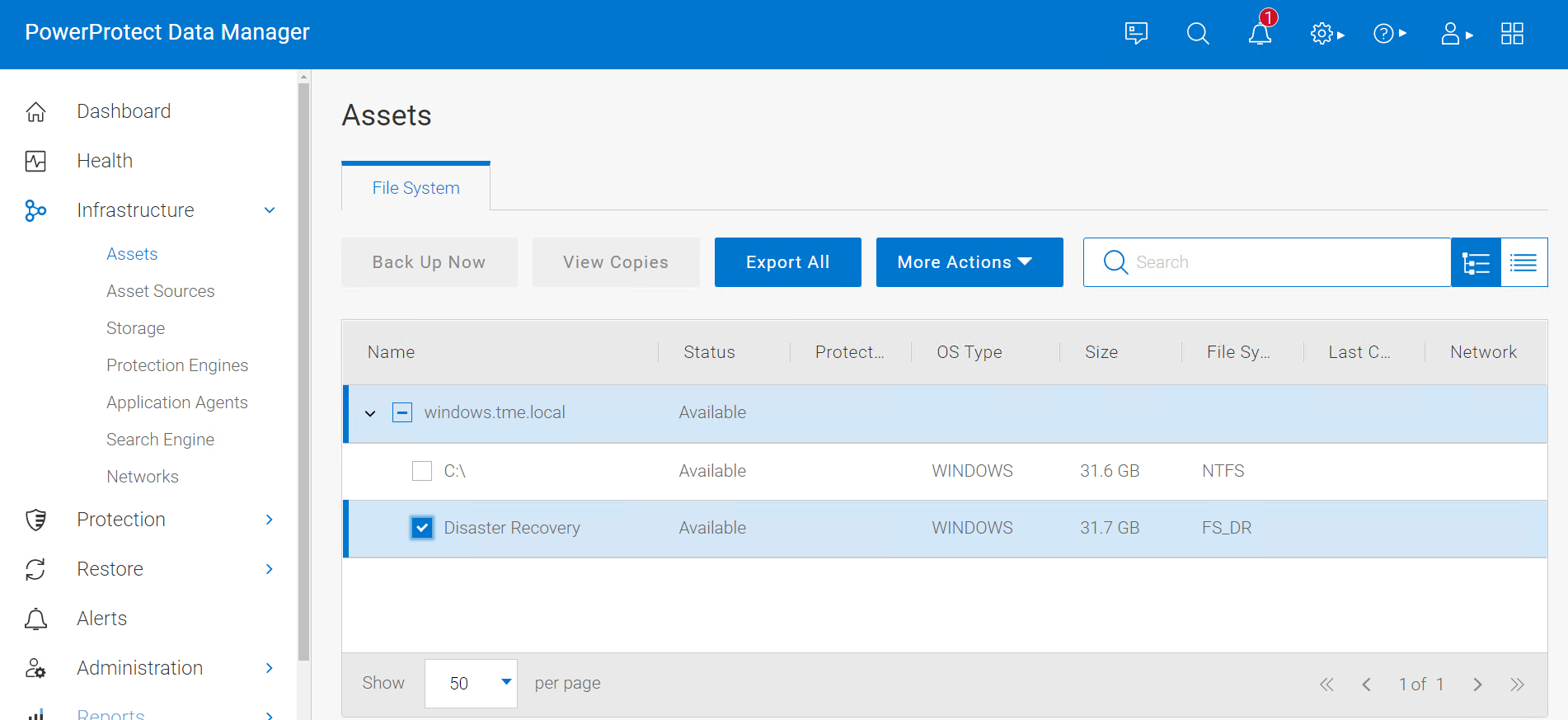
After the disaster recovery asset is discovered in PowerProtect Data Manager UI, you can create a file system protection policy and configure it to back up the disaster recovery asset. A disaster recovery protection policy should contain objects to be backed up, which include critical volumes and system state recovery files.
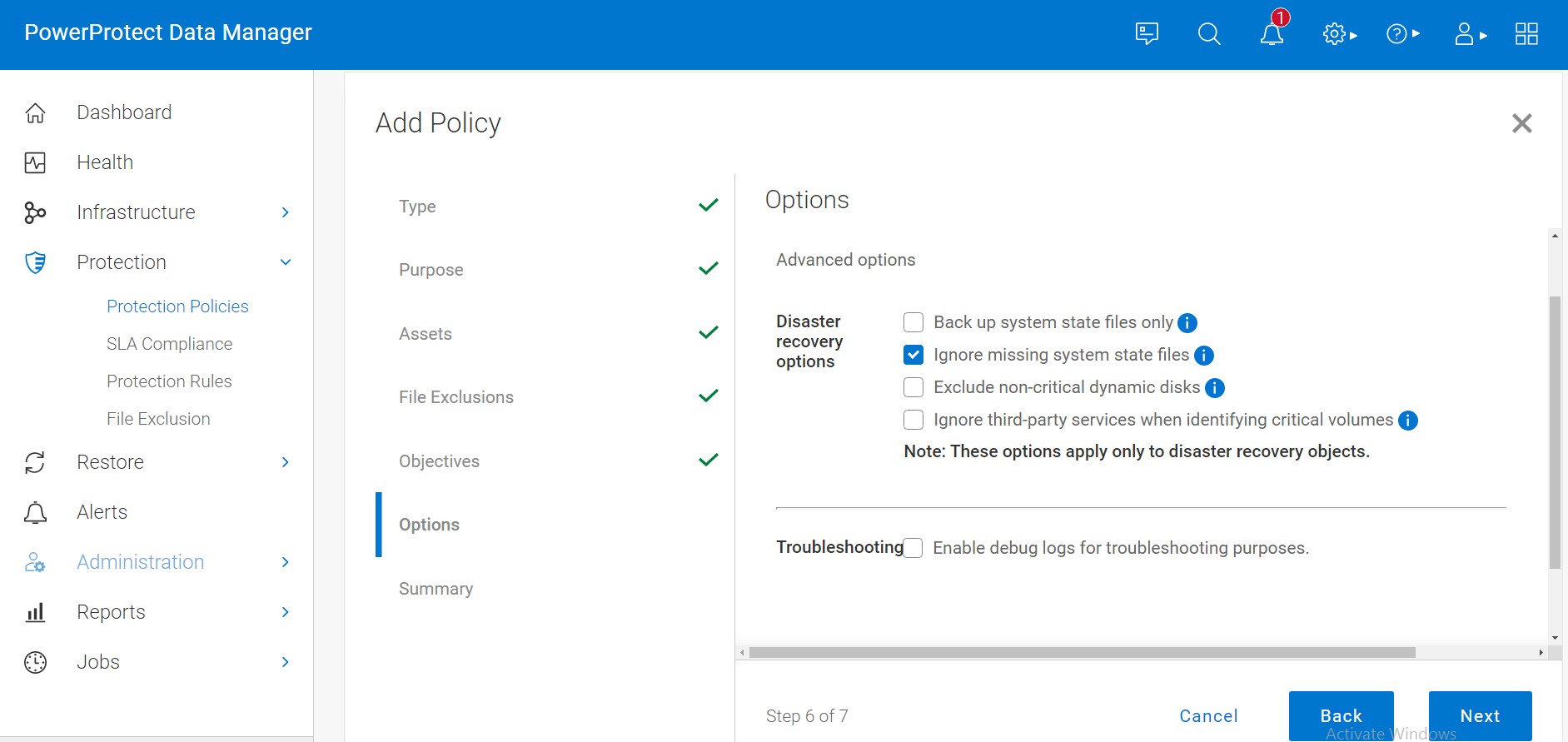
After the disaster recovery asset backup is successful, you can perform BMR using the customized PowerProtect Data Manager WinPE ISO image.
BMR data consists of the following:
- The operating system files and all data except user data on critical volumes
Note: Critical volumes include the boot volume, the system volume, and the volume that hosts system state data, such as Active Directory and application services.
- All system state information
By default, each BMR backup is system state enabled.
To protect a Windows host entirely, we recommend that you back up BMR data for critical volumes and separately back up regular assets that contain user data.
Performing Windows BMR
PowerProtect Data Manager provides a custom WinPE image that allows you to recover a source host to a target host without installing an operating system. Because local disks are not in use by the operating system, the recovery process can replace files without conflict. The custom PowerProtect Data Manager WinPE image is based on Windows PE 10.0 and contains the NIC and disk drivers for the Windows versions that the WinPE image supports.
Before you perform a BMR, verify that the environment meets the requirements and that you have the necessary information.
Note: For BMR requirements, see the the PowerProtect Data Manager File System User Guide.
When a recovery of a system is required, you can download the Windows BMR ISO image from the PowerProtect Data Manager UI. The image contains the necessary files to boot and create a WinPE system. The image includes a PowerProtect Data Manager Bare Metal Recovery Wizard that is launched and used as part of the restore.
Note: Ensure that the hardware on the target computer is operational and that the target computer is similar in make, model, and hardware configuration to the source computer to be recovered. For more details about the BMR requirements, see the PowerProtect Data Manager File System User Guide.
The target host boots with the custom WinPE image, either locally or over the network. The Welcome page of the PowerProtect Data Manager Bare Metal Recovery Wizard is displayed.
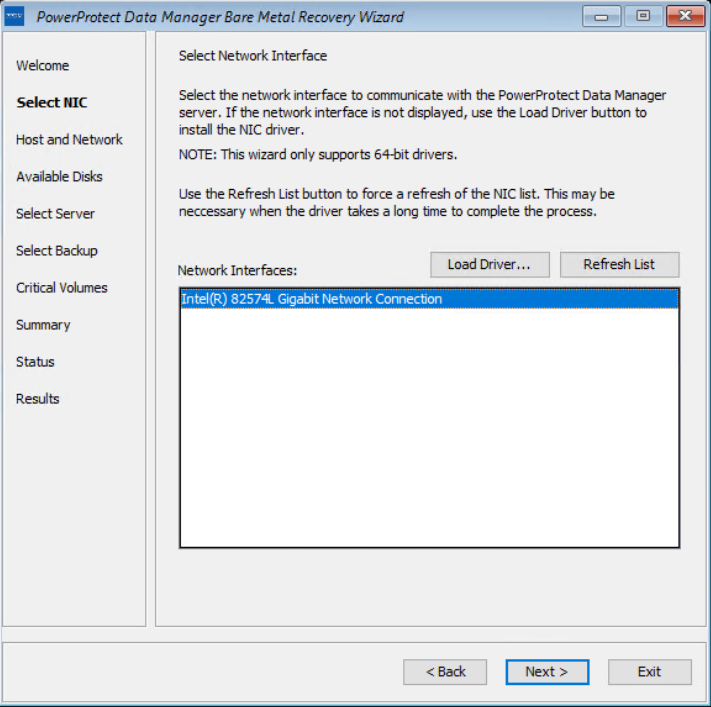
On the Select NIC page, you can select the network interface for communication with Data Manager during the BMR. If the required NIC driver is not in the list, click Load Driver to browse to it.
Note: The driver must not require a restart. The WinPE environment loads only in memory, and changes are not persistent across a restart. If a restart prompt appears, you might be able to ignore the prompt. Most NIC drivers are plug-and-play.
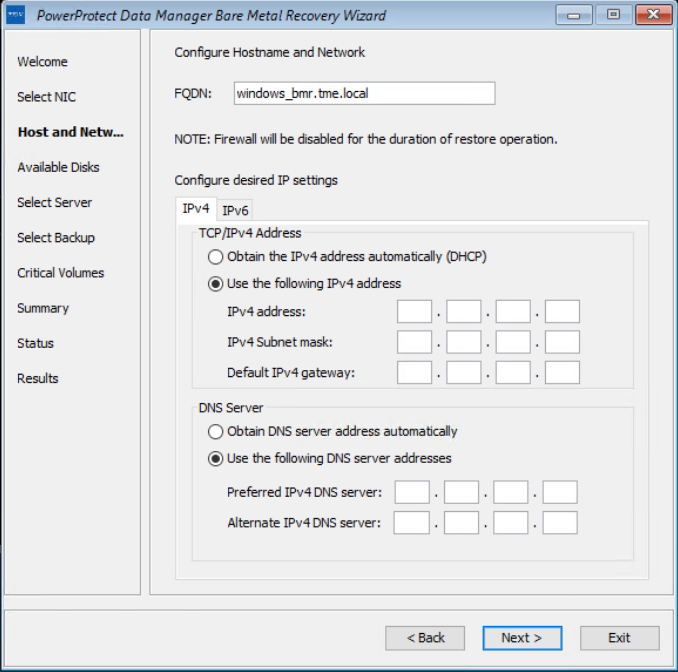
On the Host and Network Configuration page, enter the hostname of the target host and the domain name for the host.
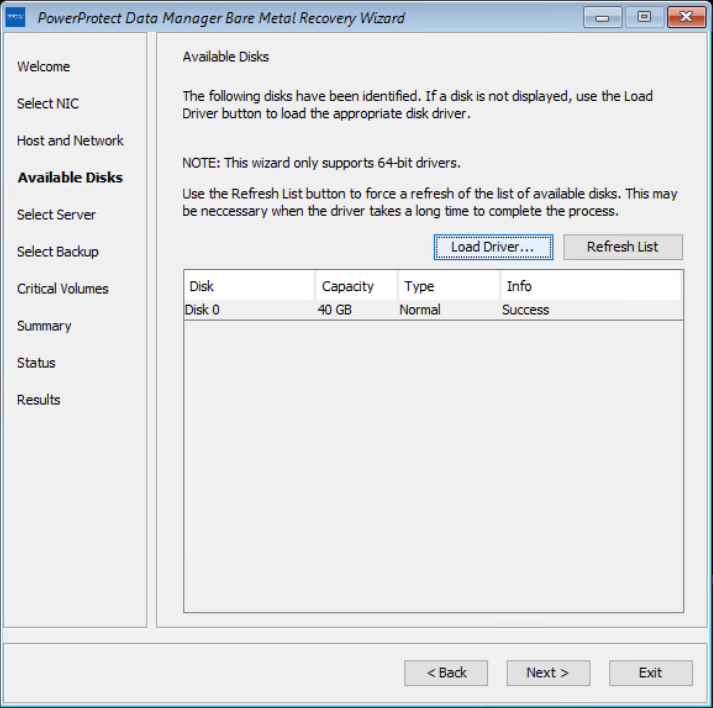
On the Available Disks page, verify the disk configuration. The size and number of hard disks that are added to the target machine should be either equal to or greater than the size and number of disks on the source machine.
On the Select Server page, enter the PowerProtect Data Manager server and source hostname details. In the Server Name or IP field, add the IP of the server or FQDN only.
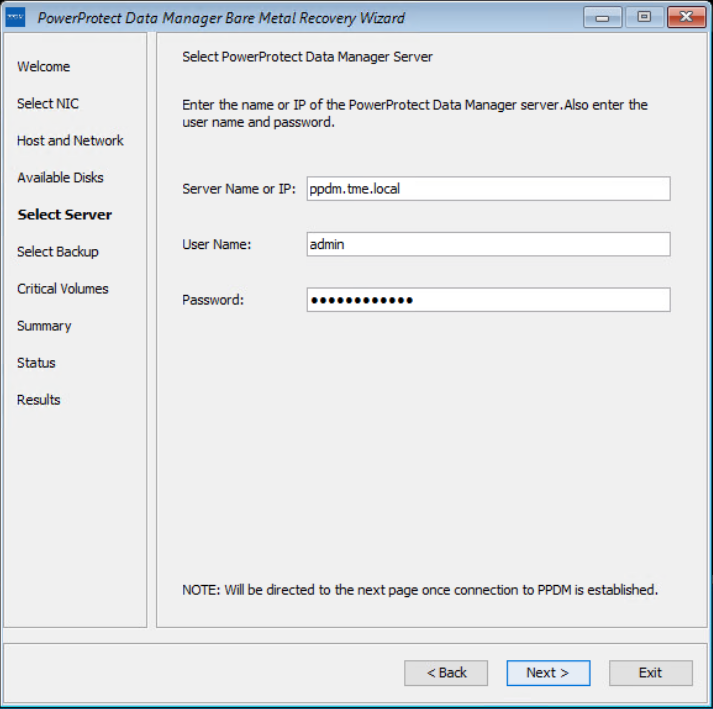
On the Select Backup page, select the respective host from the Source Host Name list and BMR data to restore to the destination host. Backups appear in the list in descending order from the most to least recent.
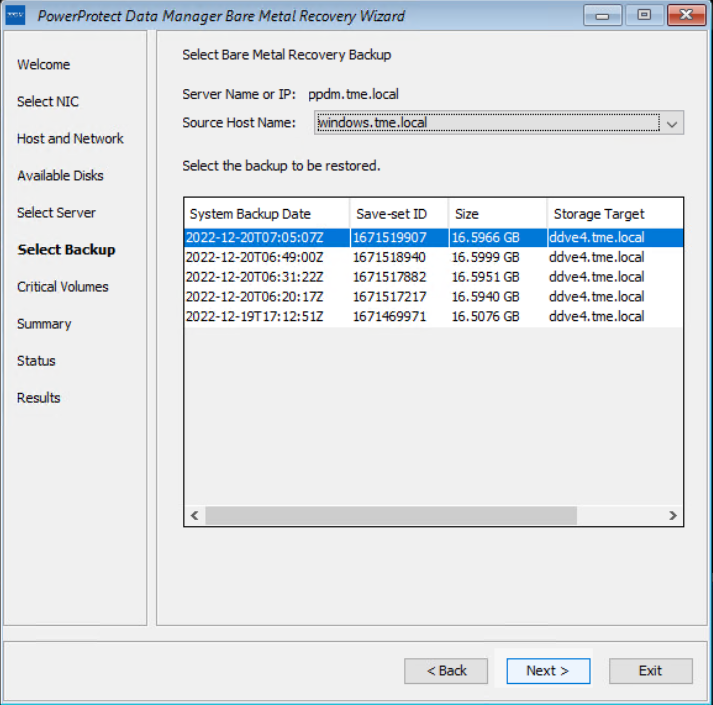
The Critical Volumes page displays the volumes that will be restored and the option to enable a quick disk format.
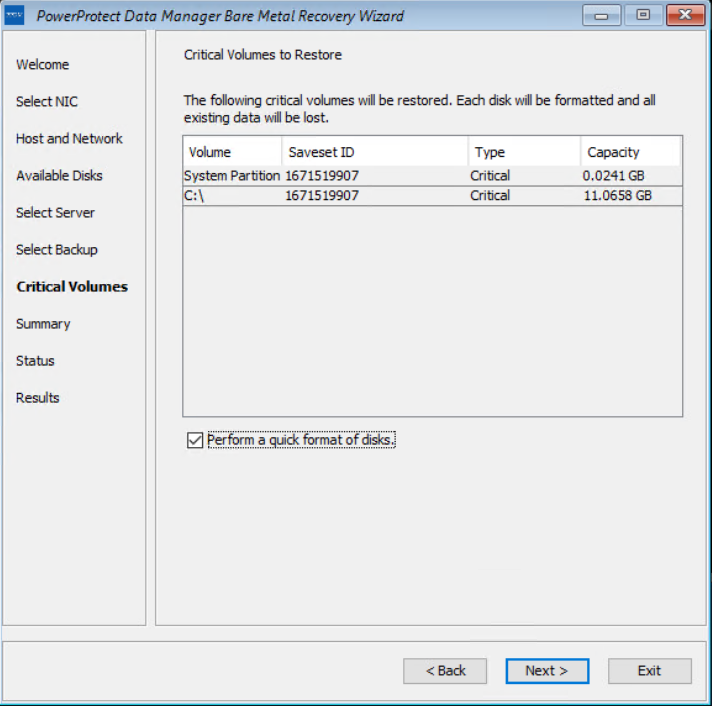
The PowerProtect Data Manager BMR wizard fetches information to perform a BMR, and the Summary page is displayed. To add custom BMR options, next to Custom restore options, click Options.
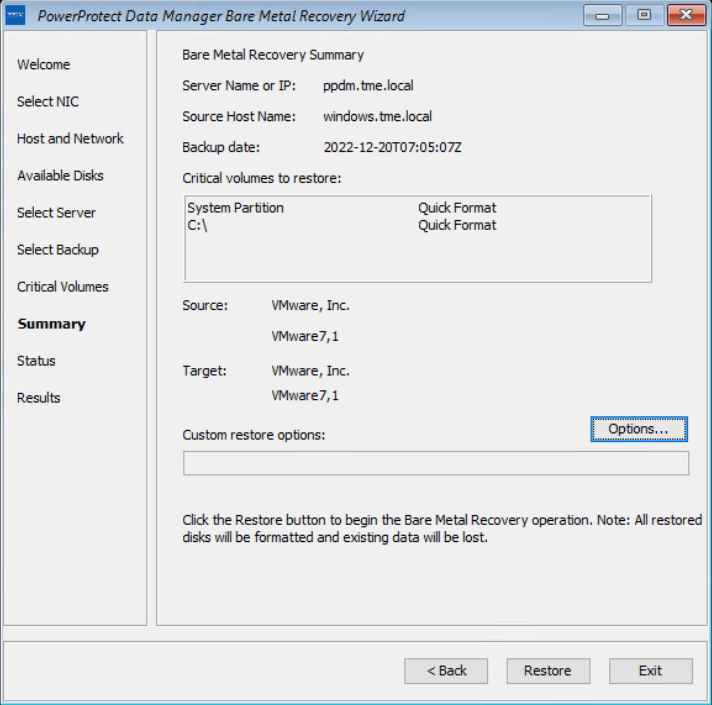
Confirm the quick format of disks and restore the backup.
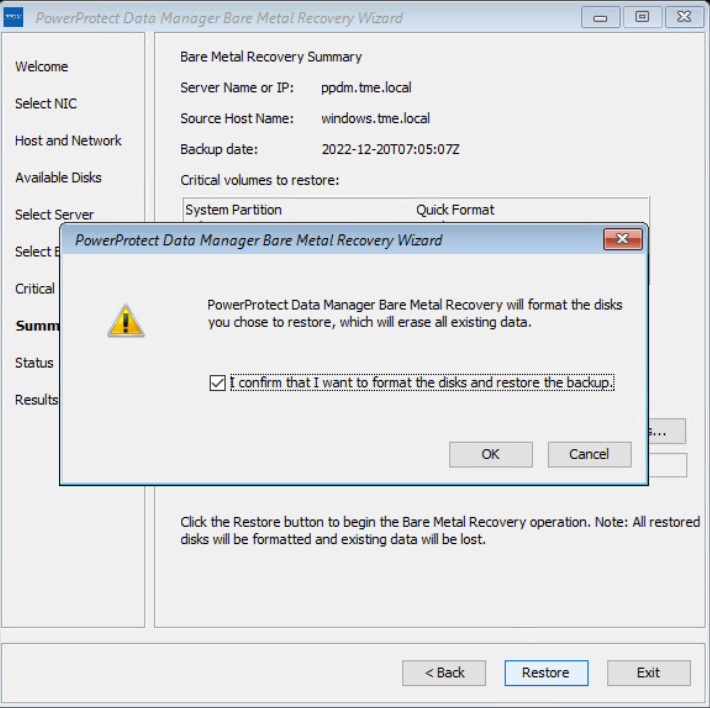
The Status page shows the restore progress.
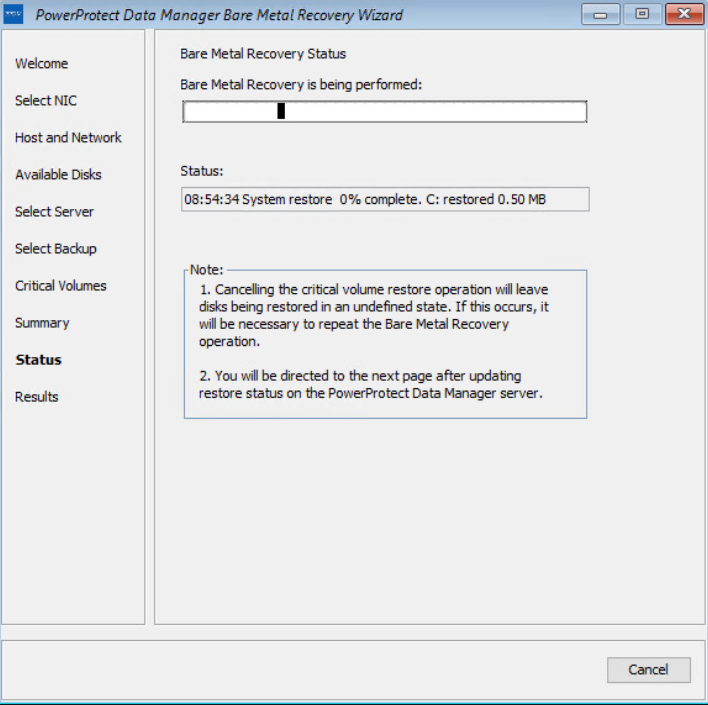
You can also monitor the Bare Metal Recovery job status in the PowerProtect Data Manager UI at Jobs > Protection Jobs.
The BMR wizard displays the results. After the recovery is successful, you can reboot the system and restore the application data as required.
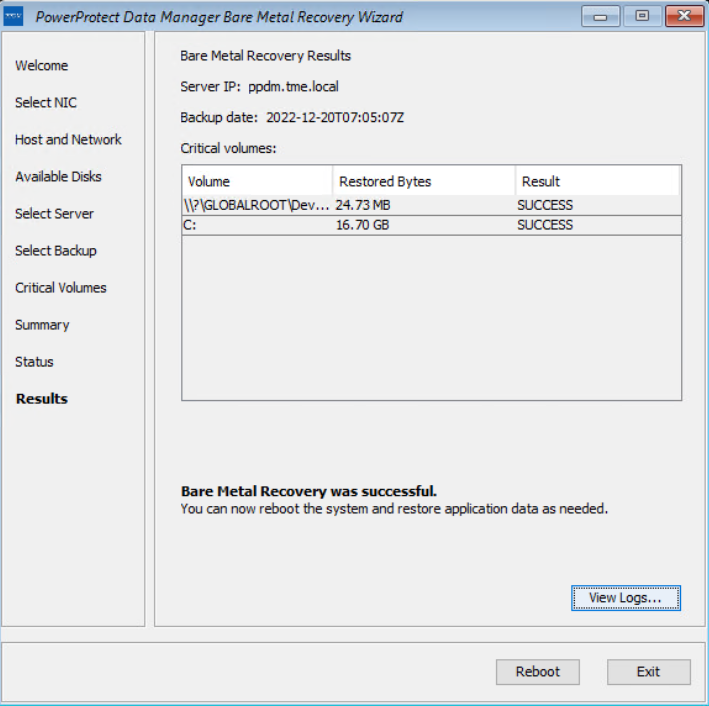
With this easy BMR solution with PowerProtect Data Manager, Dell Technologies empowers Windows administrators to recover their business-critical Windows servers quickly and resume their operations.
For more details about disaster recovery for Windows with PowerProtect Data Manager, see the technical white paper and PowerProtect Data Manager: File System User Guide.
For more details about data protection with PowerProtect Data Manager, see the PowerProtect Data Manager website.
Author: Vinod Kumar Kumaresan, Principal Engineering Technologist, Data Protection Division

Protect your SUSE Rancher managed RKE downstream Kubernetes workloads with Dell EMC PowerProtect Data Manager
Mon, 19 Sep 2022 13:46:53 -0000
|Read Time: 0 minutes
Protect your SUSE Rancher managed RKE downstream Kubernetes workloads with Dell EMC PowerProtect Data Managere

We have been continuously working to extend the level of support for Kubernetes with Dell EMC PowerProtect Data Manager, to protect Kubernetes workloads on different platforms.
With this continued services path, we now protect SUSE Rancher managed Kubernetes workloads with PowerProtect Data Manager by taking advantage of a partnership with SUSE Rancher.
Kubernetes cluster and containers have become a popular option for deploying enterprise applications in the cloud and in on-premise environments. SUSE Rancher is a Kubernetes management platform that simplifies cluster installation and operations, whether they are on-premises, in the cloud, or at the edge, giving the freedom to build and run containerized applications. PowerProtect Data Manager protects SUSE Rancher managed Kubernetes workloads and ensures high availability and consistent, reliable backup and restore for Kubernetes workloads during normal operations or during a disaster recovery situation.
Protect SUSE Rancher managed Rancher Kubernetes Engine (RKE) downstream workloads with PowerProtect Data Manager
PowerProtect Data Manager enables customers to protect, manage, and recover data for on-premises, virtualized, or cloud deployments. Using PowerProtect Data Manager, customers can discover, protect, and restore workloads in a SUSE Rancher managed Kubernetes environment to ensure that the data is easy to backup and restore.
PowerProtect Data Manager enhances the protection by sending the data directly to the Dell EMC PowerProtect DD series appliance to gain benefits from unmatched efficiency, deduplication, performance, and scalability. See the solution brief and this technical white paper for more details.
About SUSE Rancher and RKE
SUSE Rancher is an enterprise computing platform for running Kubernetes for on-premises, cloud, and edge environments. With Rancher, you can form your own Kubernetes-as-a-Service. You can create, upgrade, and manage Kubernetes clusters. Rancher can set up clusters by itself or work with a hosted Kubernetes provider. It addresses the operational and security challenges of managing multiple Kubernetes clusters anywhere. SUSE Rancher also provides IT operators and development teams with integrated tools for building, deploying, and running cloud-native workloads.
SUSE Rancher supports the management of CNCF-Certified Kubernetes distributions, such as Rancher Kubernetes Engine (RKE). RKE is a certified Kubernetes distribution for both bare-metal and virtualized servers.
Protecting data by integrating SUSE Rancher managed RKE downstream Kubernetes clusters with PowerProtect Data Manager
You can integrate PowerProtect Data Manager with SUSE Rancher managed Kubernetes clusters through Kubernetes APIs to discover namespaces and associated persistent resources PersistentVolumeClaims (PVCs). PowerProtect Data Manager discovers the Kubernetes clusters using the IP address or fully qualified domain name (FQDN). PowerProtect Data Manager uses the discovery service account and the token kubeconfig file to integrate with kube-apiserver.
PowerProtect Data Manager integrates with SUSE Rancher managed Kubernetes clusters for data protection in the following ways:
- Directly connecting to the RKE downstream single node with controlplane and etcd roles.
- Through an external load balancer, when there are multiple RKE nodes for high availability with controlplane and etcd roles in an RKE downstream cluster.
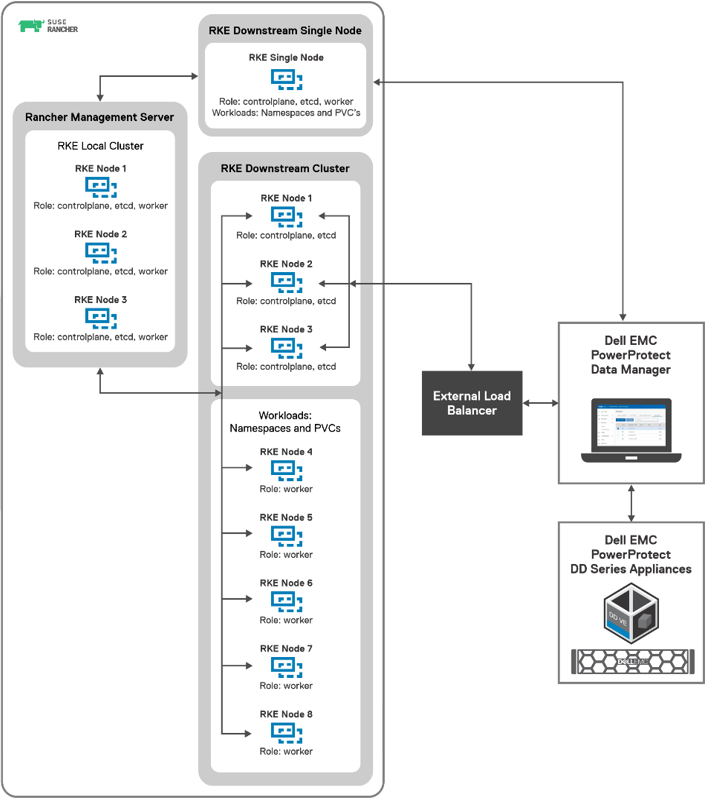
SUSE Rancher managed RKE downstream Kubernetes clusters integration with PowerProtect Data Manager
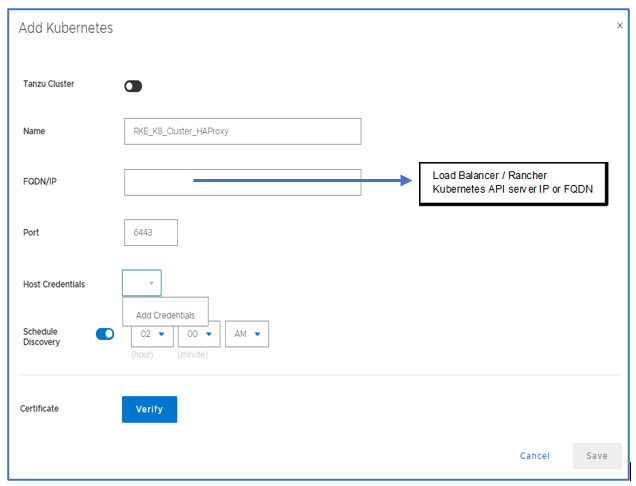
Adding the RKE downstream Kubernetes cluster with PowerProtect Data Manager as an asset source
Once the Kubernetes cluster is added as an asset source in PowerProtect Data Manager and the discovery is complete, the associated namespaces are available as assets for protection. PowerProtect Data Manager protects the following two types of Kubernetes cluster assets - Namespaces and PVCs. Note that PPDM also protects the associated meta data for namespaces and cluster resources that include secrets, ConfigMaps, custom resources, RoleBindings, and so on.
During the discovery process, PowerProtect Data Manager creates the following namespaces in the cluster:
• Velero-ppdm: This namespace contains a Velero pod to back up metadata and stage to target storage in bare-metal environments. It performs PVC snapshot and metadata backup for VMware cloud native storage.
• PowerProtect: This namespace contains a PowerProtect controller pod to drive persistent volume claim snapshot and backup and to send the backups to the target storage using dynamically deployed cProxy pods.
Kubernetes uses persistent volumes to store persisted application data. Persistent volumes are created on external storage and then attached to a particular pod using PVCs. PVCs are included along with other namespaces in PowerProtect Data Manager backup and recovery operations. Dell EMC PowerStore, PowerMax, XtremIO, and PowerFlex storage platforms all come with CSI plugins to support containerized workloads running on Kubernetes.
With this easy integration for data protection with PowerProtect Data Manager, Dell Technologies empowers Kubernetes admins to perform backup/recovery operations and ensure SUSE Rancher managed Kubernetes cluster workloads are available, consistent, durable, and recoverable.
For more details, see the white paper SUSE Rancher and RKE Kubernetes cluster using CSI Driver on DELL EMC PowerFlex about how to protect the SUSE Rancher managed Kubernetes workloads with PowerProtect Data Manager.

Say No to Costly Ransom Demands with APEX Backup Services
Tue, 14 Jun 2022 15:27:47 -0000
|Read Time: 0 minutes
Ransomware attacks are constantly evolving. Whatever you build today will be obsolete sooner than you might expect because multiple groups are constantly releasing new ransomware packages. You need to be able to evolve with them.
Ransomware is a relentless threat to every enterprise and the attacks are becoming more frequent, advanced, and expensive. Ransomware is a form of malicious software or malware that when downloaded to a computer or server, encrypts victims’ data so that threat actors can demand a “ransom” in exchange for a decryption key needed to unlock your data. Even if the ransom is paid, there is no guarantee that the attacker will provide you with the decryption key.
Ransomware attacks today play out across the entire IT infrastructure, targeting all forms of data and requiring a more robust response. In addition to solutions for preventing attacks, organizations need response and data recovery plans that can quickly bring information back online.
How does ransomware work?
Infection and attack vectors
There are several vectors that ransomware can take to access the target system. One of the most common delivery systems is phishing spam attachments or links that come to the victim in an email. When the victim falls for the phish, the ransomware is downloaded and executed on the target system where ransomware starts encrypting the data.
Encrypt data
When ransomware gains access to the system, it begins to encrypt the files. It encrypts the files with an attacker-controlled key and replaces the original files with the encrypted versions.
Ransom demand
When the file encryption is complete, the victim is presented with a message explaining that the files are now inaccessible and will only be decrypted if the victim sends the requested payment to the attacker through an untraceable medium.
Defensive steps to prevent ransomware
Some of the steps that can be taken to prevent ransomware infection include:
- Ensure that the operating system is patched regularly and up to date
- Install antivirus software that detects malicious programs such as ransomware
- Do not install unauthorized software
- Do not open email attachments automatically or trust email attachments with macros
- And of course, frequently back up important data externally
In today’s diverse and distributed IT environment, restoring your organization’s applications and data quickly in the event of a ransomware attack is a significant challenge. Reliable backup and recovery are a crucial line of defense against ransomware.
Dell Technologies APEX Backup Services ransomware recovery
Dell Technologies APEX Backup Services ransomware recovery is a fast, reliable data recovery solution that eliminates any reason to even think of paying a ransom. APEX Backup Services is based on a secure and robust cloud architecture that can help you protect your business assets, limit the impact of ransomware, and accelerate recovery. Data protected in APEX Backup Services cannot be modified or deleted by ransomware. APEX Backup Services can ensure that your backup data is safe, help you operationalize security across your backup and primary environments, and accelerate the recovery process so you can get back to normal faster.
APEX Backup Services empowers security operations and IT teams to protect, detect, respond, and recover faster from external or internal attacks, ransomware, and accidental or malicious data deletion.
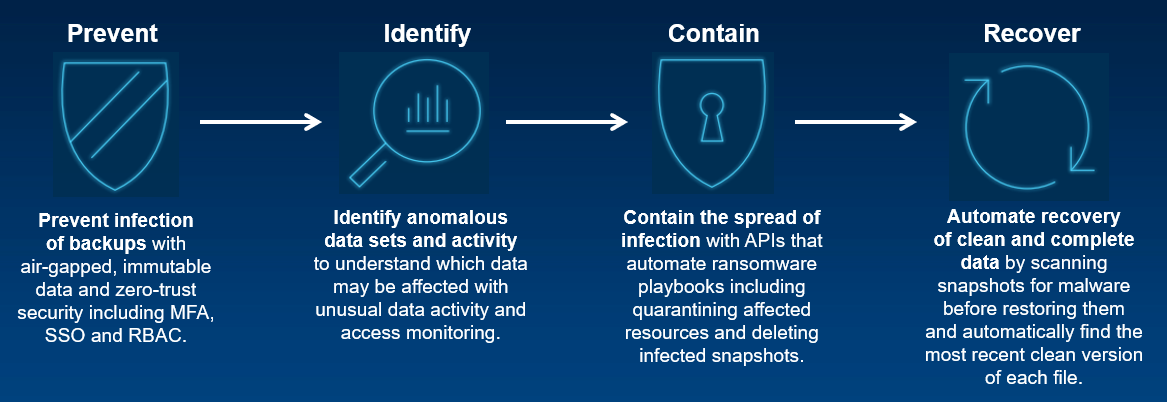
How does APEX Backup Services protect against ransomware?
Zero-trust security and immutable backups
Prevent infection of backups with air-gapped, immutable data and zero-trust security including MFA (multi-factor authentication), single sign-on (SSO) and role-based access control (RBAC).
APEX Backup Services was designed around a zero-trust security architecture and offers rich multi-layered defense features including MFA. Built natively on AWS’s security framework, APEX Backup Services also inherits the global security, compliance, and data residency controls, thus adhering to the highest standards for privacy and data security.
APEX Backup Services provides RBAC. It is strongly recommended to ensure that only a small group of administrators can perform destructive actions such as deleting backup data.
APEX Backup Services offers immutable protection in which backup data is isolated from the customer’s network and protected within the APEX Backup Services platform.
Another key to security is encryption for data, both in flight and at rest. APEX Backup Services provides a secure, multi-tenant environment for customer data. APEX Backup Services encrypts the data using envelope encryption technology, making it impossible for anyone other than the customer to access the data.
Unusual data activity monitoring and user access insights
Identify anomalous data sets and activity to understand which data may be affected with unusual data activity and access monitoring.
Suspicious modification of data on a resource is called Unusual Data Activity (UDA). A user or malicious software can make such changes. The UDA feature with APEX Backup Services provides continuous monitoring of your backup data. With UDA and access monitoring, you can identify anomalous data sets and activity to understand which data might be affected. Our proprietary entropy-based algorithm uses machine learning (ML) to understand norms for your specific backup environment and provides automated alerts for unusual data activity, including bulk deletion and encryption.
APEX Backup Services offers “Security Events”, a dashboard that shows you upfront the count of all administrator login events, data access events, API requests, and unusual data activity alerts, and nudges you to take remedial actions if required. This data helps you gain situational awareness about the backed-up data by gathering events from all APEX Backup Services products.
The APEX Backup Services accelerated ransomware recovery module provides access insights and anomaly detection that help you quickly identify possible ransomware attacks. The APEX Backup Services dashboard provides a single pane of glass where you can see all access attempts and activity across all your data sources. You can use these insights to quickly identify affected snapshots during recovery.
Contain the spread of infection and orchestrate response using API based integrations
Contain the spread of infection with APIs that automate ransomware playbooks, including quarantining affected resources and deleting infected snapshots.
The APEX Backup Services accelerated ransomware recovery enables you to quarantine infected snapshots on the impacted resources, which helps safeguard your system from further infection by barring users or administrators from downloading or restoring data to other resources.
The APEX Backup Services accelerated ransomware recovery module offers robust API integrations that make it easy to fit the solution into your overall security ecosystem. Orchestrating response activities using security information and event management (SIEM) and Security orchestration, automation, and response (SOAR) solutions can dramatically reduce your mean time to respond (MTTR) by automatically completing actions such as quarantining infected systems or snapshots based on a predetermined ransomware playbook.
After you quarantine snapshots, access to the quarantined snapshots is blocked for the administrators and the users of that resource. Administrators and users cannot download data or restore data from the quarantined snapshots.
Automated recovery with curated snapshots
Automate the recovery of clean and complete data by scanning snapshots for malware before restoring them and automatically find the most recent clean version of each file.
The APEX Backup Services cloud platform backs up workloads directly to the cloud, so that they are ready for immediate recovery in the event of a ransomware attack. The accelerated ransomware recovery module enables you to recover with confidence by ensuring the hygiene of recovery data.
You can scan snapshots for malware and IOCs (indicators of compromise) using built-in antivirus detection or using threat intelligence from your own forensic investigations or threat intel feeds. Scanning snapshots before recovery eliminates reinfection.
Accelerated ransomware recovery also solves the problem of data loss due to point-in-time recovery. Flexible recovery options allow you to restore full backups or specific files from a previous point in time. Now you can automatically identify the most recent clean version of every file within a specified timeframe and consolidate those versions into a single “Golden Snapshot”. Eliminating the manual search and recovery process drastically reduces time to recovery and prevents data loss.
The Curated Recovery feature automatically finds the most recent clean version of every file and compiles it into a single curated snapshot. 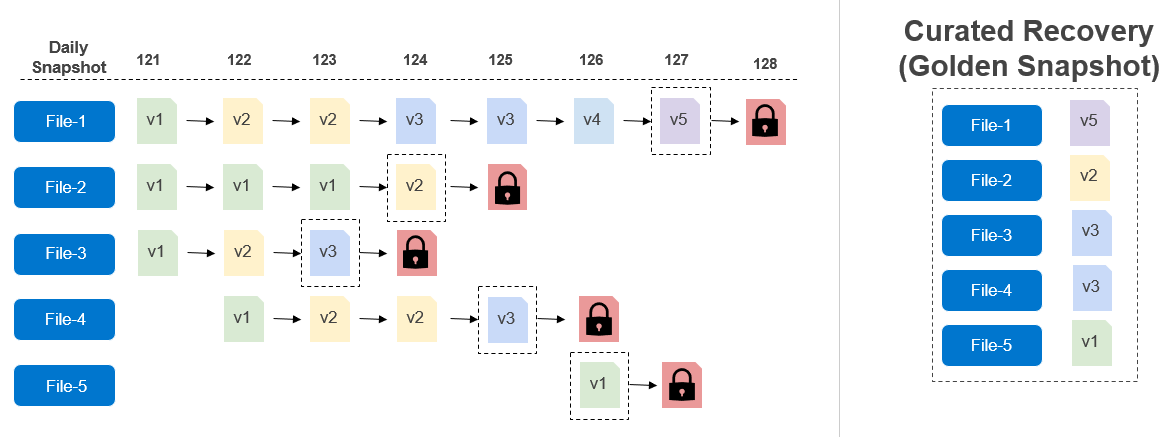
It is unlikely that paying will resolve the problem or allow the victim to recover the encrypted data. It may even make the situation worse, confirming for the hacker that they have found a good target. By selecting the right ransomware recovery solution, you can ensure that your organization has a rock-solid multi-layer defense plan in place to reduce the impact of ransomware or malware.
With APEX Backup Services accelerated ransomware recovery solution, you’ll be far less vulnerable to costly ransom demands and debilitating downtime. The APEX Backup Services cloud-based ransomware protection and accelerated ransomware recovery module prevent data loss, reduce costs, and accelerate ransomware attack response and recovery.
For more details about APEX Backup Services ransomware recovery, visit the dell.com/apex-backup-services website.
Author: Vinod Kumar Kumaresan, Principal Engineering Technologist, Data Protection Division

Conquer Your Challenges with Dell PowerProtect Data Manager Dynamic NAS Protection
Wed, 16 Feb 2022 21:53:54 -0000
|Read Time: 0 minutes
Challenges when protecting NAS
For years, NAS and backup vendors have used Network Data Management Protocol (NDMP) to protect NAS data. But NDMP has its own limitations, such as manual slicing of a NAS share to achieve multi-stream backup, limited parallel streams, and requires periodic full backups. Customers also face challenges to protect their growing amounts of data and to back up that data within their specified backup windows. With NDMP, full image restores are required for a file-level recovery and restore to any NAS device, such as NFS/CIFS, are not supported. These challenges lead to missed data protection and Service Level Agreements (SLAs).
PowerProtect Data Manager Dynamic NAS protection
Dell PowerProtect Data Manager for NAS protection addresses today’s customer challenges of protecting evolving NAS environments. In the PowerProtect Data Manager 19.9 software release, we introduced a new NAS data protection solution called Dynamic NAS protection. Unlike NDMP-based solutions, Dynamic NAS protection is a NAS-vendor-agnostic solution. With Dynamic NAS protection, customers can overcome some of the challenges they faced with NDMP.
Dynamic NAS protection addresses the challenges with the following capabilities:
- Vendor-agnostic solution for NAS protection
- Forever incremental backup
- High number of parallel streams and multiple virtual containers to address scale and performance
- Index, search, and restore
- Restore to any NAS device, such as NFS/CIFS
Dynamic NAS protection provides a non-NDMP, crawl- and backup-based solution by leveraging the NAS Protection Engine internally using Filesystem Agents (FSA) file based-backup (FBB) technology.
Dynamic NAS protection uses the NAS Protection Engine for backup and recovery orchestration. This solution is easy to use, providing automatic discovery, orchestration, and management through the Data Manager UI.
Data Manager for NAS protection solution supports all the Data Manager objectives such as DD Replication, Cloud Tier, progress monitoring, and SLA compliance.
Dynamic NAS protection - Intelligent auto slicer
The NAS file share auto slicer is a new library that is embedded in the Data Manager NAS agent. The slicer splits NAS assets (NAS share, a file system) into multiple sub-assets in preparation for multi-stream data movement to a Dell PowerProtect DD series appliance. Slices are created using parallel threads, and each slice is backed up concurrently using available NAS Protection Engine containers and moved to a PowerProtect DD series appliance.
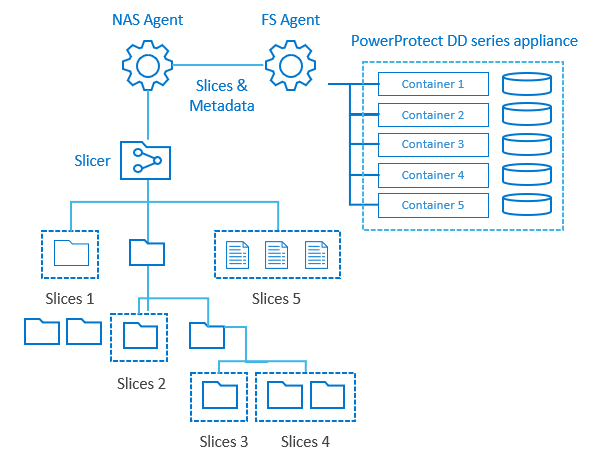
The slicer partitions NAS assets dynamically before each backup. Based on backup history and changes in the content of the NAS asset being sliced, relevant slices are added, removed, or rebalanced. Periodically, unbalanced trees are automatically managed as content changes over time. No manual reconfiguration is required. The default slice size is 200 GB or 1 million files.
For a full backup, a complete share is traversed in parallel to create slices. For an Incremental backup, only modified slices are traversed based on backup history.
Auto distribution of backup streams
Dynamic NAS protection enables automated load balancing of protection engine hosts, and automatic scaling for containers to achieve maximum backup streams and reduce manual management overhead. The NAS protection containers spin up and tear down, depending upon the workload. Each NAS Protection Engine can run multiple containers. Each container is pre-installed with a NAS agent and an FSA agent.
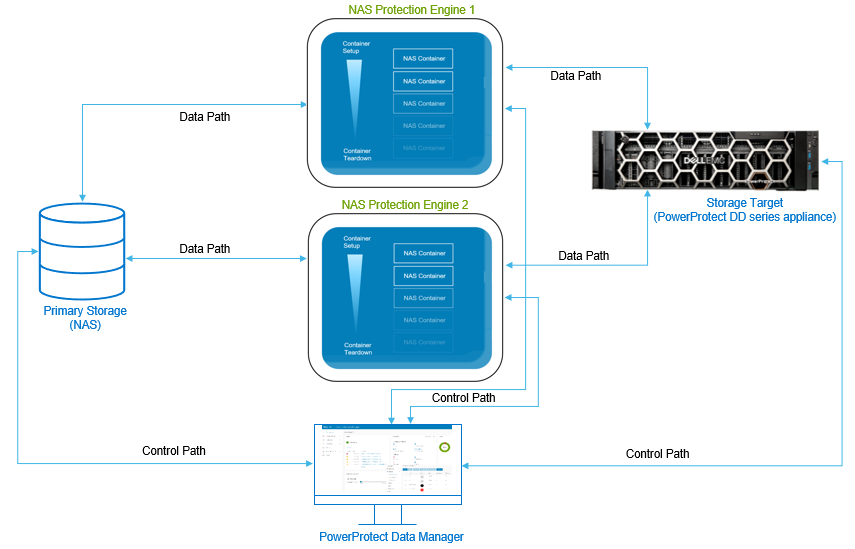
Protecting NAS assets with Data Manager
With the Data Manager 19.9 software release, the Dynamic NAS solution supports protection for Dell PowerStore, Dell Unity, and Dell PowerScale (Isilon) NAS products, and any NFS or CIFS share using generic NAS for vendors such as NetApp, Windows, and Linux file servers.
Data Manager can protect NAS assets in two ways:
- Appliances: Automatic discovery of shares on supported Dell PowerStore, Dell Unity, and Dell PowerScale (Isilon) products.
- Shares: Network File System (NFS) and Common Internet File System (CIFS) shares from other NAS platforms.
Restoring the NAS assets with Data Manager
Data Manager provides support to restore a NAS asset to the original location or to an alternate location. Data Manager also supports FLR using the search engine to restore individual files and folders from NAS backups. Once the Search Engine is deployed and NAS protection policy is enabled with indexing, individual files and folders can be restored from one or more NAS backups by using the File Search option.
Data Manager for NAS protection supports the following restore use cases:
- Share-level restore
- Restore to any device, NFS or CIFS
- Restore to original and alternate NAS shares
- File-Level Recovery (FLR): NAS backups are indexed on the Search Engine for search and restore operations.
With many enhancements across our Dell data protection software offerings, Dell Technologies continues to drive innovation without compromise. We stop at nothing to give you technology innovations that modernize the protection of your NAS infrastructure.
Easily automate and optimize with Dynamic NAS protection available with Data Manager. With its snapshot technology and intelligent slicing, Data Manager protects NAS data efficiently within the required backup window. Dynamic NAS protection offers up to 3x faster backups[1] and up to 2x faster restores[2].
For more details on Data Manager Dynamic NAS protection, see the white paper Dell PowerProtect Data Manager: Dynamic NAS Protection and visit the Dell PowerProtect Data Manager web site.
Author: Vinod Kumar Kumaresan, Senior Engineering Technologist, Data Protection Division
[1] When comparing PowerProtect Data Manager 19.9 with Dynamic NAS protection backup performance to NDMP backup performance with Avamar. Based on Dell internal testing. August 2021.
[2] When comparing PowerProtect Data Manager 19.9 with Dynamic NAS protection restore performance to NDMP restore performance with Avamar. Based on Dell internal testing. August 2021.

Protect your SUSE Rancher managed RKE downstream Kubernetes workloads with Dell EMC PowerProtect Data Manager
Thu, 09 Dec 2021 15:43:42 -0000
|Read Time: 0 minutes
We have been continuously working to extend the level of support for Kubernetes with Dell EMC PowerProtect Data Manager, to protect Kubernetes workloads on different platforms.
With this continued services path, we now protect SUSE Rancher managed Kubernetes workloads with PowerProtect Data Manager by taking advantage of a partnership with SUSE Rancher.
Kubernetes cluster and containers have become a popular option for deploying enterprise applications in the cloud and in on-premise environments. SUSE Rancher is a Kubernetes management platform that simplifies cluster installation and operations, whether they are on-premises, in the cloud, or at the edge, giving the freedom to build and run containerized applications. PowerProtect Data Manager protects SUSE Rancher managed Kubernetes workloads and ensures high availability and consistent, reliable backup and restore for Kubernetes workloads during normal operations or during a disaster recovery situation.
Protect SUSE Rancher managed Rancher Kubernetes Engine (RKE) downstream workloads with PowerProtect Data Manager
PowerProtect Data Manager enables customers to protect, manage, and recover data for on-premises, virtualized, or cloud deployments. Using PowerProtect Data Manager, customers can discover, protect, and restore workloads in a SUSE Rancher managed Kubernetes environment to ensure that the data is easy to backup and restore.
PowerProtect Data Manager enhances the protection by sending the data directly to the Dell EMC PowerProtect DD series appliance to gain benefits from unmatched efficiency, deduplication, performance, and scalability. See the solution brief and this technical white paper for more details.
About SUSE Rancher and RKE
SUSE Rancher is an enterprise computing platform for running Kubernetes for on-premises, cloud, and edge environments. With Rancher, you can form your own Kubernetes-as-a-Service by creating, upgrading, and managing Kubernetes clusters. Rancher can set up clusters by itself or work with a hosted Kubernetes provider. It addresses the operational and security challenges of managing multiple Kubernetes clusters anywhere. SUSE Rancher also provides IT operators and development teams with integrated tools for building, deploying, and running cloud-native workloads.
SUSE Rancher supports the management of CNCF-Certified Kubernetes distributions, such as Rancher Kubernetes Engine (RKE). RKE is a certified Kubernetes distribution for both bare-metal and virtualized servers.
Protecting data by integrating SUSE Rancher managed RKE downstream Kubernetes clusters with PowerProtect Data Manager
You can integrate PowerProtect Data Manager with SUSE Rancher managed Kubernetes clusters through Kubernetes APIs to discover namespaces and associated persistent resources PersistentVolumeClaims (PVCs). PowerProtect Data Manager discovers the Kubernetes clusters using the IP address or fully qualified domain name (FQDN). PowerProtect Data Manager uses the discovery service account and the token kubeconfig file to integrate with kube-apiserver.
PowerProtect Data Manager integrates with SUSE Rancher managed Kubernetes clusters for data protection in the following ways:
- Directly connecting to the RKE downstream single node with controlplane and etcd roles.
- Through an external load balancer, when there are multiple RKE nodes for high availability with controlplane and etcd roles in an RKE downstream cluster.
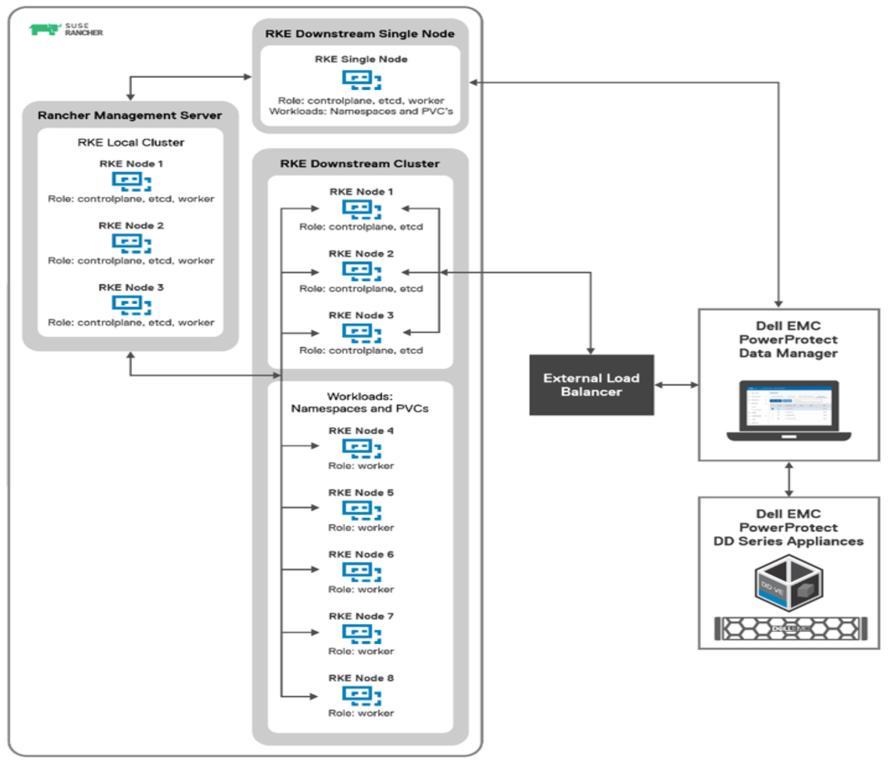
SUSE Rancher managed RKE downstream Kubernetes clusters integration with PowerProtect Data Manager
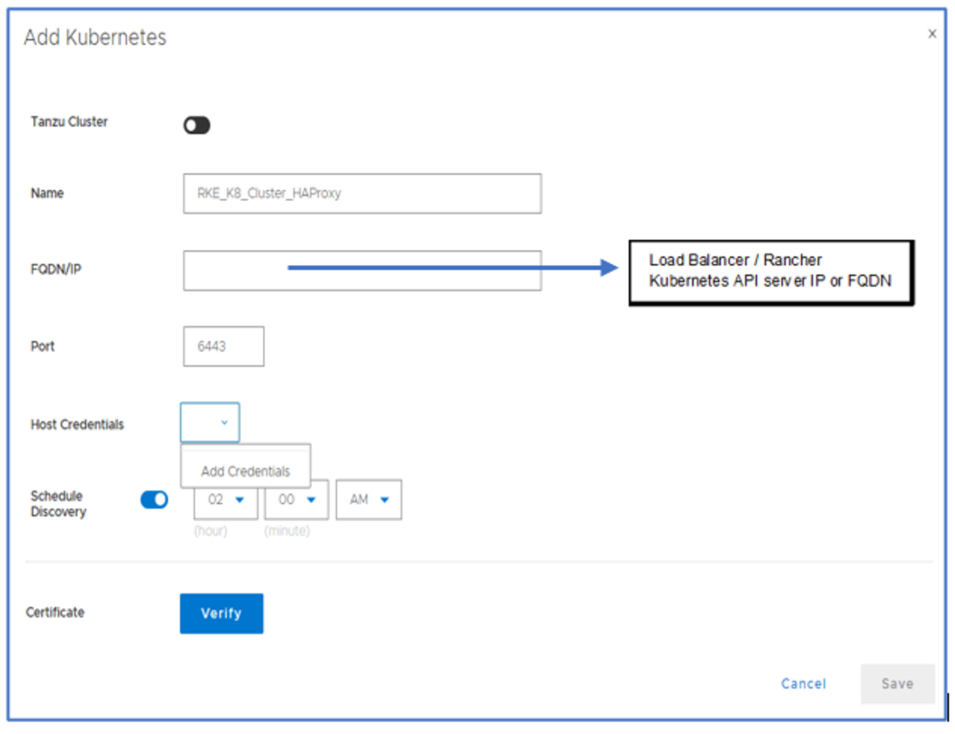
Adding the RKE downstream Kubernetes cluster with PowerProtect Data Manager as an asset source
Once the Kubernetes cluster is added as an asset source in PowerProtect Data Manager and the discovery is complete, the associated namespaces are available as assets for protection. PowerProtect Data Manager protects two types of Kubernetes cluster assets: Namespaces and PVCs. Note that PPDM also protects the associated metadata for namespaces and cluster resources that include secrets, ConfigMaps, custom resources, RoleBindings, and so on.
During the discovery process, PowerProtect Data Manager creates the following namespaces in the cluster:
- Velero-ppdm: This namespace contains a Velero pod to back up metadata and stage to target storage in bare-metal environments. It performs PVC snapshot and metadata backup for VMware cloud native storage.
- PowerProtect: This namespace contains a PowerProtect controller pod to drive persistent volume claim snapshot and backup, and to send the backups to the target storage using dynamically deployed cProxy pods.
Kubernetes uses persistent volumes to store persisted application data. Persistent volumes are created on external storage and then attached to a particular pod using PVCs. PVCs are included along with other namespaces in PowerProtect Data Manager backup and recovery operations. Dell EMC PowerStore, PowerMax, XtremIO, and PowerFlex storage platforms all come with CSI plugins to support containerized workloads running on Kubernetes.
With this easy integration for data protection with PowerProtect Data Manager, Dell Technologies empowers Kubernetes admins to perform backup/recovery operations and ensure that SUSE Rancher managed Kubernetes cluster workloads are available, consistent, durable, and recoverable.
For more details, see the white paper SUSE Rancher and RKE Kubernetes cluster using CSI Driver on DELL EMC PowerFlex about how to protect SUSE Rancher managed Kubernetes workloads with PowerProtect Data Manager.
Author: Vinod Kumaresan