Home > Storage > PowerScale (Isilon) > Product Documentation > Data Protection > PowerScale: AntiVirus Solutions > Architecture overview
Architecture overview
-
OneFS enables file-system scanning for viruses, trojans, malware, and other security threats on an PowerScale cluster by integrating with third-party scanning services through ICAP. OneFS sends files through ICAP to a server running third-party antivirus scanning software. These servers are referred to as ICAP servers. Files are scanned for threats on ICAP servers, not the cluster itself.
The overall architecture and the data flow are shown in the following figure.
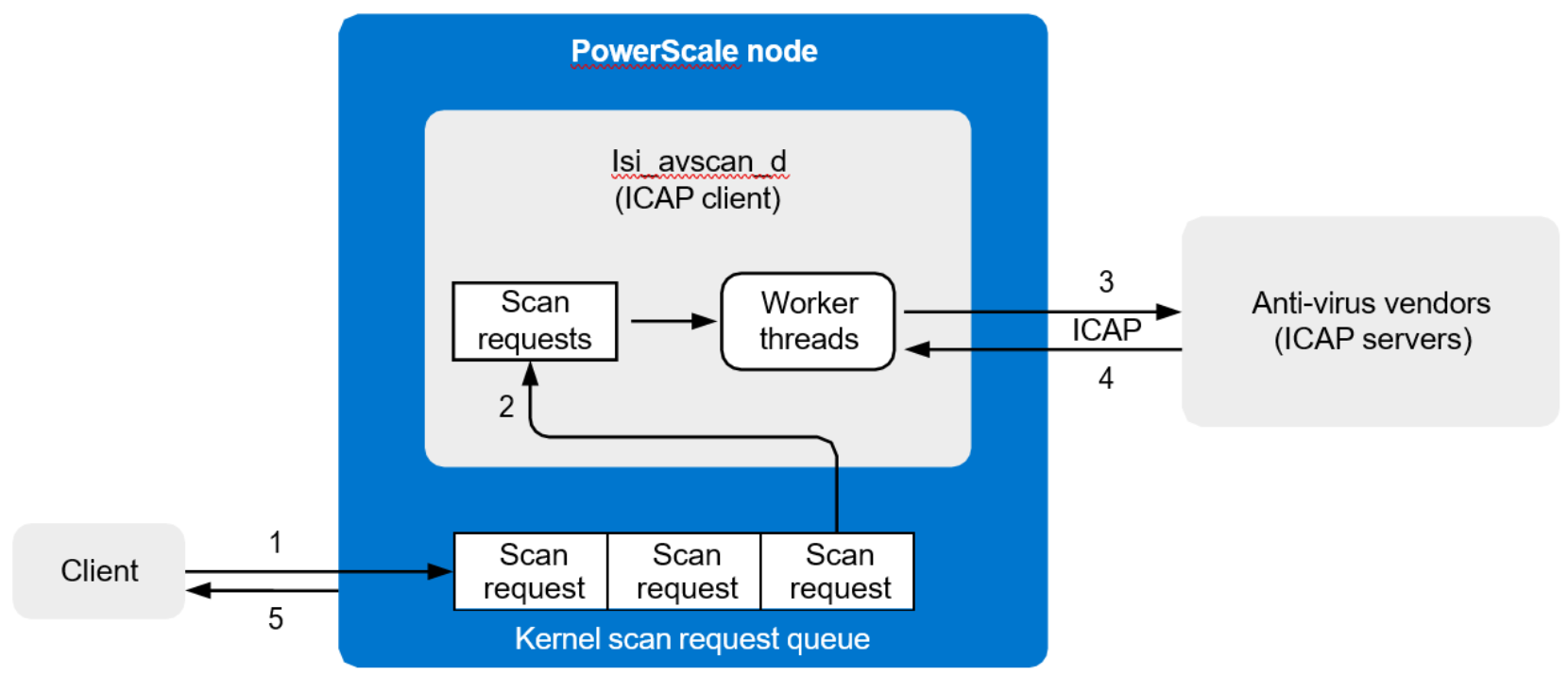
Figure 1. Architecture overview
The following steps occur when a file is scanned as it is opened:
- The end-user requests a file from the cluster.
- The kernel checks if the file scan can be skipped. For example, a file may be skipped if it has not been modified since the last scan, and if there are no updates for the antivirus definition file. If it cannot be skipped, it is placed in the kernel scan request queue.
- The isi_avscan_d process on each PowerScale node reads the kernel scan request queue. There is also filter in the user space. The isi_avscan_d process checks to see if the file should be excluded by path or by glob filter. If the scan request is not filtered out, it is assigned a worker thread which sends the file to an external ICAP server.
- The ICAP server examines the file and determines if it is clean or needs repair or quarantine. If clean, the server responds to isi_avscan_d and the file is marked as safe with metadata such as ISTag, the last scan date, and other attributes.
For more details on ISTag, refer to Updating the virus definition file.
- The PowerScale cluster serves the file to the end user.
