Assets

Ansible: Adding Security to Your Playbooks Using Ansible Vault
Mon, 19 Dec 2022 21:40:16 -0000
|Read Time: 0 minutes
Security for your Ansible Network Automation
Let me introduce Ansible Vault. Ansible Vault provides the security for your playbooks’ sensitive data. You can use Ansible Vault to encrypt any Ansible data from a single variable to a file within the Ansible projects. As we continue to explore Ansible network automation, consider including the security capabilities provided by Ansible Vault.
How does it work
Think of a bank vault with many locked vault drawers. A vault drawer key is needed to retrieve the sensitive content. In the same way, Ansible vault creates the vault drawer while you provide the key (password).
Ansible Vault is a password-based authentication feature that is built in with the Ansible framework. Ansible Vault adds security in the form of encrypted Ansible data for the playbooks, host_vars, group_vars, or inventory files. For example, with Ansible Vault, you can encrypt sensitive Ansible data like the switch login credentials used when running playbooks.

By now you might be wondering, “Where do I start?”
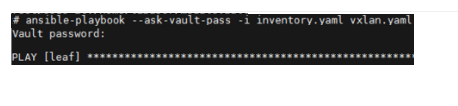
Start the encryption process on the Ansible automation control node.
Easy to use and implement
The ansible-vault command-line utility is simple to use. The overall process to implement Ansible Vault is straightforward.
In one implementation option, you provide the vault secret password when you initially encrypt the Ansible data, in this case the switch login credentials. The vault password “key” is then associated with the vaulted encrypted data within Ansible Vault.
Here is the ansible-vault utility command structure to encrypt a string.
ansible-vault encrypt_string <password_source> '<string_to_encrypt>' --name '<string_name_of_variable>'
Here is an example of encrypting the string “admin” for Ansible variable “ansible_ssh_pass.”
ansible-vault encrypt_string --ask-vault-password "admin" --name "ansible_ssh_pass"
“ansible-vault” is the command-line utility.
“encrypt_string” is the vault command to encrypt a string.
“--ask-vault-password” is source providing the vault password.
“string_name_of_variable” is the Ansible variable to use the encrypted data.
Ansible Vault requires you to provide the vault password (using a prompt or file) every time you need to run the playbook with the encrypted data.
Ansible Vault has many other commands to create, edit, view, rekey, decrypt, and more when working with encrypted data. For other implementation options, see the Ansible Vault documentation. For an interactive trial, go to Demo Center.
Additional Resources
Ansible Vault Hands-On Lab on Demo Center

Automation with Ansible Collections, the next step in your network automation journey
Thu, 03 Nov 2022 14:03:56 -0000
|Read Time: 0 minutes
SmartFabric OS10 Ansible Collection
Dell SmartFabric OS10 Ansible Collection has a lot to offer for your network automation of Dell PowerSwitches. In this blog, I am going to dig a little deeper into the roles of the Ansible Collection. Ansible has continued to evolve over the years, and I can say from experience that the introduction to Ansible can be a little overwhelming at first.
The well-organized Ansible documentation helped me to understand the workings of Ansible and to quickly get started.
Ansible Galaxy near me
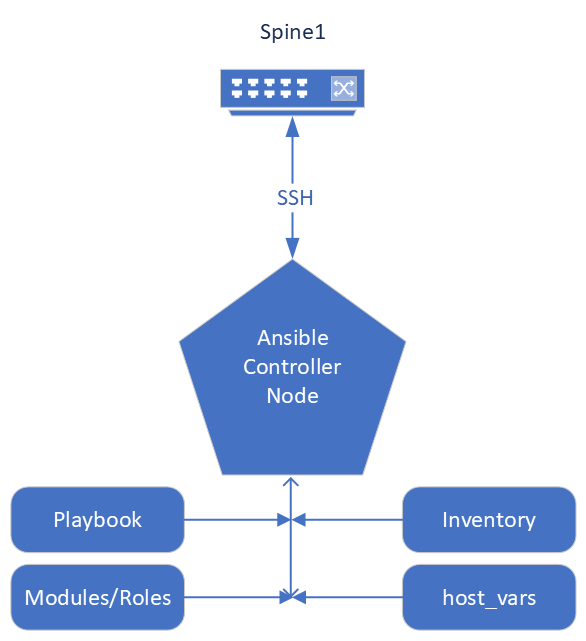
I want to mention that the great part of the Ansible evolution is the introduction of the Ansible Collection. Ansible Collection is a simpler method to package and distribute Ansible content. The Ansible Collection contains useful resources: readme files, module and role parameter descriptions, and Ansible playbook examples. Dell SmartFabric OS10 Collection has multiple modules, roles, and plugins that enable you to configure your Dell PowerSwitch devices with multiple playbook examples.
The Ansible framework has the common integrated roles, modules, and plugins included on your Ansible control node. The extension to that is the Dell SmartFabric OS10 Ansible Collection which includes the roles, modules, plugins specific to provision the Dell PowerSwitch. Combined they are the components that create the YAML playbooks, inventory files, group var files, and host var files used to manage your Dell SmartFabric switches. Ansible is an open-source project and the community upstream distribution method for Collections is the Ansible Galaxy website, where you can access Dell SmartFabric OS10 Collections. The repository for Ansible Galaxy Collections and the Dell SmartFabric OS10 Collection is on the GitHub website. The current Dell SmartFabric OS10 Collections namespace to search for on GitHub is dellemc.os10. The Dell SmartFabric OS10 Collection documentation provides a great overview and links to each of the roles.
Start with the Readme
I want to point out that collections and roles have their own readme. The collections readme provides a good overview of the collection. The role readme provides the details on each role, so let us dig into this Role readme. Each role readme will better explain the role variables, parameters, and key values. Each key parameter has a short description or notes on how to use the role key. The role readme includes all the important information explained in an easy-to-read table. Examples of each key type are provided, whether it is a string, list, integer, Boolean value, state value, or dictionary. I highly recommend reviewing the playbook example in the role to get a good sense of how the role and its parameters are structured.
There are typically multiple key parameters for each role. Each role may require a series of keys and values to describe the intended state the playbook will check for on the device. Typically, the series of key:value pairs are part of the host_vars file for each device accessed by the playbook. Using roles provides flexibility with your playbooks and host_vars files for your network automation.
The other valuable information provided in the role readme is the connection variables section. This section provides the information needed to communicate to your switch. You can place the connection information in your host_vars file, inventory file, or the playbook.
The example playbooks provide the most insight on how the collection interacts with your managed switch. The example playbook explains the components and workings of the role inside the playbook and interactions with the switch inventory file, switch host_vars, and switch group_vars files. The example playbook provides details down to the syntax and spacing of each key:value pair, to get you off the ground and running.
Show me the Role
The following example is an excerpt from the VLAN role, within the Dell SmartFabric OS10 Collection.
This role facilitates configuring virtual LAN (VLAN) attributes. It supports the creation and or deletion of a VLAN and its member ports. This role is abstracted for Dell PowerSwitch platforms running Dell SmartFabric OS10.
The VLAN role requires an SSH connection for connectivity to a Dell SmartFabric OS10 device. You can use any of the integrated operating system connection variables.
- Example role variables (see the VLAN role for the full list) role is abstracted using the ansible_network_os variable that can take dellemc.os10.os10 as the value.
- os10_vlan (dictionary) holds the key with the VLAN ID key and the default-VLAN key.
- The VLAN ID key should be in format "vlan ID" (1 to 4094)
- Variables and values are case-sensitive
Table 1: VLAN ID keys
Key | Type | Notes | Support |
description | string | Configures a single-line description for the VLAN | os10 |
tagged_members | list | Specifies the list of port members to be tagged to the corresponding VLAN | os10 |
Note: See the VLAN role for the full table.
Ansible Dell network roles require connection information to establish communication with the nodes in your inventory.
Table 2: Example connection variable
Key | Required | Choices | Description |
ansible_host | yes | N/A | Specifies the hostname or address for connecting to the remote device over the specified transport |
ansible_ssh_user | no | N/A | Specifies the username that authenticates the CLI login for the connection to the remote device; if value is unspecified, the ANSIBLE_REMOTE_USER environment variable value is used |
Note: See the VLAN role for the full table.
Ansible playbook
Let us wrap up this discussion with the Playbook. An example playbook with a simple host file and an inventory file are shown below.
Example playbook.yaml file:
---
- hosts: os10_switches
connection: network_cli
collections:
- dellemc.os10
roles:
- os10_vlan
Example host_vars/os10_sw1.yaml
hostname: os10_sw1
# Parameters for connection type network_cli
ansible_ssh_user: xxxx
ansible_ssh_pass: xxxx
ansible_network_os: dellemc.os10.os10
# Create vlan100 and delete vlan888
os10_vlan:
vlan 100:
description: "Edge Group1"
state: present
vlan 888:
state: absent
Example inventory.yaml file:
[os10_sw1]
os10_sw1 ansible_host=100.104.28.119
[os10_sw2]
os10_sw2 ansible_host=100.104.28.120
[os10_switches:children]
os10_sw1
os10_sw2
Run the playbook
Run the playbook using the following simple Ansible-playbook syntax:
Ansible-playbook -i inventory playbook.yaml
Conclusion
I recommend starting your automation and innovation journey now. Dell SmartFabric OS10 Collections offer a great deal of options to include in your Ansible automation journey for your Dell PowerSwitch devices and overall DevOps and NetOps Automation ecosystem. Go to the Ansible Galaxy website to review the Dell SmartFabric OS10 Collection roles and details. Another key resource is the Dell Fabric Design Center, where you can interact and build your network fabric and download the switch configurations in OS10 or Ansible playbook collection format.
Additional information
For more about Ansible Dell SmartFabric OS10 Collections by Dell Technologies, see:
- Dell Technologies Info Hub
- Network Automation Journey with Ansible
- Simplify BGP EVPN VXLAN data center deployment challenges with Ansible
- Dell Demo Center
- Dell Fabric Design Center.

Introduction to Ansible Network Collection for Dell SmartFabric Services
Wed, 19 Oct 2022 18:54:48 -0000
|Read Time: 0 minutes
SFS Ansible collection
With Dell OS10.5.4.0, the OS10 Ansible automation journey continues. Ansible helps DevOps and NetOps reduce time and effort when designing, managing, and monitoring OS10 networks in enterprise IT environments. Updates to Ansible collections provide new automation benefits for increased operational efficiencies. This blog provides a quick introduction to the Ansible network collection for Dell SmartFabric Services (SFS).
The Ansible network collection for SFS allows you to provision and manage OS10 network switches in SmartFabric Services mode. The collection includes core modules and plugins and supports network_cli and httpapi connections. Supported versions include Ansible 2.10 or later. Sample playbooks and documentation are also included to show how you can use the collection.
With this introduction, there are now additional SFS automation choices. The following table lists some examples of the included modules:
| Module Name | Module Description |
|---|---|
sfs_setup | Manage configuration of L3 Fabric setup |
sfs_backup_restore | Manage backup restore configuration |
sfs_virtual_network | Manage virtual network configuration |
sfs_preferred_master | Manage preferred master configuration |
sfs_nodes | Manage nodes configuration |
More SFS automation choices
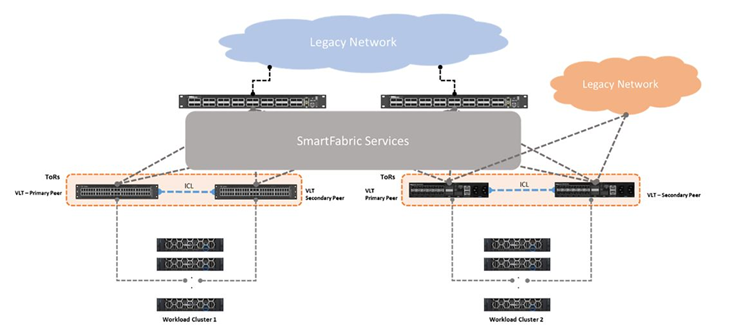
The SmartFabric OS10 SFS feature provides network fabric automation. The SFS leaf and spine personality is integrated with systems including VxRail and PowerStore. SFS delivers autonomous fabric deployment, expansion, and life cycle management. SFS automatically configures leaf and spine fabrics. SFS for leaf and spine is supported on S-series and Z-series Dell PowerSwitches. See the Support matrix for a complete list of supported platforms. For more details see Dell SmartFabric Services User Guide, Release 10.5.4.
You can access the collection by searching for dellemc.sfs on the Ansible Galaxy website. For more information, see the Dell OS10 SmartFabric Services Ansible collection.
 Ansible for SFS now available
Ansible for SFS now available


