Third-party Analysis

Securing the Digital Frontier: Inside Dell and AMD’s Zero Trust Approach
Fri, 23 Feb 2024 17:01:00 -0000
|Read Time: 0 minutes
Introduction
The devices that connect us make incredible things possible, but these connections also provide additional points of vulnerability that malicious actors can exploit. In fact, some estimates predict that cyber attacks will cost organizations as much as $10.5 trillion USD by 2025.1 And according to one estimate, recovering from the damage of a cyber attack takes about 277 days.2
While newer tech such as artificial intelligence (AI) offers improvements in productivity and business operations for many organizations, it also leaves data vulnerable to more sophisticated cyber attacks. With each advancement in technology, tech industry leaders must shift strategies to effectively counter cyber criminals as they find new ways to attain and exploit data. To thwart these threats and keep data safe, every data center component—from servers and storage to networks, software, and firmware–needs built-in protection. Protection starts with supply chain tampering mitigations on the manufacturing floor and continues through the transportation process and customer use. And attacks no longer stop at the data center walls. Organizations with a presence in the cloud face additional challenges in keeping data secure.
Together, Dell and AMD provide a purpose-built cyber resilient architecture that helps organizations adopt a Zero Trust strategy, embracing the idea that system components are vulnerable at each link in the chain and offering protection at every point. A Zero Trust strategy uses strong, identity-based policies for every IT asset along with “least privilege” principles for access. Dell Cyber Resilient Architecture includes in-depth features centered around boot integrity and data protection as well as security features in Integrated Dell Remote Access Controller (iDRAC). Dell PowerEdge servers are anchored with a silicon-based Root of Trust (RoT) that establishes a chain of trust for cryptographic verification of hardware and software components on the server. AMD Infinity Guard provides an additional layer of security that decreases the potential of attack during software boot and execution. AMD Infinity Guard encompasses several additional security features, including Platform Secure Boot and Platform Secure Processor, that ensure PowerEdge servers are protected at each stage in their lifecycle.
Dell Cyber Resilient Architecture
Dell Cyber Resilient Architecture utilizes PowerEdge security features that work in concert to provide both resiliency and enable a zero trust strategy. Security features must protect against potential threats, detect suspicious activity, and recover quickly in case of a breach. At the same time, they must also maintain a “verify before trust” posture for a zero trust approach of least privilege, where users and devices are given access only to what they need to perform their tasks. By working together, these PowerEdge security controls provide a comprehensive security solution that ensures resiliency while enforcing a zero trust posture. For more details on the full Dell Cyber Resilient Architecture features and services, see the whitepaper.
Ensuring Boot Integrity
The pre-boot environment it often overlooked and, if safeguards aren’t taken, could be open to attack. If a malicious actor compromises the BIOS, firmware, or a driver during boot, they could potentially obtain access to the entire system. Without the proper controls in place, they could successfully infiltrate the system at any point and reach their desired target: your data.
To mitigate vulnerabilities, the server vendor must protect the BIOS, but also verify and validate specific server components and firmware such as memory and processors. Server hardware manufacturers must ensure that their components integrate fully with the server architecture for security and validation checks to work seamlessly. Every Dell PowerEdge server offers multiple layers of security to protect the boot cycle: a silicon-based RoT, UEFI Secure Boot, and iDRAC security features, including Firmware Rollback and Rapid Operating System Recovery.
On top of these Dell PowerEdge server-based security layers, AMD processors feature Platform Secure Boot (PSB) and Platform Security Processor (PSP) to protect data in use. Combined, Dell and AMD cover every aspect of the boot cycle to ensure a secure foundation for your data and workloads.
Dell iDRAC and Root of Trust
The RoT concept assumes that if a system verifies a foundation or baseline as safe, then all subsequent validations and security checks are anchored in a continuous chain of trust. Imagine a house: If the foundation is unstable and beginning to crumble, the integrity of the wall supports matters little. Similarly, if your server’s BIOS is compromised, protecting the server OS may be in vain.
The PowerEdge server chain of trust provides a seamless cryptographic verification across all server components from foundation to data. This ensures that the components of the system software stack (hypervisor, OS, applications) are aware that they can trust the underlying server when the server is operational. This layer establishes the foundation of a chain of trust within a server and creates a trusted and secure server platform. Dell servers use a unique silicon-based RoT burned into each server for cryptographic verification that ensures secure booting on every cold boot or A/C cycle. Starting with version 4.10.10.10, iDRAC provides an RoT mechanism to verify the BIOS image at boot and will not allow the server to boot until it verifies the BIOS image. For PowerEdge servers with AMD processors, integrated Dell Remote Access Controller (iDRAC) leverages AMD PSB technology to verify the BIOS code before the OS loads. AMD PSB scrutinizes the BIOS integrity, interfacing with the primary BIOS ROM and AMD fusion controller hub (FCH) for thorough RoT processing. This meticulous validation extends up to the OS bootloader, guaranteeing a continuous chain of trust.
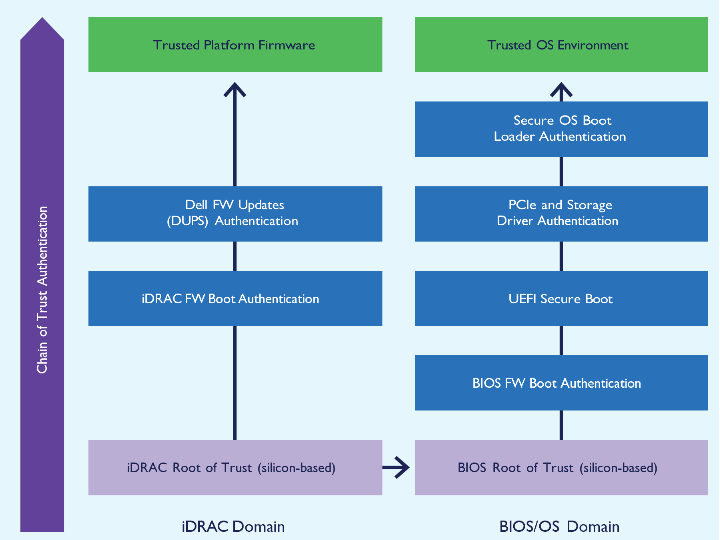 Figure 1: Silicon-based Root of Trust Domains in PowerEdge Servers with iDRAC9.
Figure 1: Silicon-based Root of Trust Domains in PowerEdge Servers with iDRAC9.
Should BIOS validation fail, iDRAC immediately shuts down the server and notifies the user, preventing the booting of unauthorized firmware. iDRAC also includes a backup and recovery system for BIOS and iDRAC firmware, which reinforces server reliability and safeguards server operations against potential firmware corruption. To provide additional protection, iDRAC also offers a live BIOS scan that users can run on demand or schedule to run regularly. This scan requires the iDRAC Datacenter license and allows users to catch potential issues before they reboot, allowing proactive mitigation.3
UEFI Secure Boot
Dell PowerEdge servers use the industry-standard UEFI Secure Boot to validate operating system-specific bootloaders, ensuring the integrity of the OS kernel and other critical components. UEFI acts as a shield from malware and ransomware in pre-boot environments. To ensure interoperability, both server and component manufacturers need to collaborate to ensure that the UEFI-enabled BIOS recognizes driver and firmware signatures for components. By validating cryptographic signatures of UEFI drivers and other pre-OS code, UEFI Secure Boot endeavors to ensure that any code loaded during boot is free of malicious content.
To heighten security customization, administrators can configure custom OS bootloader signing certificates for UEFI Secure Boot. (To learn more about UEFI Secure Boot Customization options, visit https://infohub.delltechnologies.com/section- assets/direct-from-development-uefi-boot-enhanced-security-to-combat-threats.) This restricts execution to trusted secure OS bootloaders, which uphold the secure boot chain by authenticating the OS kernel and filesystem. This feature provides additional flexibility, particularly for Linux administrators who prefer to sign their own OS bootloaders rather than depend on third-party default UEFI Certificate Authorities. Administrators can upload custom certificates through the iDRAC API, enhancing authentication of their specific OS bootloaders. Uniquely, Dell PowerEdge servers support complete customization of Secure Boot, including the option to remove all standard certificates from Microsoft, VMware, or UEFI CA.4
CPLD Validation
Every Dell PowerEdge server validates the Complex Programmable Logic Device (CPLD) on every A/C boot. CPLD, a versatile programmable logic device,5 comprises multiple simple PLDs connected by a programmable switching matrix. Its firmware, typically stored in EEPROM, flash memory, or SRAM, enables modifications to system board functions beyond BIOS capabilities, including the implementation of specific logic for system board device interactions. CPLD Validation ensures that system board modifications will not harm your servers or your data.
iDRAC Hardware Security
Extending the chain of trust to additional hardware components, iDRAC uses the Security Protocol and Data Model (SPDM), which standardizes how servers gather information about their components. Each component’s identity, firmware, and configuration information is encrypted. iDRAC hardware security uses authenticated key exchanges to secure lines of communication between components and iDRAC. With SPDM, iDRAC can authenticate the validity of components such as PowerEdge RAID Controllers (PERC)12 and network interface cards (NICs), which not only enhances server security by authenticating components’ Device Identity certificates but also alerts users to any authentication failures.
AMD Platform Secure Boot
AMD processors feature AMD Platform Secure Boot (PSB) to help counteract another growing concern in today’s digital landscape: firmware-level threats. PSB leverages the AMD silicon RoT and verifies the boot process from the BIOS code to the OS Bootloader through UEFI secure boot.6 Dell uses AMD PSB-enabled motherboards to permit only their cryptographically signed BIOS code to run. Additionally, Dell binds each AMD processor to a specific motherboard with one- time-programmable fuses that tie the processor to the Dell firmware code signing keys.7 To protect against attacks aimed at embedding malware into firmware, PSB boots authorize only firmware authenticated by AMD Secure Processor.8
By cryptographically verifying the software stack, AMD Platform Secure Boot adds a substantial layer of defense against unauthorized intrusion across various platforms, particularly in virtualized environments or in the cloud.
AMD Platform Secure Processor
Together with PSB, AMD Platform Secure Processor (PSP) fortifies the Dell PowerEdge server boot process. When a CPU first powers on in the Dell factory, the AMD Platform Secure Processor embeds a unique Dell ID permanently into the CPU. This ID effectively ties the CPU to the PowerEdge server, creating a secure bond.9
This integration means that PSP will prevent a PowerEdge server from booting if it detects a CPU from a different server. However, CPU portability is still possible in the event of a hardware failure. The AMD processor is locked to the vendor’s signing key rather than the motherboard, offering a balance between security and component mobility.10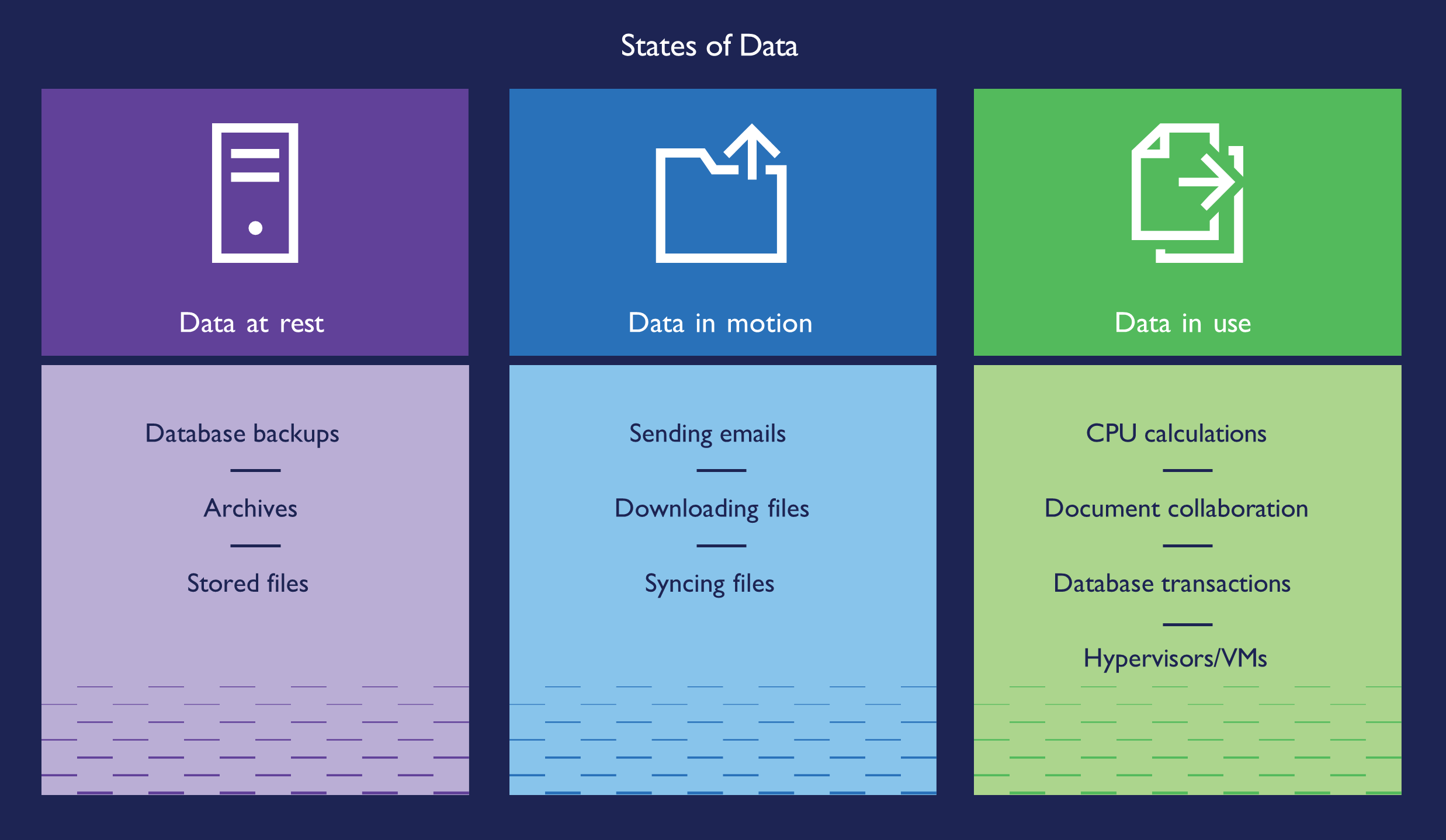 Figure 2: States of Data
Figure 2: States of Data
Protecting Your Data
While attackers gain access to systems, the end goal is always the same: to find your data and steal, manipulate, sell, or destroy it. The physical server isn’t the only point of vulnerability. Bad actors can attack networking, IT policies can contain errors, end-users can have weak passwords, and IT teams can set access permissions too broadly. Attackers may target users with phishing emails to distribute malware.
Dell enables customers to employ a Zero Trust approach that relies on multiple security layers to help protect against all these types of vulnerabilities. To guard against theft or compromise, you must secure data at rest, data in process, and data in flight, through to data decommissioning.11 With features such as at-rest encryption, robust encryption key management, and automated certificate renewal, Dell PowerEdge servers work to block, deter, and mitigate malicious attacks after first boot. Dell PowerEdge servers with AMD processors offer additional features to bolster security, including AMD Secure Memory Encryption (SME) and Secure Encrypted Virtualization (SEV).
Data at Rest
To protect data at rest, Dell provides three main security features: software-based encryption, enterprise key management, and hardware drive encryption. With drives that support Instant Secure Erase (ISE), Dell customers can cryptographically erase any data on self-encrypted drives (SEDs), ISE drives, and NVM devices such as NVDIMMs. SEDs protect data from attacks in instances where a disgruntled employee or other malicious actor physically removes drives from a server. Because the encrypted drive’s locking key password ties it to the specific server and RAID controller it came from, another server cannot access the data. For further protection, iDRAC can use Dell OpenManage Secure Enterprise Key Manager with local key management (iLKM, LKM) which works in conjunction with an external third-party key manager to lock and unlock the storage controller at boot. If someone boots the server away from the key manager, iDRAC keeps the storage controller locked so that the data stored on the device remains encrypted. To find out more about other encryption key options, visit https://infohub.delltechnologies.com/section-assets/openmanage-sekm-storage-performance- infographic.
Data in Flight
With data in flight, vulnerabilities in the network and data access control could allow attackers to intercept or modify data traveling over the network. The iDRAC web connection is one possible point of vulnerability—so Dell provides several options to secure the connection with a TLS/SSL certificate, thus mitigating the chance of attack. While this certificate is self-signed by default, admins can create a custom certificate, or one signed by a trusted Certificate Authority (CA). This certificate enables encrypted, secure connections for web browsers and tools such as command-line utilities to safely interact with the server via the iDRAC connection.
iDRAC also provides several controls for users to modify strict, narrow access rules that allow SSH access to the server. For iDRAC users with a Datacenter level license, iDRAC offers Simple Certificate Enrollment Protocol (SCEP), which maintains web server certificates with automatic renewal to avoid accidental lapses in coverage. A 2020 study from third party Principled Technologies found that this automatic renewal feature keeps servers more secure while saving IT staff valuable time—especially when it comes to maintaining a fleet of server certificates.12
Data in Use
To protect data in use, Dell PowerEdge servers enable AMD confidential compute features, including AMD Secure Memory Encryption (SME) and Secure Encrypted Virtualization (SEV) to protect data as it flows through memory and processing components.
Secure Memory Encryption
AMD SME encrypts all data as it enters the memory, further securing your data. Without memory encryption, data is vulnerable to malicious software and other intrusions, especially with newer memory technology such as NVDIMMs that do not lose data when powered down. This protection extends to memory via high-performance encryption engines integrated into the memory channels, ensuring both security and speed. Because it’s completely transparent to the host OS and application layers, AMD SME accomplishes this without necessitating any changes to application software, providing a user-friendly approach to enhanced memory security.13
AMD SME in-memory data encryption marks a departure from older memory encryption methods that were tailored to specific use cases. A key advantage of AMD SME is its flexibility, allowing software to utilize it in different ways: either by encrypting all of DRAM for comprehensive protection or selectively encrypting specific regions, such as those used by guest virtual machines (VMs).14
AMD Secure Encrypted Virtualization
AMD SEV enhances encryption for memory and virtual machines by implementing a virtual machine-based Trusted Execution Environment (TEE). Integrating with AMD V architecture, AMD SEV encrypts each VM’s memory separately, protecting the VMs from each other and from the hypervisor. This approach employs cryptography to safeguard code within a VM from potentially vulnerable higher-privileged code, such as the hypervisor. The added layer of security is especially crucial in cloud environments. This method ensures enhanced protection for VMs, fortifying them against external vulnerabilities. The encryption happens right at the memory controller, where it encrypts and decrypts data without slowing processing speed—thanks to the AMD Secure Processor handling all the encryption details invisibly.15
There are still some situations when a VM’s data needs to communicate with other VMs or with the hypervisor. In these instances, AMD SEV allows the VM to choose which encryption key to apply to specific memory pages: a guest key that keeps the page private to the VM or a hypervisor key that allows the hypervisor and other VMs to decrypt the page. This flexibility allows for security and communication based on the needs of each VM.16
AMD SEV offers additional features that expand the cryptographic isolation of VMs: SEV-Encrypted State (SEV-ES) and SEV-Secure Nested Paging (SEV-SNP). SEV-ES further isolates VMs from each other and the hypervisor by encrypting CPU register content when a VM powers down, protecting it from unauthorized access via a neighbor VM or the hypervisor. SEV-SNP builds on SEV and SEV-ES, adding memory integrity protection and optional additional security features for VMs. The memory integrity enhancement makes it so that a VM can access data in memory only if it can read the last value it wrote. If another entity modified the data in the memory, the VM cannot access the data. This protects the VM from running compromised data or code.
Encryption and Encryption Keys
AMD SEV uses a unique encryption key for each VM, cryptographically isolating VMs and the hypervisor. This encryption engine secures data on write and decrypts it on read. Each VM, upon creation, receives a unique key, ensuring that any unauthorized attempt to access its memory results in incomprehensible data. Every 4th Generation AMD EPYC™ processor offers up to one thousand encryption keys. This architecture doesn’t alter applications within the VM; instead, it operates at the operating system level and elevates data security. Designed to protect data in use, including memory contents, the encryption hardware built into the memory controller manages VRAM traffic encryption and decryption, strengthening protection of data in use.17
Resources
1- Chuck Brooks, “Cybersecurity Trends & Statistics For 2023; What You Need to Know,” accessed December 4, 2023, https://www.forbes.com/sites/chuckbrooks/2023/03/05/cybersecurity-trends--statistics-for-2023-more-treachery- and-risk-ahead-as-attack-surface-and-hacker-capabilities-grow/?sh=9885ce219dba.
2- Ken Kizzee, “Cyber Attack Statistics to Know,” accessed December 19, 2023,https://parachute.cloud/cyber-attack- statistics-data-and-trends/.
3- Dell, “Improved security with iDRAC9 using Root of Trust and BIOS Live Scanning,” accessed December 19, 2023, https://dl.dell.com/manuals/common/dell-emc-idrac9-security-root-of-trust-bios-live-scanning.pdf.
4- Dell, “Cyber Resilient Security in Dell PowerEdge Servers,” accessed December 4, 2023, https://www.delltechnologies. com/asset/en-us/products/servers/industry-market/cyber-resilient-security-with-poweredge-servers.pdf.
5- Technopedia, “Complex Programmable Logic Device,” accessed December 4, 2023, https://www.techopedia.com/definition/6655/complex-programmable-logic-device-cpld.
6- AMD, “AMD Pro Security,” accessed December 4, 2023, https://www.amd.com/en/technologies/pro-security.
7- AMD, “AMD Infinity Guard,” accessed December 4, 2023, https://www.amd.com/en/technologies/infinity-guard.
8- AMD, “4 Ways AMD Infinity Guard Helps Protect Your Data,” accessed December 4, 2023, https://www.amd.com/system/files/documents/content-security-infographic.pdf.
9- AMD, “AMD Infinity Guard.”
10- Dell, “Defense in-depth: Comprehensive Security on PowerEdge AMD EPYC Generation 2 (Rome) Servers,” accessed December 4, 2023, https://infohub.delltechnologies.com/p/defense-in-depth-comprehensive-security-on-poweredge- amd-epyc-generation-2-rome-servers/.
11- Dell, “Reduce Your Risk of Unauthorized Server Data Access,” accessed January 24, 2024, https://infohub.delltechnologies.com/section-assets/data-protection-infographic.
12- Principled Technologies, “Reduce hands-on deployment times to near zero with iDRAC9 automation,” accessed December 4, 2023, https://www.principledtechnologies.com/Dell/iDRAC9-v6.10-provisioning-infographic-0323.pdf.
13- AMD, “AMD Infinity Guard.”
14- AMD, “AMD Memory Encryption,” accessed December 4, 2023,
https://www.amd.com/content/dam/amd/en/ documents/epyc-business-docs/white-papers/memory-encryption-white- paper.pdf.
15- AMD, “AMD Secure Encrypted Virtualization,” accessed December 4, 2023, https://www.amd.com/en/developer/sev.html
16- AMD, “AMD Memory Encryption.” https://www.amd.com/content/dam/amd/en/documents/epyc-business-docs/ white-papers/memory-encryption-white-paper.pdf
17- AMD, “AMD Secure Encrypted Virtualization.”

Foundation for Enterprise Security and Cyber Resiliency: Dell PowerEdge and Broadcom
Wed, 13 Mar 2024 20:49:09 -0000
|Read Time: 0 minutes
Executive Summary
There are numerous challenges companies face to establish and maintain the cybersecurity capabilities required to operate in today’s complex and increasingly hostile digital world. Companies are reminded daily of the potential cost to their reputation, revenue and more for failing to maintain a competent cyber resiliency profile. Often, even a single breach can result in regulatory fines, loss of revenue and customers, and in some cases may even cause existential implications for a firm.
A Futurum Group study conducted in 2023, with more than 150 IT Security professionals from companies with 1,000 or more employees resulted in several insights. More than 80% of companies surveyed reported an increase in their cybersecurity budgets while nearly 50% are increasing their cybersecurity headcount in response to these growing threats. In terms of challenges faced, the top two items were limited budgets and high solution costs, indicating a need to improve cybersecurity without significant cost implications.
As part of The Futurum Group’s ongoing research and analysis, The Futurum Group Labs has developed a cyber-resiliency framework that is designed as a holistic tool for evaluating how well a product or service offering helps a company meet their cybersecurity requirements. This framework incorporates multiple industry standards and best practices to provide a comprehensive perspective for evaluating their security requirements. The Futurum Group utilizes this framework when evaluating security aspects of products and services.
In this paper we review the important security features of Dell and Broadcom components, and how they can help companies improve their security posture and overall cyber resiliency. The Futurum Group Labs tested Dell 16th Generation PowerEdge servers with Broadcom 57508 Ethernet Network Interface Card (NIC) and PERC RAID controller cards both within our lab facilities, and remotely within Dell’s lab. This analysis provides a real-world use case of managing security across a multi-site, distributed environment.
Summary of Findings
The Futurum Group Labs performed hands on testing and review of many of the security features and capabilities of Dell PowerEdge 16th Generation servers, together with Broadcom 57508 dual port 100 Gb Ethernet NIC and Broadcom SAS4116W ROC based Dell PERC 12, H965i RAID cards. Our evaluation included analyzing security best practices, along with overall system security features and capabilities.
Additionally, The Futurum Group has developed a security framework comprising areas for review across multiple areas of enterprise security. The Futurum Group’s Security Framework builds upon industry best practices and multiple NIST standards and provided the basis for our evaluation process.
Against this framework, we found the Dell PowerEdge servers, together with Dell PowerEdge RAID Controller 12 (PERC) and Broadcom NICs provided an integrated security solution that met or exceeded requirements in all areas evaluated. Strengths included the following areas:
- Adherence to standards, including the NIST concepts of Identify, Protect, Detect, Respond & Recover
- Zero Trust security principles utilized by both Dell and Broadcom for all aspects of the systems
- Integrated security management via iDRAC, OME and CloudIQ provide enterprise-wide capabilities
- Dell’s Secure Component Verification Process helps ensure security from order to delivery
Futurum Group’s Security Framework
The Futurum Group has developed a security framework for evaluating the overall cyber resiliency rating of products operating within IT environments. This framework encompasses multiple inter-related aspects of security including ensuring that secure design methodologies are utilized during product creation.
The first area assessed is the design methodology utilized for developing products and services. Next the security features of a product are evaluated, along with the security of the manufacturing and supply chain processes. Finally, the IT security implementation of a company using the product is important. Taken together, these components provide a comprehensive tool for evaluating and analyzing the security profile of a product operating within a particular company. An overview is shown in Figure 1.
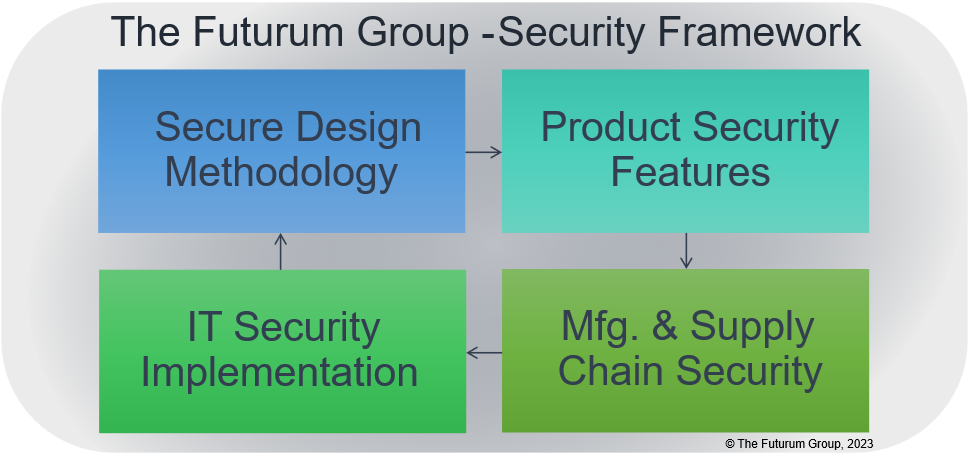
Figure 1: Security Framework Overview (Source: The Futurum Group)
It should be noted that “IT Security Implementation” was outside of the scope of work for this project. Since security responsibilities fall upon each company to utilize and implement security features appropriately.
Dell Solution Overview
As a foundation for securing PowerEdge server products, intrinsic security practices are incorporated into hardware product design and software or firmware code development. These practices include the following processes to ensure security features are implemented at the time of product inception and continue throughout the development cycle. To perform this practice effectively, Dell engineers are required to take mandatory security training before handling the code. Security “champions” are assigned to each development team to drive a security culture within the organization. Dell combines all components to create an integrated solution with hardware, software and services that together address security threats companies are facing.
Dell and Broadcom asked The Futurum Group Labs to evaluate Dell’s servers together with Broadcom add-in cards with respect to how these products can help IT clients address security vulnerabilities and achieve the levels of cyber resiliency necessary for operations in today’s challenging environment.
Specifically, The Futurum Group Labs validated the latest, 16th Generation Dell PowerEdge servers, together with Dell - Broadcom PERC 12 RAID cards and Broadcom 57508 NIC cards, along with relevant firmware and software that address security and cyber resiliency within IT environments. The Broadcom components helped provide overall end-to-end security capabilities through integration into Dell’s management tools.

Figure 2: Dell PowerEdge and Broadcom NIC Products (Source: Dell and Broadcom)
Dell’s Security Principles for Cyber Resiliency
As companies have become increasingly sophisticated in their approach to security, it is clear that point solutions are insufficient to address today’s complex cybersecurity requirements. While there is naturally a focus on the hardware components themselves, an important part of the overall Dell and partner security ecosystem is the use of critical software elements that help enable security features and provide easy-to-use interfaces for IT users.
| Futurum Group Comment: Too often, security features require IT administrators to choose between usability or security. As a result, IT administrators may ignore or circumvent security best practices to improve ease of use. The management tools of the PowerEdge systems enable IT users to easily follow best practices while utilizing the comprehensive security features of Dell servers and Broadcom. This functionality helps reduce attack surfaces for malicious actors, while maintaining usability and performance. |
As described previously, The Futurum Group’s Security Framework incorporates multiple best practices and industry standards, including NIST Cybersecurity Framework (CSF) which outlines five tenants:
- Identify: Ensure that an organization understands and can manage cybersecurity risk, assets, and data
- Protect: Develop and implement appropriate safeguards to ensure critical infrastructure is protected
- Detect: Quickly detect cyber events via anomaly detection and continuous monitoring
- Respond: Prepare and implement the ability to take appropriate action in response to a cyber event
- Recover: Establish the ability to maintain business resiliency and restore impacted systems
The Futurum Group Security Framework extends the NIST framework, including the following areas for assessing Dell’s Cyber Resilient Architecture for security:
- User authentication and authorization using multi-factor authentication applied to users and devices (User AA and Device AA) with role-based and least privileged access controls.
- Dell PowerEdge hardware RoT creates a chain of trust from firmware to devices and supports complete customization of Secure Boot, including removal of all industry-standard certificates provided by Microsoft, VMware, or the UEFI CA.
- Using PowerEdge cyber resilient platform RoT extends to Secure Enterprise Key Management for data-at-rest protection.
- Applications and workload security to protect runtime environments, leveraging data and network security technologies including end-to-end encryption and cryptographic signatures.
- Utilize Security Protocol and Data Model (SPDM) capabilities for device attestation as part of the Zero-Trust/cyber resiliency architecture. Future capabilities include internal encrypted communication capabilities.
- Auditing and analytics for visibility and alerting of security issues using persistent event logging and real-time code and firmware scanning.
- Automation and orchestration technologies to enable automated API and CLI driven actions, along with enterprise web UI tools to provide easy-to-use global management of security alerting, reporting and automation.
Test and Validation Findings
The Futurum Group Labs Security Framework shown previously in Figure 1, was used to analyze the overall security capabilities of products or features. Our analysis examined each aspect of the Security Framework with details provided in the following four sections.
1 - Secure Design Methodology
Requirements
Confirm that security considerations begin at product inception with cybersecurity and resiliency capabilities integrated throughout product design and development.
Verify that hardware security features based on Zero Trust, such as tamper proof TPM often form the basis of software security, to deliver an integrated secure system.
Asses if the software architectures leverage hardware security and utilize the available security capabilities. Additionally, validate that threat modeling and penetration testing along with external audits and ongoing mitigation of vulnerabilities are performed.
Dell PowerEdge and Broadcom Design
Dell utilizes a secure Software Development Lifecycle (SDL) as the basis for instilling security throughout the design process. A comprehensive SDL process should ensure that any identifiable attack methods are mitigated utilizing standards-based security mechanisms to thwart these attack vectors.
As outlined previously, security starts with using a secure design methodology, with multiple considerations required to help products provide cyber resiliency:
| - Security is considered for each feature - Following industry best practices, Dell software is designed to obstruct, oppose and counter malicious attacks - External audits of security features - On-going evaluation of new vulnerabilities - Rapid response to common vulnerability exposures (CVEs) with remediation | |
Table 1: Dell SDL Principles | Figure 2: Dell SDL Model |
Additional aspects of secure design include end-to-end secure communication based upon cryptographically signing certificates used to authenticate and authorize components such as with Device-ID, 802.1x, and SPDM.
Finally, even with good design and secure implementations, vulnerabilities and breaches may still occur. Thus, it is important for products to be designed with resiliency and Zero Trust implementation, so that when penetrations do occur, their impact is limited. Dell’s rapid response to critical CVEs and patching of identified components is an important aspect of mitigating threats from CVE’s as they arise.
| Futurum Group Comment: Dell’s rapid response to critical CVEs and patching of identified components is an important aspect of mitigating threats from CVE’s as they arise. As one of the largest system vendors, Dell leverages their significant real-time monitoring via CloudIQ and other tools, to quickly respond to emerging threats and provide their customers with tools and processes to thwart attacks. |
2 – Product Security Features
Product security was an area of particular focus by The Futurum Group Labs when measuring how Dell PowerEdge servers, together with Broadcom based PERC 12 and 57508 Ethernet NICs met Futurum’s Security Framework. System security requires a layered approach, with hardware security features and capabilities utilized by the firmware, that provides a secure foundation for the operating system (OS) and applications running within the OS. The hardware root of trust provides several foundational security capabilities including a secure, tamper-proof key storage location, a unique hardware encryption key, and other facilities required as part of a cryptographic framework.
Specifically, The Futurum Group Labs tested the following system components:
- Dell PowerEdge 16th Generation systems with a Trusted Platform Module (TPM)
- Dell PERC 12 (PowerEdge RAID Controller, 12th generation)
- Broadcom 57508 Dual Port, 100 Gb Ethernet NIC with QSFP adapter connectivity
- Secure BIOS management system settings, via iDRAC
- Device identification via cryptographic framework (devices attestation uses a devices hardware RoT)
Each aspect of a system must be secured, ideally with each element utilizing industry best practices including Zero Trust principles, enabled via a silicon Root of Trust (RoT) as the foundation of physical security. Utilizing a certified RoT device that provides tamper resistance, the hardware protects the device firmware, which in turn is utilized to ensure critical software security features are verifiably operating securely. Security breach examples could include the exchange of entire PCIe cards, uploading compromised firmware or other attacks that target PCIe cards.
Delivering end-to-end security requires the entire solution integrates multiple hardware RoT devices, together with software features that leverage the underlying hardware capabilities. Dell’s PowerEdge servers together with Broadcom NIC and RAID controllers provide this capability by validating each layer, from hardware to firmware and the OS using cryptographic attestation. Dell’s iDRAC and other management tools leverage this integrated security environment to deliver a secure, easy to manage solution.
| Futurum Group Comment: A key aspect of the Zero Trust approach is to utilize hardware RoT devices to provide cryptographic verification to build a secure ecosystem. Using Zero Trust, each component first verifies, then trusts their counterpart based upon certified key exchanges and mutual authentication, attestation and authorization. These features are critical for the additional security mechanisms used throughout the Dell servers along with supported devices. |
As part of a standards-based approach to secure system management, a new Security Protocol and Data Model (SPDM) standard has emerged. This standard leverages Zero Trust principles and enables devices to securely verify each other (device attestation) and then establish secure communications over a variety of internal, server transport connections. Dell’s 16th Generation servers, along with 12th generation PERC and Broadcom 57508 NICs now utilize SPDM, to enhance security. The SPDM standard leverages existing technologies including public key encryption, and cryptographic signing of certificates to provide device attestation between Dell’s servers and Broadcom devices. In future implementations, the SPDM standard can also enable secure communication channels between devices.
Broadcom Networking
Broadcom 57508 Ethernet NIC, with speeds from 25 Gb to 200 Gb operate with Dell’s security features and leverage some of the same Zero Trust principles. Broadcom’s NICs also have a hardware based, silicon RoT which enable multiple additional benefits, including:
- Silicon RoT with secure key storage on servers and PCIe devices
- Secure firmware loading, updates and recovery on servers and PCIe devices
- Signed UEFI drivers, with Secure PXE boot for onboard NICs and PCIe NICs
- Device attestation (SPDM 1.2) between servers and devices, and audit logging of all devices
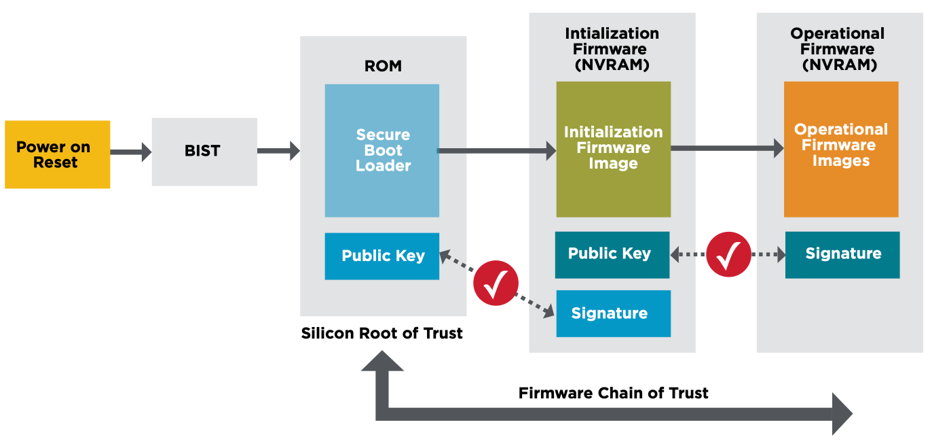
Figure 3: Broadcom’s Silicon RoT w/ Secure Firmware Loading (Source: Broadcom)
Hardware TPM
The Futurum Group Labs verified that Dell PowerEdge’s hardware security operated correctly by testing the supplied TPM version 2.0. Testing verified that all supplied features operated correctly including key generation using a true random number generator, and a secure key store. Additionally, after verifying TPM functionality, we then enabled security features including secure boot, secure lifecycle management, out of band management, and firmware updating.
Dell PowerEdge RAID Controller (PERC)
Dell’s PowerEdge RAID Controllers, aka PERC 12th generation use Broadcom controller interfaces and support a variety of RAID levels and device connectivity. The PERC 12 H965i controllers tested are designed for internal and external device support and include multiple RAID levels along with SAS and NVMe connectivity.
The Dell 12th gen PERC security features include:
- Silicon based hardware RoT: Foundation for Zero Trust
- Onboard RoT builds a chain of trust by authenticating all PERC firmware prior to execution, permits only authenticated firmware upgrades
- SPDM support: Provides device attestation and secure communications
- UEFI secure boot: Helps reduce attack vectors, and root kit installations
- Secure Firmware Updates: Simplifies administrative security updates
As shown above previously in Figure 3, the process for secure booting from a Dell PERC 12 controller card is similar to securely booting via a NIC.
Dell PowerEdge 16th Generation Servers
Multiple areas of evaluation and testing were performed with the PowerEdge servers together with PERC RAID cards and Broadcom NICs. One of NIST’s specifications (NIST SP 800-193) specifically addresses platform firmware resiliency. It stipulates methods for securing the BIOS, boot ROMS, along with firmware and driver signatures to verify authenticity. This guideline also outlines a method for providing a “secure boot” mechanism, whereby each component verifies subsequent components in the stack from hardware all the way to the operating system.
Secure Boot
Dell PowerEdge secure boot via Broadcom NIC, Dell PERC or local disk occurs via similar mechanisms. The secure boot process is important to ensure that a validated OS image is ultimately loaded and is used to operate the system. If an OS is altered, system security cannot be guaranteed. At a high-level, secure boot validates the UEFI drivers and boot loaders which then guarantees the authenticity and integrity of each subsequent component, firmware or software element that is loaded. This chain of trust is one of the basic elements of the Zero Trust model and basic system security. Secure boot functionality was verified with multiple devices, including secure boot of a verified OS image from Dell’s PERC 12 controller, and via PXE boot using a Broadcom 100 GbE NIC card.
Authentication Access, Authorization and Auditing (IAM)
These areas include identity and access management of systems (IAM), components and users, multi-factor authentication, audit logging and alerting, and access based upon authenticated authorization. The IAM capabilities are implemented throughout Dell’s management tools, including iDRAC, OME and CloudIQ.
Secure Lifecycle Management
Secure lifecycle management features were verified by first establishing a baseline, and then updating to the latest firmware and drivers via iDRAC. The secure process was verified both via the successful updates and notices, along with one image that did not update due to an invalid security certificate. The test properly identified an invalid certificate, and would not allow the firmware to be updated, which was the correct behavior. Upon obtaining a firmware image with the proper security certificate, the firmware update was successfully applied, which again was the desired security behavior.
Management, Alerting and Reporting
A critical part of Dell’s cybersecurity capabilities are the management tools available. Dell’s iDRAC tool continues to evolve and add capabilities for BIOS and low-level system management of PowerEdge servers and attached devices. Incorporating standards such as Redfish for secure remote manageability, enables secure programmatic API, CLI and scripting access, while also enabling secure web UI access for users preferring a graphical interface.
The Futurum Group Labs utilized and validated numerous functions and capabilities of each of Dell’s enterprise management solution. iDRAC, Open Manage Enterprise and CloudIQ are designed to work together to enable a spectrum of management, alerting and reporting capabilities.
- Dell’s iDRAC: system level management software pre-installed on all Dell PowerEdge servers, providing secure out-of-the box management capabilities for individual systems.
- OpenManage Enterprise (OME): Designed for IT staff to monitor and manage Dell servers within a datacenter. OME provides roll-up features to aggregate information while still providing the ability to manage individual systems, either from within OME or via linking to iDRAC.
- CloudIQ: Enables multi-site and enterprise-wide monitoring and management, with high-level management and reporting while also providing drill-down system management of some features and function.
A key part of iDRAC with OME is the integration of Broadcom components throughout, including the ability to monitor Broadcom-based PERC and NICs for firmware levels, vulnerabilities and provide updates through the secure lifecycle management capabilities.
The Dell OME management server was utilized throughout testing. Installation was straightforward and accomplished without needing to consult manuals. Downloading a preconfigured VMware image (OVA) and deploying to a VMware cluster, the OME server was operational in under 30 minutes. OME provided a way to both perform health monitoring and alerting, along with active management of desired systems. The OME interface was intuitive and provided significant fleet management features, by helping to highlight potential issues and providing the ability to resolve problems.
| Futurum Group Comment: Looking specifically at the security features of iDRAC, OME and CloudIQ, we found the health and security scoring mechanism and recommendations to be extremely effective. A significant challenge for most IT environments is prioritizing which updates are the most critical and then quickly remediating these issues. Dell’s management tools enable finding and applying critical updates quickly, and is one of the most effective solutions for security we have evaluated to date. |
With CloudIQ’s health scores and recommendations, it required only a few clicks to sort by the most critical issues, and then utilize the appropriate management tools to apply remediation for the vulnerabilities. Some issues may be resolved entirely from CloudIQ, with others enabled via links to OME for remediation.
Dell’s CloudIQ service has continued to evolve since its storage system origins into a Dell product-wide SaaS application that effectively provides health monitoring and alerting, along with recommendations. Dell’s overall management architecture provides robust security manageability, alerting and reporting capabilities that provide the critical link IT administrators require to effectively manage a secure IT environment.
3 - Manufacturing & Supply Chain Security
The concept of evaluating a product’s manufacturing and supply chain for security is relatively new to many companies. Although these practices have been standard for regulated industries for years, only recently have companies began to apply supply chain security practices to products designed for commercial use. One reason is that due to increased focus on other threats, the supply chain is now seen as an area of increasing vulnerability.
One area of supply chain security that sets Dell apart from their competitors is Dell’s Secured Component Verification (SCV), which is designed to help verify that the security of all components is maintained from order until it is delivered and installed at the customers location. Dell’s approach to supply chain threats includes supply chain integrity with ISO certification of sites, software bill of materials and the Dell SCV process, which all help to prevent counterfeit components or malware being inserted into systems or components.
| Futurum Group Comment: Dell’s approach to securing product manufacturing and supply chain is perhaps the best processes the Futurum Group Labs has evaluated. In particular, Dell’s Secured Component Verification process provides unique value, enabling IT clients to quickly and easily ensure their products have not been altered or modified, including verification of both hardware and firmware components. Dell SCV is an important tool for addressing overall cybersecurity. |
An overview of the Dell SCV process is shown below in Figure 4.
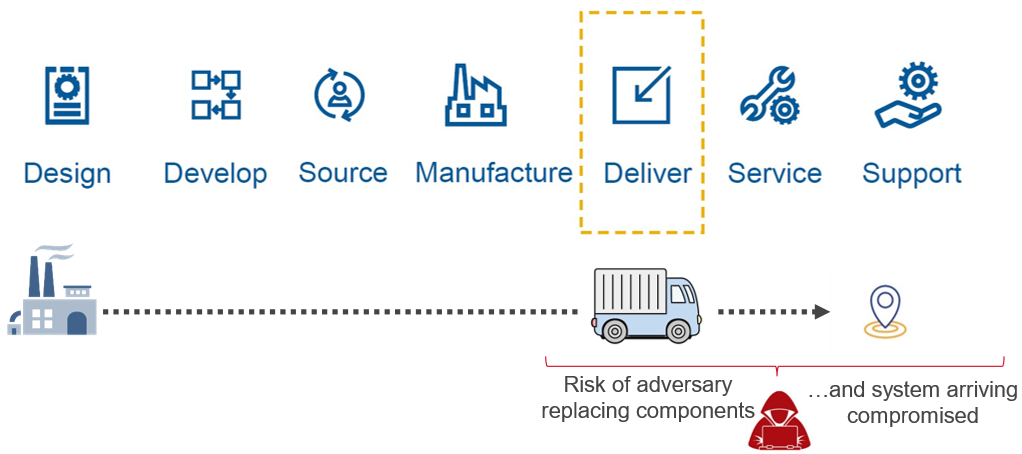
Figure 4: Dell’s Secured Component Verification Process (Source: Dell)
The Futurum Group Labs verified that Dell’s SCV can accurately report on each major system element, showing whether it is a verifiable component that was part of the original bill of materials or not. The SCV leverages the earlier security principles and technologies outlined, including Secure RoT and hardware TPM modules, cryptographic signatures for device attestation and Zero Trust principles to create a process to verify that a system has not been altered in any way.
During testing The Futurum Group Labs verified that the SCV correctly verified components that were part of the original bill of material and order, and items that were added afterwards. This capability provides a unique and easy-to-use method for IT users to attest to the authenticity and integrity of their systems.
4 - IT Security Implementation
The last major component of the Futurum Group’s Security Framework is how well a company and the IT organization operates with respect to security. IT security has multiple standards, industry best practices and recommendations to help inform and guide companies towards implementations that provide the necessary security and cyber resiliency.
One guideline covering IT security is the NIST CSF [1] which includes the key phrases, Identify, Protect, Detect, Respond and Recover. The most recent update to this framework, the version 2.0 draft, adds a sixth area “Govern” to the previous list, placing more emphasis on corporate oversight and implementations.
Although important, this area falls largely outside the scope of vendors’ product offerings but may be supplemented via professional services and training. As a result, The Futurum Group did not formally assess the IT Security aspects of the Futurum Group’s Security Framework.
| Futurum Group Comment: The Futurum Group’s Security Framework evaluates IT security through the lens of a products ease-of-use and ability to implement security best practices. In this regard, Dell enables IT security by making security best practices the default option when possible, and ensuring security features are easy-to-use. As a result of security integration between PowerEdge servers, Broadcom 57508 NICs and Dell management tools helps companies implement security best practices. |
For companies that desire security consulting to help supplement their capabilities, Dell and their partners offer a variety of security services, including cybersecurity advisory services that are designed to assess a company’s security posture, and help improve internal procedures and help elevate security capabilities to attain proficiency in this area. Based upon the principles outlined previously, Dell security services include Cybersecurity Advisory Services, Recovery Services for Cyber-attacks, along with managed services for cyber-attack detection and response.
Moreover, the product design, product features, together with the secure supply chain features and security consulting services all provide sufficient tools to enable IT organizations to manage and maintain a highly secure environment that meets NIST and industry best practices for maintaining a cyber resilient posture.
Final Thoughts
Security and cyber resiliency have become areas of critical focus for enterprises according to The Futurum Group’s research. Additionally, conversations with IT clients often include a discussion of ransomware and cyber resiliency. Organizations that follow best practices follow the NIST or other frameworks to integrate security throughout their organization and operational procedures.
Attempting to purchase point products, or simply “add security” to existing infrastructure is challenging at best. Starting with products that are designed from the ground up with security is a key priority. According to The Futurum Group’s research, a significant number of security breaches utilize compromised servers as part of their attack vector. Thus, securing servers, their networking interfaces and storage devices is an ideal area of focus for companies looking to improve their cyber resiliency.
In assessing Dell PowerEdge servers together with Broadcom add-in cards against the Futurum Group’s Security Framework, we found that the systems meet or exceed requirements in all categories. There were several areas of strength noted, where PowerEdge significantly exceeded expectations. These include several security integrations between Dell’s silicon RoT and Zero Trust approach, together with Broadcom NICs and PERC RAID cards own embedded RoT and Zero Trust capabilities and importantly with Dell’s management tools.
Another area where PowerEdge exceeded expectations is the seamless management capabilities of iDRAC for baseboard system management, with OME for datacenter management, coupled with CloudIQ for global monitoring, alerting and reporting of multiple datacenters. The particular focus on security alerting and recommended actions of CloudIQ help IT administrators move from inaction due to an overwhelming number of issues, to action focused on the most important configuration or security issues.
Finally, Dell’s SCV process significantly exceeded expectations, offering a best-in-class end-to-end process for ensuring system integrity from suppliers, manufacturing and configuration, shipping, delivery and installation. A significant area of concern for organizations is ensuring their systems do not contain malicious hardware elements that could circumvent even robust security practices. Dell’s SCV provides a simple and easy way for organizations to ensure their infrastructure has not been compromised.
Taken together, Dell PowerEdge servers, with Broadcom NIC cards provide comprehensive security capabilities that provide a foundation for IT users to quickly and efficiently establish a highly secure computing environment that leverages industry best practices.
Resources
[1] NIST Cybersecurity Framework, draft version 2.0, August 2023:
About The Futurum Group
The Futurum Group is dedicated to helping IT professionals and vendors create and implement strategies that make the most value of their storage and digital information. The Futurum Group services deliver in-depth, unbiased analysis on storage architectures, infrastructures, and management for IT professionals. Since 1997 The Futurum Group has provided services for thousands of end-users and vendor professionals through product and market evaluations, competitive analysis, and education.
Copyright 2023 The Futurum Group. All rights reserved.
No part of this publication may be reproduced or transmitted in any form or by any means, electronic or mechanical, including photocopying and recording, or stored in a database or retrieval system for any purpose without the express written consent of The Futurum Group. The information contained in this document is subject to change without notice. The Futurum Group assumes no responsibility for errors or omissions and makes no expressed or implied warranties in this document relating to the use or operation of the products described herein. In no event shall The Futurum Group be liable for any indirect, special, inconsequential, or incidental damages arising out of or associated with any aspect of this publication, even if advised of the possibility of such damages. All trademarks are the property of their respective companies.
This document was developed with funding from Dell Inc. and Broadcom. Although the document may utilize publicly available material from various vendors, including Dell, Broadcom and others, it does not necessarily reflect such vendors' positions on the issues addressed in this document.