

Computing on the Edge: NEBS Criteria Levels
Tue, 15 Nov 2022 14:43:44 -0000
|Read Time: 0 minutes
In our previous blogs, we’ve explored the type of tests involved to successfully pass the criteria of GR-63-CORE, Physical Protections, GR-1089-CORE, Electromagnetic Compatibility, and Electrical Safety. The goal of successfully completing these tests is to create Carrier Grade, NEBS compliant equipment. However, outside of highlighting the set of documents that compose NEBS, nothing is mentioned of the NEBS levels and the requirements to achieve each level. NEBS levels are defined in Special Report, SR-3580.
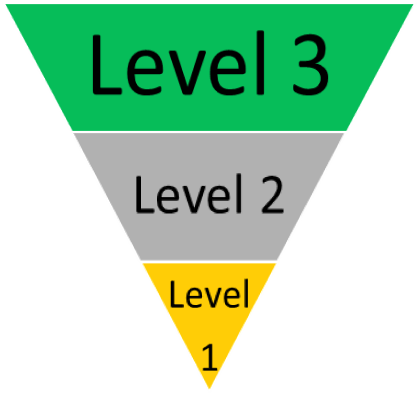 Figure 1. NEBS Certification LevelsNEBS Level 3 compliance is expected from most Telecom environments, outside of a traditional data center. So, what NEBS level do equipment manufacturers aim to achieve?
Figure 1. NEBS Certification LevelsNEBS Level 3 compliance is expected from most Telecom environments, outside of a traditional data center. So, what NEBS level do equipment manufacturers aim to achieve?
At first, I created Figure 1 as a pyramid, not inverted, with Level 1 as the base and Level 3 as the peak. However, I reorganized the graphic because Level 1 isn’t really a foundation, it is a minimum acceptable level. Let’s dive into what is required to achieve each NEBS certification level.
NEBS Level 1
NEBS Level 1 is the lowest level of NEBS certification. It provides the minimum level of environmental hardening and stresses safety criteria to minimize hazards for installation and maintenance administrators.
This level is the minimum acceptable level of NEBS environmental compatibility required to preclude hazards and degradation of the network facility and hazards to personnel.
This level includes the following tests:
- Fire resistance
- Radiated radiofrequency (RF)
- Electrical safety
- Bonding or grounding
Level 1 criteria does not assess Temperature/Humidity, Seismic, ESD or Corrosion.
Operability, enhanced resilience, and environmental tolerances are assessed in Levels 2 and 3.
NEBS Level 2
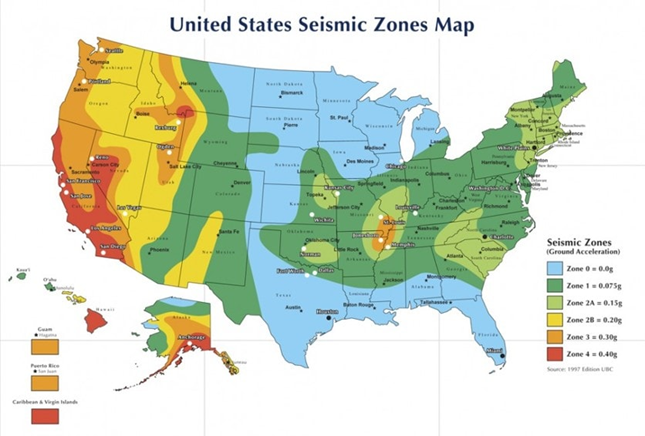
Figure 2. Map of Seismic Potential in the US
NEBS Level 2 assesses some environmental criteria, but the target deployment is in a “normal” environment, such as data center installations where temperatures and humidity are well controlled. These environments typically experience limited impacts of EMI, ESD, and EFTs, and have some protection from lightning, Surges and Power Faults. There is also some Seismic Testing performed on the EUT, but only to Zone 2. While there is no direct correlation between seismic zones and earthquake intensity, in the United States, zone 2 generally covers the Rocky Mountains, much of the West and parts Southeast and Northeast Regions.
NEBS Level 2 certification may be sufficient for some Central Office (CO) installations but is not sufficient for deployment to Far Edge or Cell Site Enclosures which can be exposed to environmental and electromagnetic extremes, or in regions covered by seismic zones 3 or 4.
NEBS Level 3
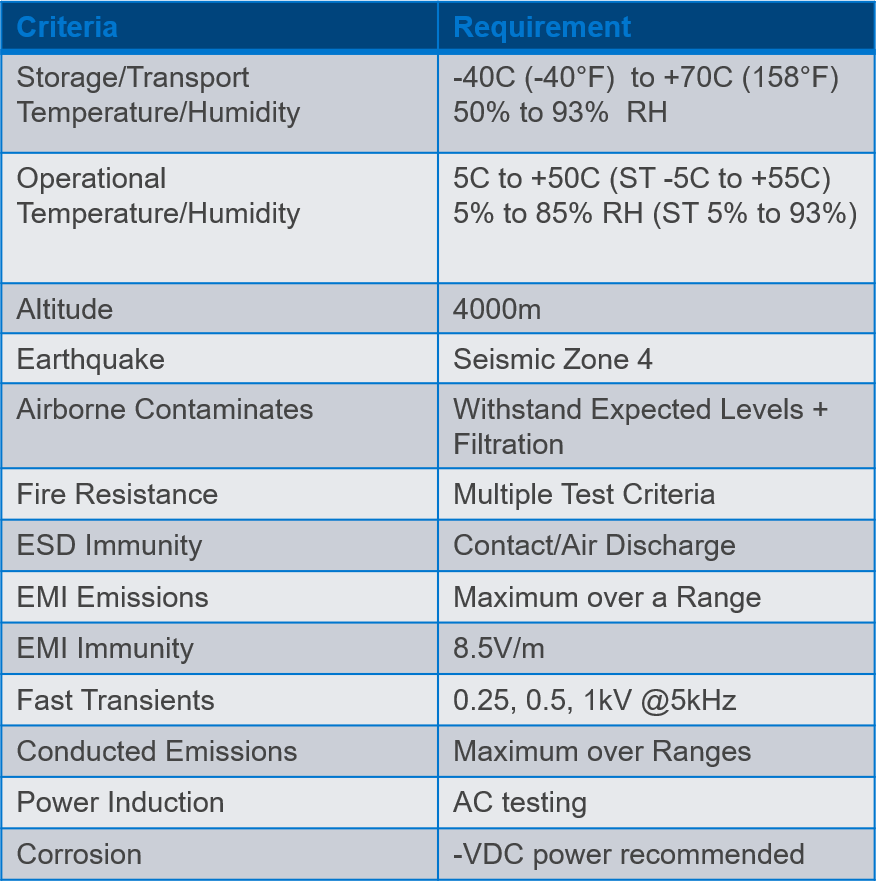 Figure 3. Level 3 criteria
Figure 3. Level 3 criteria
NEBS Level 3 certification is the highest level of NEBS Certification and is the level that is expected by most North American telecom and network providers when specificizing equipment requirements for installation into controlled environments.
Level 3 is required to provide maximum assurance of equipment operability within the network facility environment.
Level 3 criteria are also suited for equipment applications that demand minimal service interruptions over the equipment’s life.
Full NEBS Level 3 certification can take from three to six months to complete. This includes prepping and delivering the hardware to the lab, test scheduling, performance, analysis of test results, and the production of the final report. If a failure occurs, systems can be redesigned for retesting.
Conclusion
While environmental, electrical, electromagnetic, and safety specifications described in NEBS Level 3 certification, it is the minimum required for deployment into a controlled telecom network environment; these specifications are only the beginning for outdoor deployments. The next blog in this series will explore more of these specifications such as GR-3108-CORE and general requirements for Network Equipment in Outside Plant (OSP). Stay tuned.
Related Blog Posts
Computing on the Edge: Other Design Considerations for the Edge – Part 1
Fri, 13 Jan 2023 19:46:50 -0000
|Read Time: 0 minutes
In past blogs, the requirements for NEBS Level 3 certifications were addressed, with even higher demands depending on the Outside Plant (OSP) installation requirements. Now, additional design considerations need to be considered, to create a hardware solution that is not only going to survive the environment at the edge, but provides a platform that can be effectively deployed to the edge.
Ruggedized Chassis Design
The first design consideration that we’ll cover for an Edge Server is the Ruggedized Chassis. This is certainly a chassis that can stand up to the demands of Seismic Zone 4 testing and can also withstand impacts, drops, and vibration, right?
Not necessarily.
While earthquakes are violent, demanding, but relatively short-duration events, the shock and vibration profile can differ significantly when the server is taken out from under the Cell Tower. We are talking beyond the base of the tower, and to edge environments that might be encountered in Private Wireless or Multi-Access Edge Compute (MEC) deployments. Some vibration and shock impacts are tested in GR-63-Core, under test criteria for Transportation and Packaging, but ruggedized designs Figure 1. Portable Edge Compute Platforms need to go beyond this level of testing.
Figure 1. Portable Edge Compute Platforms need to go beyond this level of testing.
For example, the need for ruggedized servers in mining or military environments, where setting up compute can be more temporary in nature and often includes the use of portable cases, such as Pelican Cases. These cases are subject to environmental stresses and can require ruggedized rails and upgraded mounting brackets on the chassis for those rails. For longer-lasting deployments, enclosures can be less than ideal and require all the requirements of a GR-3108 Class 2 device and perhaps some additional considerations.
Dell Technologies also tests our Ruggedized (XR-series) Servers to MIL-STD-810 and Marine testing specifications. In general, MIL-STD-810 temperature requirements are aligned with GR-63-CORE on the high side but test operationally down to -57C (-70F) on the low side. This reflects some extreme parts of the world where the military is expected to operate. But MIL-STD-810 also covers land, sea, and air deployments. This means that non-operational (shipping) criteria is much more in-depth, as are acceleration, shock, and vibration. Criteria includes scenarios, such as crash survivability, where the server can be exposed to up to 40Gs of acceleration. Of course, this tests not only the server, but the enclosure and mounting rails used in testing.
So why have I detoured onto MIL-STD and Marine testing? For one, it’s interesting in the extreme “dynamic” testing requirements that are not seen in NEBS. Secondly, creating a server that is survivable in MIL-STD and Marine environments is only complementary to NEBS and creates an even more durable product that has applications beyond the Cellular Network.
Server Form Factor
 Figure 2. Typical Short Depth Cell Site EnclosureAnother key factor in chassis design for the edge is the form factor. This involves understanding the physical deployment scenarios and legacy environments, leading to a server form factor that can be installed in existing enclosures without the need for major infrastructure improvements. For servers, 19 inch rackmount or 2 post mounting is common, with 1U or 2U heights. But the key driver in the chassis design for compatibility with legacy telecom environments is short depth.
Figure 2. Typical Short Depth Cell Site EnclosureAnother key factor in chassis design for the edge is the form factor. This involves understanding the physical deployment scenarios and legacy environments, leading to a server form factor that can be installed in existing enclosures without the need for major infrastructure improvements. For servers, 19 inch rackmount or 2 post mounting is common, with 1U or 2U heights. But the key driver in the chassis design for compatibility with legacy telecom environments is short depth.
Server depth is not something covered by NEBS, but supplemental documentation created by the Telecoms, and typically reflected in RFPs, define the depth required for installation into Legacy Environments. For instance, AT&T’s Network Equipment Power, Grounding, Environmental, and Physical Design Requirements document states that “newer technology” deployed to a 2 post rack, which certainly applies to deployments like vRAN and MEC, “shall not” exceed 24 inches (609mm) in depth. This disqualifies most traditional rackmount servers.
The key is deployment flexibility. Edge Compute should be able to be mounted anywhere and adapt to the constraints of the deployment environment. For instance, in a space-constrained location, front maintenance is a needed design requirement. Often these servers will be installed close to a wall or mounted in a cabinet with no rear access. In addition, supporting reversible airflow can allow the server to adapt to the cooling infrastructure (if any) already installed.
Conclusion
While NEBS requirements focus on Environmental and Electrical Testing, ultimately the design needs to consider the target deployment environment and meet the installation requirements of the targeted edge locations.

Edge AI Integration in Retail: Revolutionizing Operational Efficiency
Mon, 12 Feb 2024 11:43:11 -0000
|Read Time: 0 minutes
Edge AI plays a significant role in the digital transformation of retail warehouses and stores, offering benefits in terms of efficiency, responsiveness, and enhanced customer experience in the following areas:
- Real-time analytics—Edge AI enables real-time analytics for monitoring and optimizing warehouse management systems (WMS). This includes tracking inventory levels, predicting demand, and identifying potential issues in the supply chain. In the store, real-time analytics can be applied to monitor customer behavior, track product popularity, and adjust pricing or promotions dynamically based on the current context using AI algorithms that analyze this data and provide personalized recommendations.
- Inventory management—Edge AI can improve inventory management by implementing real-time tracking systems. This helps in reducing stockouts, preventing overstock situations, and improving the overall supply chain efficiency. On the store shelves, edge devices equipped with AI can monitor product levels, automate reordering processes, and provide insights into shelf stocking and arrangement.
- Optimized supply chain—Edge AI assists in optimizing the supply chain by analyzing data at the source. This includes predicting delivery times, identifying inefficiencies, and dynamically adjusting logistics routes for both warehouses and stores.
- Autonomous systems—Edge AI facilitates the deployment of autonomous systems, such as autonomous robots, conveyor belts, robotic arms, automated guided vehicles (AGVs), and collaborative robotics (cobots). Autonomous systems in the store can include checkout processes, inventory monitoring, and even in-store assistance.
- Predictive maintenance—In both warehouses and stores, Edge AI can enable predictive maintenance of equipment. By analyzing data from sensors on machinery, it can predict when equipment is likely to fail, reducing downtime and maintenance costs.
- Offline capabilities—Edge AI systems can operate offline, ensuring that critical functions can continue even when there is a loss of internet connectivity. This is especially important in retail environments where uninterrupted operations are crucial.
The Operational Complexity Behind the Edge-AI Transformation
The scale and complexity of Edge-AI transformation in retail are influenced by factors such as the number of edge devices, data volume, AI model complexity, real-time processing requirements, integration challenges, security considerations, scalability, and maintenance needs.
The Scalability and Maintenance Challenge
A mid-size retail organization is composed of tens of warehouses and hundreds of stores spread across different locations. In addition to that, it needs to support dozens of external suppliers that also need to become an integral part of the supply chain system. To enable Edge-AI retail, it will need to introduce many new sensors, devices, and systems that will enable it to automate a large part of its daily operation. This will result in hundreds of thousands of devices across the stores and warehouses.
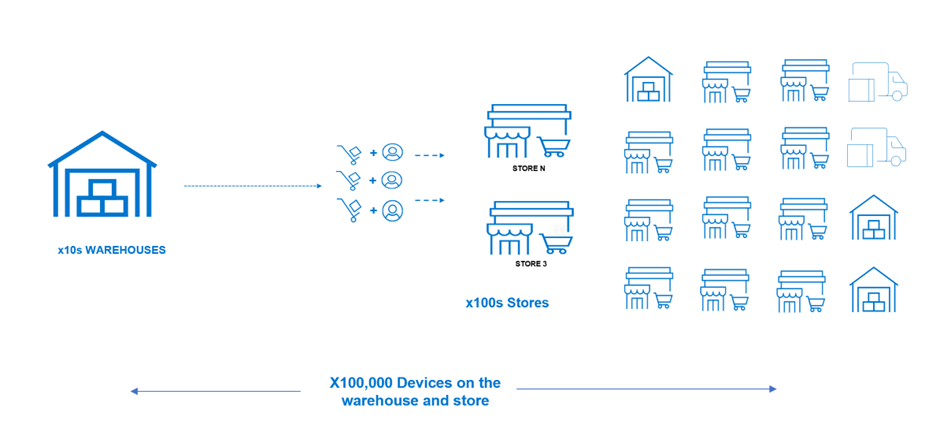
Figure 1. The Edge-AI device scale challenge
The scale of the transformation depends on the number of edge devices deployed in retail environments. These devices could include smart cameras, sensors, RFID readers, and other internet of things (IoT) devices. The ability to scale the Edge-Ai solution as the retail operation grows is an essential factor. Scalability considerations involve not only the number of devices but also the adaptability of the overall architecture to accommodate increased data volume and computational requirements.
Breaking Silos Through Cloud Native and Cloud Transformation
Each device comes with its proprietary stack, making the overall management and maintenance of such a diverse and highly fragmented environment extremely challenging. To address that, Edge-Ai transformation also includes the transformation to a more common cloud-native and cloud-based infrastructure. This level of modernization is quite massive and costly and cannot happen in one go.
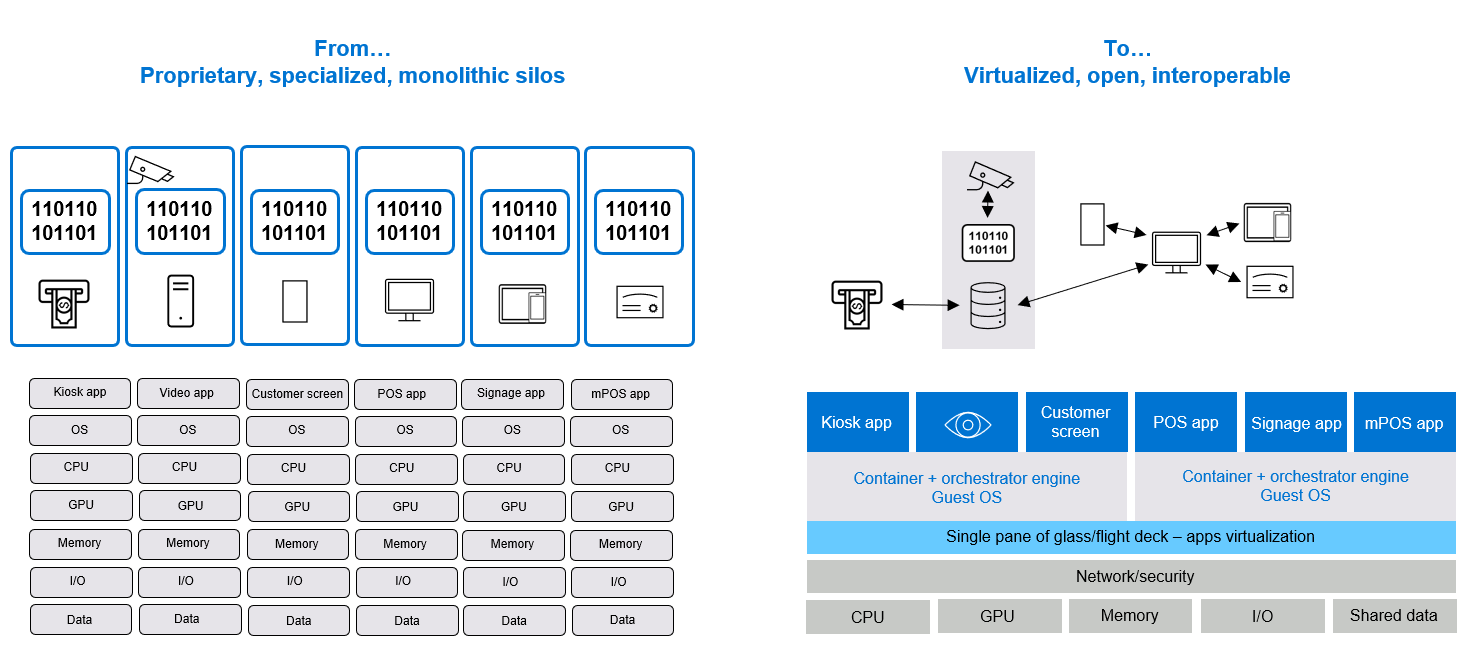
Figure 2. Cloud native and cloud transformation break the device management silos challenges
This brings the need to handle the integration with existing systems (brownfield) to enable smoother transformation. This often involves integration with existing retail systems, such as point-of-sale systems, inventory management software, and customer relationship management tools.
NativeEdge and Centerity Solution to Simplify Retail Edge-AI Transformation
Dell NativeEdge serves as a generic platform for deploying and managing edge devices and applications at the edge of the network. One notable addition in the latest version of NativeEdge is the ability to deliver an end-to-end solution on top of the platform that includes PTC, Litmus, Telit, Centerity, and so on. This capability allows users to get a consistent and simple management from Bare-Metal provisioning to a fully automated full-blown solution.
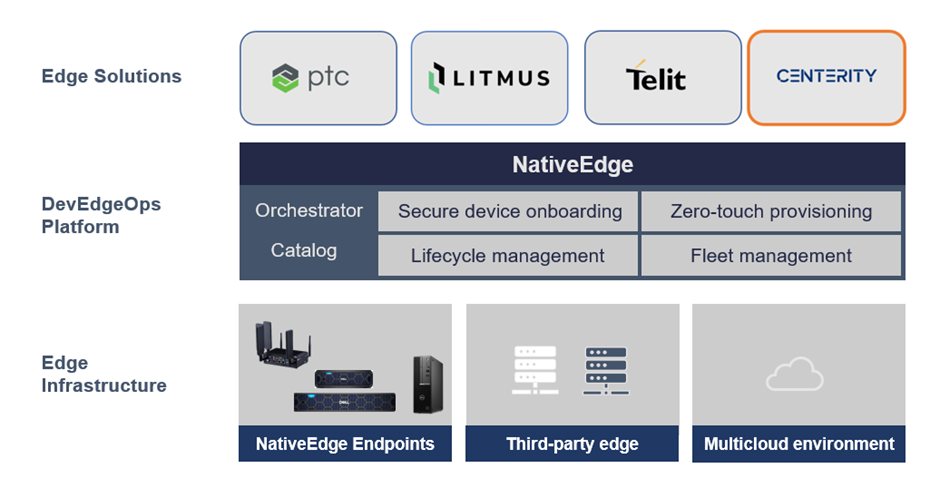
Figure 3. Using NativeEdge and Centerity as part of the open edge solution stack
In this blog, we demonstrate the benefits behind the integration of NativeEdge and Centerity that simplify the retail Edge-AI transformation challenges.
Introduction to Centerity
Centerity CSM² is a purpose-built monitoring, auto-remediation, and asset management platform for enterprise retailers that provides proactive wall-to-wall observability of the in-store technology stack. The key part in the Centrity architecture is the Centerity Manager is responsible for collecting all the data from the edge devices into a common dashboard.
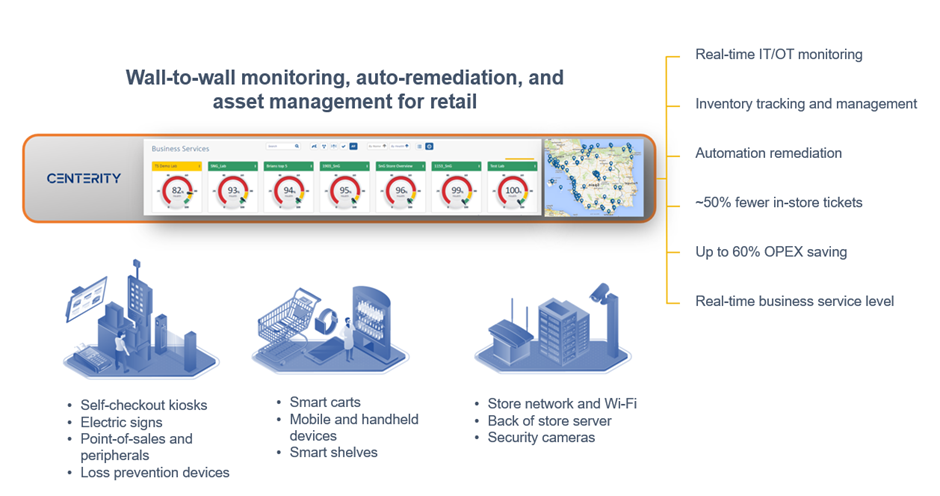
Figure 4. Centerity retail management and monitoring
Using NativeEdge and Centerity to Automate the Entire Retail Operation
The following are the architecture choices made to address the Edge-AI transformation challenges with Dell NativeEdge as the edge platform and Centerity as the asset management and monitoring for both the retail warehouse and store. In this case, we have two sites, one representing a warehouse where we connect to the customer’s existing environment running on VMware infrastructure, and a retail store running in a different location.
Note: The Centrify Proxy (customer site-1 in the following figure) is used to aggregate multiple remote devices through a single network connection.
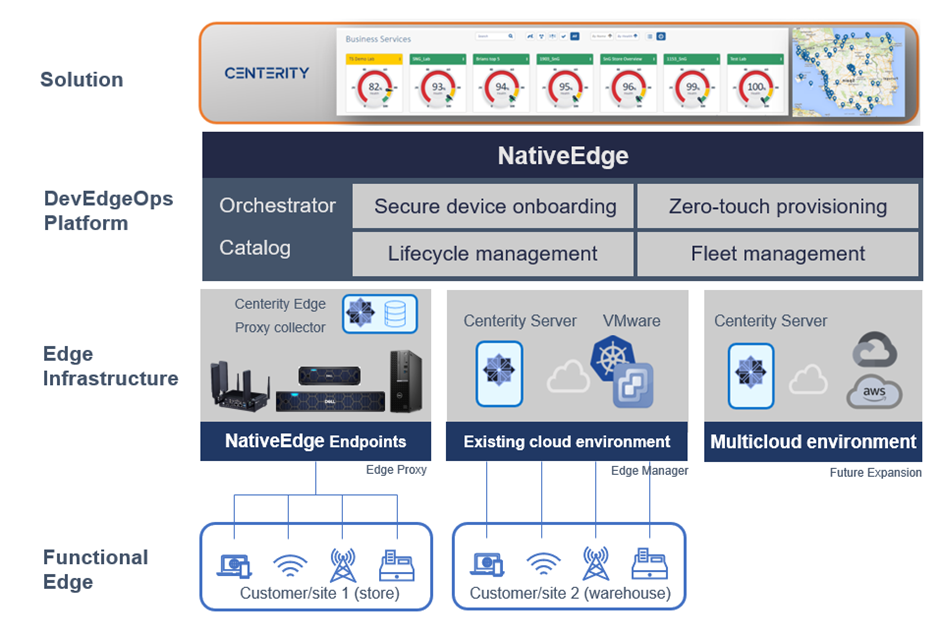
Figure 5. Using NativeEdge and Centerity to fully automate and manage and retail warehouse and store
Since the store is often limited by infrastructure capacity, we will use a gateway to aggregate the data from all the devices. For this purpose, we will use a NativeEdge Endpoint as a gateway and install the Centerity monitoring agent on it. The monitoring agent will act as a proxy that on one hand connects to the individual devices in the store and, on the other hand, sends this information back to the Centerity Manager to aggregate all this information into one control plane. In this case, the warehouse runs on a private cloud based on VMware and represents a central data center. Since we have more capacity on this environment, we will collect the data directly from the device to the manager without the need for a proxy agent. The architecture is also set to enable future expansion to public clouds such as AWS and GCP.
Step 1: Use NativeEdge for zero-touch secure on-boarding of the edge infrastructure
Secure device onboarding—In this step, we will onboard three different edge compute classes (PowerEdge, OptiPlex, and Gateway) to represent a warehouse facility with diverse set of devices. NativeEdge will treat each of these devices as a separate ECE instance and, thus, provide a consistent management layer to all the devices, regardless of their compute class.
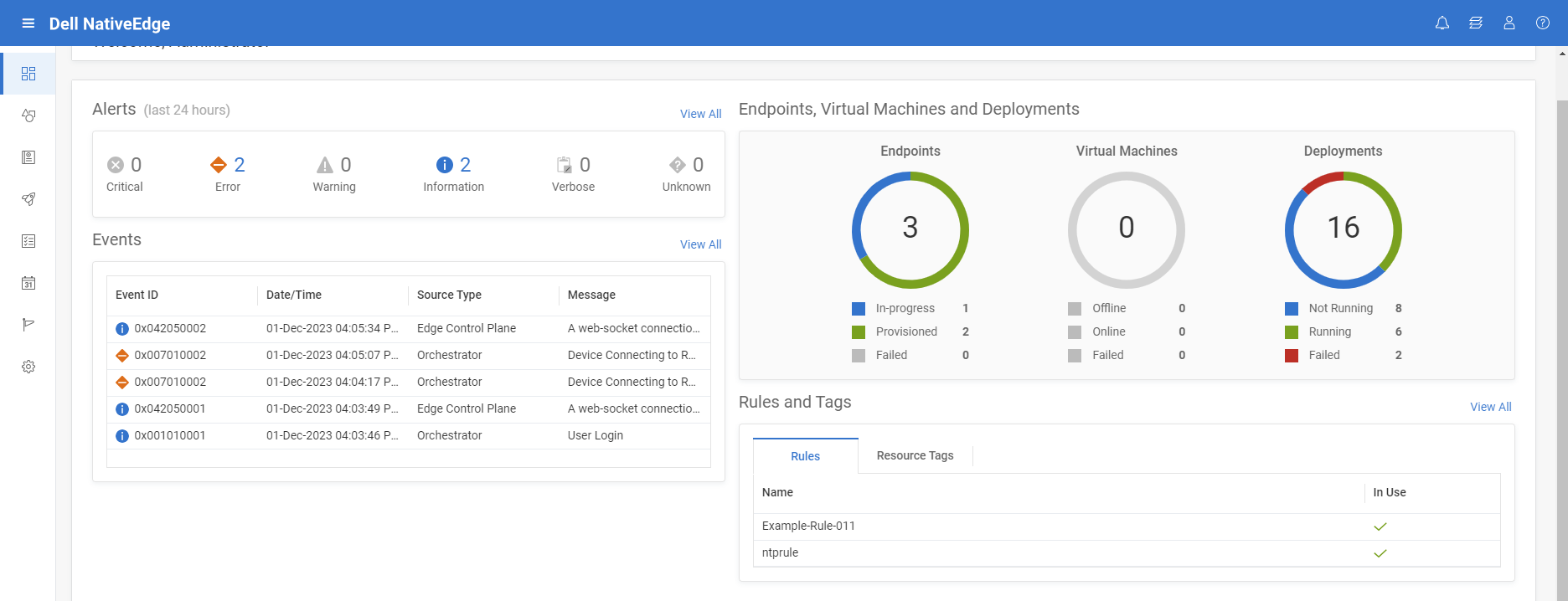
Figure 6. Zero-touch provisioning of edge infrastructure from BareMetal to cloud
Step 2: Deploy Centerity solution on top of NativeEdge infrastructure
This phase is broken down into two parts; The first is provisioning the Centerity Manager which is the main component and then provision the edge proxy on the target store and warehouse.
Step 2.1: Deploy and manage the Centerity Manager on VMware (Site 2)
To do that:
- Choose the on-prem Centerity server catalog item from the NativeEdge solution tab. Full Centerity server installation starts on VMware private cloud (external infra, not NativeEdge Endpoint).
- Use the deployment output to fetch the newly created Centerity server endpoint, credentials, and so on.
Step 2.2: Deploy and manage the Centerity Edge proxy (agent) on NativeEdge Endpoints
To install Centerity Edge proxy collector on each warehouse:
- Choose the Centerity Collector or Edge proxy catalog item.
- Select the target environment and deploy the proxy on all the selected sites. The installation happens in parallel installation on all sites.
- Fill the relevant deployment inputs and install deployment.
- Native Edge starting the fulfillment phase with all operations.
- Install and configure Centos VM per each warehouse, install edge proxy agent/ collector, and connect it to server.
- Execute day-2 operations, such as updating one of the warehouses using security update check, custom workflow.
The following blueprint automates the deployment of the Centerity agent on a NativeEdge Endpoint. It launches a virtual machine (VM) on the remote device which is configured to connect to the Centerity Manager. It also optimizes the VM to support AI workload by enabling GPU passthrough.
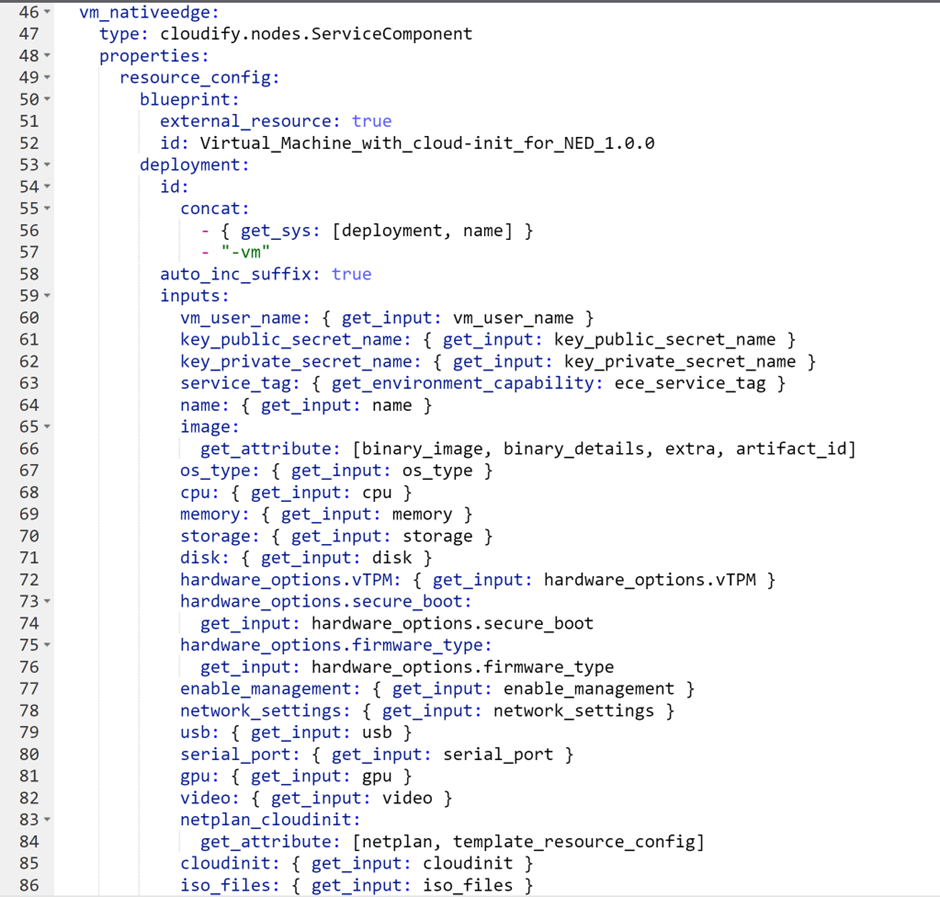
Figure 7. Create an AI optimized VM on the target device
NativeEdge can execute the above blueprint simultaneously on all the devices. The following figure shows the result of executing this blueprint on three devices.
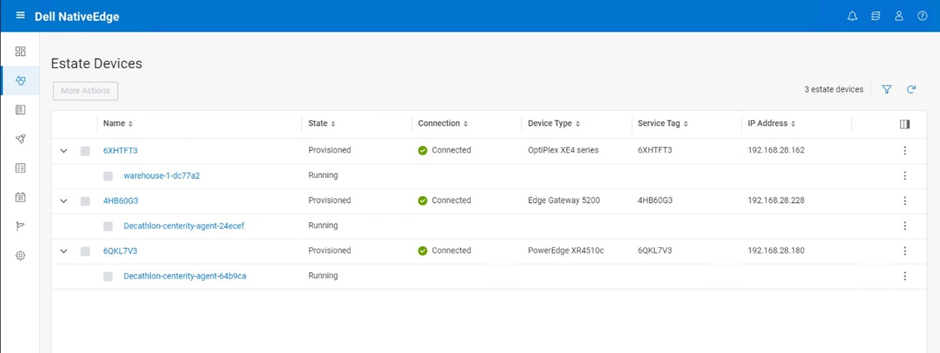
Figure 8. Deploy the Edge Proxy on all the stores in one bulk
Step 3: Connect the retail and logistic devices to Centerity
In this step, we will configure and set up the devices and connect them to the Centerity monitoring service. Note that this step is done directly on the centerity management console and not through NativeEdge console.
In this case, we chose the following endpoints within the logistic center or warehouse.
- Tablet type – Dell Windows11
- Mobile terminal type – Zebra TC52
- API based devices – SES (Digital signage)
- Printer – Bixolon (Log based)
- Agentless based devices – Security camera
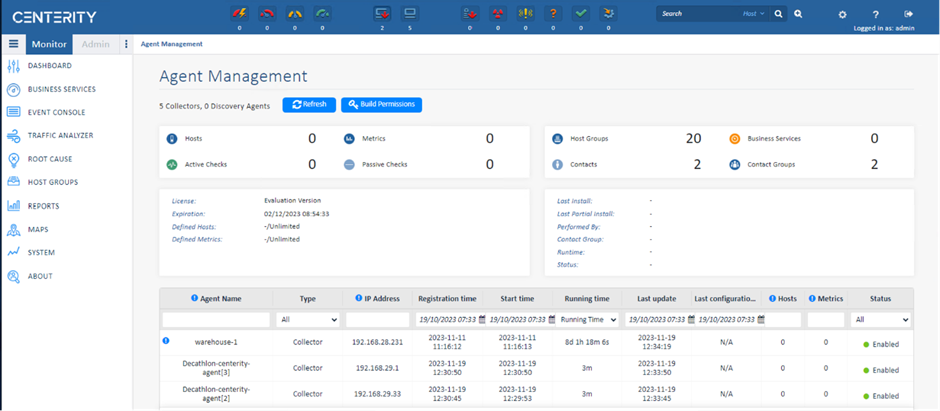
Figure 9. Centerity Management connected to the edge device managed by NativeEdge
Step 4: Managing and monitoring the retail warehouse and store
In this step, we will manage the retail warehouse and store through the monitoring of the devices that we connected to the system in the previous step. This will include the following set of operations:
- Device monitoring
- Inventory tracking (if applicable)
- Failures alerts
- Auto remediation (if applicable)
- Operational and business SLA dashboards
- Reports
- Generating events for proactive operational support
- Updating and keeping up the system software for compliance
- Breaking or fixing the workflow

Figure 10. Monitoring and managing retail devices
Conclusion
Dell NativeEdge provides a fully-automated secure device onboarding from Bare Metal to the cloud. As a DevEdgeOps platform, NativeEdge also provides the ability to validate and continuously manage the provisioning and configuration of those devices in a secure way. This minimizes the risk of failure and security breaches due to misconfiguration or human errorThose potential vulnerabilities can be detected earlier in the pre-deployment development process. The introduction of NativeEdge Orchestrator enables customers to have a consistent and simple management of built-in solutions across their entire fleet of new and existing devices. The separation between the device management and solution is key to enabling consistent operational management between different solution vendors as well as cloud infrastructure. In addition to that, the ability to integrate with the retail existing infrastructure (VMware in this specific example) as well as cloud-native infrastructure simultaneously ensures smoother transformation to a modern Edge-AI-enabled infrastructure.
The specific integration between NativeEdge and Centerity in this specific use case enables customers to deliver a full-blown retail management which integrates with both their legacy and new AI enabled devices. According to recent studies, this level of end-to-end monitoring and automation can reduce the maintenance overhead and potential downtime by 57 percent.
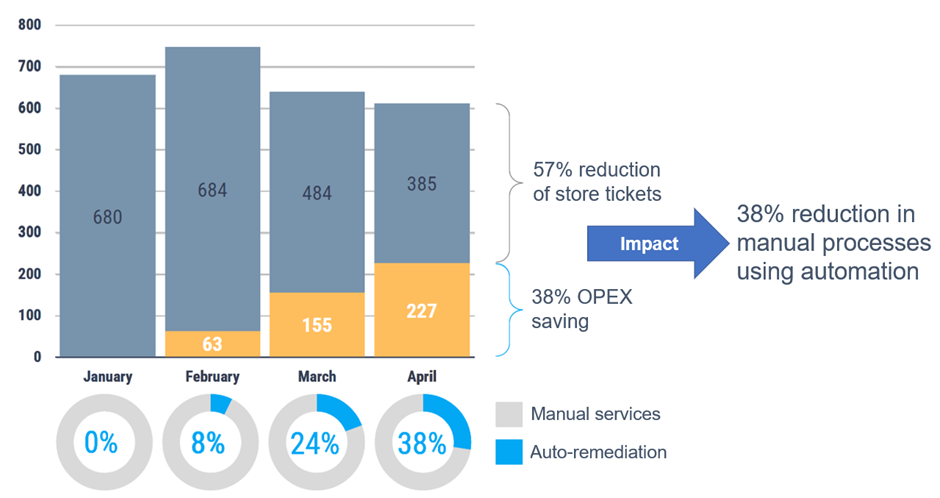
Figure 11. Moving to a fully automated and monitored retail warehouse and store brings a significant TCO saving
It is also worth noting that the open solution framework provided by NativeEdge allows partners such as Centerity to use Dell NativeEdge as a generic edge infrastructure framework, addressing fundamental aspects of device fleet management. Vendors can then focus on delivering the unique value of their solution, be it predictive maintenance or real-time monitoring, as demonstrated by the Centerity use case in this blog.



