Assets

Next-Generation Dell PowerEdge Servers: Transition to Modern UEFI
Thu, 20 Apr 2023 14:42:18 -0000
|Read Time: 0 minutes
Summary
To combat and reduce the threat surface in the pre-boot environment, a broad transitioning is happening industry-wide from legacy BIOS boot to Unified Extensible Firmware Interface (UEFI) boot. UEFI changes the interface and data structures to interact with I/O device firmware and operating systems. The primary intent of UEFI is to eliminate shortcomings in the legacy BIOS boot environment, enabling system firmware to continue scaling with industry trends. System administrators are using UEFI boot throughout their data centers for cyber resilience and secure end-to-end boot.
Threat surface in the pre-boot environment
As security breaches are becoming more frequent, system administrators must employ a wider variety of defenses. Cyber threats not only affect traditional areas of security focus, such as network, operating system, and applications; they affect firmware as well. Attackers find this pre-boot environment lucrative and use firmware rootkits to hide malicious code, called malware, in device or system firmware.
Firmware is software that is embedded in a piece of hardware. While server components are often viewed strictly as hardware, many components have firmware, such as network interface cards, storage controllers, graphics cards, and more. The firmware acts as the device’s operating system, providing control, monitoring, and data manipulation functions. Firmware runs before the operating system environments come into existence.
Malware can control system firmware and then gain full access to the system. Pre-boot malware avoids operating system privilege levels, escapes detection by operating system anti-malware tools, and even survives reinstallation of the operating system. If an attacker injects malware into the pre-boot environment, administrators might find it difficult to remove, if they detect it at all.
Industry transition to UEFI boot
To combat and reduce the threat surface in the pre-boot environment, many vendors and customers are embracing UEFI boot and have stopped certifying operating systems and applications with legacy BIOS boot mode.
- Microsoft requires UEFI boot on Windows Server 2022 and beyond.
- VMware only certifies UEFI boot in their latest ESXi offerings.
- Intel has stopped supporting legacy BIOS boot with certain platforms such as the Intel® Xeon® E-2300 series processors.
- Many new technologies, such as PCIe Gen 5 and NVMe, have eliminated legacy BIOS boot, and the modern data center is transitioning with them.
UEFI benefits
UEFI was designed to overcome many limitations of legacy BIOS boot.
 UEFI supports drive sizes up to 9 zettabytes, whereas BIOS supports only 2.2 terabytes.
UEFI supports drive sizes up to 9 zettabytes, whereas BIOS supports only 2.2 terabytes.
 UEFI can provide faster boot time by allowing parallel execution for sections of the boot flow.
UEFI can provide faster boot time by allowing parallel execution for sections of the boot flow.
 UEFI has discrete driver support, while BIOS has drivers stored in its ROM and lacks modularity, so updating BIOS firmware can be more difficult.
UEFI has discrete driver support, while BIOS has drivers stored in its ROM and lacks modularity, so updating BIOS firmware can be more difficult.
 UEFI offers improved security, including Secure Boot. Secure Boot prevents the computer from running unauthorized and unverified code during boot, which helps prevent rootkit and bootkit attacks.
UEFI offers improved security, including Secure Boot. Secure Boot prevents the computer from running unauthorized and unverified code during boot, which helps prevent rootkit and bootkit attacks.
 UEFI is easier to deploy and manage. The UI supports mouse-based navigation due to UEFI’s ability to run in 32-bit and 64-bit modes. BIOS runs in 16-bit mode and only allows keyboard-based navigation.
UEFI is easier to deploy and manage. The UI supports mouse-based navigation due to UEFI’s ability to run in 32-bit and 64-bit modes. BIOS runs in 16-bit mode and only allows keyboard-based navigation.
UEFI operations
UEFI does not change the traditional purposes of the system BIOS. To a large extent, UEFI performs the same initialization, boot, configuration, and management tasks as a traditional BIOS. However, UEFI does change the interfaces and data structures that the BIOS uses to interact with I/O device firmware and operating systems. The interface consists of data tables that contain platform-related information, plus boot and runtime service calls that are available to the operating system and its loader. Together, these provide a standard, modern environment for booting an operating system and running pre-boot applications. The primary intent of UEFI is to eliminate shortcomings in the traditional BIOS environment, enabling system firmware to continue scaling with industry trends.
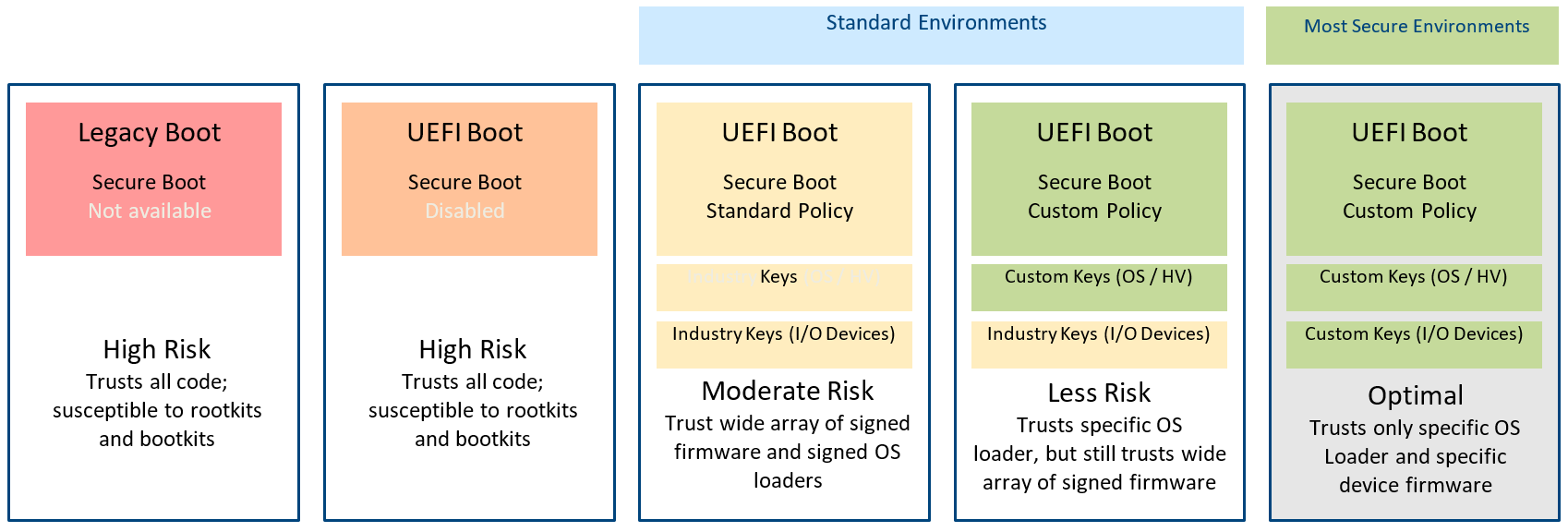
Figure 1. Levels of UEFI boot
UEFI Secure Boot
UEFI Secure Boot is a technology that eliminates a major security void that might occur during a handoff between the UEFI firmware and the operating system.
Users configure a Secure Boot policy consisting of X.509 certificates and hash values for both authorized and unauthorized entities. The system firmware enforces this policy when determining whether to run pre-boot software including I/O device firmware and operating system loaders. When enabled, UEFI Secure Boot prevents unsigned or compromised UEFI device drivers from being loaded, displays an error message, and does not allow the device to function. You must disable Secure Boot to load the unsigned device drivers.
Since mid-2017, you can enable or disable the Secure Boot feature on Dell PowerEdge servers through various interfaces. The Secure Boot Management on Dell PowerEdge Servers white paper provides more details about Secure Boot and how to configure it on PowerEdge servers.
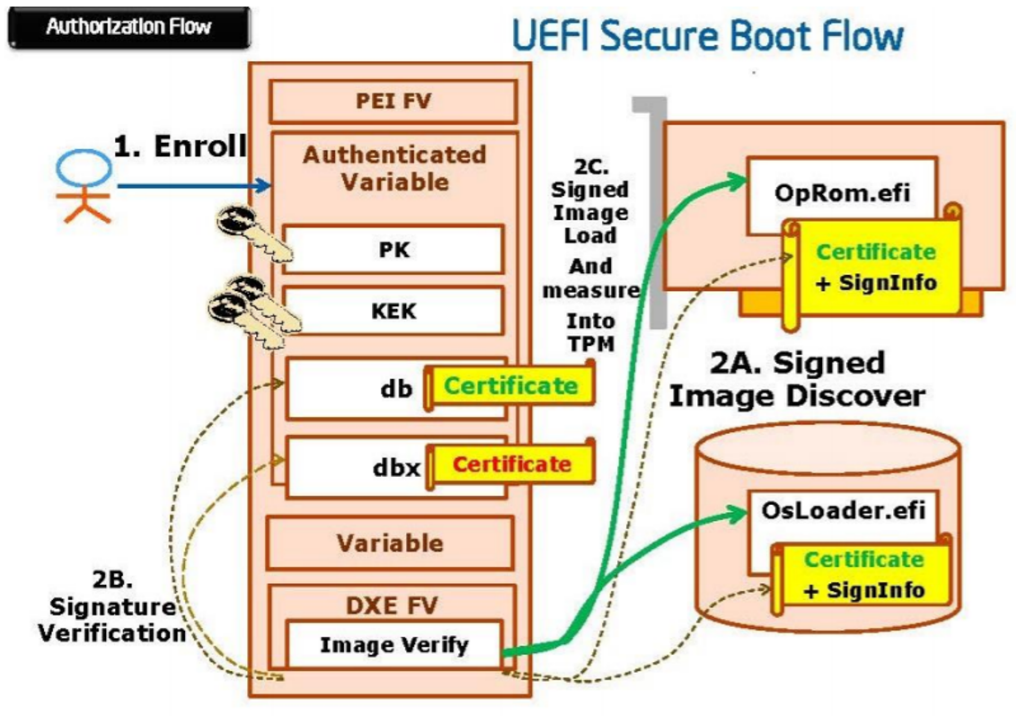
Figure 2. UEFI Secure Boot working principle
Dell Secure Boot customization
For customers wanting to avoid standard keys because of some of the risks they present, Dell Technologies provides complete customization capabilities for UEFI Secure Boot. This gives system owners an option to eliminate reliance on industry keys and third-party certificate authorities. In Figure 1, the yellow boxes have one CA certificate that authorizes multiple versions of firmware, whereas the green boxes signify a customized certificate for a specific version of firmware. Dell PowerEdge offers tools to enable capture of firmware hashes and create customized certificates so system administrators can optimize the effectiveness of their UEFI Secure Boot policies according to their security requirements.
In a recent Cybersecurity Technical Report, the National Security Agency highlighted the need for enabling UEFI Secure Boot and the benefits of using customization to realize the highest level of server security available today. The report showcases the fully customized Secure Boot capabilities of PowerEdge servers as the example of how to achieve this highest level of boot security.
Impact to environments with servers configured for legacy BIOS boot
For customers whose environments include servers configured for legacy BIOS boot, the primary impact of switching to UEFI boot mode is likely to their deployment and maintenance model. Customers who use PXE servers to deploy and perform routine maintenance need to plan for adaption of the PXE server. For more information about this process, see Boot Mode Considerations: BIOS vs. UEFI.
Another impact is the use of NVMe drives that natively boot UEFI. However, they can be used as data drives in both legacy BIOS and UEFI boot modes.
Conclusion
Cyber attacks are becoming more numerous, frequent, and difficult to detect. Strengthening your organization’s security posture by implementing the latest security approaches positions your organization to respond to today’s cyber threat environment. The security features and boot mechanisms available only when a system is configured for UEFI boot mode is driving the industry-wide transition to UEFI boot.
To achieve additional boot security, UEFI-enabled systems include Secure Boot as a setup option, providing additional security checks during the boot process.
References
Dell documents
- Secure Boot Management on Dell PowerEdge Servers
- Boot Mode Considerations: BIOS vs. UEFI
- Dell PowerEdge UEFI Boot: Enhanced Security to Combat Persistent Firmware Threats
NSA documents
- UEFI Defensive Practices Guidance
- Boot Security Modes and Recommendations
- UEFI Lockdown Quick Guidance
- UEFI Secure Boot Customization
UEFI Forum documents

The power of cyber resiliency at your core
Thu, 26 Jan 2023 21:34:59 -0000
|Read Time: 0 minutes
At Dell Technologies, we often talk about how security is ingrained into our product DNA. What we mean is that security is never an afterthought — it’s never something that we build on after the product itself is complete.
Instead — and our Secure Development Lifecycle (SDL) is a key part of this — we continually design our products with past, current and future security threats in mind. And we supplement secure product development with external audits and continuous testing and evaluation to find and remedy vulnerabilities that do occur.
Dell’s commitment to customers
Attacks on the infrastructure layer, especially the firmware, are on rise. According to a Microsoft Security Signals report, more than 83% of enterprises have experienced at least one firmware attack in the past two years.
At Dell, we understand that securing the infrastructure layer is fundamental to protecting any IT environment against modern threats. Our cyber-resilient infrastructure has security built into every phase starting from the supply chain to the operation and eventual retirement of products. We are also committed to making sure any vulnerabilities or exposures found in the field, that could impact our products, get mitigated through rapid response on our end.
Let’s talk about how we secure our PowerEdge servers.
Cyber resiliency is key
Modern server platforms are highly complex, with hundreds of components — a lot of which require firmware for configuration and management of the component during the boot process and operation of the server.
Given the complexity of today’s platforms and the level of sophistication of cyberattacks, we recognize that it is not possible to prevent 100% of attacks. Some breaches are inevitable, especially when it comes to new devices and firmware, for example. Cyber resiliency — the ability to anticipate, withstand and recover from attacks — is therefore fundamental to surviving in this threat landscape.

At Dell, we use the NIST framework of Protect, Detect and Recover to guide our resiliency efforts. At the same time, the process of identifying and designing these capabilities is done through the zero-trust approach — with a focus on increasing the granularity of controls and checks in the systems — and by anticipating how our customers will want to use these capabilities while they are setting up their zero-trust IT environments and deployments.
Cyber resiliency built into PowerEdge
Dell PowerEdge servers offer cyber-resilient infrastructure by anchoring platform integrity to a silicon-based Root of Trust and using automated features to continuously protect the system during its operation.
Root of Trust: PowerEdge offers end-to-end boot resilience by enabling UEFI secure boot, which is anchored in our silicon-based platform Root of Trust. This immutable Root of Trust is the starting point of the chain of trust used to cryptographically authenticate the different pieces of firmware that get loaded on PowerEdge servers. Our secure boot helps to make sure that the firmware is coming from a trusted source and has not been tampered with in any way.
UEFI certificate customization: PowerEdge servers provide capabilities for complete customization of UEFI secure boot, giving system owners an option to avoid relying on third-party industry keys and industry certificate authorities. The NSA has recognized that fully customized UEFI secure boot offers the highest level of security and provides the best protection against threats. And it’s important to note that Dell was the first server vendor to provide these capabilities to customers.
CPU security
In addition to fully customizable UEFI secure boot, PowerEdge servers offer a complementary layer of protection against things like sleep attacks by enabling Intel Boot Guard and AMD Platform Secure Boot features. These features add robustness to the chain of trust process by verifying the firmware before it gets executed on the processor and eliminating attacks between time of check by UEFI secure boot and time of use of the firmware on the processor.
Drift detection: Beyond assuring boot integrity, PowerEdge can also lock down the system configuration and automatically detect drift in firmware versions and the configuration of the system. If drift is detected, PowerEdge can respond by automatically initiating rollback of the firmware and OS to a “known good” version.
Through these features, PowerEdge servers offer end-to-end boot resilience by protecting against attacks on the firmware, detecting any ongoing attack on firmware and/or system configuration, and automatically recovering from attacks by rolling the system configuration and firmware back to a safe, verified version. What’s also important to note is that this happens with no manual intervention at machine speed, which is critical for minimizing system downtime.
But Dell goes even further
When it comes to the firmware, it's important to reiterate that Dell is committed to providing rapid response and mitigation to CVEs. What you might not know is that the majority of attacks occur because known vulnerabilities are not being patched in the field.
We don’t want to leave our customers vulnerable, which is why we’re always working to improve our service-level agreements (SLA) for updates and patches that help mitigate new threats as quickly as possible.
Resiliency is just one small facet of Dell’s overall security stance. Take time to learn more about what we’re doing to protect your devices, your data, and your business. PowerEdge, like the rest of the Dell fleet of products, has a broad feature set that goes beyond resiliency — and is capable of meeting your risk tolerance requirements and regulatory and compliance needs.
Find additional resources on Dell Technologies Info Hub.

The power of cyber resiliency at your core
Wed, 19 Oct 2022 21:10:14 -0000
|Read Time: 0 minutes
At Dell Technologies, we often talk about how security is ingrained into our product DNA. What we mean is that security is never an afterthought — it’s never something that we build on after the product itself is complete.
Instead — and our Secure Development Lifecycle (SDL) is a key part of this — we continually design our products with past, current and future security threats in mind. And we supplement secure product development with external audits and continuous testing and evaluation to find and remedy vulnerabilities that do occur.
Dell’s commitment to customers
Attacks on the infrastructure layer, especially the firmware, are on rise. According to a Microsoft Security Signals report, more than 83% of enterprises have experienced at least one firmware attack in the past two years.
At Dell, we understand that securing the infrastructure layer is fundamental to protecting any IT environment against modern threats. Our cyber-resilient infrastructure has security built into every phase starting from the supply chain to the operation and eventual retirement of products. We are also committed to making sure any vulnerabilities or exposures found in the field, that could impact our products, get mitigated through rapid response on our end.
Let’s talk about how we secure our PowerEdge servers.
Cyber resiliency is key
Modern server platforms are highly complex, with hundreds of components — a lot of which require firmware for configuration and management of the component during the boot process and operation of the server.
Given the complexity of today’s platforms and the level of sophistication of cyberattacks, we recognize that it is not possible to prevent 100% of attacks. Some breaches are inevitable, especially when it comes to new devices and firmware, for example. Cyber resiliency — the ability to anticipate, withstand and recover from attacks — is therefore fundamental to surviving in this threat landscape.

At Dell, we use the NIST framework of Protect, Detect and Recover to guide our resiliency efforts. At the same time, the process of identifying and designing these capabilities is done through the zero-trust approach — with a focus on increasing the granularity of controls and checks in the systems — and by anticipating how our customers will want to use these capabilities while they are setting up their zero-trust IT environments and deployments.
Cyber resiliency built into PowerEdge
Dell PowerEdge servers offer cyber-resilient infrastructure by anchoring platform integrity to a silicon-based Root of Trust and using automated features to continuously protect the system during its operation.
Root of Trust: PowerEdge offers end-to-end boot resilience by enabling UEFI secure boot, which is anchored in our silicon-based platform Root of Trust. This immutable Root of Trust is the starting point of the chain of trust used to cryptographically authenticate the different pieces of firmware that get loaded on PowerEdge servers. Our secure boot helps to make sure that the firmware is coming from a trusted source and has not been tampered with in any way.
UEFI certificate customization: PowerEdge servers provide capabilities for complete customization of UEFI secure boot, giving system owners an option to avoid relying on third-party industry keys and industry certificate authorities. The NSA has recognized that fully customized UEFI secure boot offers the highest level of security and provides the best protection against threats. And it’s important to note that Dell was the first server vendor to provide these capabilities to customers.
CPU security
In addition to fully customizable UEFI secure boot, PowerEdge servers offer a complementary layer of protection against things like sleep attacks by enabling Intel Boot Guard and AMD Platform Secure Boot features. These features add robustness to the chain of trust process by verifying the firmware before it gets executed on the processor and eliminating attacks between time of check by UEFI secure boot and time of use of the firmware on the processor.
Drift detection: Beyond assuring boot integrity, PowerEdge can also lock down the system configuration and automatically detect drift in firmware versions and the configuration of the system. If drift is detected, PowerEdge can respond by automatically initiating rollback of the firmware and OS to a “known good” version.
Through these features, PowerEdge servers offer end-to-end boot resilience by protecting against attacks on the firmware, detecting any ongoing attack on firmware and/or system configuration, and automatically recovering from attacks by rolling the system configuration and firmware back to a safe, verified version. What’s also important to note is that this happens with no manual intervention at machine speed, which is critical for minimizing system downtime.
But Dell goes even further
When it comes to the firmware, it's important to reiterate that Dell is committed to providing rapid response and mitigation to CVEs. What you might not know is that the majority of attacks occur because known vulnerabilities are not being patched in the field.
We don’t want to leave our customers vulnerable, which is why we’re always working to improve our service-level agreements (SLA) for updates and patches that help mitigate new threats as quickly as possible.
Resiliency is just one small facet of Dell’s overall security stance. Take time to learn more about what we’re doing to protect your devices, your data, and your business. PowerEdge, like the rest of the Dell fleet of products, has a broad feature set that goes beyond resiliency — and is capable of meeting your risk tolerance requirements and regulatory and compliance needs.
Find additional resources on Dell Technologies Info Hub.


