Blogs
Short articles related to Data Protection.

RecoverPoint for VMs Automation – Advanced VM Protection
Wed, 21 Feb 2024 21:39:22 -0000
|Read Time: 0 minutes
In the spirit of automating everything, this blog will discuss a new automation solution in the RecoverPoint for VMs (RP4VMs) collection of automation solutions.
We have a variety of automation solutions for RP4VMs, including per-tag and per-cluster VM protection and use-case driven tasks, as well as a complete deployment automation solution. Now, I would like to present a new automation solution – Advanced VM Protection.
Let’s take a closer look at this exciting new solution.
What does the solution do?
The RecoverPoint for VMs advanced VM protection solution automates VM protection in RP4VMs with a wide variety of options:
- Automates VM protection based on pre-defined parameters in a JSON configuration file:
- VM name
- RP4VMs cluster name
- Plugin server IP or FQDN
- vCenter user/password or path to credentials file
- Production journal capacity (GB)
- Replica journal capacity (GB)
- Required RPO (sec)
- Failover networks per vNIC
- Performs and monitors mass VM protection
- Protects VMs for a specific RP4VMs cluster (optional)
- Performs VM protection operations on a specific plugin server (optional)
- Includes an option to skip the monitoring of VM protection preparation tasks
- Configures failover networks on a per network adapter basis as a post-protection operation
What is the solution?
It is a Python-based script that exclusively leverages the RP4VMs REST API.
Here is the list of prerequisites:
- Python 3.x (The script supports every platform Python is supported on)
- Python requests module, which can be installed using pip with the command:
pip install requests or python -m pip install requests
- RP4VMs 5.3.x and later
- Connectivity from the host running the script to the RP4VMs plugin server(s), specifically on tcp port 443
How do I use the script?
The script accepts the following parameters:
- One mandatory parameter, file, for a full path to the JSON configuration file.
- The optional parameters, rpvmcluster and server, limit script execution only for VM protection on a specified RP4VMs cluster and/or plugin server accordingly.
- The no-monitor parameter skips monitors of VM protection preparation task.
Here is the full script syntax:
# python advprotectvm.py -h usage: advprotectvm.py [-h] -file CONFIG_FILE [-cl RPVM_CLUSTER] [-s SERVER] [-nmonitor] Scripts advanced VM Protection in RecoverPoint for VMs options: -h, --help show this help message and exit -file CONFIG_FILE, --vm-config-file CONFIG_FILE Path to VM config file -cl RPVM_CLUSTER, --rpvmcluster RPVM_CLUSTER Optionally specify the RP4VMs cluster -s SERVER, --server SERVER Optionally specify RP4VMs Plugin Server DNS/IP -nmonitor, --no-monitor Optionally prevents protection monitoring
Use Cases and Examples
Let’s look at some common use cases for RP4VMs automated advanced VM protection:
- RP4VMs mass VM protection for onboarding of a new application:
# python advprotectvm.py -file idan-vms.json
- Batch VM protection only for a specific RP4VMs cluster:
# python advprotectvm.py -file idan-vms.json -cl Tel-Aviv
- Mass VM protection for a specific vCenter/ plugin or onboarding of a new datacenter:
# python advprotectvm.py -file vms.json -s pluginserver.idan.dell.com
Script output
# python advprotectvm.py -file vms.json -> Protecting VM prodwebsrv1 ---> Protection of VM prodwebsrv1 initiated -> Protecting VM prodappsrv1 ---> Protection of VM prodappsrv1 initiated -> Protecting VM proddbsrv1 ---> Protection of VM proddbsrv1 initiated -> VM protection initiated, monitoring ---> Protection of VM: prodwebsrv1, Transaction: d6783e2d-55be-47db-a082-de1d251c2375, Status: RUNNING ---> Protection of VM: prodappsrv1, Transaction: 808ab022-e79a-4ad1-a633-cc86e17644f2, Status: RUNNING ---> Protection of VM: proddbsrv1, Transaction: c7895dce-f3e6-4e70-872e-9d0b104d6273, Status: RUNNING ---> Protection of VM: prodwebsrv1, Transaction: d6783e2d-55be-47db-a082-de1d251c2375, Status: RUNNING ---> Protection of VM: prodappsrv1, Transaction: 808ab022-e79a-4ad1-a633-cc86e17644f2, Status: RUNNING ---> Protection of VM: proddbsrv1, Transaction: c7895dce-f3e6-4e70-872e-9d0b104d6273, Status: RUNNING ---> Protection of VM: prodwebsrv1, Transaction: d6783e2d-55be-47db-a082-de1d251c2375, Status: RUNNING ---> Protection of VM: prodappsrv1, Transaction: 808ab022-e79a-4ad1-a633-cc86e17644f2, Status: RUNNING ---> Protection of VM: proddbsrv1, Transaction: c7895dce-f3e6-4e70-872e-9d0b104d6273, Status: RUNNING ---> Protection of VM: prodwebsrv1, Transaction: d6783e2d-55be-47db-a082-de1d251c2375, Status: COMPLETED ---> Protection of VM: prodappsrv1, Transaction: 808ab022-e79a-4ad1-a633-cc86e17644f2, Status: COMPLETED ---> Protection of VM: proddbsrv1, Transaction: c7895dce-f3e6-4e70-872e-9d0b104d6273, Status: COMPLETED -> Configuring failover networks ---> Skipping failover network config for VM: prodwebsrv1 ---> Failover networks config is not required for VM: prodappsrv1 ---> Failover network config is successful for VM: proddbsrv1
Where can I find it?
The script and the config file can be found on GitHub: https://github.com/IdanKen/Dell-EMC-RecoverPoint4VMs.
Resources
- The Dell developer site provides comprehensive online API documentation, including full API references, tutorials, and use cases for the RP4VMs REST API.
- The RP4VMs REST API offers self-documentation – Swagger UI running on the plugin server itself – https://{plugin-server}/ui
- RecoverPoint for VMs GitHub repository
- RecoverPoint for VMs 5.3 – New RESTful API Demo
How can I get help?
For additional support, you are more than welcome to raise an issue in GitHub or reach out to me by email: Idan.kentor@dell.com
Thanks for reading!
Idan
Author: Idan Kentor

RecoverPoint for VMs Deployment Automation – How to Deploy Complete RP4VMs Systems in Minutes
Wed, 21 Sep 2022 22:02:31 -0000
|Read Time: 0 minutes
I’m a firm believer in automating EVERYTHING, so in this blog we are going to show how we automate just about everything in RecoverPoint for VMs 😊.
In RP4VMs land, we have VM protection automation solutions, per-tag and per-cluster protection, use-case driven tasks, and so on. And now, I’m honored to present you a complete deployment automation solution.
So, first things first, what does it do?
- Automatically provisions vRPAs and the Plugin Server from OVA
- Automatically deploys an RP4VMs cluster based on the JSON configuration file
- Configures the Plugin Server (Optional)
- Connects to existing RP4VMs environments (Optional)
What is it?
It’s a Python-based script that operates with the RecoverPoint for VMs Deployment REST API and vCenter.
In terms of requirements, the following list should help:
- The script requires Python 3.x and supports every platform on which Python is supported.
- Requires the Python requests module. It can be installed using pip with the command: “pip install requests” or “python -m pip install requests”.
- RecoverPoint for VMs 5.3.x.
- Connectivity from the host on which the script is running to vCenter, vRPAs. It also requires connectivity to the plugin server and peer clusters if applicable.
- RP4VMs 5.3.x vRPA and Plugin Server OVA images must be located on the host that is running the script.
How do I use it?
The script accepts one mandatory parameter -configfile or --config-file and two optional parameters: (1) pluginserver and (2) connect to prevent configuration of the plugin server and to skip connection to other clusters accordingly.
Here is the full script syntax:
# python rp4vms_deploy.py -h
Usage: rp4vms_deploy.py [-h] -configfile CONFIGFILE [-pluginserver] [-connect] Script to automate RP4VMs deployment options: -h, --help show this help message and exit -configfile CONFIGFILE, --config-file CONFIGFILE Full path to the JSON config file -pluginserver, --config-plugin-server Optionally prevents Plugin Server configuration -connect, --connect-another-cluster Optionally prevents connection to a different cluster
Use cases
I might be biased but there are so many cases where this solution can come in handy. Let’s look at some common use cases:
- Greenfield deployment of a two-cluster system:
In this case, we would run the script twice in the following manner:
a) Deploying the first cluster:
# python rp4vms_deploy.py -configfile clusterA_config.json -connect
b) Deploying the second cluster including cluster connect:
# python rp4vms_deploy.py -configfile clusterB_config.json
2. Adding a new cluster to an existing system:
# python rp4vms_deploy.py -configfile cluster_config.json
3. Scale out – adding new clusters to a separate system on the same vCenter and plugin server:
a) Deploying the first cluster:
# python rp4vms_deploy.py -configfile clusterA_config.json -pluginserver -connect
b) Deploying the second cluster including cluster connect:
# python rp4vms_deploy.py -configfile clusterB_config.json -pluginserver
Script output
# python rp4vms_deploy.py -configfile config.json -> Provisioning Plugin Server from OVA Opening OVA source: C:\Users\idan\Downloads\RecoverPoint-PluginServer_v5.3.3_282.ova Opening VI target: vi://Administrator%40vsphere.local@10.0.0.10:443/Hopkinton/host/Hop_HA1/ Deploying to VI: vi://Administrator%40vsphere.local@10.0.0.10:443/Hopkinton/host/Hop_HA1/ Transfer Completed Powering on VM: Manchester_Plugin-Server Task Completed Completed successfully ---> OVA deployment completed successfully -> Provisioning vRPA1 from OVA Opening OVA source: C:\Users\idan\Downloads\EMC_RecoverPoint_vRPA-RP4VMs_rel5.3.SP3_m.348.ova Opening VI target: vi://Administrator%40vsphere.local@10.0.0.10:443/Hopkinton/host/Hop_HA1/ Deploying to VI: vi://Administrator%40vsphere.local@10.0.0.10:443/Hopkinton/host/Hop_HA1/ Transfer Completed Powering on VM: Manchester_vRPA1 Task Completed Completed successfully ---> OVA deployment completed successfully -> Provisioning vRPA2 from OVA Opening OVA source: C:\Users\idan\Downloads\EMC_RecoverPoint_vRPA-RP4VMs_rel5.3.SP3_m.348.ova Opening VI target: vi://Administrator%40vsphere.local@10.0.0.10:443/Hopkinton/host/Hop_HA1/ Deploying to VI: vi://Administrator%40vsphere.local@10.0.0.10:443/Hopkinton/host/Hop_HA1/ Transfer Completed Powering on VM: Manchester_vRPA2 Task Completed Completed successfully ---> OVA deployment completed successfully -> Checking connectivity to vRPAs ---> vRPA Mgmt IP 10.247.8.118 is reachable ---> vRPA Mgmt IP 10.247.8.119 is reachable ---> All vRPAs are reachable -> Running deployment pre-validation checks ---> Transaction LOCAL_1 RUNNING 0% ---> Pre-installation validation passed successfully -> Timezone detected: Europe/London -> Searching for available vRPAs ---> Transaction LOCAL_2 RUNNING 0% ---> Transaction LOCAL_2 RUNNING 50% ---> Transaction LOCAL_2 RUNNING 50% ---> Transaction LOCAL_2 RUNNING 50% -> DS for Repository Volume detected -> Mgmt Network detected -> Building deployment configuration -> Deploying RP4VMs cluster ---> Transaction DEPLOY_3 RUNNING 0% ---> Transaction DEPLOY_3 RUNNING 52% ---> Transaction DEPLOY_3 RUNNING 52% ---> Transaction DEPLOY_3 RUNNING 52% ---> Transaction DEPLOY_3 RUNNING 53% ---> Transaction DEPLOY_3 RUNNING 53% ---> Transaction DEPLOY_3 RUNNING 84% ---> Transaction DEPLOY_3 RUNNING 84% ---> Transaction DEPLOY_3 RUNNING 84% ---> Transaction DEPLOY_3 RUNNING 84% -> Cluster deployed successfully -> Checking connectivity to cluster Mgmt IP ---> vRPA Cluster is reachable -> Checking connectivity to Plugin Server ---> Plugin Server is reachable -> Configuring Plugin Server -> Plugin Server configured successfully -> Running connectivity checks to peer cluster ---> Transaction LOCAL_28 RUNNING 0% ---> Transaction LOCAL_28 RUNNING 14% ---> Transaction LOCAL_28 RUNNING 44% ---> Transaction LOCAL_28 RUNNING 48% ---> Transaction LOCAL_28 RUNNING 52% ---> Transaction LOCAL_28 RUNNING 84% ---> Connectivity checks to peer cluster completed successfully -> Connecting clusters ---> Transaction LOCAL_29 RUNNING 0% ---> Transaction LOCAL_29 RUNNING 51% ---> Transaction LOCAL_29 RUNNING 51% ---> Clusters Connect completed successfully -> All tasks completed successfully
Where can I find it?
The script and the config file can be found at GitHub:
https://github.com/IdanKen/Dell-EMC-RecoverPoint4VMs
How can I get help?
You are more than welcome to file an issue in GitHub or reach out to me via email:
Idan.kentor@dell.com
Thanks for reading!
Idan
Author: Idan Kentor

How Dell Technologies Simplifies Data Protection
Thu, 04 Aug 2022 19:31:34 -0000
|Read Time: 0 minutes
As we are moving to the era of digitalization, more data is vulnerable to corruption, compromise, and loss. As a result, organizations are focusing on data protection strategies to improve security and data integrity. The key principle of data protection is to safeguard and make data available under all circumstances. Dell Technologies offers a variety of data protection products to make sure that data is secure and readily available. In this blog I’ll be covering a few of the outstanding data protection products that Dell provides.
Data protection and backup solutions
Cloud
As organizations are redistributing and extending their data to the cloud or to multiple clouds, protecting that data becomes critical. By implementing a multi-cloud data protection solution, users and developers can avoid cloud vendor lock-in by keeping data independent of the cloud, to reduce worry about high egress charges, migration risk, or time required to move data. Multi-Cloud Data Services for Dell PowerProtect, enabled by Faction, supports a data centric approach for users, allowing them to separate their data and cloud management strategies across public cloud providers. Multi-Cloud Data Services for Dell PowerProtect is a fully managed service that provides a single target for backup and recovery for AWS, Microsoft Azure, Google Cloud, and Oracle Cloud.
VMware
Data protection solutions from Dell Technologies gives customers the power to confidently plan their modern data protection strategies through constant innovation, agile engineering, and tight integration with VMware - all at a lower cost of ownership (TCO). Dell offers protection solutions for VMs, applications, and Kubernetes for a single platform for containerized products and workloads. The solution simplifies deployment and management of VMware workloads on-premises or in one or more public clouds.
Dell PowerProtect Cyber Recovery
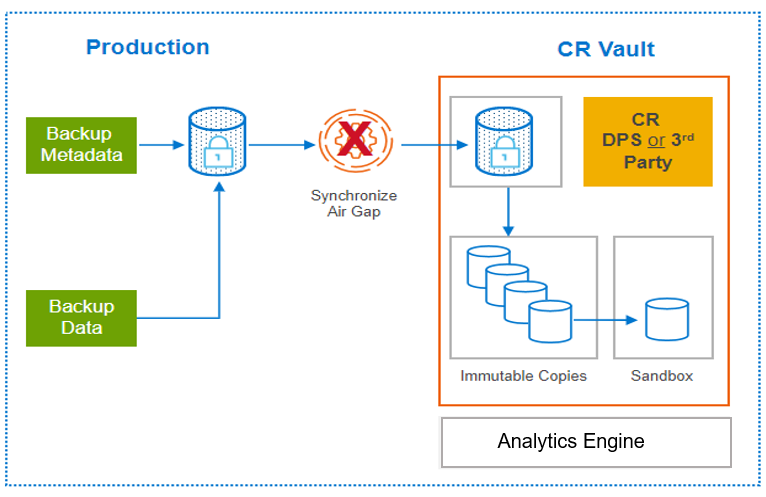
PowerProtect Cyber Recovery provides proven, modern, and intelligent protection to isolate critical data, identify suspicious activity, and accelerate data recovery, allowing you to resume normal business operations with confidence in case of a cyberattack. Critical data is stored immutably in a hardened vault, enabling recovery with assured data availability, integrity, and confidentiality. CyberSense is the analytics engine that is integrated with Cyber Recovery to help find data corruption when an attack penetrates the data center. CyberSense enables confident recovery of good data and offers insight into attack vectors from within the Cyber Recovery vault.
Data protection and backup appliances
Dell PowerProtect DD series appliances
 DD series is our purpose built backup target appliance. The DD operating system (DDOS) provides inline deduplication for data protection and disaster recovery (DR) in the environment. DDOS is the intelligence that powers DD series and PowerProtect systems. It provides the agility, security, and reliability that enables the platform to deliver scalable, high-speed and cloud-enabled protection storage for backup and archive. DD series appliances vary in storage capacity and data throughput. PowerProtect DD Virtual Edition (DDVE) is the software-defined version of the DD series: a virtual deduplication appliance that provides data protection for small-to-medium sized business, enterprise and service provider environments both on-prem and in-cloud.
DD series is our purpose built backup target appliance. The DD operating system (DDOS) provides inline deduplication for data protection and disaster recovery (DR) in the environment. DDOS is the intelligence that powers DD series and PowerProtect systems. It provides the agility, security, and reliability that enables the platform to deliver scalable, high-speed and cloud-enabled protection storage for backup and archive. DD series appliances vary in storage capacity and data throughput. PowerProtect DD Virtual Edition (DDVE) is the software-defined version of the DD series: a virtual deduplication appliance that provides data protection for small-to-medium sized business, enterprise and service provider environments both on-prem and in-cloud.
Dell PowerProtect DP series appliances
DP series is an integrated appliance solution thatprovides complete backup, replication, recovery, deduplication, instant access and restore, search & analytics, seamless VMware integration — plus, cloud readiness with disaster recovery (DR) and long-term retention (LTR) to the cloud — all in a single appliance. With the DP series, customers reduce their time-to-protect and become more agile with a reliable solution that’s fast, protected more efficiently, and can be recovered quickly.
Data protection and backup software
Dell Data Protection Suite
Dell PowerProtect Data Manager
 PowerProtect Data Manager software protects data and delivers governance control for modern cloud workloads across your evolving physical, virtual, and cloud environments. Address ever-changing growth and IT complexity by leveraging Dell software defined data protection platforms. PowerProtect Data Manager delivers next generation data protection that enables faster IT transformation, while giving you the assurance that you can easily safeguard and quickly unlock your data’s value. This software-defined solution includes self-service protection, centralized governance, and SaaS-based reporting and monitoring.
PowerProtect Data Manager software protects data and delivers governance control for modern cloud workloads across your evolving physical, virtual, and cloud environments. Address ever-changing growth and IT complexity by leveraging Dell software defined data protection platforms. PowerProtect Data Manager delivers next generation data protection that enables faster IT transformation, while giving you the assurance that you can easily safeguard and quickly unlock your data’s value. This software-defined solution includes self-service protection, centralized governance, and SaaS-based reporting and monitoring.
Dell Avamar
Avamar is backup and recovery software that provides integrated data deduplication technology. Avamar solves the challenges that are associated with traditional data protection, enabling fast and reliable backup and recovery for remote offices, VMware environments, DD series and Cloud Tier, and data center LANs. Unlike traditional solutions, Avamar reduces the size of backup data at the source—before it transfers across the network and stores to disk. As a result, Avamar delivers fast, efficient daily full backups despite slow or congested infrastructure, and data encryption for added security.
Avamar is available as a virtual edition or as a component of Data Protection Suite, which offers you a complete suite of data protection software options.
Dell NetWorker
NetWorker software provides unified backup and recovery of enterprise applications and databases. With centralized administration, NetWorker helps you take advantage of the data protection that fits your needs best: deduplication, backup to disk and tape, snapshots, replication, and NAS. NetWorker protects both physical and virtual environments including VMware and Microsoft Hyper-V. It provides the same enterprise-level experience, whether you are protecting data and applications within the data center or in the public cloud.
NetWorker is available as virtual edition (NVE) or as a component of the Data Protection Suite, which offers you a complete suite of data protection software options.
Dell Data Protection Advisor
Data Protection Advisor allows you to unify and automate monitoring, alerting, and reporting across your data protection software and storage environments, including on-premises and cloud. Data Protection Advisor enables you to make informed decisions faster, to increase efficiency.
Dell RecoverPoint for Virtual Machines
RecoverPoint for Virtual Machines enables quick recovery of VMware virtual machines to any point in time. RecoverPoint for VMs provides continuous data protection (CDP) for operational recovery and disaster recovery. It is hypervisor-based, software-only data replication that integrates with VMware vCenter.
Dell APEX Backup Services
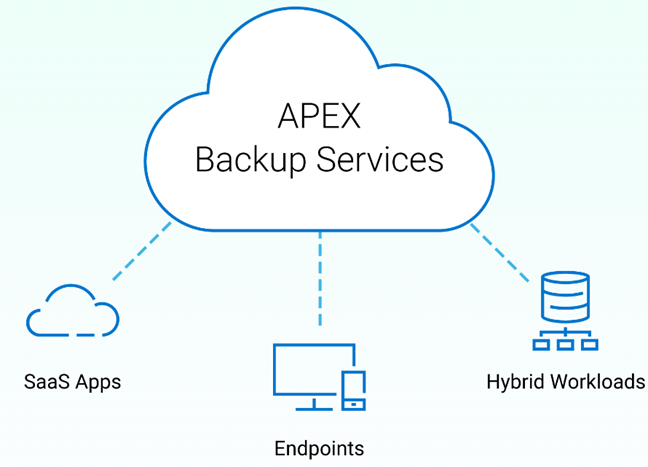
APEX Backup Services is a cloud-based data protection solution that ensures predictable, controllable costs without increasing complexity. It deploys in minutes and provides unlimited on-demand scaling to ensure that growing data volumes are always protected. An intuitive web-based experience provides centralized visibility and management across workloads and users, to ensure that your data is always protected.
With changing times, data protection solutions provided by Dell have also changed, and for the better. The variety of data protection products provided by Dell Technologies makes sure that data is easy to access, readily available, secured, and uncorrupted.
For more details, see the following resources:
Author: Charu, Engineering Technologist 2
