Encryption types offered by DD series encryption appliance
Home > Data Protection > PowerProtect DD Series Appliances > PowerProtect DD Series Appliances: Encryption Software > Encryption types offered by DD series encryption appliance
Encryption types offered by DD series encryption appliance
-
There are three types of encryption offered with DD series appliances:
- Inline encryption of data at rest using the DD Encryption feature
- Encryption of data in-flight using DD Replicator software, which is used for replicating data between sites over the WAN
- Encryption of data in-flight using DD Boost software, using Transport Layer Security (TLS)
Inline encryption of data at rest using DD Encryption
DD Encryption provides inline encryption. As data is ingested, the stream is deduplicated, compressed, and encrypted using an encryption key before it is written to the RAID group. DD Encryption uses RSA BSAFE libraries, which are validated according to the Federal Information Processing Standards (FIPS) 140-2.
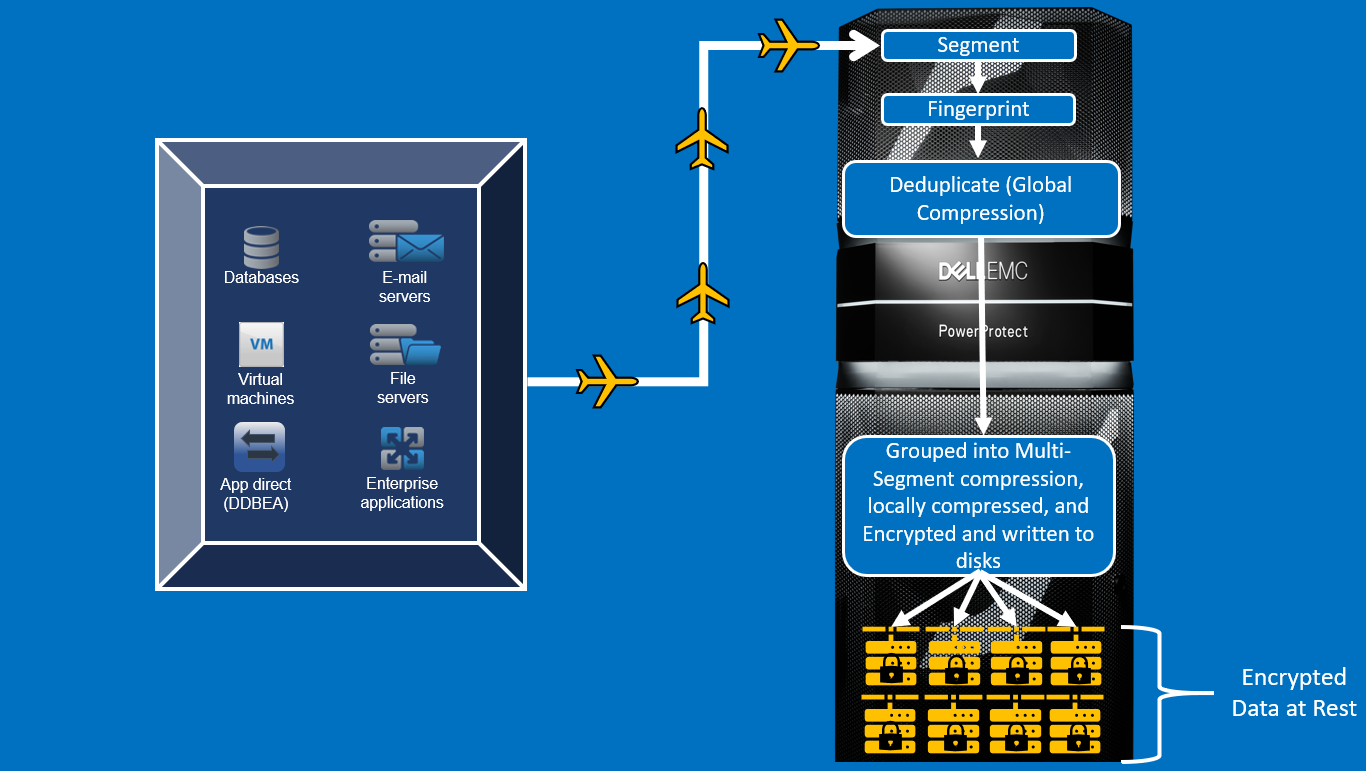
Figure 2. DD Encryption overview
Encryption is not enabled by default. When enabled, the Embedded Key Manager (EKM) is in effect. DD series appliances also support external key managers (SafeNet KeySecure and Vormetric Data Security Manager) that are compliant with the Key Management Interoperability Protocol (KMIP). External Certificate Authority (CA) and host certificates are required to set up SafeNet KeySecure Key Manager (KMIP). You can request these certificates from third-party certificate authorities or create them using the appropriate OpenSSL utility. If encryption is enabled on Cloud Tier, only EKM is supported.
You can select one of two cipher modes, Cipher Block Chaining (CBC) mode or Galois/Counter mode (GCM), to best fit your security and performance requirements. GCM is the most secure algorithm, but it is slower than the CBC mode. The system also uses a user-defined passphrase to encrypt that key before it is stored in multiple locations on disk. The system encryption key cannot be changed and is not accessible to a user. Without the passphrase, the file system cannot be unlocked, and data is not accessible. For more information, see the document Dell EMC DD OS Version 7.3 Administration Guide (may require login).
Encryption of data in flight using DD Replicator
Encryption of data in flight encrypts data that is being transferred using DD Replicator between two DD series appliances. It uses AES 256-bit encryption to encapsulate the replicated data over the wire. The encryption-encapsulation layer is immediately removed when it transfers to the destination system. Data within the payload can also be encrypted using DD Encryption.
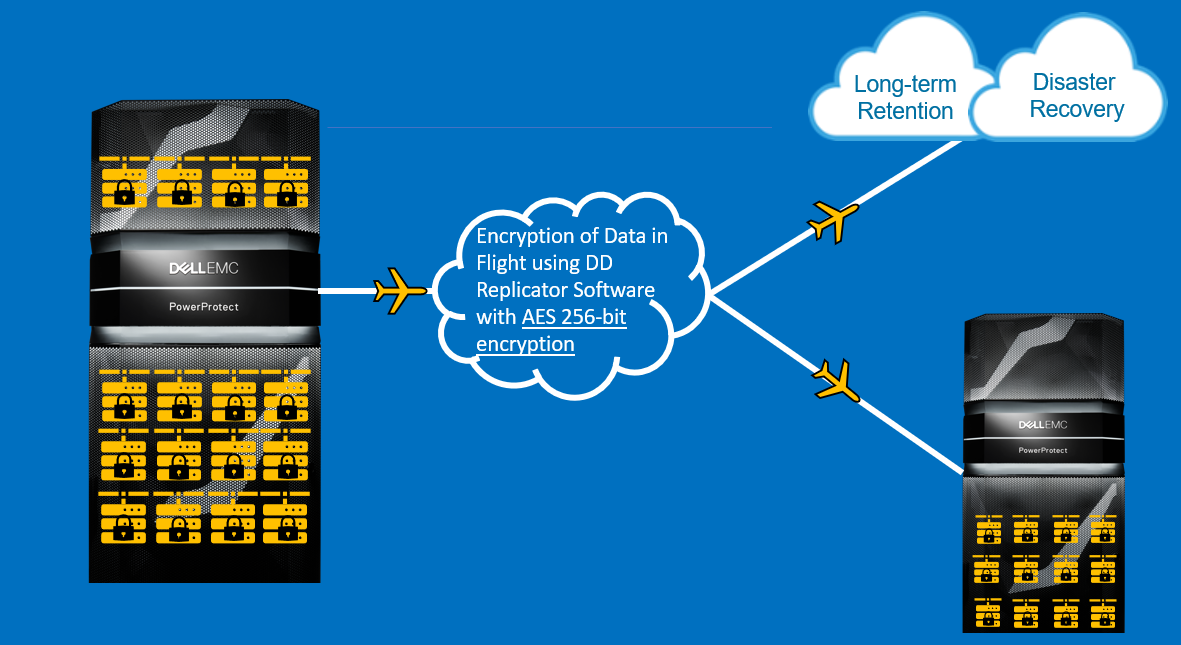
Figure 3. DD Replicator overview
DD Replicator
DD Replicator provides automated, policy-based, network-efficient replication for disaster recovery, remote-office data protection, and multisite tape consolidation. DD Replicator software asynchronously replicates only the compressed, deduplicated data over the WAN or LAN during the backup process, making network-based replication fast, reliable, and cost-effective.
For environments that do not use a VPN for secure connections between sites, DD Replicator can securely encapsulate its replication payload over SSL with AES 256-bit encryption. This ability enables secure transmission over the wire, a process also known as encrypting data in flight.
Encryption of data in flight over NFS
NFSv3 and NFSv4 support Kerberos v5 protocol with integrity checking using checksums (krb5i) and Kerberos v5 protocol with privacy service (krb5p) for integrity and privacy, respectively. However, there are performance penalties for encryption.
Encryption of data in flight with DD Boost
The DD Boost protocol can be used with or without certificates for authentication and encryption of data. The use of certificates was introduced to offer a more secure data-transport capability.
In-flight encryption enables applications to encrypt in-flight backup or restore data over LAN from the system. When it is configured, the client can use TLS to encrypt the session between the client and the system. If TLS with certificates is used, the specific suites that are used are DHE-RSA-AES128-SHA and DHE-RSA-AES256-SHA for medium and high encryption, respectively. If anonymous TLS is used to encrypt the session, either of these options is used: ADH-AES256-SHA for the HIGH encryption option, or ADH-AES128-SHA for the MEDIUM encryption option.
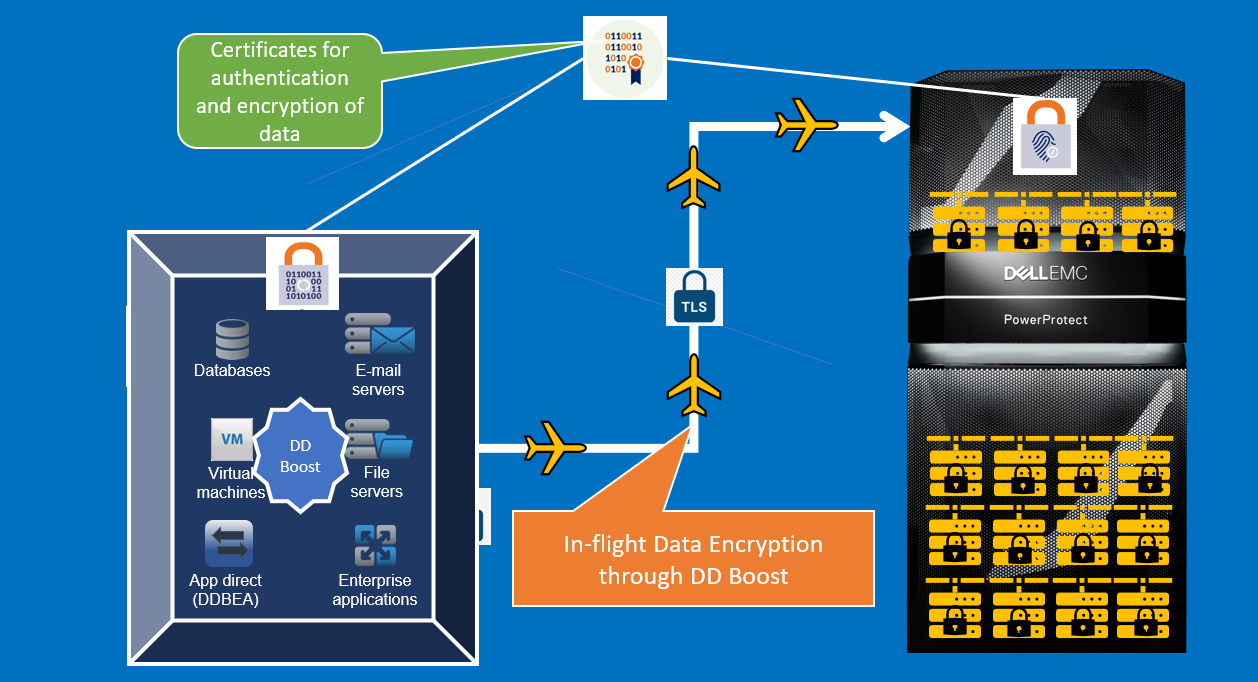
Figure 4. DD Boost overview
