Assets

The Influence of Artificial Intelligence on Video, Safety, and Security
Fri, 23 Feb 2024 22:45:15 -0000
|Read Time: 0 minutes
SIA recently unveiled its 2024 Security Megatrend report in which AI prominently claims the top position, dominating all four top spots. With AI making waves across global industries, there arises a set of concerns that demand thoughtful consideration. The key megatrends highlighted are as follows:
- AI: Security of AI
- AI: Visual Intelligence (Distinct from Video Surveillance)
- AI: Generative AI
- AI: Regulations of AI
This discussion will specifically delve into the first two trends—AI Security and Visual Intelligence.
Security of AI
The top spot on the list is occupied by the security of AI. Ironically, the most effective security for AI is AI itself. AI is tasked with monitoring behaviors related to data creation and access, identifying anomalies indicative of potential malicious activities. As businesses increasingly adopt AI, the value of data rises significantly for the organization. However, with AI becoming a more integral operational component, a cyber incident could disrupt not only data but also overall operations and production, particularly when there's a lack of metadata for decision-making.
Ensuring robust cyber protection for data becomes crucial, and solutions like the Ransomware Defender in Dell Technologies' unstructured data offering play a key role. Cyber recovery strategies are also imperative to swiftly resume normal operations. An air-gapped cyber recovery vault is essential, minimizing disruptions and securing a clean and complete dataset for rapid recovery from incidents.
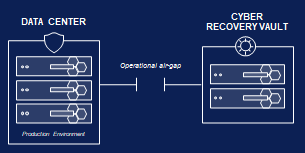 Figure 1. Air-gapped cyber recovery vault
Figure 1. Air-gapped cyber recovery vault
AI visual intelligence
AI Visual Intelligence has been increasingly used across various industries for a multitude of purposes, including object recognition and classification, anomaly detection, predictive analytics, customer insights and experience enhancement, autonomous systems, healthcare diagnostics, environmental monitoring, and surveillance and security. By integrating AI Visual Intelligence into their operations, businesses can harness the power of visual data to improve decision-making, automate processes, enhance efficiencies, and unlock new opportunities for innovation and growth.
Video extends beyond security to impact business operations, enhancing efficiencies as the metadata collected from cameras serves business use cases beyond security functions. An example is the collection of this metadata, such as image metadata, timestamps, objects metadate, geo location, and more. The collection of this metadata necessitates a robust storage solution to preserve complete datasets readily available for models to achieve desired outcomes. This data is considered a mission-critical workload, demanding optimal uptime for storage solutions.
Adopting an N+X node-based storage architecture on-premises guarantees that data is consistently written and available, providing 99.9999% (6 nines) availability in an on-prem cloud environment. Dell Unstructured Data Solutions align perfectly with this workload, ensuring uninterrupted business operations compared to server-based storage solutions facing challenges during deployment or encountering issues with public cloud connectivity. The potential cost-prohibitive nature of public cloud storage for the data required in regular AI modeling may lead to a continued trend of cloud repatriation to on-premises.
Security practitioners evaluating the need for cameras must now strategically map out potential stakeholders within organizations to determine camera requirements aligned with their business outcomes. This strategic approach is anticipated to drive a higher demand for cameras and associated services.
Resources
Check out Dell PowerScale for more information about Dell PowerScale solutions.
Authors: Mordi Shushan, Brian Stonge

Harnessing Artificial Intelligence for Safety and Security
Wed, 22 Nov 2023 00:17:57 -0000
|Read Time: 0 minutes
In the rapidly evolving landscape of technology, we find ourselves on the brink of a major technological leap with the integration of artificial intelligence (AI) into our daily lives. The potential impact of AI on the global economy is staggering, with forecasts predicting a whopping $13 trillion contribution. While the idea of AI isn't entirely new in the security sector which has previously employed analytics to monitor and report pixel changes in CCTV footage, the integration of AI technologies such as machine and deep learning has opened up a world of possibilities. One particularly rich source of data that organizations are eager to harness is video data, which is pivotal in a variety of use cases including operational improvements for retail, marketing strategies, and the enhancement of overall customer experiences.
Industries across the board are exploring AI's ability to enhance business efficiency, underscored by a whopping 63% of enterprise clients considering their security data as mission critical. That said, the success of AI deployments hinges on the collection and storage of data. AI models thrive on large, diverse datasets to achieve effectiveness and accuracy. For instance, when analyzing traffic patterns within a city, having access to comprehensive data spanning multiple seasons allows for more accurate planning. This necessity has led to the emergence of exceptionally large storage volumes to cater to AI's insatiable appetite for data.
A considerable portion of data – approximately 80% – collected by organizations is unstructured, including video data. Data scientists are faced with the arduous task of mapping this unstructured data into their models, thanks in part to the fragmented nature of security solutions. Shockingly, over 79% of a data scientists’ time is consumed by data wrangling and collection rather than actual data analysis due to siloed data storage. Complex scenarios involving thousands of cameras pointed at different targets further complicate the application of AI models to this data.
Recent discussions in the field of AI have introduced the concept of ‘Data Fuzion,’ which underscores the importance of consolidating and harmonizing data, overcoming the current infrastructure's obstacles, and making data more accessible and usable for data science applications in the security industry. There is a significant divide between the potential for data science solutions to drive business outcomes and the actual implementation, largely attributed to – as previously mentioned – the fragmented, siloed nature of data storage and the scarcity of in-house data science expertise.
The AI solutions available today in the security domain often come as black box offerings with pre-programmed models, however end-users are increasingly seeking low- or no-code AI tools that allow them to tailor and modify models to meet their specific organizational needs. This shift enables organizations to fine-tune AI to their precise requirements, further optimizing business outcomes. Additionally, the rise of cloud computing has presented budgetary challenges as organizations are increasingly paying for data access, leading to a trend of cloud repatriation – moving data back to on-premises environments to better manage costs and reduce latency in real-time applications.
AI is transforming the way organizations protect not only their external security but also their internal data. Dell Technologies, for example, offers a solution known as Ransomware Defender within its unstructured data offerings, an AI-based detection tool which identifies anomalies and takes action when malicious actors attempt to encrypt or delete data by modeling typical behaviors and sounding alarms when suspicious activities occur. Check out the Dell Technologies cyber security solution page for more information.
To fully harness the power of AI and navigate these complex data landscapes, organizations are turning to single-volume unstructured data solutions that embody the concept of ‘Data Fuzion.’ Dell Technologies Unstructured Data Solutions, with their petabyte-scale single-volume architecture, offer not only the ability to support this burgeoning workload but also robust cyber protection and multi-cloud capabilities. In this way, organizations can chart a seamless path towards AI adoption while ensuring data-driven security and efficiency. Visit the Dell Technologies PowerScale solutions page to learn more.
Resources
Authors: Mordekhay Shushan | Safety and Security Solution Architect & Brian Stonge | Business Development Manager, Video Safety and Security

PowerScale for Safety and Security
Fri, 29 Sep 2023 22:24:17 -0000
|Read Time: 0 minutes
Advanced Safety and Security Validation Labs
At the heart of the Dell Technologies computer vision offerings is our global validation and testing labs, where reference architectures and design guides are built, implemented, and calibrated to design concepts, all in a scalable and controlled loading environment.
Validating computer vision solutions for hardware and software performance within the customer environment can be complex and time consuming. Dell Technologies Safety and Security Validation Labs are outfitted with leading technology from all major safety and security vendors, allowing us to validate best-of-breed computer vision applications with the entire Dell Technologies edge-to-cloud portfolio.
These proven lab validations with key partners accompany extensive documentation to simplify deployment and reduce the risk of data loss for our customers.
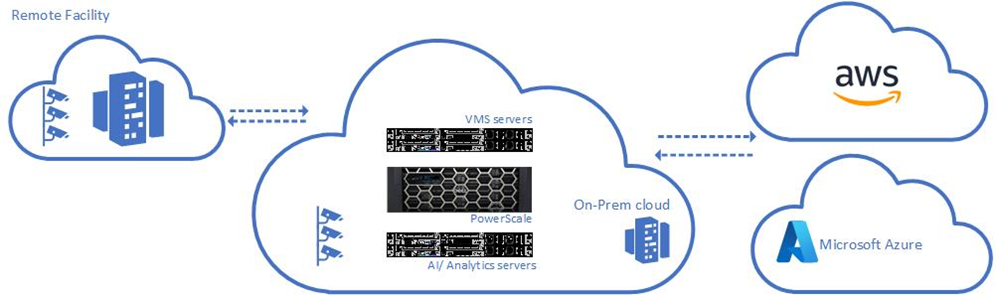
PowerScale is designed with your mission-critical video, safety, security, and business needs in mind.

Figure 1. Dell PowerScale offers unmatched storage performance for demanding workloads such as AI
Scalability
Start small and seamlessly grow large as needs expand by simply adding nodes to the cluster. This makes additional volume available in minutes, with no disruption to business. A single volume can support hundreds to thousands of cameras.
Avalability
With N+X architecture and six nines availability, you will always have access to recorded video. The system will continue recording, maintaining access to your data at all times.
Multicloud
Supporting S3 protocols, PowerScale integrates seamlessly with your hybrid and multicloud environment and reduces the cyber-attack surface without the need of third party bridges or data moving services.
Security
Security data is often sensitive in nature, raising privacy concerns. With ransomware defender available, you can ensure that your data is safe and secure from these attacks with a strategy to isolate, detect, and recover rapidly from a cyber incident. Designed with a cyber recovery vault, petabytes of data can be recovered within the hour limiting the impact of the cyber incident on your business.
Artificial Intelligence
Traditional security solutions will store your data in silos or “luns”. This adds a layer of complexity for data scientists while applying AI models to data sets. With PowerScale you have one single volume or target for your data. This dramatically simplifies applying data science to your data and speeds up time to market for your AI projects.
Modern Technology infrastructure for safety and security
The vital importance of security data in business operations is driving demand for modern architecture that can effectively store, protect, and manage. In addition, the combination of on-premises and off-premises cloud, known as hybrid cloud, has evolved into an essential requirement of modern architecture. Leveraging Dell PowerScale's multi-protocol support, your storage system becomes ready for multicloud environments. As businesses continue to incorporate AI solutions to optimize outcomes, consolidating data archives into a single volume expedites the introduction of AI projects to the market.

The #1 provider of enterprise storage[1] now offers an as-a-Service portfolio of scalable and elastic storage resources designed for OpEx treatment and 99.9999%[2] availability[3]. Simply choose the service levels that your workloads require and pay for what you use. Deploy on-premises in your data center or Dell-managed interconnected colocation facilities, enabling you to connect to the customers, partners, and ecosystems that deliver the most value.
Cloud Storage Services for unstructured data

Dell Technologies provides a wide range of choices for private, multicloud, and native cloud storage services for unstructured data.
- Enterprise-class performance, scale, and cyber resiliency for your most demanding workloads
- Flexibility to adjust your multicloud strategy as business and workload needs shift
- Enhanced productivity to simplify multicloud management so your team can spend more time on mission critical tasks
[1] IDC WW Quarterly Enterprise Storage Systems Tracker, 2022 Q4 historical release, March 9, 2023. Ranking by vendor revenue.
[2] OpEx treatment is subject to customer internal accounting review and policies.
[3] Based on hardware availability on common underlying block and file platform configurations. Actual hardware availability may vary.

A Quick Run Down: Mission Critical Architecture for Modern Security Solutions
Tue, 20 Jun 2023 20:21:51 -0000
|Read Time: 0 minutes
Nowadays, end users view their security data as mission critical. This means having uninterrupted access to recorded video and ensuring that recorders and archivers remain functional, which are essential for daily business operations. As a result, designs need to prioritize uptime while also taking other end user considerations into account.
A key consideration is storage efficiency. Stacking 2U NVRs for storage purposes is highly inefficient, both in terms of sustainability and rack space. To avoid over-procuring compute nodes to expand storage, it is better to build a proper on-premises storage solution that can scale at the petabyte scale. This ensures that the end user has sufficient storage capacity without compromising on the availability of compute nodes.
In addition to availability, regulatory compliance is another critical issue for end users. Achieving six 9s availability is possible, but if a node requires servicing, there may be no access to recorded video, leading to potential compliance issues. To mitigate this risk, it is recommended to shift from a RAID appliance to a node-based NAS storage system that uses erasure coding. This enables the end user to drop a full node of 20 HDDs and still record and access the video with six 9s availability.
In mission-critical environments such as airports and casinos, operations must continue during storage maintenance. For that reason, it’s important to have a storage solution that allows for maintenance that won’t affect daily operations. To sum it up: designing a storage solution that prioritizes efficiency, scalability, and regulatory compliance is critical for meeting the needs of end users in mission-critical environments.
What about Cloud?
Over the past several years, the trend of implementing a cloud-first strategy has been no secret. However, this strategy has posed numerous challenges for end-users. Although it is simple and fast to ramp up with a third-party cloud provider, and it provides a finance model that does not require large capital, over time the costs escalate with network access and egress fees. This has surprised many clients, causing them to re-evaluate this model.
The SIA Security Industry Privacy Guide suggests that best practice would not be to share security data with a third-party. These third-party contracts can also be through another third-party, such as a hardware manufacturer that has a third-party cloud contract and resells cloud services. As a result, it becomes challenging to manage risks as control of the data is no longer within the organization, yet the organization still holds liability for the security of the data being collected. This has led many organizations to repatriate to an on-premises or hybrid model for better control of their data.
We are now seeing a shift from a cloud-first to a cloud-smart strategy, where clients are becoming more selective about what they keep on-premises and what they store in a public cloud to maintain control and apply their policies to the data volumes more easily. This approach enables organizations to maintain control over sensitive data while still taking advantage of the benefits of cloud technology. In this way, adopting a cloud-smart strategy allows organizations to balance the benefits of cloud technology with the need for data control and security.
Cyber Security by Design
In today's security landscape, protecting sensitive privacy data and intellectual property is a top priority for most organizations. Unfortunately, we have witnessed high-profile incidents, such as the loss of biometric data for millions of people, resulting in privacy breaches and legislative action against end users. Even with the use of cloud providers, organizations must recognize that they are ultimately responsible for the security of the data they collect and store. Cloud environments are also susceptible to cyber breaches, which can be costly and time-consuming to recover from. Many organizations are still struggling to recover from incidents that occurred a year ago, causing significant operational disruptions and financial losses.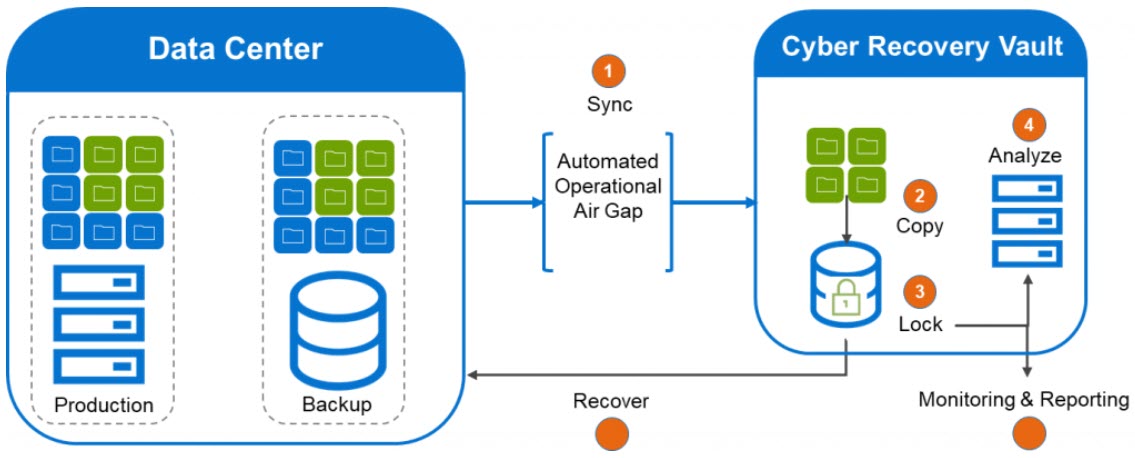
To mitigate the risks associated with cyber threats, today's mission critical architecture should prioritize cyber recovery by design. One effective strategy is to secure data in a cyber recovery vault that is offline and separated from the production cluster through an air gap. This approach allows for rapid recovery, enabling an end user to quickly regain control and resume operations with a clean data set. The recovery of a PB of data can now be achieved within an hour, as opposed to months in the past. By adopting a cyber recovery by design approach, organizations can proactively safeguard their data and minimize the impact of cyber incidents.
Embracing AI
Video is no longer just a tool for security purposes: it has become a valuable source of metadata that can be leveraged by multiple stakeholders within an organization. In fact, I have seen up to 14 different stakeholders within a single organization look to video metadata for a variety of non-security-related business outcomes. One such example is the retail industry, where video data has been used to enhance the overall customer experience.
As we shift towards using video for data science, new challenges arise for data scientists in achieving meaningful outcomes for their stakeholders. According to recent studies, data scientists spend 79% of their time searching for data in various silos to leverage. This is particularly true in LUN environments, where data silos are numerous, and correlating the appropriate camera feed to the disk group can be time-consuming and complex.
To address this challenge, organizations can create a single-volume data lake to store all necessary data. This allows data scientists to quickly map data targets and dramatically reduces the time-to-market for AI projects, making their time more productive and allowing them to focus on actual data science work rather than wrangling with data.
Summary
To sum up, we’ve discussed the importance of mission-critical architecture for modern security solutions, and highlighted the need for storage efficiency, scalability, and regulatory compliance to meet the needs of end-users in mission-critical environments. We discussed the shift from a cloud-first to a cloud-smart strategy, with a focus on maintaining control and security of data. Cybersecurity is a top priority for organizations, and we stress the need to prioritize cyber recovery by design to minimize the impact of cyber incidents. Finally, we touched upon the use of AI and the challenges of data silos and suggested creating a single-volume data lake to store all necessary data for AI projects, allowing data scientists to focus on actual data science work.
Thanks for reading! To learn more about modern security solutions, see:
Info Hub: https://infohub.delltechnologies.com/t/safety-security
Authors:
Mordekhay Shushan, Solution Architect
Brian St.Onge, Business Development Manager, Video Surveillance

