Assets

Trusted Execution: A Secure Foundation for AI and Beyond
Wed, 16 Oct 2024 10:56:02 -0000
|Read Time: 0 minutes
In this article, the third entry of our VxRail security series, we are picking up where we last left off with supply chain security to examine the foundational role of the Trusted Execution Environment (TEE) alongside the critical function of cryptography in fortifying data protections. We're delving into how VxRail, a cornerstone of Dell Technologies’ infrastructure, reflects the Zero Trust principle of “Never Trust, Always Verify” through TEE and cryptographic layers, ensuring robust defense throughout a product's lifecycle. At the heart of any secure system lies TEE, a sanctuary for your most sensitive operations, providing security for both conventional and AI-centric applications.
Trusted Execution Environment
For a long time, protecting data while it is actively in use was considered a significant challenge. While the performance of cryptographic processing has significantly improved, real-time software encryption on data in use is simply not practical. This limitation led chip manufacturers to identify an alternative in leveraging hardware to provide a secure space in which to process the data to decrease the risk of exposure. This space is the Trusted Execution Environment.
A TEE starts with the main processing unit. Modern CPUs from both Intel and AMD provide a secure area that ensures the confidentiality and integrity of that data being processed by preventing unauthorized access within the TEE. This approach limits the ability of a bad actor accessing or modifying the data running in the secure area. While the AMD TEE is all hardware, Intel provides its Software Guard Extensions (SGX) API which allows for, among other things, direct user and OS level calls to define enclaves and protected private regions of memory, enable secure execution of code on remote servers, protect encryption keys, and more.
Other hardware that can increase security:
- Trusted Platform Modules (TPMs) providing basic hardware-based security functions leveraged for secure storage, key management, and remote attestation.
- Secure Memory Management Units (Secure MMUs) to enhance the CPU TEE by ensuring secure memory isolation and access control.
- Hardware Security Modules (HSMs), typically used for cryptographic operations.
Dell and VxRail recognize that the availability of a TEE is critical to creating a secure operating environment. For AI deployments, a solid TEE can provide protections against injection, infection, extraction, and excessive agency attack vectors. VxRail with PowerEdge offers the ability to choose both Intel and AMD chips enabled for TEE, with TPM 2.0 hardware for increased security capabilities including Silicon Root of Trust, SecureBoot, and Secured Component Verification (SCV).
VxRail, Dell Technologies’ robust infrastructure solution, adheres to the Zero Trust principle. This security philosophy extends across the entire lifecycle of our products, from inception to decommissioning. A Zero Trust Architecture is multifaceted, comprising various layers of security that intersect at different points within this lifecycle. Each layer addresses specific security concerns, collectively forming a formidable defense against malicious actors. In the context of AI environments, where attack vectors are diverse, VxRail’s comprehensive protection becomes even more critical.
Cryptography
Building on the security of TEE, let’s now discuss the uses of cryptography across the entire lifecycle to add additional protections to keep conventional and AI use cases secure.
Cryptographic operations, in one form or another, continue to be a powerful tool in the security toolbox. In terms of infrastructure, typical cryptography takes the form of encryption and signing. With encryption, the goal is to ensure the confidentiality of the data, and signing ensures the integrity of the data. Both actions can be taken separately or in conjunction for added protections. As with most things security, which to use and when are dependent on use case, performance, and usability requirements.
Two artifacts are needed to perform cryptographic operations are:
- Cryptographic processor (hardware) and cryptographic module (software)
- Encryption keys (typically symmetric and asymmetric)
Of course, not all cryptography is equal. Security conscious customers, especially those deploying an AI environment, will want to ensure that the algorithms and methodologies used are strong enough to meet industry standards. In the encryption case that would be NIST (National Institute of Standards and Technology) FIPS 140. This living standard defines the security requirements that cryptographic modules must meet for U.S. Federal deployments while organizations in other industries and verticals recognize that the user of FIPS validated encryption libraries and modules will go a long way to ensure secure cryptography.
Within the datacenter, cryptography is typically applied to communications (data in flight) and storage (data at rest).
Communications
While there are multiple ways to perform data in flight encryption, the most common is by using TLS, or Transport Layer Security. This protocol dictates how to provide secure communication over computer networks ensuring privacy, integrity, and authentication. This protocol is typically used between applications and is a successor to Secure Sockets Layer (SSL).
Another use case for cryptographic operations in communication is with Single Sign-On (SSO). There are industry accepted standards for SSO communications and some of them offer and require the use of cryptography for encryption and/or signatures. Both use cases usually require the creation and use of asymmetric encryption keys which must be properly managed by an infrastructure administrator.
Storage
Data at rest encryption is typically handled in two ways:
- Self-Encrypting Drives (SEDs)
- Software-based encryption
Either or both use cases can be chosen and require the use and proper management of, in this case, symmetric encryption keys.
Cryptography is a security control that is critical to all infrastructure use cases, including AI. Protecting the data from exfiltration and modification is essential to all users. For the AI use case, encrypted communications and storage are the best controls to remediate against the poisoning attack vector. VxRail offers FIPS 140-2 validated encrypted communications and storage built into the appliance using TLS for communications, SEDs for purchase, and supporting VMware vSphere VM and vSAN encryption features.
Be sure to join us next week as we go beyond the technology and examine the vital role of Identity and Access Management (IAM) in the VxRail security ecosystem, which provides peace of mind regardless of an application's nature.
Joann Kent, Cybersecurity Product Manager

Protecting AI Infrastructure: VxRail's Answer to Advanced Threat Vectors
Wed, 09 Oct 2024 14:16:27 -0000
|Read Time: 0 minutes
As AI entwines itself within the fabric of our technological ecosystem, it brings with it a host of sophisticated vulnerabilities that require equally sophisticated defenses. In last week’s initial entry to the series, we introduced key attack vectors for AI deployments and highlighted how VxRail and Dell Technologies’ ecosystem can help establish a secure environment. This week, we take a magnifying glass to these previously identified potential breach points and explore how VxRail's security measures are uniquely positioned to protect your AI infrastructure.
Countering AI Threats with VxRail
Diving into the world of AI security, we explore how VxRail's inherent design anticipates AI-related threats. VxRail’s security controls provide mitigations for a range of attacks, from Injection to Denial of Service, utilizing both physical hardware measures and advanced software protocols.
Supply Chain Security
In any deployment, supply chain security takes center stage, especially when hosting an AI environment. The integrity of the infrastructure, training data, and AI models hinges on preventing the introduction of malware and other threats. Attack vectors related to supply chain contamination—such as Injection, Infection, Poisoning, and Excessive Agency—aim to infiltrate vulnerable software or hardware during development, manufacturing, shipment, and assembly processes.
Production
Supply chain security measures extend across the entire product lifecycle, starting from the initial stages of product development and production. Vendors must adhere to industry standards, including guidelines like the NIST (National Institute of Standards and Technology) Guidance for Supply Chain Risk Management. At the operational level, maintaining a traceable chain of custody, rigorous quality assurance, and thorough inspection and testing are critical controls to minimize the risk of using compromised materials. Dell Technologies, for instance, employs asset tracking processes to ensure that materials come exclusively from their approved vendor list, matching the bill of materials, and directly from the original manufacturers — thereby avoiding third-party intermediaries. These processes align with industry specifications and standards, reinforcing supply chain security.
Shipment
Dell Technologies’ factories meet the stringent security requirements outlined by the Transported Asset Protection Association (TAPA). These measures come into play during packaging and transportation to the customer. Key TAPA controls include closed-circuit cameras in critical areas, access controls, and vigilant monitoring of entries and exits. To safeguard shipments, Dell employs tamper-evident packaging, conducts security reviews of shipping lanes, ensures locks and hardware meet required specifications, and even utilizes GPS tracking devices for continuous monitoring until delivery confirmation.
Deployment & Maintenance
Silicon-Based Root-of-Trust
Beyond physical controls, VxRail and PowerEdge servers incorporate Silicon-based Root-of-Trust. This technology, in conjunction with Intel Boot Guard or AMD Root-of-Trust capabilities, attests to the integrity of BIOS and iDRAC firmware. Attestation is accomplished when, during manufacturing, encryption keys cryptographically sign a hash of the boot image before it leaves the factory. These read-only keys are used during the boot process and if any tampering evidence surfaces, the server is promptly shut down. VxRail and PowerEdge also extends signature verification to firmware updates, ensuring only authentic firmware runs on the server platform.
Secured Component Verification (SCV)
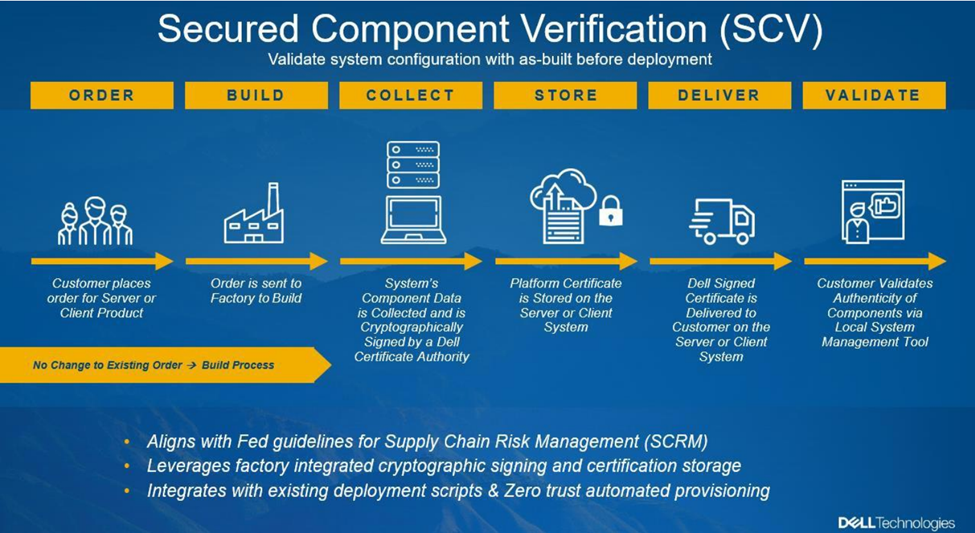
Dell VxRail and PowerEdge servers offer an optional feature called SCV to enhance the supply chain assurance of Silicon-based Root-of-Trust. SCV validates that the server and components received at the customer site match the factory-shipped configuration. A certificate containing a unique system component IDs is generated during manufacturing, cryptographically signed, and stored within iDRAC. Customers can leverage SCV to verify their current inventory against the original shipment.
Protecting Software Supply Chain
Moving beyond hardware and firmware, VxRail employs multiple security controls to safeguard the software supply chain:
- Proactive Verification and Validation: Rigorous security testing occurs throughout the software development lifecycle, ensuring robust protection against vulnerabilities.
- Third-Party Code Scanning: Regular scans prevent the inclusion of compromised supporting software.
- Code Signing and SecureBoot: Pairing code signing with SecureBoot guarantees that our software remains untampered.
- Software Bill of Materials (SBOM): We provide an SBOM upon request, offering full transparency regarding third-party software usage.
Decommission
In the lifecycle of any device, there comes a critical step: decommissioning. Whether a device is discarded or repurposed, handling this phase properly is essential to prevent bad actors from accessing sensitive data related to its original use.
Steps taken during decommissioning to protect the overall supply chain include:
- Reconfiguring Access Controls: To prevent unauthorized access, reconfigure access controls and invalidate previous credentials associated with the system.
- Asset Tracking: Maintain a traceable chain of custody during decommissioning to protect against attacks during the final transport phase.
- Trusted Partnerships: Collaborate with trusted partners who adhere to Zero Trust security practices for secure decommissioning.
- Data Sanitization: Render any remaining data on the system inaccessible.
Data Sanitization
VxRail provides functionality to support the data sanitization step. The goal is to make all data on the system completely unrecoverable—even by advanced digital forensics. VxRail employs cryptographic sanitization, where targeted data is encrypted, and the encryption keys are subsequently destroyed. This efficient approach aligns with NIST SP 800-88 guidelines. Three paths lead to a full cryptographic erase:
- PowerEdge System Erase: Sanitizes server storage devices and nonvolatile stores.
- VMware vSAN Encryption: Once a vSAN is encrypted, vSphere allows destruction of relevant encryption keys, rendering vSAN-stored data inaccessible.
- VMware VM Encryption: Similar capabilities encrypt VMs and then destroy the associated encryption keys.
Zero Trust: Securing AI's Supply Chain
Supply chain security is foundational in modern Zero Trust practices. As AI becomes increasingly central to our lives, safeguarding against supply chain attacks is imperative. Together VxRail and PowerEdge provide solid supply chain security to protect infrastructure and AI deployments.
Stay tuned for our next post where we merge technology with trust, detailing how VxRail establishes a Trusted Execution Environment, a vital component for any AI-driven operation.
Author:
Joann Kent, Cybersecurity Product Manager

VxRail Security for Life: Defending the Foundation of Digital Transformation
Tue, 01 Oct 2024 19:58:56 -0000
|Read Time: 0 minutes
Welcome to our VxRail Security for Life blog series, where over the next five weeks, we will embark on a comprehensive journey through VxRail's security features. In an age where technology evolves at breakneck speed, understanding how to protect your infrastructure—including AI deployments—is critical for any forward-thinking enterprise.
Today’s Digital Battlefield: Navigating the New Era of AI
In today’s rapidly evolving tech landscape, the proliferation of Large Language Model (LLM) "AI" tools has brought about a significant shift. There are significant changes—not just in capabilities but also in the security challenges that come hand-in-hand with such transformation. Organizations diving into AI services and platforms are compelled to strengthen their existing security frameworks, to effectively combat the threats posed by increasingly sophisticated cyber adversaries. The good news for VxRail users is the inherent robustness of their system's security toolkit is thoughtfully designed for such an era of innovation and challenge. To see how VxRail’s comprehensive, security-by-design approach addresses these evolving needs, check out the VxRail Security Infographic.
As the opening chapter of our "VxRail Security for Life" blog series, this post marks the beginning of a deep dive into the comprehensive array of security features that VxRail offers. Our journey will cover the entire product lifecycle, shedding light on how each built-in security measure fortifies the support structure of your entire IT infrastructure, with a special focus on AI deployments. Join us as we navigate through the multifaceted landscape of security in this dynamic new age, underscored by VxRail's commitment to resilient and adaptive defense mechanisms.
Understanding AI Attack Vectors
To address these security challenges, we must first grasp the potential attack vectors that can be exploited by bad actors. These vectors include:
- Injection – Manipulating the AI to follow “bad” instructions.
- Infection – Introducing vulnerabilities/malware in AI model’s source code.
- Evasion – Tricking the AI into behaving badly with carefully crafted inputs.
- Poisoning – Corrupting the training data with vulnerabilities, malware, or false information.
- Extraction – Stealing the AI model by reverse engineering it through strategic questioning.
- Denial of Service – Overwhelming the AI service with rapid queries.
- Excessive Agency – Exploiting broad permissions granted to the model within the infrastructure.
Once we’ve identified the attack vectors, the next crucial step is safeguarding against them. While deploying LLM/AI tools with built-in security is essential, it’s just one layer of defense. Fortunately, modern Zero Trust infrastructure security provides a solid foundation, allowing customers to rely on established practices to mitigate risks effectively.
Infrastructure Security for AI
VxRail
VxRail, an HCI appliance built on Dell PowerEdge and engineered with VMware by Broadcom, offers comprehensive security controls to counter each AI attack vector.
Hardware/Firmware security with:
- Physical controls
- Silicon Root of Trust
- Trusted Execution Environment
- TPM 2.0
- Secured Component Verification
Software security with:
- SecureBoot
- Signed and Trusted binaries
- Encryption
- Modern IAM
- Hardening
Across all levels:
- Secure Development Lifecycle
- Monitoring/Logging Auditing
VxRail’s Zero Trust security features and capabilities are ready today for an AI environment.
Dell Technologies Ecosystem
While VxRail provides an excellent starting point for AI infrastructure, customers can elevate their security posture by complementing VxRail with Dell's PowerProtect Data Manager. PowerProtect offers infrastructure monitoring, intrusion detection, and behavioral analysis—bolstering defenses against the identified AI attack vectors.
Deploying an LLM/AI model as a service is a significant undertaking—one that demands security considerations from the outset. Dell Technologies' VxRail, combined with PowerProtect, forms a winning security combination, safeguarding your AI deployments.
In the next post of the VxRail Security for Life Series we will start a deep dive into VxRail’s security features and capabilities across the entire lifecycle and how VxRail is ready now to secure your AI infrastructure.
Dell References
- VxRail Comprehensive Security by Design
- PowerEdge/iDRAC Security Configuration Guide
- PowerProtect Data Manager Security Configuration Guide
Third party references
- Artificial Intelligence: The new attack surface - YouTube video from IBM's, Jeff Crume, Distinguished Engineer
- Intel Trusted Execution Technology
- OWASP Top 10 for LLM Applications
- VMware reset attack protection
- Information Security Management at VMware
Author: Joann Kent, Cybersecurity Product Manager

PowerFlex and CloudLink: A Powerful Data Security Combination
Mon, 17 Aug 2020 21:41:08 -0000
|Read Time: 0 minutes
Security and operational efficiency continue to top IT executives’ datacenter needs lists. Dell Technologies looks at the complete solution to achieve both so customers can focus on their business outcomes.
Dell Technologies’ PowerFlex is a software-defined storage platform designed to significantly reduce operational and infrastructure complexity, empowering organizations to move faster by delivering flexibility, elasticity, and simplicity with predictable performance and resiliency at scale. PowerFlex provides a unified fabric of compute and storage with scale out flexibility for either of these ingredients to match workload requirements with full lifecycle simplification provided by PowerFlex Manager. Dell Technologies’ CloudLink, data encryption and key management solution, supports workload deployments from edge to core to cloud, providing a perfect complement to the PowerFlex family that enables flexible encryption tailored to the modern datacenter’s needs.
With increasing regulatory and compliance requirements, more and more customers now realize how critical encryption is to securing their data centers and need solutions that are built into their platforms. CloudLink, integrated with PowerFlex, provides reliable data encryption and key management in one solution with the flexibility to satisfy most customer's needs.
Built-in, not bolt on
CloudLink’s rich feature set integrates directly into the PowerFlex platform allowing our customers access to CloudLink's encryption and key management functionality, including data at rest and data in motion encryption, full key lifecycle management, and lightweight multi-tenancy support.
- Encryption for PowerFlex
CloudLink provides software-based data encryption and a full set of key management capabilities for PowerFlex, including:
- Policy-based key release to ensure data is only unlocked in a safe environment
- Machine grouping to ensure consistent policy configuration across drives
- Full key lifecycle management to maintain proper encryption key hygiene
- Key Management for Self-Encrypting Drives (SED)
SEDs offer high performant hardware-based Data-at-Rest Encryption ensuring that all data in the deployment is safe from prying eyes. On a PowerFlex platform, CloudLink can manage the keys for each individual drive and store them safely within our encrypted vault where customers can leverage CloudLink's full key lifecycle management feature set. This option, also integrated and deployable with PowerFlex Manager, is ideal for your sensitive data assets that require high-performance.
- Encryption for Machines
Sometimes Data-at-Rest Encryption is not enough, and our customers need to encrypt their virtual machines. CloudLink provides VM encryption by deploying agents on the guest OS. CloudLink's agent encryption gives our customers the ability to move encrypted VMs throughout their environment making tasks such as replication, deployment to production from QA, or out to satellite offices, safer and easier.
CloudLink’s encryption for machines agent can also encrypt data volumes on bare metal servers allowing customers to keep their data safe even when deployed on legacy hardware.
- Key Management over KMIP
When 3rd party encryptors need external key management, they turn to solutions that implement KMIP (Key Management Interoperability Protocol). This open standard defines how encryptors and key managers communicate. CloudLink implements the KMIP protocol both as a client and a server to provide basic key storage and management for encryptors such as VMware’s native encryption features, or to plug-in to a customer’s existing keystore. These capabilities provide the flexibility required for today’s heterogenous environments.
Supporting the modern datacenter
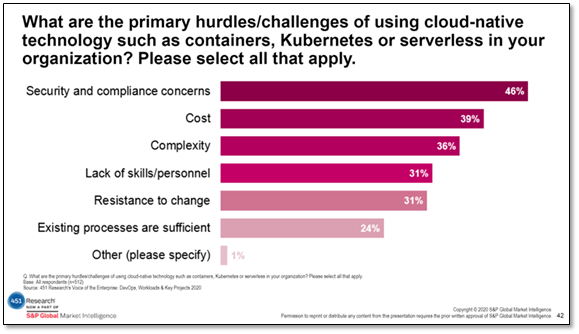
There is a sea change occurring in data centers brought on by the relatively new technology of containers. 451 Research, a global research and advisory firm, released the results of its 2020 Voice of the Enterprise survey, which indicates that as companies consider the move to containerized deployments, security and compliance concerns are top of mind. However, for so many of the new container technology products from which to choose, proper security is not built-in.
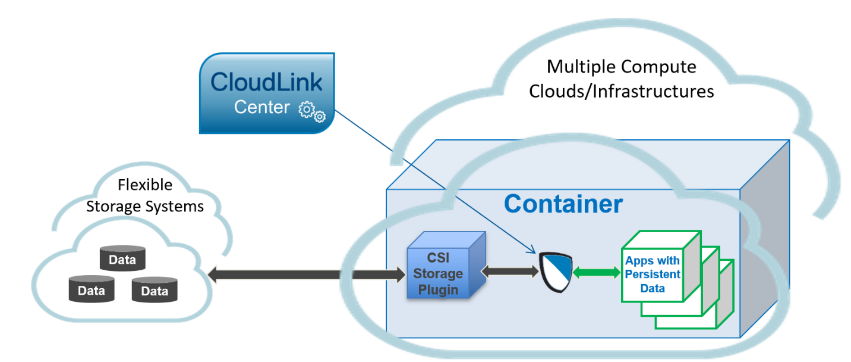
Given the extreme mobility of containers, keeping customers’ data safe as applications move throughout a deployment – especially within the cloud – is a challenge. To address this gap, we introduced file volume encryption for Kubernetes container deployments in our CloudLink 7.0 release, which has been validated with PowerFlex 3.5. Our container encryption functionality is built on the same full lifecycle key management and agent-based encryption architectural model that we currently offer for PowerFlex. We deploy an agent within the container such that it sits directly on the data path. As the data is saved, we intercept it and make sure it is encrypted as it travels to and then comes to rest in the data store.
Data security doesn’t need to mean complex management
Hand in hand with PowerFlex, CloudLink provides data encryption and key management with unmatched flexibility, superior reliability, and simple and efficient operations complete with support from Dell as a complete solution. The PowerFlex Manager is a comprehensive IT operations and lifecycle management tool that drastically simplifies management and ongoing operation. CloudLink is integrated into this tool to make the deployment of the CloudLink agent a natural part the PowerFlex management framework.
Are you interested in PowerFlex and CloudLink? Please visit our websites for PowerFlex or CloudLink or reach out to your Dell Technologies sales representative for help.

