

Secure Cloud: Check! Flexible Cloud Networking: Check! Powerful Cloud Hardware: Check!
Wed, 03 Aug 2022 21:32:14 -0000
|Read Time: 0 minutes
Dell Technologies and VMware are happy to announce the availability of VMware Cloud Foundation 4.3.0 on VxRail 7.0.202. This new release provides several security-related enhancements, including FIPS 140-2 support, password auto-rotation support, SDDC Manager secure API authentication, data protection enhancements, and more. VxRail-specific enhancements include support for the more powerful, 3rd Gen AMD EYPC™ CPUs and NVIDIA A100 GPUs (check this blog for more information about the corresponding VxRail release), and more flexible network configuration options with the support for multiple System Virtual Distributed Switches (vDS).
Let’s quickly discuss the comprehensive list of the new enhancements and features:
VCF and VxRail Software BOM Updates
These include the updated version of vSphere, vSAN, NSX-T, and VxRail Manager. Please refer to the VCF on VxRail Release Notes for comprehensive, up-to-date information about the release and supported software versions.
VCF on VxRail Networking Enhancements
Day 2 AVN deployment using SDDC Manager workflows
The configuration of an NSX-T Edge cluster and AVN networks are now a post-deployment process that is automated through SDDC Manager. This approach simplifies and accelerates the VCF on VxRail Bring-up and provides more flexibility for the network configuration after the initial deployment of the platform.
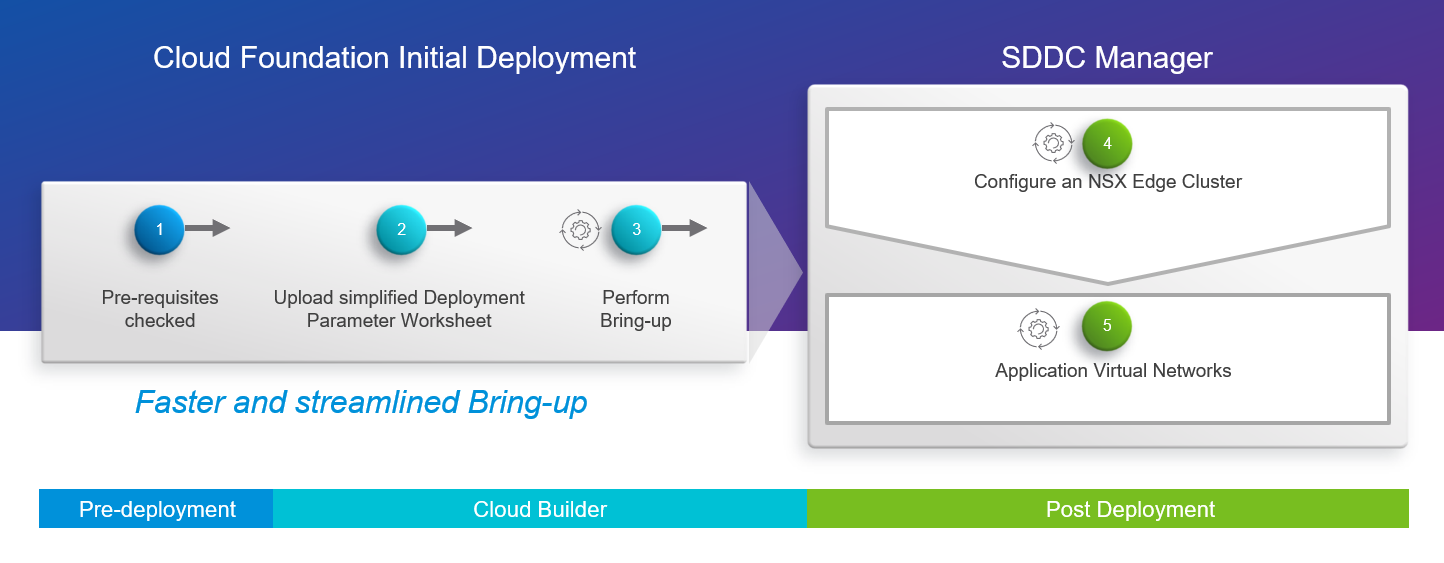
Figure 1: Cloud Foundation Initial Deployment – Day 2 NSX-T Edge and AVN
Shrink and expand operations of NSX-T Edge Clusters using SDDC Manager workflows
NSX-T Edge Clusters can now be expanded and shrunk using in-built-in automation from within SDDC Manager. This allows VCF operators to scale the right level of resources on-demand without having to size for demand up-front, which results in more flexibility and better use of infrastructure resources in the platform.
VxRail Multiple System VDS support
Two System Virtual Distributed Switch (vDS) configuration support was introduced in VxRail 7.0.13x. VCF 4.3 on VxRail 7.0.202 now supports a VxRail deployed with two system vDS, offering more flexibility and choice for the network configuration of the platform. This is relevant for customers with strict requirements for separating the network traffic (for instance, some customers might be willing to use a dedicated network fabric and vDS for vSAN). See the Figure 2 below for a sample diagram of the new network topology supported:
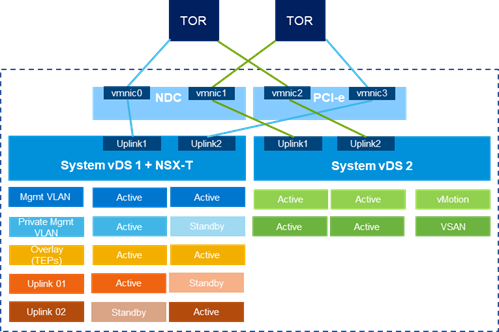
Figure 2: Multiple System VDS Configuration Example
VCF on VxRail Data Protection Enhancements
Expanded SDDC Manager backup and restore capabilities for improved VCF platform recovery
This new release introduces new abilities to define a periodic backup schedule, retention policies of backups, and disable or enable these schedules in the SDDC Manager UI, resulting in simplified backup and recovery of the platform (see the screenshot below in Figure 3).
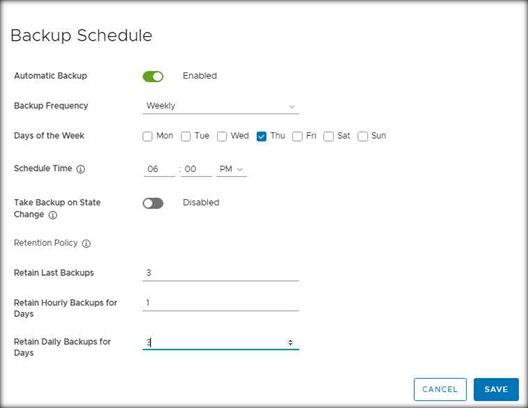
Figure 3: Backup Schedule
VCF on VxRail Security Enhancements
SDDC Manager certificate management operations – expanded support for using SAN attributes
The built-in automated workflow for generating certificate signing requests (CSRs) within SDDC Manager has been further enhanced to include the option to input a Subject Alternate Name (SAN) when generating a certificate signing request. This improves security and prevents vulnerability scanners from flagging invalid certificates.
SDDC Manager Password Management auto-rotation support
Many customers need to rotate and update passwords regularly across their infrastructure, and this can be a tedious task if not automated. VCF 4.3 provides automation to update individual supported platform component passwords or rotate all supported platform component passwords (including integrated VxRail Manager passwords) in a single workflow. This feature enhances the security and improves the productivity of the platform admins.
FIPS 140-2 Support for SDDC Manager, vCenter, and Cloud Builder
This new support increases the number of VCF on VxRail components that are FIPS 140-2 compliant in addition to VxRail Manager, which is already compliant with this security standard. It improves platform security and regulatory compliance with FIPS 140-2.
Improved VCF API security
Token based Auth API access is now enabled within VCF 4.3 for secure authentication to SDDC Manager by default. Access to private APIs that use Basic Auth has been restricted. This change improves platform security when interacting with the VCF API.
VxRail Hardware Platform Enhancements
VCF 4.3 on VxRail 7.0.202 brings new hardware features including support for AMD 3rd Generation EPYC CPU Platform Support and Nvidia A100 GPUs.
These new hardware options provide better performance and more configuration choices. Check this blog for more information about the corresponding VxRail release.
VCF on VxRail Multi-Site Architecture Enhancements
NSX-T Federation guidance - upgrade and password management Day 2 operations
New manual guidance for password and certificate management and backup & restore of Global Managers.
As you can see, most of the new enhancements in this release are focused on improving platform security and providing more flexibility of the network configurations. Dell Technologies and VMware continue to deliver the optimized, turnkey platform experience for customers adopting the hybrid cloud operating model. If you’d like to learn more, please check the additional resources linked below.
Additional Resources
VMware Cloud Foundation on Dell EMC VxRail Release Notes
VxRail page on DellTechnologies.com
VCF on VxRail Interactive Demos
Author Information
Author: Karol Boguniewicz, Senior Principal Engineering Technologist, VxRail Technical Marketing
Twitter: @cl0udguide
Related Blog Posts

Announcing VMware Cloud Foundation 4.4.1 on Dell VxRail 7.0.371
Wed, 25 May 2022 14:07:35 -0000
|Read Time: 0 minutes
With each turn of the calendar, as winter dissipates and the warmer spring weather brings new life back into the world, a certain rite of passage comes along with it: Spring Cleaning! As much as we all hate to do it, it is necessary to ensure that we keep everything operating in tip top shape. Whether it be errands like cleaning inside your home or repairing the lawn mower to be able to cut the grass, we all have them, and we all recognize they are important, no matter how much we try to avoid it.
The VMware Cloud Foundation (VCF) on Dell VxRail team also believes in applying a spring cleaning mindset when it comes to your VCF on Dell VxRail cloud environment. This will allow your cloud environment to keep running in an optimal state and better serve you and your consumers.
So, in the spirit of the spring season, Dell is happy to announce the release of Cloud Foundation 4.4.1 on VxRail 7.0.371. Beginning on May 25, 2022, existing VCF on VxRail customers will be able to LCM to this latest version while support for new deployments will be made available beginning June 2, 2022.
This new release introduces the following “spring cleaning” enhancements:
- New component software version updates
- New VxRail LCM logic improvements
- New VxRail serviceability enhancements
- VCF and VxRail software security bug fixes
- VCF on VxRail with VMware Validated Solution Enhancements
VCF on VxRail life cycle management enhancements
New VxRail prechecks and vSAN resync timeout improvements
Starting with this release, the VxRail LCM logic has been modified to address scenarios when the cluster update process may fail to put a node into Maintenance Mode. This LCM logic enhancement is leveraged in addition to similar SDDC Manager prechecks that already exist. All VxRail prechecks are used when SDDC Manager calls on VxRail to run its precheck workflow prior to an LCM update. SDDC Manager does this by using its integration with the VxRail Health Check API. SDDC Manager also calls on these prechecks during an LCM update using its integration with the VxRail LCM API. So, VCF on VxRail customers benefit from this VxRail enhancement seamlessly.
Failing to enter Maintenance Mode can cause VxRail cluster updates to fail. Finding ways to mitigate this type of failure will significantly enhance the LCM reliability experience for many VCF on VxRail customers.
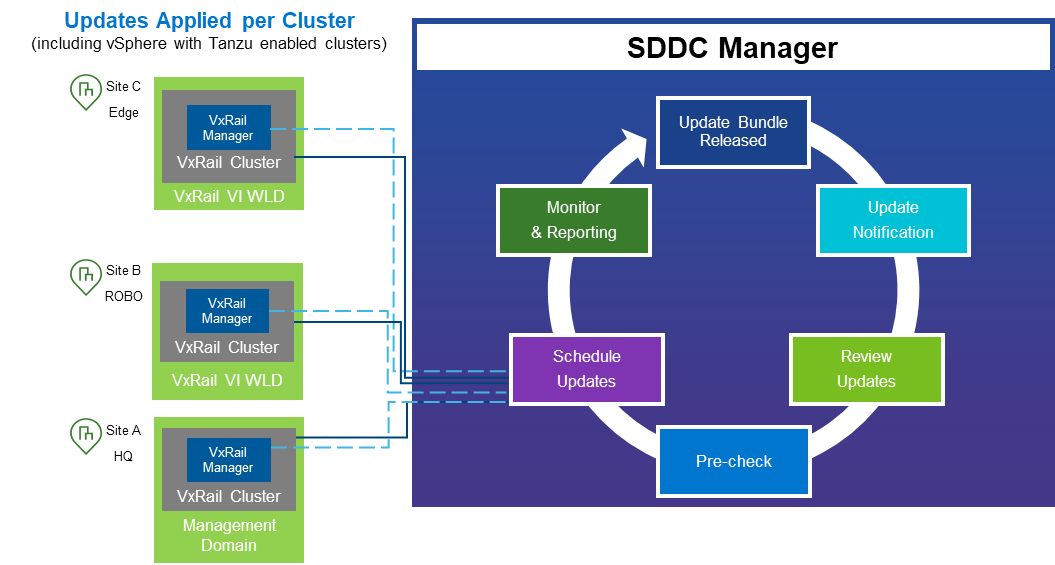
Figure 1: VCF on VxRail LCM
The following list describes scenarios in which a VxRail node could fail to enter maintenance mode, but are improved with the latest enhancements:
- If VMtools are mounted to customer VM workloads: VxRail LCM precheck now checks for this state to detect if VMtools are mounted. If this exists, it is the administrator’s responsibility to address the issue in their environment before initiating a VxRail cluster update.
- If VMs are pinned to specific hosts: VxRail LCM precheck will now detect whether there is host pinning configured for VMs. If this exists, it is the administrator’s responsibility to address the configuration in their environment before initiating a cluster update.
- vSAN Resync Time Timeout: During the cluster update process, a VxRail node can fail if vSAN resync takes too long. When the system waits before the node is put into Maintenance Mode, it causes a timeout. To prevent this from happening, the VxRail vSAN Resync timeout value has been increased by 2x while the cluster update waits for the vSAN resync to finish.
VCF on VxRail serviceability enhancements
Support for next generation Dell secure remote service connectivity agent and gateway
VxRail systems will now use the next generation secure remote service connectivity agent and the Secure Connect Gateway to connect to the Dell cloud for dial home serviceability. This new connectivity agent running within VxRail will also be used on all Dell infrastructure products.
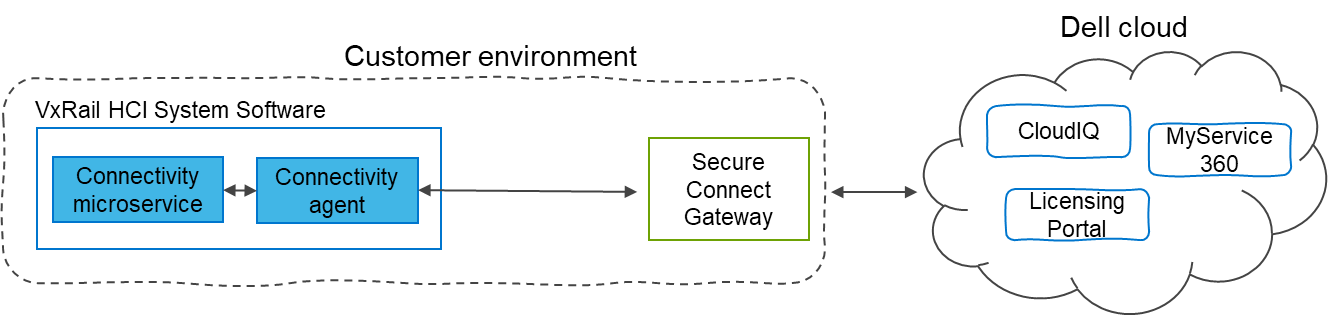
Figure 2: Next Generation Dell Secure remote connectivity agent and gateway architecture
The Secure Connect Gateway is the 5th generation gateway that acts as a centralization point for Dell products in the customer environment to manage the connection to the Dell cloud. This remote connectivity enables a bi-directional communication between the product and Dell cloud. Products can send telemetry data and event information to the Dell cloud which can be used to facilitate remote support by Dell services as well as to deliver cloud services such as CloudIQ, MyService360, Licensing Portal, and Service Link.
The latest generation remote service connector is intended to provide a uniform telemetry experience across all Dell ISG products. By providing standardization, customers can reduce redundant infrastructure used to provide remote services for all their Dell products. The connectivity agent also introduces a simpler setup experience by streamlining and automating setup process of the secure remote service for new VxRail cluster deployments.
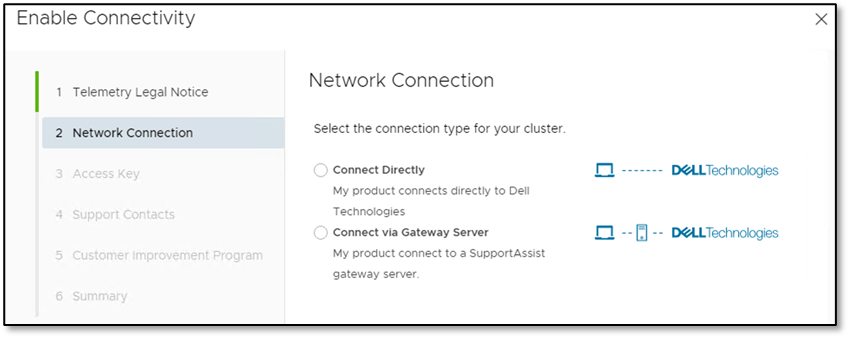
Figure 3: Enabling secure remote gateway connectivity
For existing VxRail clusters running an earlier version than VCF 4.4.1 on VxRail 7.0.371 in a VCF on VxRail deployment, the migration effort to adopt the new secure connect gateway requires the administrator to first upgrade their older generation dell serviceability gateways in their environment (whether it’s the 3rd generation Secure Remote Service gateway or the 4th generation Dell SupportAssist Enterprise gateway).
Once the gateways are upgraded to the latest 5th generation Dell Secure Connect Gateway, the VCF on VxRail administrator can perfrom the VxRail cluster update for the migration, as part of the standard VCF on VxRail LCM process. The built-in VxRail LCM precheck steps will inform the administrator to upgrade their gateways if necessary. The VxRail cluster update will now retrieve the gateway configuration for the connectivity agent and convert the device or access key to a unique connectivity key for remote connection authentication. Administrators should be aware that this additional migration work may add a one time 15 minutes or so time increase to the total cluster update time.
New nodes that are shipped with VxRail 7.0.350 or higher will also now include a unique connectivity key for the secure remote gateway. Dell manufacturing will embed this key into the iDRAC of the VxRail nodes. So, instead of a user logging onto the Dell support portal to retrieve the access key to enable secure remote services, the enablement process will automatically retrieve this unique connectivity key from iDRAC for the connectivity agent to enable the connection. This feature is designed to simplify and streamline the secure connect gateway serviceability setup experience.
Customers can also have a direct connection to Dell cloud bypassing having a gateway deployed. This option is available for any clusters running VxRail 7.0.350 and higher.
VxRail dial home payload improvements
VxRail dial home payload improvements have been introduced to help provide Dell support with additional key cluster information in the dial home payload itself and capture more system error conditions to help further improve VCF on VxRail serviceability and reduce time to resolution of any VxRail related issues.
Additional payload information now includes:
- Smart Logs: Smart logging automatically collects the logs on the node of the call-home event, which provides additional information to the Support team when necessary. Starting with VCF 4.4.1 on VxRail 7.0.371, smart logging functionality has been redesigned to achieve the following tasks:
- Adapt smart logging workflow to the new secure remote gateway architecture
- Associate smart log with Dell Service Request (SR) such that the smart log file can be included in the SR as a link.
- Sub-component details: These include information such as the part number and slot number for CRU/FRU items such as disk drives and memory DIMMs for more efficient auto-dispatch of these failed components.
- VxRail cluster personality identifier information: To help making the troubleshooting experience more efficient, this cluster metadata information allows Dell Support to know that the VxRail clusters are deployed within a VCF on VxRail environment.
Also included are additional error conditions that are now captured to bring VxRail events in parity with existing PowerEdge events and additional ADC error states. And finally, to reduce the cost of service and improve the customer experience by avoiding a deluge of unnecessary event information, some events are no longer being reported.
VxRail physical view UI update now includes Fiber Channel HBA hardware view
New support for FC HBA Physical HW views have been introduced as part of the VxRail Manager vCenter Plugin Physical View UI for E560F, P570F, and V570F VxRail nodes that support externally attached storage.
Supported FC HBAs include the following Emulex and QLogic models:
- Emulex LPE 35002 Dual Port 32 Gb HBA
- Emulex LPE 31002 Dual Port 16 Gb HBA
- QLogic 2772 Dual Port 32 Gb HBA
- QLogic 2692 Dual Port 16 Gb HBA
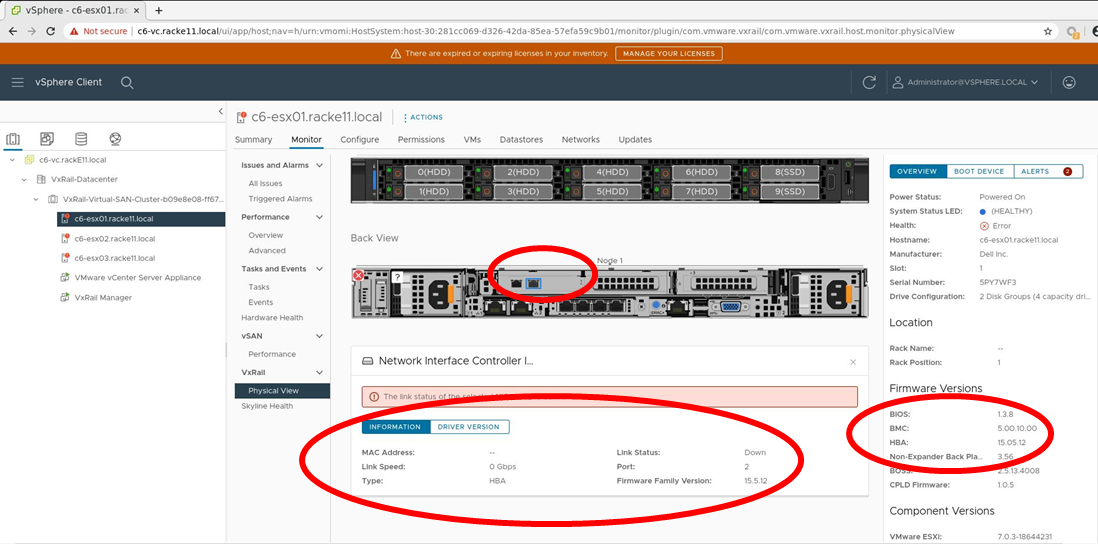
Figure 4: Fiber Channel HBA physical hardware view in VxRail Manager vCenter Plugin – firmware
This new functionality provides a similar UI viewing experience to what administrators are already used to seeing, regarding physical NICs and NIC ports. This new FC HBA view will include port link status and firmware/driver version information. An example of the firmware/driver views is shown in Figure 4.
VCF on VxRail security enhancements
VCF and VxRail software security vulnerability fixes
This release includes several security vulnerabilities fixes for both VxRail and VCF software components.
VxRail Software 7.0.371 contains fixes that resolve multiple security vulnerabilities. Some of these include:
- DSA-2022-084
- DSA-2022-056
- DSA-2021-255
- iDRAC8 Updates
For more information, see iDRAC8 2.82.82.82 Release Notes
For more details on the DSAs, see the Dell Security Advisory (DSA) portal and search for DSA IDs.
VCF 4.4.1 Software: This contains fixes that resolve issues in NSX-T by introducing support for NSX-T 3.1.7.3.2. For more information about these issues, see the VMware KB Article.
vRealize Suite Software: In the last VCF 4.4 on VxRail 7.0.320 release we introduced vRealize Flexible Upgrades. Read more about it here. As a result, the vRealize Suite components (other than vRealize Suite Lifecycle Manager) are no longer a part of the VCF core software package. So if there are security vulnerabilities that are discovered and relevant patches that need to be applied, the process of doing so has changed. No longer will those vRealize component software updates be delivered and applied through VCF software update bundles. Administrators now must apply them independently using vRSLCM starting from the VCF 4.4 on VxRail 7.0.320 release.
I bring this up because there has been some vRealize Suite component security patches that have also been released that are relevant to VCF 4.4.1 on VxRail 7.0.371 deployments. See this blog post, written by my peers on the VMware team, describing the issue related to VMSA-2022-0011 and how to apply the fixes for it.
VCF on VxRail with VMware Validated Solution enhancements
New VCF on VxRail qualification with VMware Validated Solutions
For those of you who aren’t aware, VMware Validated Solutions are technical validated implementations built and tested by VMware and VMware Partners. These solutions are designed to help customers solve common business problems using VMware Cloud Foundation as the foundational infrastructure. Types of solutions include Site Protection and Disaster Recovery for VMware Cloud Foundation using multi-site VCF deployments with stretched NSX-T networks and Advanced Load Balancing for VMware Cloud Foundation using VMware NSX Advanced Load Balancer for workloads on VCF. These validated solution designs have been enhanced over time to include VMware developed automation scripts to help customers further simplify and accelerate getting these implemented. You can learn more about them here.
Although this solution is not directly tied to this latest VCF 4.4.1 on VxRail 7.0.371 release as a release feature itself, VMware and Dell can now qualify the VMware Validated Solutions on VCF on VxRail. All VVS solutions that are qualified will be marked with a VxRail tag.
 Figure 5: VMware Validated Solutions Portal
Figure 5: VMware Validated Solutions Portal
These solutions get updated asynchronously from VCF releases. Be sure to check the VMware VVS portal for the latest updates on existing solutions or to see when new solutions are added.
That’s a wrap
Thanks for taking the time learn more about VMware Cloud Foundation on Dell VxRail. For even more solution information, see the Additional Resources links at the bottom of this post. I don’t know about you, but I feel squeaky clean already! Can’t say the same about my outdoor landscaping though...I should probably go address that…
Author: Jason Marques
Twitter: @vWhipperSnapper
Additional Resources
VMware Cloud Foundation on Dell VxRail Release Notes
VxRail page on DellTechnologies.com

Learn more about the latest major VxRail software update: VxRail 7.0.240
Wed, 24 Apr 2024 12:00:32 -0000
|Read Time: 0 minutes
In a blink of an eye, September is already here. All those well-deserved August holidays have come and gone. As those summer memories with colorful umbrella drinks in hand fade into the background, your focus now turns to finishing this year strong. With the recent announcement on the latest VxRail software release, VxRail is providing the juice to get you well on your way.
VxRail HCI System Software version 7.0.240 has arrived with much anticipation as it includes the expansion of the VxRail product portfolio in the form of VxRail dynamic nodes and significant lifecycle management (LCM) enhancements that our VxRail customers will surely appreciate. Dynamic nodes extend the spectrum of use cases for VxRail by addressing more workload types. The LCM enhancements in the latest software release add to the operational simplicity that VxRail users truly value by increasing the level of automation and flexibility to ensure cluster integrity throughout the life of their cluster.
VxRail dynamic nodes
As VxRail dynamic nodes were described in the external launch event, they benefit customers who are committed to continue running their mission-critical data-centric workloads on Dell EMC storage arrays because of the enterprise-level resiliency and data protection capabilities but value the operational certainty that VxRail offers to their IT teams. This use case can be particularly relevant for customers who have standardized on VCF on VxRail as their infrastructural building block for their cloud operating model. These scenarios can apply to financial and medical industries among many others. For some customers, scaling of storage and compute independently in their HCI environments can better suit some of their application workloads, whether it is a better use of resources or potential reduction in license costs for compute-intensive workloads like Oracle.
Piqued your interest? Let’s move deeper into the technical details so you can better understand how VxRail dynamic nodes address these use cases.
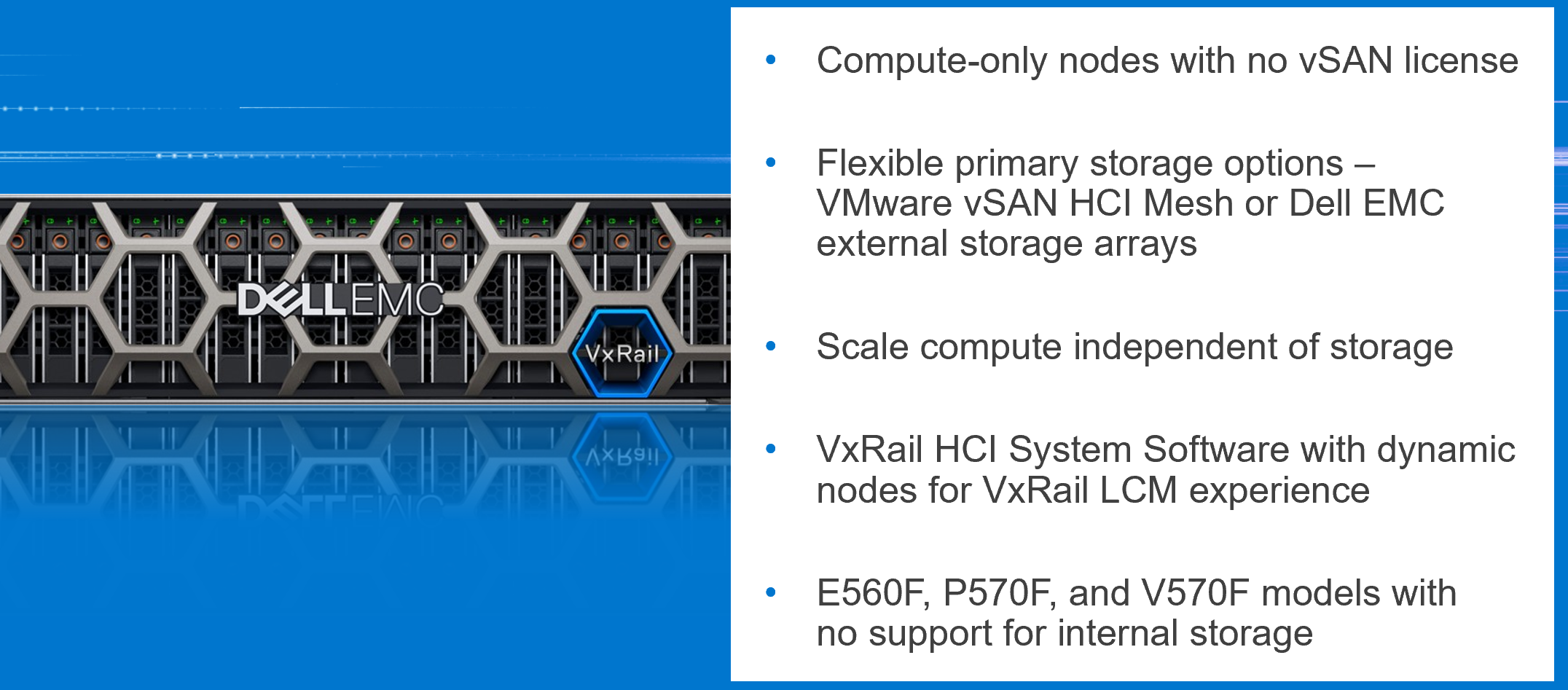
Figure 1: VxRail dynamic node offering
- VxRail dynamic nodes are compute-only nodes running vSphere. Dynamic nodes run VMware ESXi with vSphere Enterprise Plus licenses but do not have vSAN licenses.
- They do not have any internal drives. As a result, the VxRail Manager VM runs on an external datastore that can come from either Dell EMC storage arrays (PowerStore-T, PowerMax, and Unity XT) or VMware vSAN HCI Mesh. Customers can now scale their compute and storage independently while some customers can continue to leverage their Dell EMC storage arrays for enterprise-level resiliency options.
- Dynamic nodes run on the same VxRail HCI System Software as any other VxRail cluster. The same intelligent LCM experience backed by VxRail’s Continuously Validated States exists in dynamic nodes.
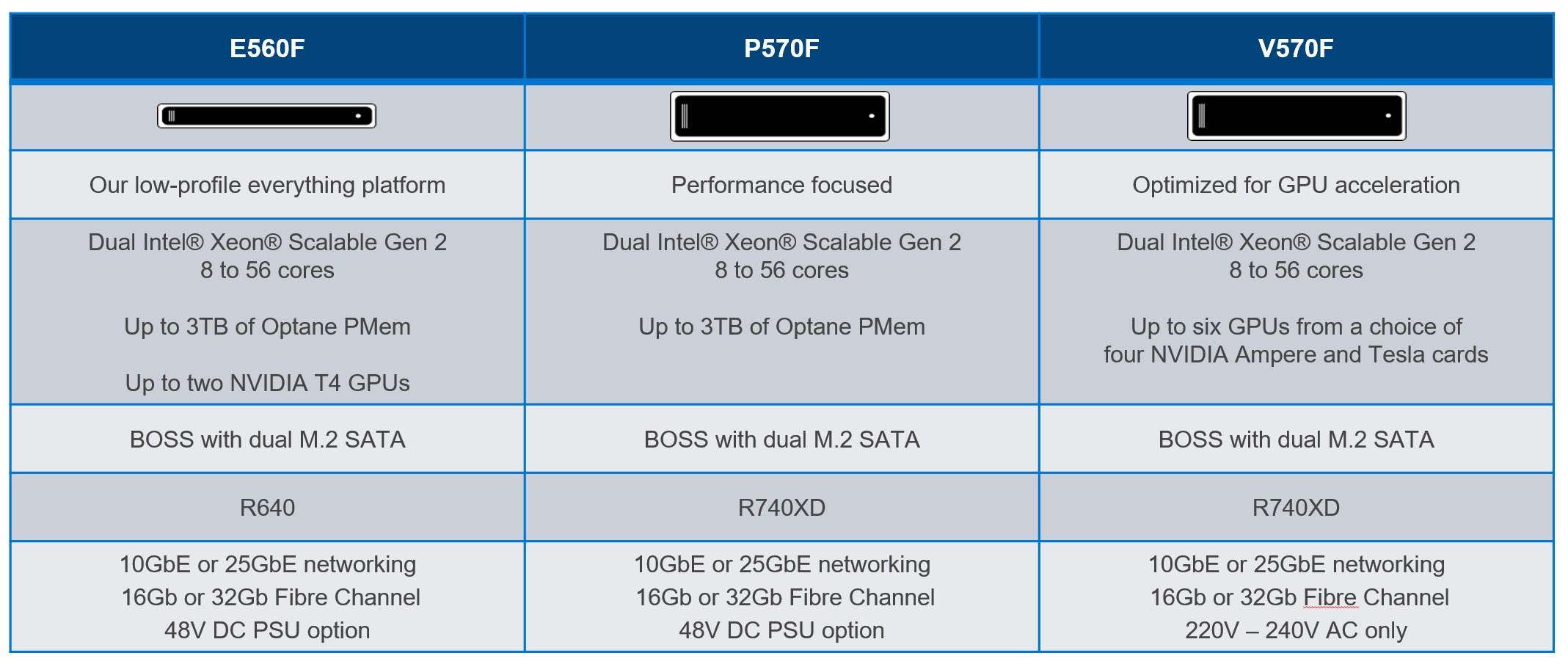
Figure 2: VxRail dynamic node platforms
Like the three-flavor Neapolitan ice cream tub, there’s a flavor of dynamic nodes to match each application requirement. While there are not any cache and capacity drives on dynamic nodes, all other hardware configurations on these models are available. The E-series is the space-efficient 1U platform. The P-series is the performance-focused platform. The V-series is optimized for GPU-acceleration with up to six GPUs per node.
For those wanting to use their Dell EMC storage arrays with these brand-new VxRail dynamic nodes, here are some important pieces of information to consider.
- With VxRail 7.0.240, Dell EMC PowerStore-T, PowerMax, and UnityXT are the supported external arrays for this use case. Third-party storage arrays are not supported.
- Storage connectivity is through Fibre-Channel, either 16Gb or 32Gb Dell EMC Connectrix Brocade or Cisco MDS FC switches.
- Management of the storage array and Fibre-Channel switch is done separately including lifecycle management, zoning, and provisioning of storage. VxRail HCI System Software is responsible for the LCM of the dynamic nodes themselves.
- When deploying a dynamic node cluster, the datastores need to be already provisioned and zoned to the dynamic nodes.
- The storage array and dynamic nodes are sold separately and supported discretely by Dell Technologies.
LCM Enhancements
Now let’s move onto the LCM enhancements in VxRail 7.0.240. There are three notable enhancements that VxRail users will notice – unless their thoughts have drifted away into those summertime memories.
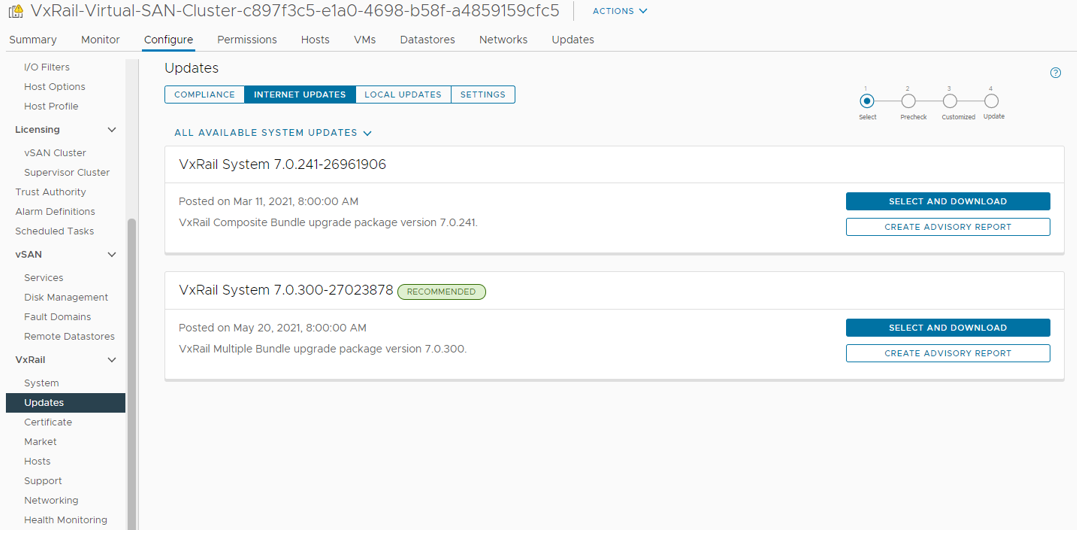
Figure 3: Update advisor
First, update advisor is a new tool to help you plan for their next cluster update. From the Updates > Internet Updates tab, you can now see a list of available update paths for their specific cluster. This feature does not replace your responsibility to review the release notes and decide on to which version to update their cluster but, it does generate an advisory report with critical information to let you know what needs to be updated based on your cluster’s current Continuously Validated State. Update advisor is a helpful tool to plan your maintenance window.
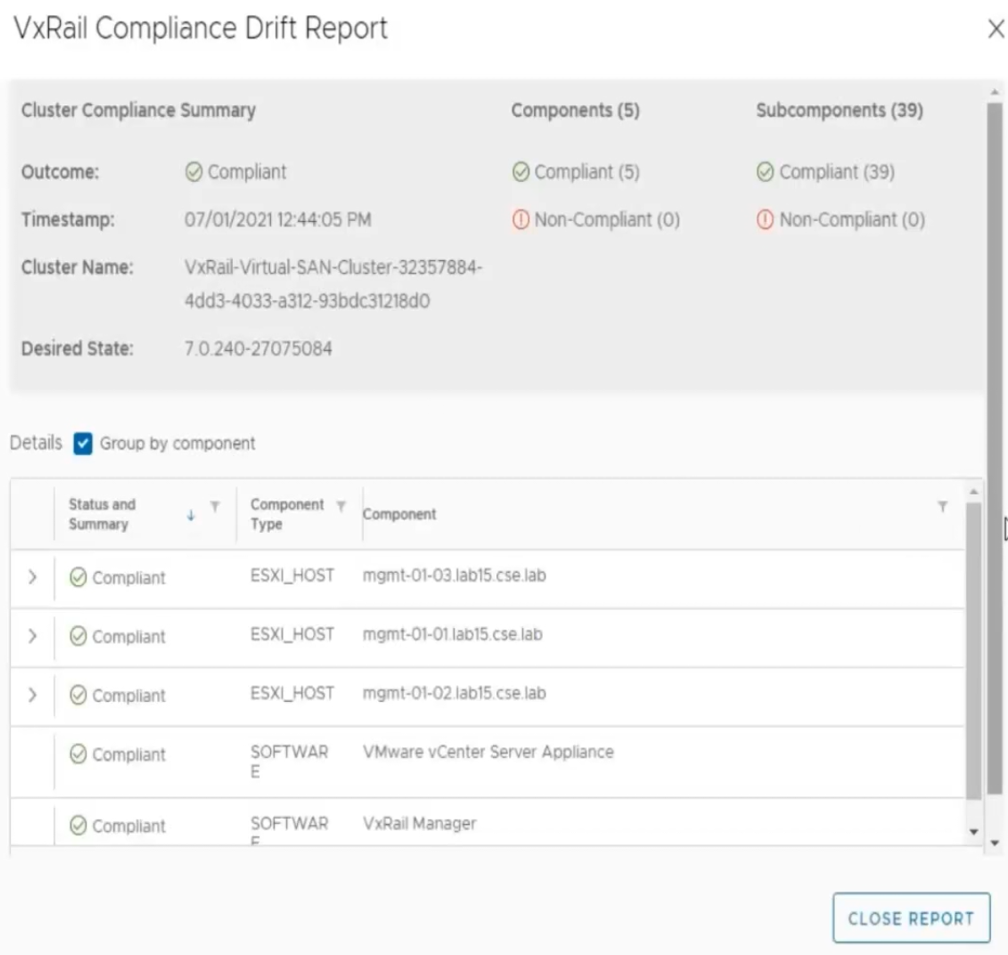
Figure 4: Sample compliance drift report
Second, VxRail Manager now has a compliance checker that will detect any unforeseen version drift from the current Continuously Validated State running on your VxRail cluster. As shown on the image above, it provides a component-by-component report as part of the compliance check. It is run daily by default and can be initiated on-demand.
The third LCM enhancement is VxRail LCM compatibility with VMware vSphere Lifecycle Manager (vLCM).
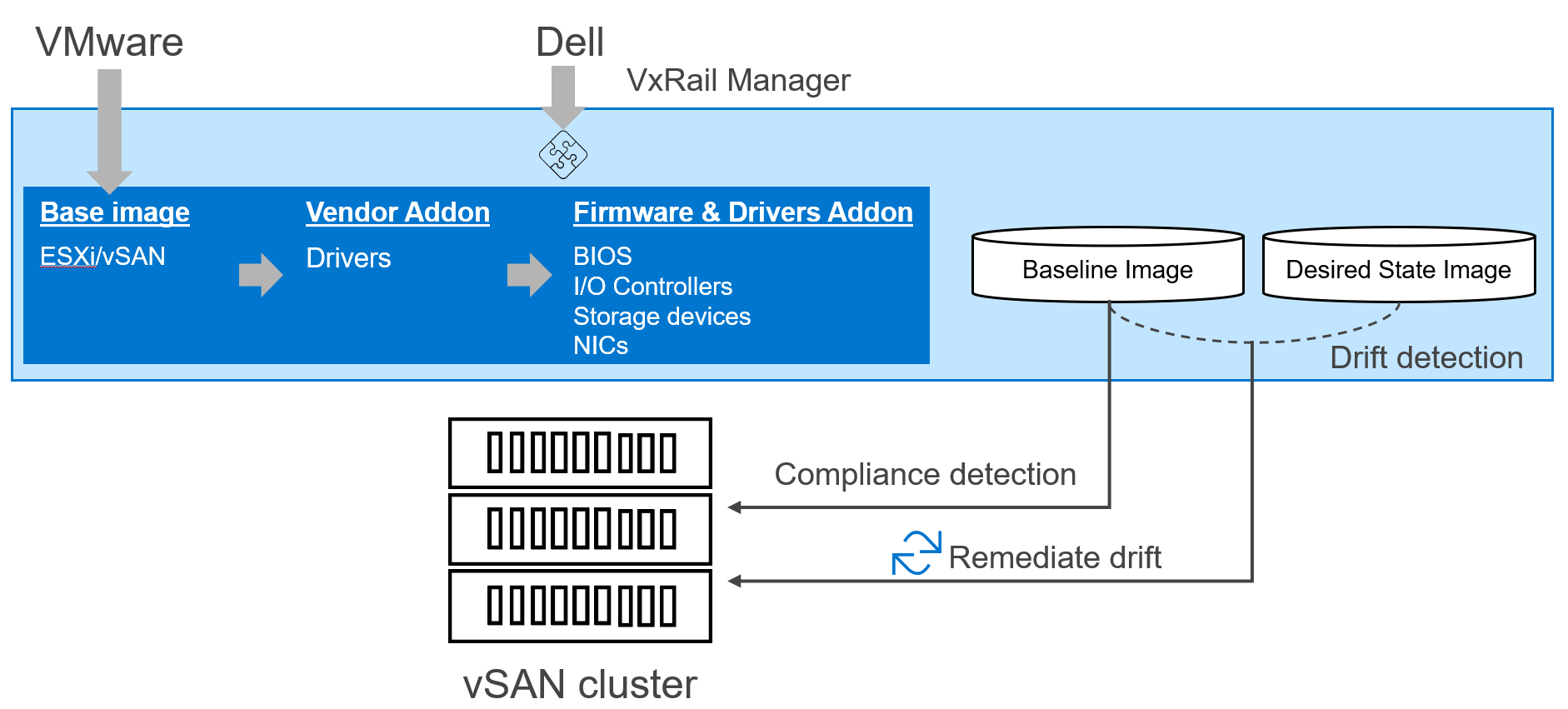
Figure 5: VMware vSphere Lifecycle Manager vLCM framework
As a refresher, VMware vLCM was introduced in vSphere 7.0 as a framework to allow for software (ESXi) and hardware (firmware and drivers) to be updated together as a single system. VMware supplies the base image which is the ESXi image, and then it is up to the hardware vendors, like Dell Technologies, to provide the hardware support manager that plugs into that framework to supply the necessary firmware and drivers and to update them. Together, they form the baseline image which is used for the compliance checker. When updating the cluster, a desired state image is built from a combination of VMware-provided ESXi image and vendor(s)-provided firmware and drivers. Based on the drift detection analysis between the baseline and desired state images, vLCM will remediate the hosts on the cluster to complete the update.
VxRail’s newly introduced vLCM compatibility enables the VxRail Manager VM to plug into the framework to perform cluster updates using VxRail-provided desired state images in the form of Continuously Validated States. Essentially, VxRail has automated the hardware support manager plugin setup and exporting the depot of firmware and drivers to vCenter, which is a very manual process for other HCI solutions. While other hardware support manager plugins to vLCM require a multiple-step procedure to establish a baseline image and desired state image and interaction with multiple interfaces, VxRail’s implementation leverages the vLCM APIs to truly obfuscate those complexities into a streamlined experience all within VxRail Manager. Because VxRail Manager already stores the Continuously Validated State on its VM, the process of identification and exporting of the hardware firmware and drivers on the VxRail stack can easily be automated. The simplicity of VxRail’s support for vLCM cannot be understated.
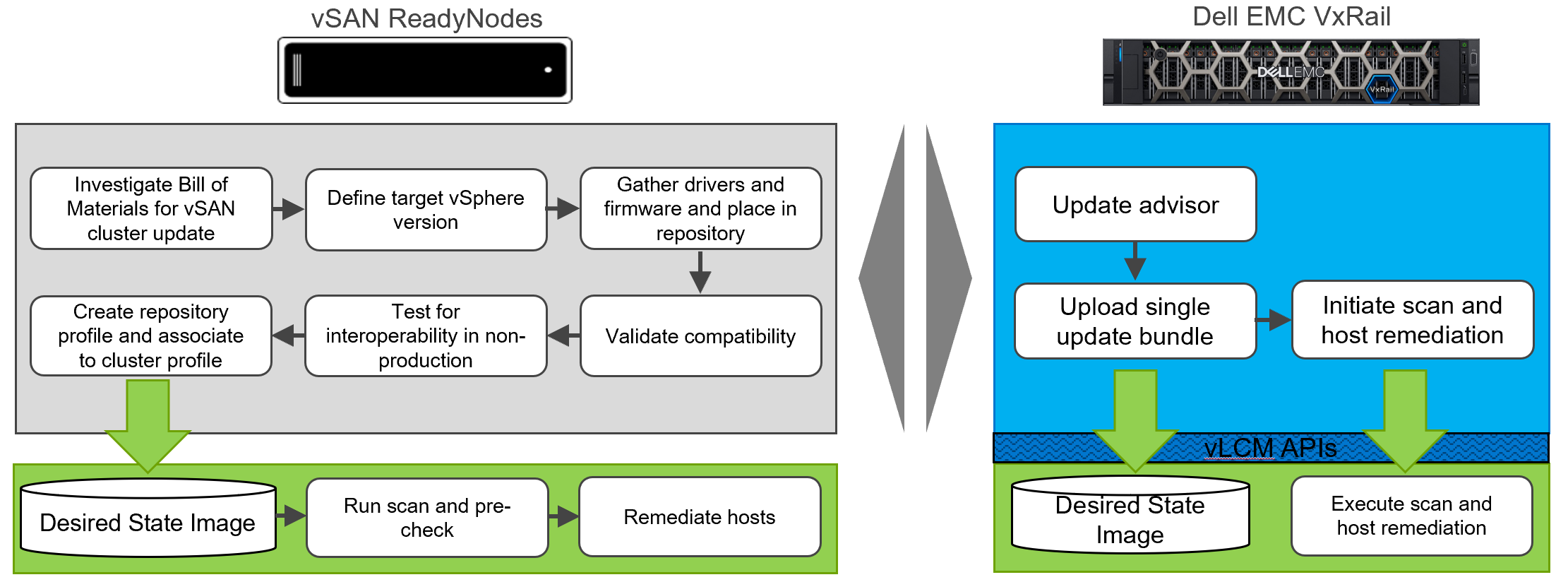
Figure 6: VxRail’s vLCM implementation automates and simplifies the user’s cluster update experience
Similarly, performing cluster updates is a streamlined process once the LCM bundle is downloaded onto the VxRail Manager VM. From VxRail Manager, via the vLCM APIs, the bundle is loaded onto the vLCM framework as the desired state image. In short, vLCM compatibility is mostly transparent to the user as the LCM experience still runs through VxRail Manager.
The next likely question is why offer this enhancement? The explanation can be conveyed in two points both related to cutting down the time to update the cluster.
- Consolidate VMware software updates – for users that already run NSX-T or vSphere with Tanzu, vLCM allows for those VIBs to be included into the desired state image. Instead of updating each VMware software separately, they can be done together in a single boot cycle.
- Consolidate non-VxRail managed components – there are a few components such as the FC HBA that are not part of Continuously Validated State. Those components would then need to be updated separately which may require additional host reboots. The vendor addon feature in vLCM, as shown in the image above, provides the capability to include component firmware/drivers into the cluster image for a consolidated update cycle. Using vLCM APIs, VxRail has incorporated the vendor addon feature into its vLCM implementation in VxRail Manager.
By introducing vLCM compatibility into VxRail LCM, users can benefit from these cool capabilities. With VxRail 7.0.240, the use of vLCM is disabled by default. Users can choose to enable vLCM immediately or enable it later. Developing vLCM compatibility is also a strategic decision to put VxRail in a position to enhance more vLCM capabilities as they come.
Conclusion
VxRail 7.0.240 is a monumental software release that expands the breadth of the VxRail portfolio’s reach in addressing workload types with VxRail dynamic nodes and its depth by enhancing is differentiated LCM experience by providing more ways to ensure cluster integrity and to improve cluster maintenance times. Though the summer is drawing to a close, VxRail is providing you the boost to stay dynamic and finish 2021 strong. Keep an eye out for more content about the latest VxRail release.
For more information about VxRail dynamic nodes, you can check out the VxRail launch page: https://www.delltechnologies.com/en-us/events/vxrail-launch.htm.
If you want to learn more about how VxRail LCM differentiates itself from other HCI vendors using VMware vLCM, you can read these previously posted blogs:
Exploring the customer experience with lifecycle management for vSAN ReadyNodes and VxRail clusters
How does vSphere LCM compare with VxRail LCM?
Author Information
Daniel Chiu, Senior Technical Marketing Manager at Dell Technologies



