Blogs

The power of cyber resiliency at your core
Wed, 19 Oct 2022 21:10:14 -0000
|Read Time: 0 minutes
At Dell Technologies, we often talk about how security is ingrained into our product DNA. What we mean is that security is never an afterthought — it’s never something that we build on after the product itself is complete.
Instead — and our Secure Development Lifecycle (SDL) is a key part of this — we continually design our products with past, current and future security threats in mind. And we supplement secure product development with external audits and continuous testing and evaluation to find and remedy vulnerabilities that do occur.
Dell’s commitment to customers
Attacks on the infrastructure layer, especially the firmware, are on rise. According to a Microsoft Security Signals report, more than 83% of enterprises have experienced at least one firmware attack in the past two years.
At Dell, we understand that securing the infrastructure layer is fundamental to protecting any IT environment against modern threats. Our cyber-resilient infrastructure has security built into every phase starting from the supply chain to the operation and eventual retirement of products. We are also committed to making sure any vulnerabilities or exposures found in the field, that could impact our products, get mitigated through rapid response on our end.
Let’s talk about how we secure our PowerEdge servers.
Cyber resiliency is key
Modern server platforms are highly complex, with hundreds of components — a lot of which require firmware for configuration and management of the component during the boot process and operation of the server.
Given the complexity of today’s platforms and the level of sophistication of cyberattacks, we recognize that it is not possible to prevent 100% of attacks. Some breaches are inevitable, especially when it comes to new devices and firmware, for example. Cyber resiliency — the ability to anticipate, withstand and recover from attacks — is therefore fundamental to surviving in this threat landscape.

At Dell, we use the NIST framework of Protect, Detect and Recover to guide our resiliency efforts. At the same time, the process of identifying and designing these capabilities is done through the zero-trust approach — with a focus on increasing the granularity of controls and checks in the systems — and by anticipating how our customers will want to use these capabilities while they are setting up their zero-trust IT environments and deployments.
Cyber resiliency built into PowerEdge
Dell PowerEdge servers offer cyber-resilient infrastructure by anchoring platform integrity to a silicon-based Root of Trust and using automated features to continuously protect the system during its operation.
Root of Trust: PowerEdge offers end-to-end boot resilience by enabling UEFI secure boot, which is anchored in our silicon-based platform Root of Trust. This immutable Root of Trust is the starting point of the chain of trust used to cryptographically authenticate the different pieces of firmware that get loaded on PowerEdge servers. Our secure boot helps to make sure that the firmware is coming from a trusted source and has not been tampered with in any way.
UEFI certificate customization: PowerEdge servers provide capabilities for complete customization of UEFI secure boot, giving system owners an option to avoid relying on third-party industry keys and industry certificate authorities. The NSA has recognized that fully customized UEFI secure boot offers the highest level of security and provides the best protection against threats. And it’s important to note that Dell was the first server vendor to provide these capabilities to customers.
CPU security
In addition to fully customizable UEFI secure boot, PowerEdge servers offer a complementary layer of protection against things like sleep attacks by enabling Intel Boot Guard and AMD Platform Secure Boot features. These features add robustness to the chain of trust process by verifying the firmware before it gets executed on the processor and eliminating attacks between time of check by UEFI secure boot and time of use of the firmware on the processor.
Drift detection: Beyond assuring boot integrity, PowerEdge can also lock down the system configuration and automatically detect drift in firmware versions and the configuration of the system. If drift is detected, PowerEdge can respond by automatically initiating rollback of the firmware and OS to a “known good” version.
Through these features, PowerEdge servers offer end-to-end boot resilience by protecting against attacks on the firmware, detecting any ongoing attack on firmware and/or system configuration, and automatically recovering from attacks by rolling the system configuration and firmware back to a safe, verified version. What’s also important to note is that this happens with no manual intervention at machine speed, which is critical for minimizing system downtime.
But Dell goes even further
When it comes to the firmware, it's important to reiterate that Dell is committed to providing rapid response and mitigation to CVEs. What you might not know is that the majority of attacks occur because known vulnerabilities are not being patched in the field.
We don’t want to leave our customers vulnerable, which is why we’re always working to improve our service-level agreements (SLA) for updates and patches that help mitigate new threats as quickly as possible.
Resiliency is just one small facet of Dell’s overall security stance. Take time to learn more about what we’re doing to protect your devices, your data, and your business. PowerEdge, like the rest of the Dell fleet of products, has a broad feature set that goes beyond resiliency — and is capable of meeting your risk tolerance requirements and regulatory and compliance needs.
Find additional resources on Dell Technologies Info Hub.

Why Fortify with Modern Security and Zero Trust?
Thu, 06 Oct 2022 20:17:13 -0000
|Read Time: 0 minutes
Today’s infrastructure landscape is rapidly changing. Customers’ data is scattered — across cloud, multi-cloud, core datacenter, and edge. And with that comes a more challenging threat landscape. The security provisions you deployed yesterday may not be ready for today’s security reality. Cyberattacks can come from anywhere — inside and outside of your organization. This means that you must have a comprehensive and continuous security strategy that is cyber resilient and enables zero trust principles.
Why bother with a comprehensive approach like zero trust?
Cyber threats are real. And the damage caused by attacks can be costly and devastating. Likewise, regulatory pressures (from a compliance, financial, and liability perspective) that have come about as a result of these attacks are growing.
This, combined with the complexity of the modern IT infrastructure and the sophistication of today’s threat landscape, requires a trust model that validates at every point in the IT environment before permissions are granted.
Zero trust is an approach to security that assumes that every part of your infrastructure is at risk — requiring continuous verification and validation. While the purpose of this blog is not to talk in depth about what zero trust is, we do want to explain its validity given today’s threat landscape and explain how Dell Technologies’ cyber-resilient architecture is the foundation for the critical elements of a zero-trust environment.
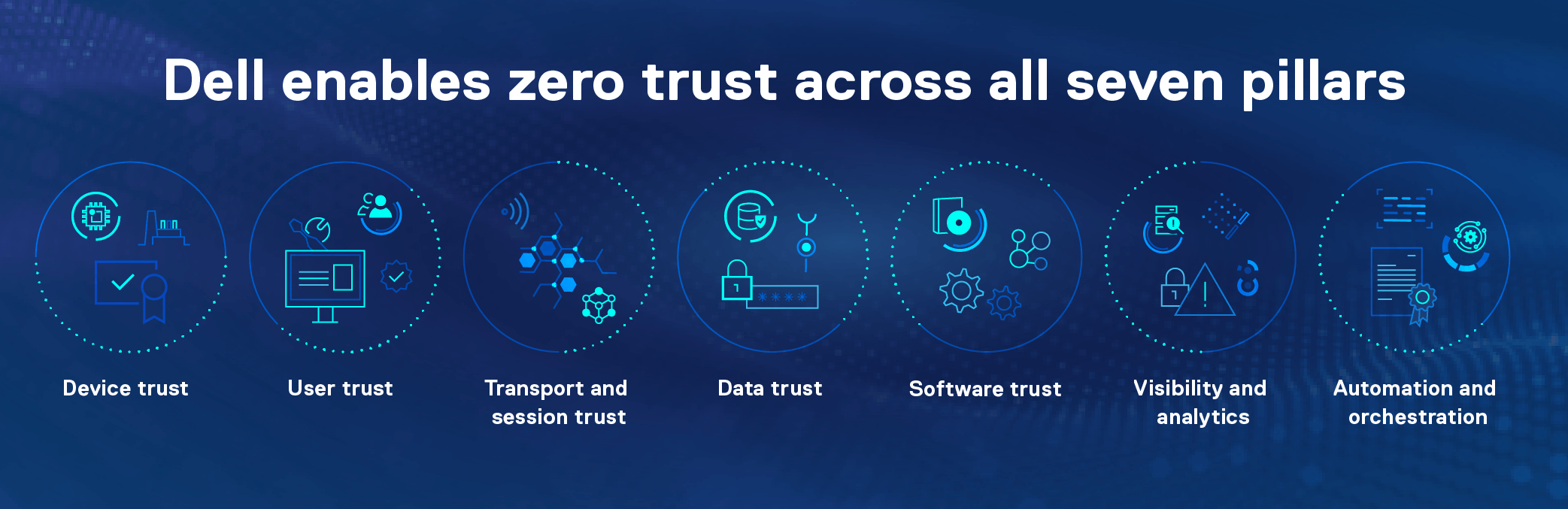
Learn more about how Dell provides broad coverage across these pillars in our Zero trust architecture infographic.
You might be wondering, why does zero trust have so many categories? The simple answer is that you need as complete and continuous coverage as possible across your infrastructure if you want your security efforts to be successful. For example, your organization might do encryption really well. But this doesn’t matter if you don’t have strong multifactor authentication to identify the users of that encrypted data. Your organization is only as secure as your weakest link, which is why focusing on all seven pillars is your best defense in combating threats.
While the ultimate goal is to keep attacks from coming in at all, rejecting them at the point of entry, that’s not always possible. The zero-trust model requires more refined validation at key intersections for verified trust, optimizing least privilege without impacting workload efficiency. However, if a breach does occur, the sphere in which they could do damage should be minimized, along with an enhanced ability to detect and remediate immediately. Dell Technologies’ cyber-resilient architecture, enhanced over many years, is the foundation for the critical elements of a zero-trust environment.
What is the value of having a cyber-resilient architecture?
In simple terms, cyber resiliency within your infrastructure is what helps minimize the exposure to attacks. Dell Technologies solutions are hardened and designed to help you protect, detect, and recover from cyberattacks.
Dell, of course, has been talking about its cyber-resilient architecture for a long time. What’s changed now, however, is that given the emerging threat landscape, we can see how zero trust goes hand in hand with a cyber-resilient architecture. And it’s why we’re continually making enhancements to our cyber-resilient architecture: to provide even greater visibility, risk reduction, and resilience — so that your infrastructure intrinsically supports a zero-trust approach.
We’ll explore cyber resiliency in more detail in a later blog. For now, you can find additional information about Dell’s cyber-resilient architecture in our infographic and video.
Why partner with Dell?
Dell creates the products and features to help you meet your zero-trust goals. We also watch the regulatory landscape to make sure that our solutions meet industry standards and exceed capabilities in the area of security. We do this through:
Processes: Delivering a cyber-resilient architecture requires security awareness and discipline at each stage of development. The Dell Secure Development Lifecycle (SDL), for example, outlines the set of activities required throughout the product lifecycle to promptly build security resiliency and consistent security capabilities into our products and respond to any security vulnerability.
Additional security solutions: In addition to embedding layered security into our products, we provide standalone security solutions focused on specific areas, like data protection. If data does get compromised, you want a backup system that enables business continuity and provides assurance that the backup itself hasn’t been compromised. Offerings like Dell PowerProtect Cyber Recovery and CyberVault enable a robust backup, including the use of Airgap and CyberSense to detect anomalies and mitigate potential problems that could compromise your data.
Simplification: Security controls are useless if they’re not being used. While Dell provides you with sophisticated security controls, we’ve also significantly simplified their use and deployment. Look for more information about “security complexity” in a later blog.
Supply chain security: At Dell, we’re also focused on personnel, operational, and supplier provisions for supply chain security. We have technologies and programs in place, like Secured Component verification that enable the verification of your components from the factory to your site.
Regulatory certifications: We closely monitor regulatory requirements around the world — and make sure our solutions contain the certifications (FIPS, USGv6, Common Criteria, and others) that matter to you. With this focus, we’re able to provide security controls that match emerging regulatory requirements, helping to keep your business secure and compliant.
This is just a glimpse of what Dell Technologies is doing in this space. As Cybersecurity Awareness month kicks off, please take time to read the follow-on blogs in this series and discover the different ways that Dell Technologies is working hard to protect your business.
Author: Craig Phelps

